Cas Server源码编译现场实例
最近公司有项目需要做单点登录,根据要求就写下这篇从github上下载的包到项目编译通过,再到修改原代码实现自己的特殊逻辑。
前提:
java环境
tomcat环境
maven环境
MyEclipse开发环境
一、cas项目构建方式汇总
cas-4.2.0以后(包括4.2.0)使用gradle构建

二、怎样构建一个自定义的cas源码项目
2.1 资源地址
官网:https://www.apereo.org/projects/cas
源码:https://github.com/Jasig/cas
https://github.com/Jasig/java-cas-client(后面要用到)
PS: 我这里演示的cas-server版本是Maven版的4.0.5
2.2 下载源码并转成项目代码
从https://github.com/apereo/cas/releases?after=v4.1.0下载cas-4.0.5的源码Source code (zip),然后解压放至你的workspace中。打开命令窗口,进入cas项目的根目录(E:\me_workspace2\cas-4.0.5>),键入命令mvn eclipse:eclipse,回车,让它飞一会,结束后你就可以。然后你可以使用MyEclipse导入项目了,如下图:
2.3 将源码编译成war包
在命令窗口执行E:\me_workspace2\cas-4.0.5>mvn install -DskipTests,等待若干分钟后\cas-4.0.5\cas-server-webapp\target\目录下未发现生成cas.war 文件,并且发现下文的问题1,并且在问题1中得到你想要的war包。
2.4 怎样将构建一个带有源码的cas项目
将cas.war包修改扩展名,cas.zip,解压。得到一堆文件。
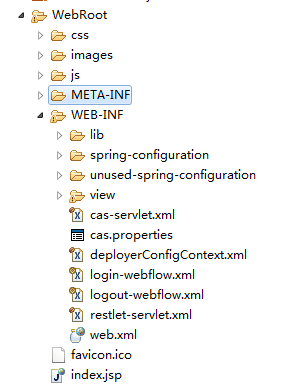
新建一个Web项目,并将解压好的文件放入项目中,\WEB-INF\classes目录下文件统统放入src目录下,其他的文件根据下图自行拷贝。
这样的话,你就可以部署到Tomcat中运行了,localhost:8080/项目名。
2.5 新增数据库
这里使用SQLserver数据库,配置文件在WEB-INF目录下的deployerConfigContext.xml文件,内容如下:
1 <?xml version="1.0" encoding="UTF-8"?> 2 <!-- 3 4 Licensed to Jasig under one or more contributor license 5 agreements. See the NOTICE file distributed with this work 6 for additional information regarding copyright ownership. 7 Jasig licenses this file to you under the Apache License, 8 Version 2.0 (the "License"); you may not use this file 9 except in compliance with the License. You may obtain a 10 copy of the License at the following location: 11 12 http://www.apache.org/licenses/LICENSE-2.0 13 14 Unless required by applicable law or agreed to in writing, 15 software distributed under the License is distributed on an 16 "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY 17 KIND, either express or implied. See the License for the 18 specific language governing permissions and limitations 19 under the License. 20 21 --> 22 <!-- 23 | deployerConfigContext.xml centralizes into one file some of the declarative configuration that 24 | all CAS deployers will need to modify. 25 | 26 | This file declares some of the Spring-managed JavaBeans that make up a CAS deployment. 27 | The beans declared in this file are instantiated at context initialization time by the Spring 28 | ContextLoaderListener declared in web.xml. It finds this file because this 29 | file is among those declared in the context parameter "contextConfigLocation". 30 | 31 | By far the most common change you will need to make in this file is to change the last bean 32 | declaration to replace the default authentication handler with 33 | one implementing your approach for authenticating usernames and passwords. 34 +--> 35 36 <beans xmlns="http://www.springframework.org/schema/beans" 37 xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" 38 xmlns:p="http://www.springframework.org/schema/p" 39 xmlns:c="http://www.springframework.org/schema/c" 40 xmlns:tx="http://www.springframework.org/schema/tx" 41 xmlns:util="http://www.springframework.org/schema/util" 42 xmlns:sec="http://www.springframework.org/schema/security" 43 xsi:schemaLocation="http://www.springframework.org/schema/beans http://www.springframework.org/schema/beans/spring-beans-3.2.xsd 44 http://www.springframework.org/schema/tx http://www.springframework.org/schema/tx/spring-tx-3.2.xsd 45 http://www.springframework.org/schema/security http://www.springframework.org/schema/security/spring-security-3.2.xsd 46 http://www.springframework.org/schema/util http://www.springframework.org/schema/util/spring-util.xsd"> 47 48 <!-- 49 | The authentication manager defines security policy for authentication by specifying at a minimum 50 | the authentication handlers that will be used to authenticate credential. While the AuthenticationManager 51 | interface supports plugging in another implementation, the default PolicyBasedAuthenticationManager should 52 | be sufficient in most cases. 53 +--> 54 <bean id="authenticationManager" class="org.jasig.cas.authentication.PolicyBasedAuthenticationManager"> 55 <constructor-arg> 56 <map> 57 <!