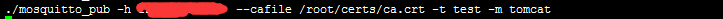
mosquitto --- 单向认证
1.生成证书
要单向配置SSL 需要 做三项前置工作
1. 生成CA证书
2.生成server 端证书,server 端key
github 的一个开源项目已经做到这点 ,详情可见 https://github.com/iandl/mqttitude/blob/master/tools/TLS/generate-CA.sh
为方便阅读,整个shell 代码先贴出来
#!/bin/sh
#(@)generate-CA.sh - Create CA key-pair and server key-pair signed by CA
# Copyright (c) 2013 Jan-Piet Mens <jpmens()gmail.com>
# All rights reserved.
#
# Redistribution and use in source and binary forms, with or without
# modification, are permitted provided that the following conditions are met:
#
# 1. Redistributions of source code must retain the above copyright notice,
# this list of conditions and the following disclaimer.
# 2. Redistributions in binary form must reproduce the above copyright
# notice, this list of conditions and the following disclaimer in the
# documentation and/or other materials provided with the distribution.
# 3. Neither the name of mosquitto nor the names of its
# contributors may be used to endorse or promote products derived from
# this software without specific prior written permission.
#
# THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS "AS IS"
# AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT LIMITED TO, THE
# IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE
# ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT OWNER OR CONTRIBUTORS BE
# LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, EXEMPLARY, OR
# CONSEQUENTIAL DAMAGES (INCLUDING, BUT NOT LIMITED TO, PROCUREMENT OF
# SUBSTITUTE GOODS OR SERVICES; LOSS OF USE, DATA, OR PROFITS; OR BUSINESS
# INTERRUPTION) HOWEVER CAUSED AND ON ANY THEORY OF LIABILITY, WHETHER IN
# CONTRACT, STRICT LIABILITY, OR TORT (INCLUDING NEGLIGENCE OR OTHERWISE)
# ARISING IN ANY WAY OUT OF THE USE OF THIS SOFTWARE, EVEN IF ADVISED OF THE
# POSSIBILITY OF SUCH DAMAGE.
set -e
DIR=${TARGET:='.'}
# A space-separated list of alternate hostnames (subjAltName)
# may be empty ""
ALTHOSTNAMES="broker.example.com foo.example.de"
CA_ORG='/O=MQTTitude.org/emailAddress=nobody@example.net'
CA_DN="/CN=An MQTT broker${CA_ORG}"
CACERT=${DIR}/ca
SERVER=${DIR}/server
SERVER_DN="/CN=$(hostname -f)$CA_ORG"
keybits=2048
openssl=$(which openssl)
function maxdays() {
nowyear=$(date +%Y)
years=$(expr 2032 - $nowyear)
days=$(expr $years '*' 365)
echo $days
}
function getipaddresses() {
/sbin/ifconfig |
sed -En '/inet6? /p' |
sed -Ee 's/inet6? (addr:)?//' |
awk '{print $1;}' |
sed -e 's/[%/].*//' |
egrep -v '(::1|127\.0\.0\.1)' # omit loopback to add it later
}
function addresslist() {
ALIST=""
for a in $(getipaddresses); do
ALIST="${ALIST}IP:$a,"
done
ALIST="${ALIST}IP:127.0.0.1,IP:::1,"
for h in $(echo ${ALTHOSTNAMES}); do
ALIST="${ALIST}DNS:$h,"
done
ALIST="${ALIST}DNS:localhost"
echo $ALIST
}
days=$(maxdays)
if [ -n "$CAKILLFILES" ]; then
rm -f $CACERT.??? $SERVER.??? $CACERT.srl
fi
if [ ! -f $CACERT.crt ]; then
# Create un-encrypted (!) key
$openssl req -newkey rsa:${keybits} -x509 -nodes -days $days -extensions v3_ca -keyout $CACERT.key -out $CACERT.crt -subj "${CA_DN}"
echo "Created CA certificate in $CACERT.crt"
$openssl x509 -in $CACERT.crt -nameopt multiline -subject -noout
chmod 400 $CACERT.key
chmod 444 $CACERT.crt
fi
if [ ! -f $SERVER.key ]; then
echo "--- Creating server key and signing request"
$openssl genrsa -out $SERVER.key $keybits
$openssl req -new \
-out $SERVER.csr \
-key $SERVER.key \
-subj "${SERVER_DN}"
chmod 400 $SERVER.key
fi
if [ -f $SERVER.csr -a ! -f $SERVER.crt ]; then
# There's no way to pass subjAltName on the CLI so
# create a cnf file and use that.
CNF=`mktemp /tmp/cacnf.XXXXXXXX` || { echo "$0: can't create temp file" >&2; exit 1; }
sed -e 's/^.*%%% //' > $CNF <<\!ENDconfig
%%% [ JPMextensions ]
%%% basicConstraints = critical,CA:false
%%% nsCertType = server
%%% keyUsage = nonRepudiation, digitalSignature, keyEncipherment
%%% nsComment = "Broker Certificate"
%%% subjectKeyIdentifier = hash
%%% authorityKeyIdentifier = keyid,issuer:always
%%% subjectAltName = $ENV::SUBJALTNAME
%%% # issuerAltName = issuer:copy
%%% nsCaRevocationUrl = http://mqttitude.org/carev/
%%% nsRevocationUrl = http://mqttitude.org/carev/
!ENDconfig
SUBJALTNAME="$(addresslist)"
export SUBJALTNAME # Use environment. Because I can. ;-)
echo "--- Creating and signing server certificate"
$openssl x509 -req \
-in $SERVER.csr \
-CA $CACERT.crt \
-CAkey $CACERT.key \
-CAcreateserial \
-CAserial "${DIR}/ca.srl" \
-out $SERVER.crt \
-days $days \
-extfile ${CNF} \
-extensions JPMextensions
rm -f $CNF
chmod 444 $SERVER.crt
fi
实际过程中大家可根据自己的需要修改这段脚本的内容,为了快速搭建我们的单向SSL, 我们这里不做任何修改,直接执行这段shell
执行完成后可生成 server.crt server.csr server.ke ca.crt ca.key ca.srl
$ wget https://github.com/iandl/mqttitude/blob/master/tools/TLS/generate-CA.sh . $ bash ./generate-CA.sh
配置mosquitto 配置文件
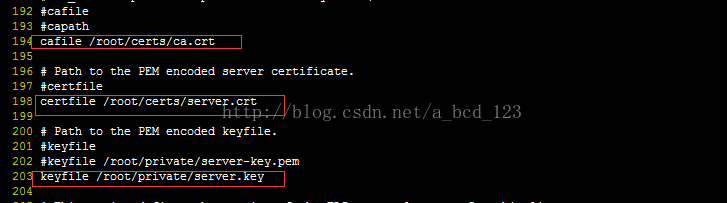
ca.crt, sever.crt, server.key 是上面生成的文件
启动 broker
启动 subscribe 端, 这里需要注意,如果sbuscreibe 端和broker 不在同一台机器,请将第一步生成的ca.crt 拷贝到 该机器的/root/certs下
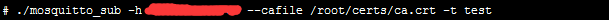
启动 publish 端, 如果publish 端和broker 不在同一台机器,请将第一步生成的ca.crt 拷贝到 该机器的/root/certs下