Understanding the difference between a Java keystore and a truststore
A truststore is a file that contains one or more public certificates, but no private keys.

A keystore is a file that contains one or more public certificates and one or more private keys. This is typically a "chain" where the keystore contains the root certificate authority (CA) certificate, the intermediate certificate authority (CA) certificate (issued by the root CA), and one or more server certificates (issued by the intermediate CA).

Let's say you have a web server that produces HTTPS web pages, such as https://www.example.com. When a client submits a request to get a web page from your web server, a TLS handshake occurs, so that the packets exchanged between the client and server are encrypted. In this scenario, a keystore could be used. The keystore on the server would contain the public certificate and private key that will be used. A keystore is a file such as foo.p12 or bar.jks.
A keystore contains both public certificates and private keys
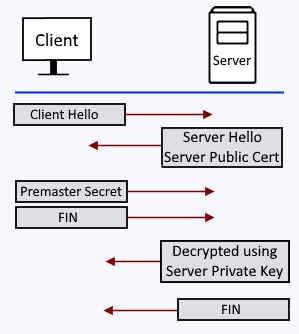
The TLS handshake look like this.
- The client sends a "Client Hello" packet to the server.
- The server sends a "Server Hello" packet to the client, which includes the public certificate in the keystore file (not the private key).
- The client validates the public certificate against it's list of known, trusted certificate authorities, and then sends the server a premaster secret (random string of data). The premaster secret is encrypted with the public certificate. The server decrypts the premaster secret with the private key in the keystore.
- The client generates a session key and sends the server a FIN (finished) packet.
- The server generates a session key and sends the client a FIN (finished) packet.
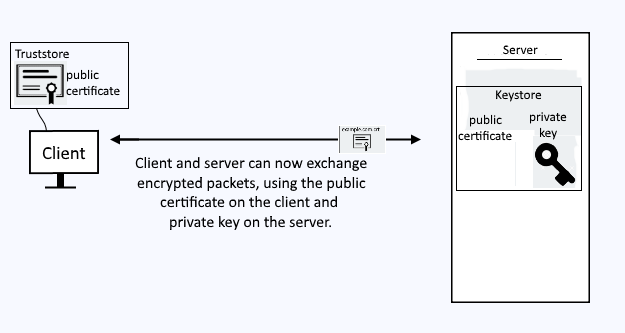
Let's say you know you are going to be requesting a resource from a server often over a secured channel, such as HTTPS. Instead of going through the SSL handshake negotiation process to have the server provide you with the public certificate, you could store the servers public certificate in a truststore. Then, when you need to request a resource from the server, you will already have the certificate, so that you can present the certificate to the server and get on with the request. A truststore is a file, such as trust.p12.
A truststore contains public certificates. A truststore does not contain private keys.
The Java keytool command can be used to view, import, add, and remove public certificates and private keys from a keystore or truststore. In this example, the key.p12 keystore contains a public certificate called "default". A private key doesn't contain user specific data, such as an "alias" or "expiration date", so the user specific data in the keystore represents the public certificates, not the private key.
~]# keytool -list -v -storetype PKCS12 -storepass changeit -keystore /path/to/key.p12
. . .
Alias: default
In this example, the trust.p12 truststore contains a public certificate called "example.com".
~]# keytool -list -v -storetype PKCS12 -storepass changeit -keystore /path/to/trust.p12
. . .
Alias: example.com



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· TypeScript + Deepseek 打造卜卦网站:技术与玄学的结合
· 阿里巴巴 QwQ-32B真的超越了 DeepSeek R-1吗?
· 【译】Visual Studio 中新的强大生产力特性
· 【设计模式】告别冗长if-else语句:使用策略模式优化代码结构
· AI与.NET技术实操系列(六):基于图像分类模型对图像进行分类
2017-09-25 DNS服务器的维护与故障排除
2017-09-25 Unbound服务的安装与运行管理
2017-09-25 DNS域名解析
2015-09-25 telnet IP不通/sybase central工具无法连接到数据库
2014-09-25 将samba加入到windows域《转载》
2014-09-25 idmap_ad — Samba's idmap_ad Backend for Winbind《转载》
2014-09-25 Enabling Active Directory Authentication for VMWare Server running on Linux《转载》