-- 58 | IMPORTANT 59 | Every handler requires a unique name. 60 | If more than one instance of the same handler class is configured, you must explicitly 61 | set its name to something other than its default name (typically the simple class name). 62 --> 63 <entry key-ref="proxyAuthenticationHandler" value-ref="proxyPrincipalResolver" /> 64 <!--原始配置--> 65 <!--<entry key-ref="primaryAuthenticationHandler" value-ref="primaryPrincipalResolver" />--> 66 <!--接入自定义数据库--> 67 <entry key-ref="dbAuthenticationHandler" value-ref="primaryPrincipalResolver" /> 68 69 </map> 70 </constructor-arg> 71 72 <!-- Uncomment the metadata populator to allow clearpass to capture and cache the password 73 This switch effectively will turn on clearpass. 74 <property name="authenticationMetaDataPopulators"> 75 <util:list> 76 <bean class="org.jasig.cas.extension.clearpass.CacheCredentialsMetaDataPopulator" 77 c:credentialCache-ref="encryptedMap" /> 78 </util:list> 79 </property> 80 --> 81 82 <!-- 83 | Defines the security policy around authentication. Some alternative policies that ship with CAS: 84 | 85 | * NotPreventedAuthenticationPolicy - all credential must either pass or fail authentication 86 | * AllAuthenticationPolicy - all presented credential must be authenticated successfully 87 | * RequiredHandlerAuthenticationPolicy - specifies a handler that must authenticate its credential to pass 88 --> 89 <property name="authenticationPolicy"> 90 <bean class="org.jasig.cas.authentication.AnyAuthenticationPolicy" /> 91 </property> 92 </bean> 93 94 <!-- Required for proxy ticket mechanism. --> 95 <!--默认配置:开启SSL--> 96 <bean id="proxyAuthenticationHandler" 97 class="org.jasig.cas.authentication.handler.support.HttpBasedServiceCredentialsAuthenticationHandler" 98 p:httpClient-ref="httpClient" /> 99 <!--新配置关闭SSL 100 <bean id="proxyAuthenticationHandler" 101 class="org.jasig.cas.authentication.handler.support.HttpBasedServiceCredentialsAuthenticationHandler" 102 p:httpClient-ref="httpClient" p:requireSecure="false"/> 103 --> 104 105 <!-- 106 | TODO: Replace this component with one suitable for your enviroment. 107 | 108 | This component provides authentication for the kind of credential used in your environment. In most cases 109 | credential is a username/password pair that lives in a system of record like an LDAP directory. 110 | The most common authentication handler beans: 111 | 112 | * org.jasig.cas.authentication.LdapAuthenticationHandler 113 | * org.jasig.cas.adaptors.jdbc.QueryDatabaseAuthenticationHandler 114 | * org.jasig.cas.adaptors.x509.authentication.handler.support.X509CredentialsAuthenticationHandler 115 | * org.jasig.cas.support.spnego.authentication.handler.support.JCIFSSpnegoAuthenticationHandler 116 --> 117 <!--默认配置:直接配置账号密码--> 118 <!-- 119 <bean id="primaryAuthenticationHandler" 120 class="org.jasig.cas.authentication.AcceptUsersAuthenticationHandler"> 121 <property name="users"> 122 <map> 123 <entry key="casuser" value="Mellon"/> 124 <entry key="castest" value="castest"/> 125 </map> 126 </property> 127 </bean> 128 --> 129 130 <bean class="org.jasig.cas.adaptors.jdbc.QueryDatabaseAuthenticationHandler"> 131 <property name="sql" value="select password from ucenter_user where username=? " /> 132 <property name="dataSource" ref="dataSource" /> 133 </bean> 134 135 136 <bean id="dataSource" class="org.springframework.jdbc.datasource.DriverManagerDataSource"> 137 <!--MySql数据库认证--> 138 <!-- 139 <property name="driverClassName"><value>com.mysql.jdbc.Driver</value></property> 140 <property name="url"><value>jdbc:mysql://192.168.0.58:3306/cassso</value></property> 141 <property name="username"><value>metro_monitor</value></property> 142 <property name="password"><value>123456</value></property> 143 --> 144 <!--MsSql数据库认证--> 145 <property name="driverClassName"><value>com.microsoft.sqlserver.jdbc.SQLServerDriver</value></property> 146 <property name="url"><value>jdbc:sqlserver://192.168.0.58:1433;DatabaseName=CasSso</value></property> 147 <property name="username"><value>sa</value></property> 148 <property name="password"><value>123456</value></property> 149 </bean> 150 151 <!