Morgan Stanley telephone interview
Today is Monday, April 28. I get a telephone call from Morgan Stanley in Shanghai. My examiner is a man, whose English is good. By the way, he is a Chinese. So he can understand my poor English. I was very nervous at the beginning, and I cannot follow him. Maybe he notice that, he slow down his speed. Let me remind the process and questions of the phone interview.
At the beginning, he said that the interview is divided into three part.
Morgan Stanley phone interview part one: What do you know about Morgan Stanley?
In this part, I acted vary stupid. I just answered that Morgan Stanley is a business bank. Then i donot kown what to say. I felt awkward at that moment. He felt that, and ask me another question "why are you think you fit for the work?" I had prepared for this question, so i illustrated him my many advantage.
Morgan Stanley phone interview part two: It is technical interview.
Question one: what is difference between pass-by-value and pass-by-reference?
Question two: what is the usage of const?
Question three: what is the difference beteen reference and pointer?
Question four: what is the usage of copy construct function?
Question five: what is the Singleton Pattern? You can explain it with any language?
Question six: what is the polymorphism? Can you explain it?
Question seven: Explain the inner join, left join and right join.
Question eight: what is the Database normalization? And what is the difference between form A and form B?
Question nine: what is the difference between concurrency and parallelism?
Question ten: what is the difference between Macro definition and inline funciton?
Question eleven: why do we need virtual destructor function?
Above is about the basic knowledge. The following is two programming problems.
Programming problem one: reverse a singly linked list
Programming problem two: find the middle of a singly linked list
Morgan Stanley phone interview part three: What do you want do know about Morgan Stanley?
In this part, I still act stupid. I donot know what to ask.
Answer one:
Pass by reference: In pass by reference address of the variable is passed to a function. Whatever changes made to the formal parameter will affect to the actual parameters. Same memory location is used for both variables. It is useful when you required to return more than one.
Pass by value: In this method value of the variable is passed. Changes made to formal will not affect the actual parameters. Different memory locations will be created for both variables. Here there will be temporary variable created in the function stack which does not affect the original variable.
Answer two:
Variables declared with ‘const’ added become constants and cannot be altered by the program.
http://duramecho.com/ComputerInformation/WhyHowCppConst.html
Answer three:
References, then, are the feature of choice when you know you have something to refer to, when you'll never want to refer to anything else, and when implementing operators whose syntactic requirements make the use of pointers undesirable. In all other cases, stick with pointers.
http://www.cplusplus.com/articles/ENywvCM9/
Answer four:
A copy constructor is a special constructor for a class/struct that is used to make a copy of an existing instance. According to the C++ standard, the copy constructor for MyClass must have one of the following signatures:
MyClass( const MyClass& other );
MyClass( MyClass& other );
MyClass( volatile const MyClass& other );
MyClass( volatile MyClass& other );
First, you should understand that if you do not declare a copy constructor, the compiler gives you one implicitly. The implicit copy constructor does a member-wise copy of the source object.
In many cases, this is sufficient. However, there are certain circumstances where the member-wise copy version is not good enough. By far, the most common reason the default copy constructor is not sufficient is because the object contains raw pointers and you need to take a "deep" copy of the pointer. That is, you don't want to copy the pointer itself; rather you want to copy what the pointer points to. Why do you need to take "deep" copies? This is typically because the instance owns the pointer; that is, the instance is responsible for calling delete on the pointer at some
point (probably the destructor). If two objects end up calling delete on the same non-NULL pointer, heap corruption results.
Answer five:
Motivation
Sometimes it's important to have only one instance for a class. For example, in a system there should be only one window manager (or only a file system or only a print spooler). Usually singletons are used for centralized management of internal or external resources and they provide a global point of access to themselves.
The singleton pattern is one of the simplest design patterns: it involves only one class which is responsible to instantiate itself, to make sure it creates not more than one instance; in the same time it provides a global point of access to that instance. In this case the same instance can be used from everywhere, being impossible to invoke directly the constructor each time.
The implementation involves a static member in the "Singleton" class, a private constructor and a static public method that returns a reference to the static member.
The Singleton Pattern defines a getInstance operation which exposes the unique instance which is accessed by the clients. getInstance() is is responsible for creating its class unique instance in case it is not created yet and to return that instance.
The constructor should not be accessible from the outside of the class to ensure the only way of instantiating the class would be only through the getInstance method.
The getInstance method is used also to provide a global point of access to the object.
Answer six:
Answer seven:

The picture is coming from:
http://i.stack.imgur.com/VQ5XP.png
Answer eight:
Database normalization is the process of organizing the fields and tables of a relational database to minimize redundancy.
Normalization usually involves dividing large tables into smaller (and less redundant) tables and defining relationships between them. The objective is to isolate data so that additions, deletions, and modifications of a field can be made in just one table and then propagated through the rest of the database using the defined relationships.
the First Normal Form,
the Second Normal Form,
the Third Normal Form,
the Boyce-Codd Normal Form,
Answer nine:
Concurrency means that two or more calculations happen within the same time frame, and there is usually some sort of dependency between them.
Parallelism means that two or more calculations happen simultaneously.
Answer ten:
The major difference between inline functions and macros is the way they are handled. Inline functions are parsed by the compiler, whereas macros are expanded by the C++ preprocessor.
The difference between an inline function and a regular function is that wherever the compiler finds a call to an inline function, it writes a copy of the compiled function definition. However, with a regular function, a normal function call is generated.
Answer eleven:
virtual destructor is used, so that while deleting the pointer to a base class but pointing to a base class invokes the Derived classes destructor first, then the base classes destrcutore. Hence preventing a memory leak.
For example, suppose B is a base class and D is a class derived from B and suppose both classes have declared their destrcutor as virtual. Suppose a pointer B *ptr is initialized as follows:
B *ptr = new D();
Now the ptr is of type B* but points to an object of D. So when this object is freed or goes out of scope D's destructor will be called since the destructors have been declared as virtual.
Programming answer one:
Solution one:
Reverse a singly linked list with three pointers.
Create three pointers pointer1, pointer2 and pointer3.
one pointer points at the new list header, and one points at the old list header and one pointer points at the next position of the old list header.
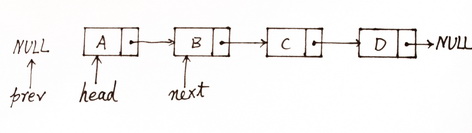
The initial status

After one iterator
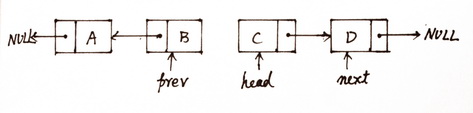
Afer two iterator
Repeat the process util the prev go to the tail of the old list.
The picture is from:http://my.csdn.net/uploads/201205/20/1337526604_2684.jpg
Solution two:
Create two header pointer, one for old list, the other for new list.
Step 1:Get the current header node in the old list, and insert into the header of the new list.
Step 2:Then the header in the old list move to next.
Step 3: Repeat the step 1 and 2 util all nodes are in the new list.
Programming answer two:
Create two pointers.
At first, the two pointers are both point at the header oh the list.
Then pointer one move forward two steps at a time, and the other point move forward one step at a time.
When the pointer one go to the tail of the list, the pointer two arives at the middle of the list.
useful reference
http://targetjobs.co.uk/employer-hubs/morgan-stanley/323465-prepare-for-your-morgan-stanley-interview-with-our-advice-on-approaching-questions
http://www.wikijob.co.uk/wiki/morgan-stanley-technology

