西电抗疫CTF(个人赛)
前言
感谢西电举办的这次抗疫CTF,既是宣传了CTF,也可以让大家学到更多的抗疫知识,让我们一起为西安加油!
Web
F12
AAEncode加密
゚ω゚ノ= /`m´)ノ ~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3; c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3) +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_') [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+/*´∇`*/(゚Д゚)[゚o゚]+ (゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((o^_^o) +(o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (o^_^o))+(o^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((o^_^o) +(o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((o^_^o) - (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (o^_^o))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((o^_^o) +(o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (o^_^o))+(゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((゚ー゚) + (o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚ー゚)+(゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((o^_^o) - (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((o^_^o) +(o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((o^_^o) +(o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (o^_^o))+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚o゚]) (゚Θ゚)) ('_');
在网站在线解密http://www.atoolbox.net/Tool.php?Id=703
flag{everything-will-be-fine};
tips
使用GET给answer传参
选错输出选错了哦,没选完整输出还有错误的选项哦,选项不多手动试了几下答案为B,E
PS:既然是抗疫CTF,我们不是不能就这样的到flag就退出,还是要看一看问题来学习如何抗疫
这里也可以写个脚本玩玩
import requests
url = "http://121.196.162.53:10000/"
answers = ['A', 'B', 'C', 'D', 'E', 'F', 'G', 'H', 'I']
answer = ''
for i in answers:
payload = {"answer": i}
r = requests.get(url, params=payload)
r.encoding = r.apparent_encoding
if "还有错误" in r.text:
answer += i+','
print(i)
payload = {"answer": answer[:-1]}
r = requests.get(url, params=payload)
print(r.text)
让我访问!
源码:
<?php
error_reporting(0);
if ($_SERVER['REQUEST_METHOD'] === "HS") {
include_once "flag.php";
echo $flag;
}
else {
highlight_file("index.php");
}
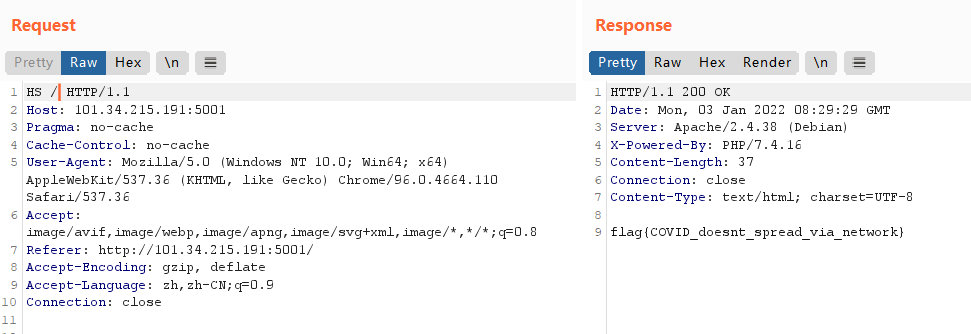
.....emmm,这个题好像是去年年底的moectf 2021中的一个原题,直接burp抓包将请求 方式改成HS就好
ez_game
小游戏的题,直接在js代码里找触发flag的方法,在crash.js最后找到可疑代码,格式化后
var _0x8818 = ['0x0', '0x2', '0x3', 'join', 'length', 'floor', '0x1', 'indexOf', '0x4', '02U03002P02V03F01X03E02N02803002P03202T02N03B02P03602N01D03702N03703302N03B03303202S02T03602U03903000X03H', '0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ'];
var _0x57c3 = function(_0x881849, _0x57c32c) { _0x881849 = _0x881849 - 0x0; var _0x4b9e4f = _0x8818[_0x881849]; return _0x4b9e4f; };
var _0x5959 = ['0x1', _0x57c3('0x4'), _0x57c3('0xa'), _0x57c3('0x7')];
var _0x293e = function(_0x2dd26e, _0x5ee868) { _0x2dd26e = _0x2dd26e - 0x0; var _0xca48db = _0x5959[_0x2dd26e]; return _0xca48db; };
var _0x10fd = [_0x57c3('0x5'), _0x293e(_0x57c3('0x6')), _0x57c3('0x3'), 'charAt', _0x293e('0x3')];
