几个开发安全产品的设计
ASPM方面以下公司做的不错,而且可以参考其UI菜单的设计:
1. https://bionic.ai
https://www.youtube.com/watch?v=02AjwgjeTxs
https://www.youtube.com/watch?v=yTOcR0SxWJk&list=PLdim1TaRKDcViuHowJgeXUBbo9srbwrZW&index=3
What is Application Security Posture Management (ASPM)? (bionic.ai)
2. https://kondukto.io/platform
https://www.youtube.com/watch?v=Z1PD2BtKi94
3. https://www.saltworks.io/saltminer/
4. https://app.snyk.io/org/saaspeter/projects?groupBy=targets&searchQuery=&sortBy=highest+severity&filters[Show]=&filters[Integrations]=&before&after
5. https://www.enso.security/
6. https://snyk.io/solutions/aspm/
7. https://phoenix.security
8. https://tromzo.com/ ()
9. https://www.armorcode.com/ ()
10. https://vulcan.io/ ()
11. https://www.defectdojo.org (参考的一个开源系统,做的一般)
https://github.com/DefectDojo/django-DefectDojo
云平台DevOps:
1. 简单云 https://ezone.work cloudwe / asdf1234
tromzo.com的描述:
How Do We Do All This? – Intelligence Graph
Prioritize remediation of vulnerable dependencies that have an exploit available.
Deduplicate thousands of vulnerabilities in production hosts and containers.
Automatically identify which code repositories are processing PCI/PII/TIN relevant information.
Comprehensive Inventory
Within minutes gain visibility on all of your software assets (code repos, containers, microservices, etc.) – from applications to infrastructure.
Understand Your Riskiest Assets
Know what assets are in production, Internet facing or business critical.
Prioritize assets with PHI/PII data or in scope of compliance.
Quickly triage assets posing the highest risk, across tools like SCA, SAST, DAST, CSPM, and more.
