华为交换机连接esight日志
主要是配置ip到交换机终端
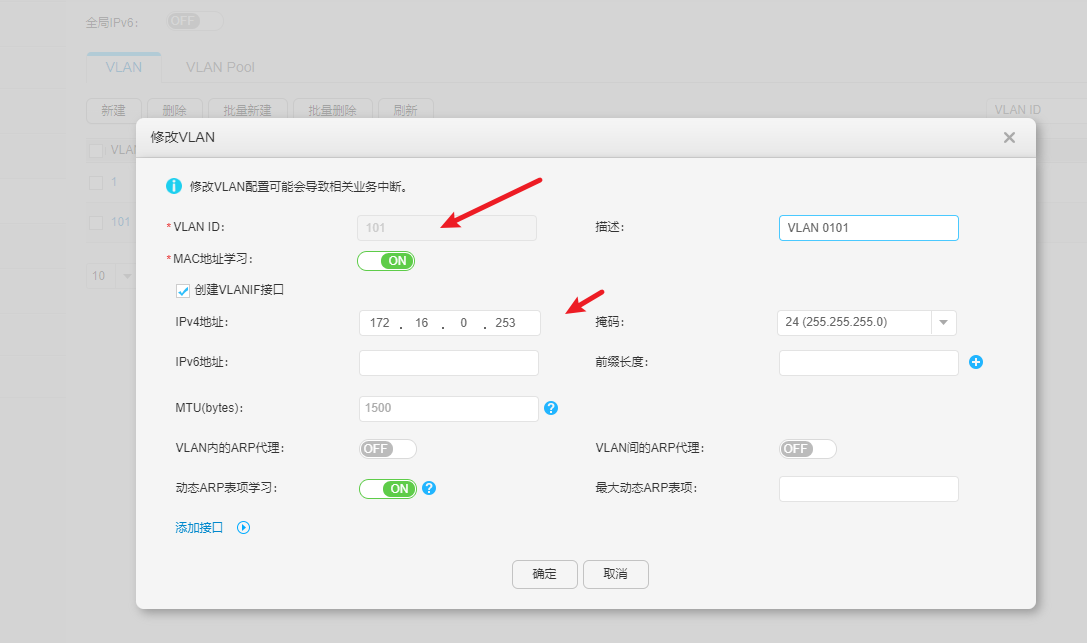
改vlan,接入口为汇聚核心到本交换机,vlan101,电脑口为vlan101。主要是接线。
改网关 ,为172.16.0.1 , ?
改静态路由 0.0.0.0 0.0.0.0 172.16.0.1
配置vlanif,
[caiwu-s5735]display current-configuration !Software Version V200R021C00SPC600 # sysname caiwu-s5735 # dns resolve dns server 202.102.152.3 dns server 202.102.154.3 # vlan batch 101 # authentication-profile name default_authen_profile authentication-profile name dot1x_authen_profile authentication-profile name dot1xmac_authen_profile authentication-profile name mac_authen_profile authentication-profile name multi_authen_profile authentication-profile name portal_authen_profile # telnet server enable telnet server-source -i Vlanif101 # http server-source -i Vlanif101 # radius-server template default # pki realm default certificate-check none # free-rule-template name default_free_rule # portal-access-profile name portal_access_profile # aaa authentication-scheme default authentication-mode local authentication-scheme radius authentication-mode radius authorization-scheme default authorization-mode local accounting-scheme default accounting-mode none local-aaa-user password policy administrator password history record number 0 password expire 0 domain default authentication-scheme radius accounting-scheme default radius-server default domain default_admin authentication-scheme default accounting-scheme default local-user root password irreversible-cipher $1c$*G7xG\-o*2$6Kit@;nL@>h[Am8:8R;&d%\|X,konBpRo7F#C3hE$ local-user root privilege level 3 local-user root ftp-directory flash: local-user root service-type telnet terminal ssh ftp x25-pad http local-user admin password irreversible-cipher $1c$kOC(G6l2'O$`rx@Nx!U^,@8x"JA:v#LTM3F+5\:f;DOvR"cqN%2$ local-user admin privilege level 13 local-user admin service-type http local-user test1 privilege level 2 # interface Vlanif101 ip address 172.16.0.253 255.255.255.0 # interface GigabitEthernet0/0/1 port default vlan 101 # interface GigabitEthernet0/0/2 port default vlan 101 # interface GigabitEthernet0/0/3 port link-type access port default vlan 101 loopback-detect enable port description desktop undo trust 8021p # interface GigabitEthernet0/0/4 port link-type access port default vlan 101 loopback-detect enable port description desktop undo trust 8021p # interface GigabitEthernet0/0/5 port link-type access port default vlan 101 loopback-detect enable port description desktop undo trust 8021p # interface GigabitEthernet0/0/6 port link-type access port default vlan 101 loopback-detect enable port description desktop undo trust 8021p # interface GigabitEthernet0/0/7 port link-type access port default vlan 101 loopback-detect enable port description desktop undo trust 8021p # interface GigabitEthernet0/0/8 port link-type access port default vlan 101 loopback-detect enable port description desktop undo trust 8021p # interface GigabitEthernet0/0/9 # interface GigabitEthernet0/0/10 # interface GigabitEthernet0/0/11 # interface GigabitEthernet0/0/12 # interface NULL0 # undo icmp name timestamp-request receive # ip route-static 0.0.0.0 0.0.0.0 172.16.0.1 # snmp-agent snmp-agent local-engineid 8000DDED033CC78621AB92 snmp-agent community write cipher %^%#VoDR=2E,%LL0&sA{s8]"MNp|5SH4wI$Xyt4`*Z:#jMR}9]>]O:LgKwOTV*kF$H_p@vK-V!h|MTXqp2Q9%^%# snmp-agent sys-info version v2c v3 snmp-agent group v3 tralin noauthentication write-view ViewDefault notify-view ViewDefault snmp-agent usm-user v3 ctquanlin snmp-agent usm-user v3 ctquanlin group tralin snmp-agent usm-user v3 ctquanlin authentication-mode md5 cipher %^%#`btr6)'rlD!qu*F@(/uS,ie{'P^[a!+]c\>'vD+E%^%# snmp-agent usm-user v3 ctquanlin privacy-mode aes256 cipher %^%#(qwVL&s`<T\n9RJ-&[%J4j8!WF8*S#m_x/:p1AND%^%# snmp-agent extend error-code enable snmp-agent protocol source-status all-interface undo snmp-agent protocol source-status ipv6 all-interface # stelnet server enable ssh user root ssh user root authentication-type password ssh user root service-type all ssh server-source -i Vlanif101 ssh server cipher aes256_ctr aes128_ctr ssh server hmac sha2_256 ssh server key-exchange dh_group16_sha512 dh_group15_sha512 dh_group14_sha256 dh_group_exchange_sha256 ssh client cipher aes256_ctr aes128_ctr ssh client hmac sha2_256 ssh client key-exchange dh_group16_sha512 dh_group15_sha512 dh_group14_sha256 dh_group_exchange_sha256 ssh server dh-exchange min-len 2048 ssh server publickey rsa_sha2_512 rsa_sha2_256 # user-interface con 0 authentication-mode password set authentication password cipher $1a$E<>dP~McZK$p,Y}"f[J[(;G_TW>#H3<2/sOC[=5f1H|654|{<qJ$ user-interface vty 0 4 authentication-mode aaa protocol inbound all user-interface vty 16 20 # dot1x-access-profile name dot1x_access_profile # mac-access-profile name mac_access_profile # ops # smi-server # return [caiwu-s5735]