var _0x8ffe = function(_0x5dd332, _0x384d47) { _0x5dd332 = _0x5dd332 - 0x0; var _0x361472 = _0x10fd[_0x5dd332]; return _0x361472; };
function _0xb14cb12d() {
var _0x2689a7 = function(_0x43d38a) {
var _0x39b80f = _0x293e(_0x57c3('0x1'));
var _0x466eee = _0x39b80f[_0x8ffe('0x1')];
var _0x180e37, _0xb14adb, _0x38ce05, _0x1f9516, _0x21bae1 = 0x0,
_0x103ebd;
_0x103ebd = new Array(Math[_0x8ffe(_0x57c3('0x0'))](_0x43d38a[_0x8ffe(_0x293e('0x0'))] / 0x3));
_0x180e37 = _0x103ebd[_0x8ffe('0x1')];
for (var _0x557bae = 0x0; _0x557bae < _0x180e37; _0x557bae++) {
_0xb14adb = _0x39b80f[_0x293e(_0x57c3('0x2'))](_0x43d38a[_0x8ffe(_0x57c3('0x2'))](_0x21bae1));
_0x21bae1++;
_0x38ce05 = _0x39b80f['indexOf'](_0x43d38a[_0x8ffe('0x3')](_0x21bae1));
_0x21bae1++;
_0x1f9516 = _0x39b80f[_0x8ffe(_0x57c3('0x8'))](_0x43d38a[_0x8ffe('0x3')](_0x21bae1));
_0x21bae1++;
_0x103ebd[_0x557bae] = _0xb14adb * _0x466eee * _0x466eee + _0x38ce05 * _0x466eee + _0x1f9516;
}
_0x180e37 = eval('String.fromCharCode(' + _0x103ebd[_0x8ffe(_0x57c3('0x1'))](',') + ')');
return _0x180e37;
};
s = _0x57c3('0x9');
s = _0x2689a7(s);
alert(s);
}
function _0x102541(_0x105247) { if (_0x105247 > 0x1388) { return 0x1; } else return 0x0; }
里面的方法_0xb14cb12d()像是加密解密算法,尝试在控制台运行一下,得到flag
这种题之前见到过,这次算是凑巧做出来的,正常应该是要逆向分析js
真是个好简单的sql注入啊!
直接就是一个登录框,试了一下单引号被过滤了,直接转义单引号
username=1\&password=or 1=1#
直接获得flag
你喜欢copy吗
通过js不允许勾选,在设置里禁用js,然后复制,直接提交即可
PS:蚌埠住啊,搞了半天解密,先是用base36解密出一堆数字就没了头绪,没想到直接提交就好......
Crypto
健康码的题好有趣,让我学到了不少xixixi!
Bob的健康码1
查看md文件,然后再看py
database = {
'alice' : 1,
'bob': 0,
'carol' : 0,
'david' : 0
}
menu = '''
1. get health code from the database
2. show your code to help alice pass the checker
'''
class server(socketserver.BaseRequestHandler):
def _recv(self):
data = self.request.recv(1024)
return data.strip()
def _send(self, msg, newline=True):
if isinstance(msg , bytes):
msg += b'\n'
else:
msg += '\n'
msg = msg.encode()
self.request.sendall(msg)
def qrdecode(self , qr , size):
qr = b64decode(qr)
code = Image.frombytes('1' , size,qr)
m = pyzbar.decode(code)
return m[0].data
def qrencode(self , data):
qr = qrcode.QRCode(
error_correction = qrcode.ERROR_CORRECT_L,
border=1,
box_size=1
)
qr.add_data(data)
qr.make(fit=True)
img = qr.make_image()
self._send(b64encode(img.tobytes()))
def send_hcode(self, name):
if name not in database:
self._send(b'this one is not in the database')
else:
data = {
'name':name,
'time':int(time.time()),
'isRed':database[name]
}
data = json.dumps(data)
self.qrencode(data)
def checker(self , data):
data = json.loads(data.decode())
delta_time = time.time() - data['time']
if delta_time < 0 or delta_time > 30:
self._send(b'this health code has been overdue')
return 0
if data['isRed'] == 1:
self._send(b'No! your health code is red!')