Leverage context from Intelligence Graph to tune out the noise and automate the remediation lifecycle, so you can eliminate the manual processes of triaging, prioritizing, associating ownership, risk acceptance, and compliance workflows.
https://tromzo.com/application-security-posture-managementhttps://tromzo.com/application-security-posture-management
https://tromzo.com/vulnerability-remediation
Vulcan.io的描述
Asset view : code projects, images, hosts
https://vulcan.io/wp-content/uploads/2023/07/Enrich-compressed.mp4
https://vulcan.io/correlate-vulnerability-data/
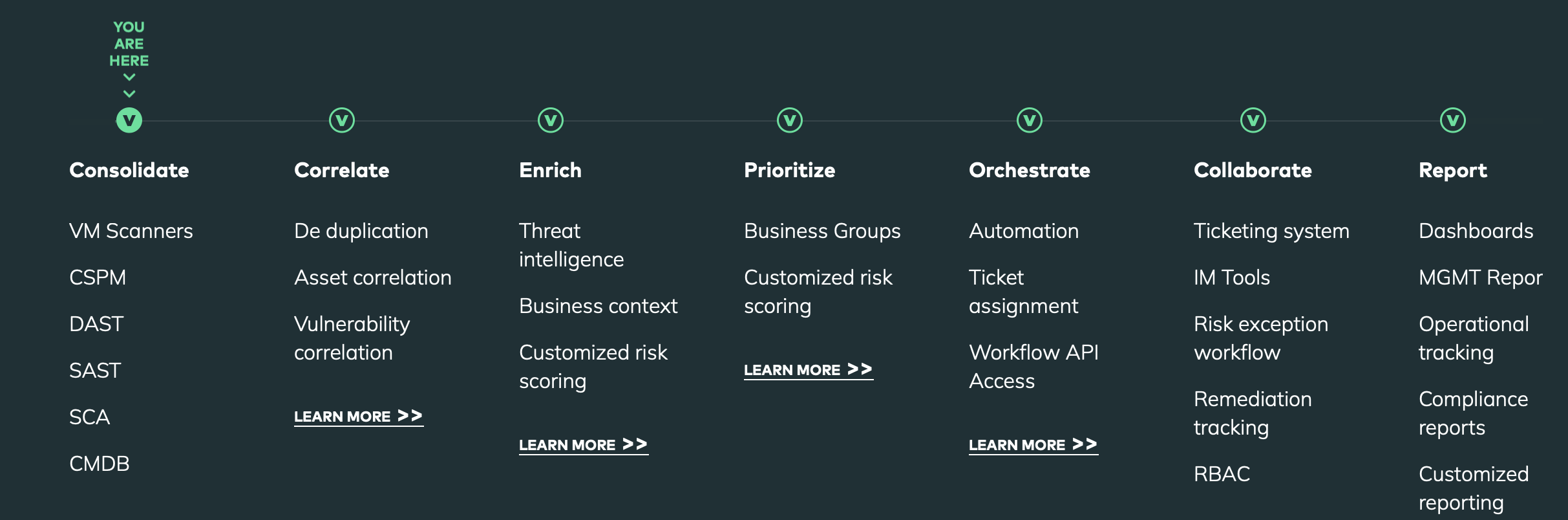
提出几步:
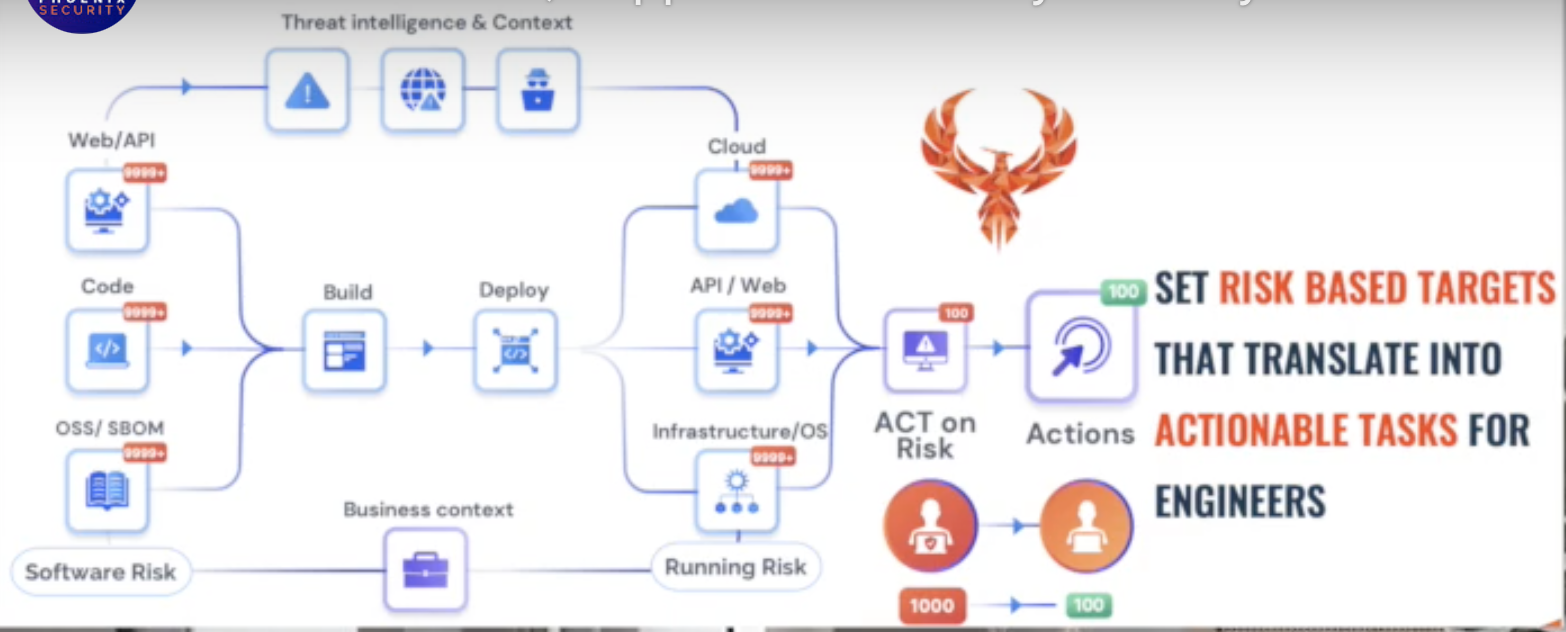
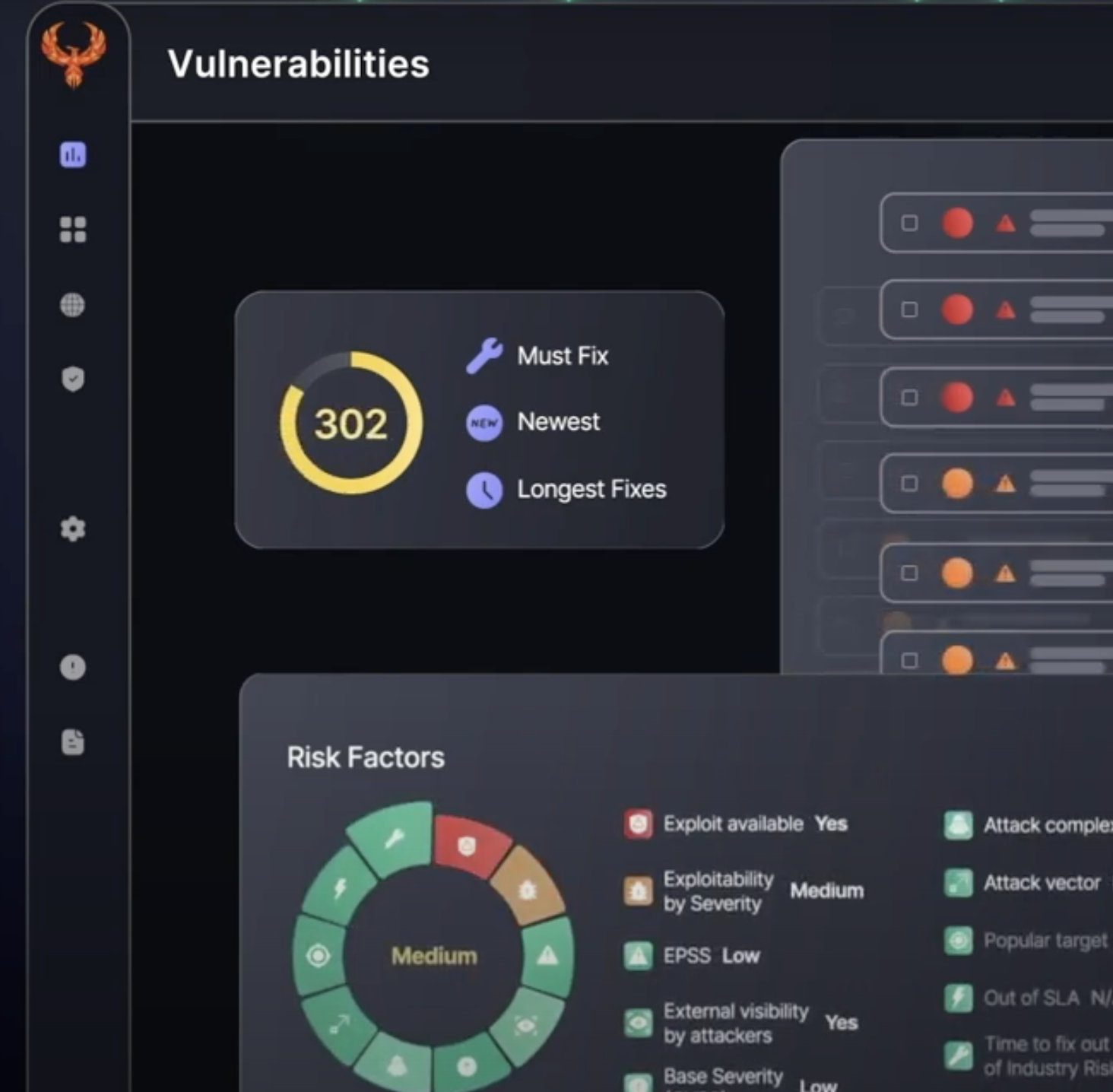
phoenix.security的截图:



 浙公网安备 33010602011771号
浙公网安备 33010602011771号