bp 开放重定向
检查:https://www.bugbountyhunter.com/vulnerability/?type=open_redirect
检查:https://portswigger.net/web-security/ssrf#bypassing-ssrf-filters-via-open-redirection
检查:https://portswigger.net/web-security/dom-based/open-redirection/lab-dom-open-redirection
Lab: DOM-based open redirection
https://portswigger.net/web-security/dom-based/open-redirection/lab-dom-open-redirection
找到审查元素(注意DOM型不是找源代码)中的DOM接收器
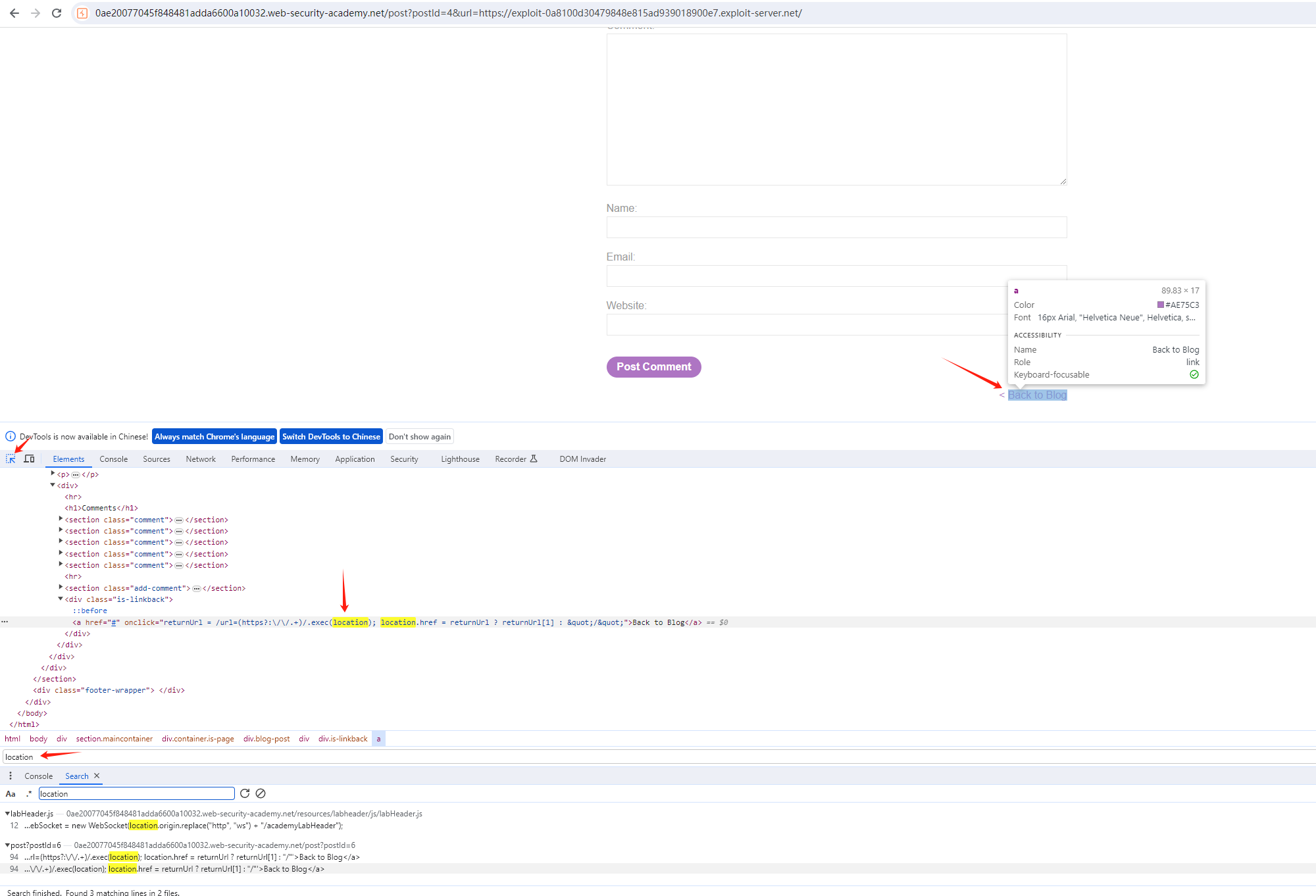
控制台:debug
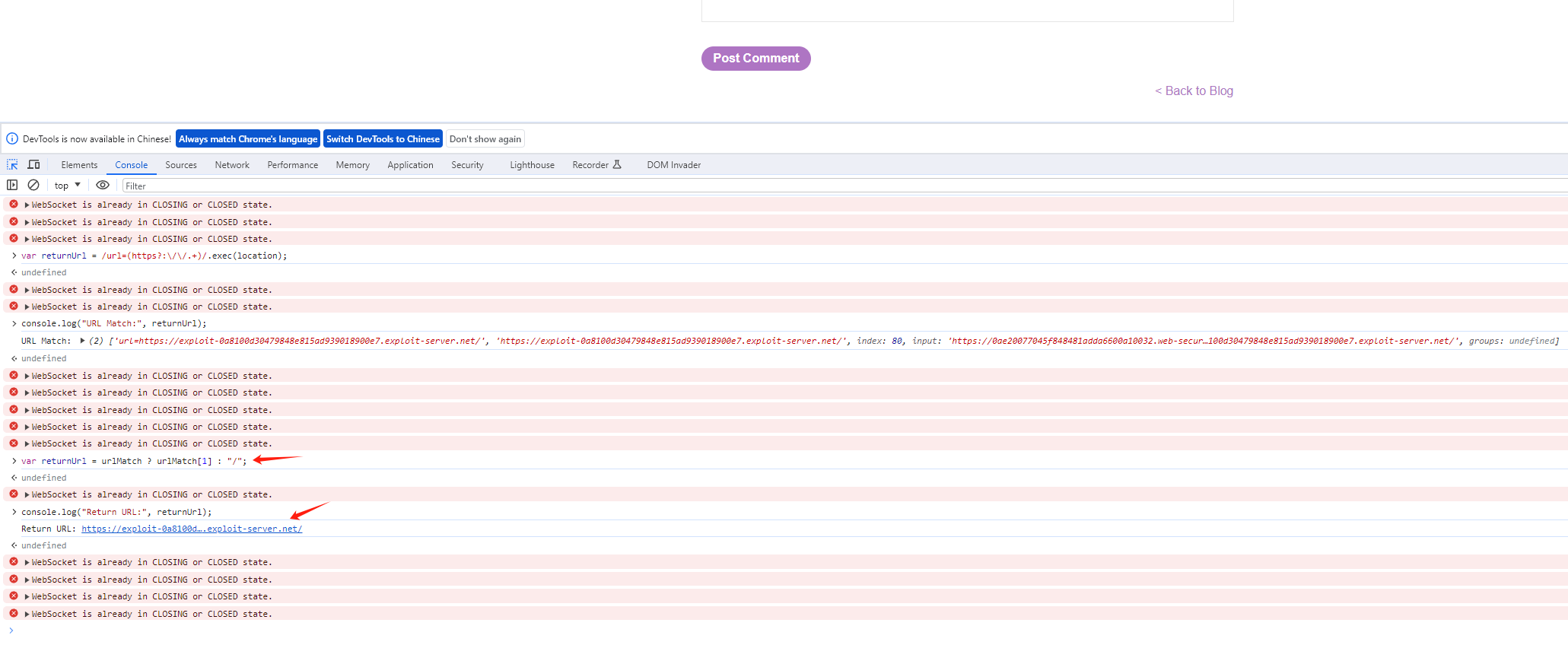
var returnUrl = /url=(https?:\/\/.+)/.exec(location);
console.log("URL Match:", returnUrl); // 查看匹配结果
var returnUrl = urlMatch ? urlMatch[1] : "/";
console.log("Return URL:", returnUrl); // 查看最终重定向的 URL
location.href = returnUrl; //所以就开放重定向了
主要接收器:
location
location.host
location.hostname
location.href
location.pathname
location.search
location.protocol
location.assign()
location.replace()
open()
element.srcdoc
XMLHttpRequest.open()
XMLHttpRequest.send()
jQuery.ajax()
$.ajax()
主要在于胡扯烂造,大家就当相声看看吧。【本人不保证技术的实用性,一切文章仅供参考,如有谬错,请留言】





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 25岁的心里话
· 闲置电脑爆改个人服务器(超详细) #公网映射 #Vmware虚拟网络编辑器
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· 零经验选手,Compose 一天开发一款小游戏!
· 一起来玩mcp_server_sqlite,让AI帮你做增删改查!!