return 0
self._send('hi '+data['name']+' your health code is green and you are healthy.')
if data['name'] == 'alice':
return 1
else:
return 0
def handle(self):
signal.alarm(120)
while 1:
self._send(menu)
choice = int(self._recv())
if choice == 1:
self._send(b'who are you')
name = self._recv()
self.send_hcode(name.decode())
elif choice == 2:
self._send(b'size:')
size = int(self._recv()) # the height or the width of the qrcode
self._send(b'your health code(in base64):')
qr = self._recv()
data = self.qrdecode(qr , (size,size))
if self.checker(data) == 1:
self._send(flag)
else:
self._send(b'wrong!')
exit(0)
这里只粘贴了中间的重要代码,通过下载相应的包,然后理清楚逻辑就可以nc回答出问题得到flag
这里特别的友好,给出了QR的生成代码,通过审计,大概意思是要让我们生成QR使得alice同学的健康码不为红色,我们通过加密算法,在生成图片时输出图片尺寸得知size=31,最后nc得到了flag,这里生成的健康码需要在30秒内提交,否则就失效了哦!
exp
import qrcode
import time
import pyzbar.pyzbar as pyzbar
from base64 import *
from PIL import Image
import json
database = {'alice': 0}
def qrencode(data):
qr = qrcode.QRCode(error_correction=qrcode.ERROR_CORRECT_L,
border=1,
box_size=1)
qr.add_data(data)
qr.make(fit=True)
img = qr.make_image()
print(img.size)
return b64encode(img.tobytes())
def send_hcode(name):
if name not in database:
print('this one is not in the database')
else:
data = {
'name': name,
'time': int(time.time()),
'isRed': database[name]
}
data = json.dumps(data)
return qrencode(data)
name = 'alice'
print(send_hcode(name))
做个核酸签个到
我的密码是真的差啊,这里的位运算是通过离散数学里的并集和交集求的
from Crypto.Util.number import *
from secret import flag
flag = bytes_to_long(flag)
tmp = getRandomNBitInteger(142)
a = flag | tmp
b = flag & tmp
print(tmp)
print(a)
print(b)
'''OUTPUT
4475588893486760807434877361949655702156202
10403436853134845129656953606837707260539903
2994485173442830774576326061629704337957160
'''
这里拿一个图来形容一下
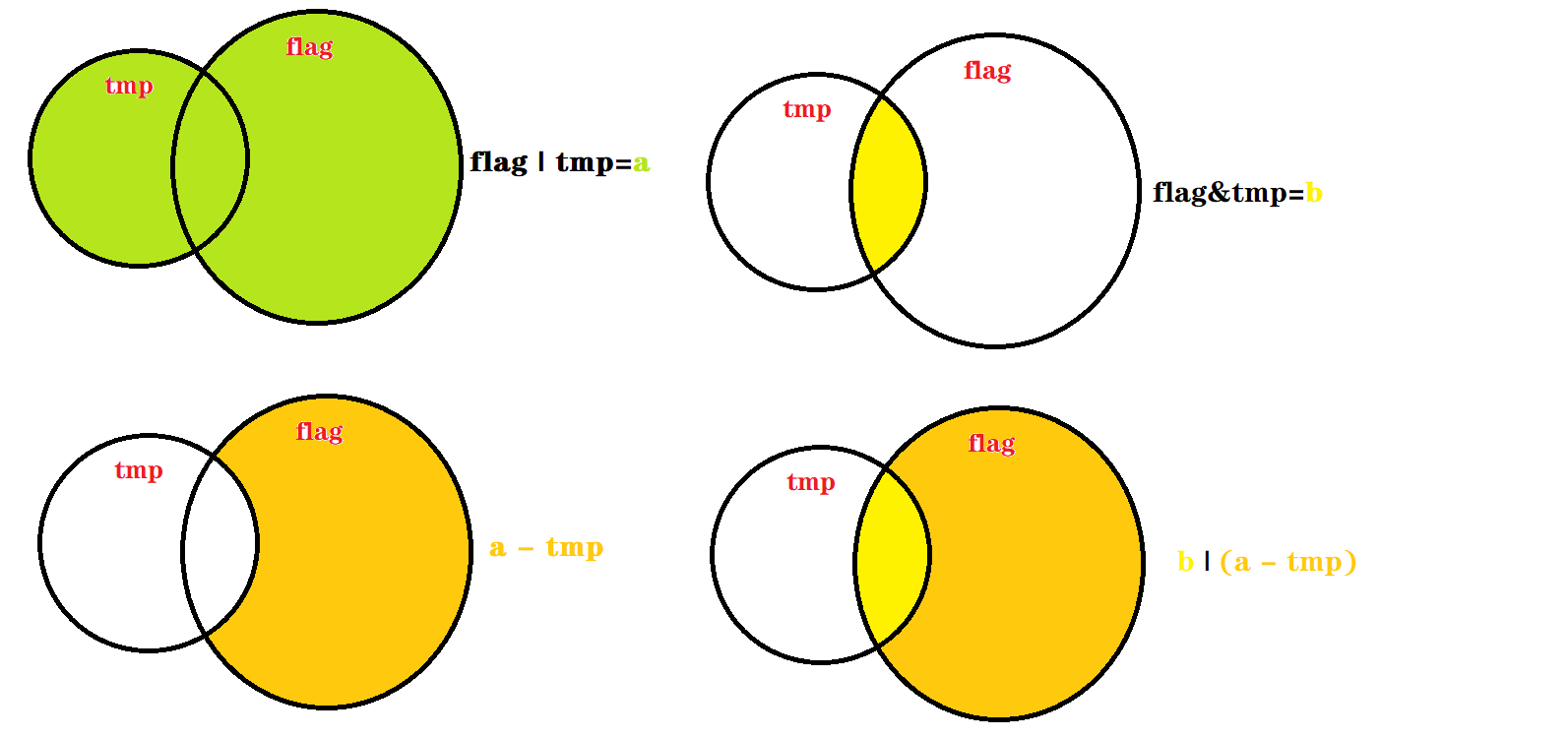
exp:
from Crypto.Util.number import *
tmp=4475588893486760807434877361949655702156202
a=10403436853134845129656953606837707260539903
b=2994485173442830774576326061629704337957160
flag = (a-tmp)|b
print(long_to_bytes(flag))
Misc
佛说
哆是恐礙怯心集曳哆瑟切侄。諳夜俱滅怯吉明呐恐摩缽涅罰夷想罰亦怯耨侄呼礙等梵三諳切缽大侄呼世諳亦醯哆世集數吉即爍大缽故俱羅缽若缽利訶奢菩梵利真姪哆藐勝
在前面加个佛曰:到与佛论禅上解密即可
戴上口罩
口罩图片下有个文本框,里面就是flag
打不开的压缩包
zip伪加密
使用ZipCenOp.jar直接解密,或者也可以通过Winhex等工具进行修改解密
java -jar ZipCenop.jar r xxx.zip
ZipCenOp.jar 百度网盘下载链接:https://pan.baidu.com/s/1RLRPN0fKWmqdaqLlV409Wg 提取码:twl4
不一样的贝斯
解密
4B355754434E4442495A5858555A444E48455A4534565A564F4A53464B3342534D455A5655324353493532444356334A48465A47493233514F3551564D33435A4B5257584F4D4B554A4244455157544D4955345641554A3548553D3D3D3D3D3D
==>Hex解码
K5WTCNDBIZXXUZDNHEZE4VZVOJSFK3BSMEZVU2CSI52DCV3JHFZGI23QO5QVM3CZKRWXOMKUJBDEQWTMIU4VAUJ5HU======
==>base32解码
Wm14aFozdm92NW5rdUl2a3ZhRGt1Wi9rdkpwaVlYTmw1THFHZlE9PQ==
==>base64两次解码
flag{这下你也会base了}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号