--Mysql密码加密--> 152 <bean id="passwordEncoder" 153 class="org.jasig.cas.authentication.handler.DefaultPasswordEncoder" 154 c:encodingAlgorithm="MD5" 155 p:characterEncoding="UTF-8" /> 156 157 <!--验证处理--> 158 <bean id="dbAuthenticationHandler" 159 class="org.jasig.cas.adaptors.jdbc.QueryDatabaseAuthenticationHandler"> 160 <property name="dataSource" ref="dataSource"></property> 161 <property name="sql" value="select LoginPassword as password from ssoaccount where LoginAccount=? "></property> 162 <property name="passwordEncoder" ref="passwordEncoder"></property> 163 </bean> 164 165 <!-- Required for proxy ticket mechanism --> 166 <bean id="proxyPrincipalResolver" 167 class="org.jasig.cas.authentication.principal.BasicPrincipalResolver" /> 168 169 <!-- 170 | Resolves a principal from a credential using an attribute repository that is configured to resolve 171 | against a deployer-specific store (e.g. LDAP). 172 --> 173 <bean id="primaryPrincipalResolver" 174 class="org.jasig.cas.authentication.principal.PersonDirectoryPrincipalResolver" > 175 <property name="attributeRepository" ref="attributeRepository" /> 176 </bean> 177 178 <!-- 179 Bean that defines the attributes that a service may return. This example uses the Stub/Mock version. A real implementation 180 may go against a database or LDAP server. The id should remain "attributeRepository" though. 181 +--> 182 <!--注释掉默认配置 183 <bean id="attributeRepository" class="org.jasig.services.persondir.support.StubPersonAttributeDao" 184 p:backingMap-ref="attrRepoBackingMap" /> 185 186 <util:map id="attrRepoBackingMap"> 187 <entry key="uid" value="uid" /> 188 <entry key="eduPersonAffiliation" value="eduPersonAffiliation" /> 189 <entry key="groupMembership" value="groupMembership" /> 190 </util:map> 191 --> 192 <!-- 此处为增加部分 start --> 193 <bean id="attributeRepository" class="org.jasig.services.persondir.support.jdbc.SingleRowJdbcPersonAttributeDao" > 194 <constructor-arg index="0" ref="dataSource"/> 195 <constructor-arg index="1" value="SELECT * FROM ssoaccount WHERE {0}"/> 196 <property name="queryAttributeMapping"> 197 <map> 198 <!-- key对应登录信息, vlaue对应数据库字段 --> 199 <entry key="username" value="LoginAccount"/> 200 </map> 201 </property> 202 <property name="resultAttributeMapping"> 203 <map> 204 <!-- key对应数据库字段 value对应attribute中的key --> 205 <entry key="Sex" value="Sex"/> 206 <entry key="Address" value="Address"/> 207 </map> 208 </property> 209 </bean> 210 <!-- 此处为增加部分 end --> 211 <!-- 212 Sample, in-memory data store for the ServiceRegistry. A real implementation 213 would probably want to replace this with the JPA-backed ServiceRegistry DAO 214 The name of this bean should remain "serviceRegistryDao". 215 +--> 216 <bean id="serviceRegistryDao" class="org.jasig.cas.services.InMemoryServiceRegistryDaoImpl" 217 p:registeredServices-ref="registeredServicesList" /> 218 219 <util:list id="registeredServicesList"> 220 <bean class="org.jasig.cas.services.RegexRegisteredService" 221 p:id="0" p:name="HTTP and IMAP" p:description="Allows HTTP(S) and IMAP(S) protocols" 222 p:serviceId="^(https?|imaps?)://.*" p:evaluationOrder="10000001" /> 223 <!-- 224 Use the following definition instead of the above to further restrict access 225 to services within your domain (including sub domains). 226 Note that example.com must be replaced with the domain you wish to permit. 227 This example also demonstrates the configuration of an attribute filter 228 that only allows for attributes whose length is 3. 229 --> 230 <!-- 231 <bean class="org.jasig.cas.services.RegexRegisteredService"> 232 <property name="id" value="1" /> 233 <property name="name" value="HTTP and IMAP on example.com" /> 234 <property name="description" value="Allows HTTP(S) and IMAP(S) protocols on example.com" /> 235 <property name="serviceId" value="^(https?|imaps?)://([A-Za-z0-9_-]+\.)*example\.com/.*" /> 236 <property name="evaluationOrder" value="0" /> 237 <property name="attributeFilter"> 238 <bean class="org.jasig.cas.services.support.RegisteredServiceRegexAttributeFilter" c:regex="^\w{3}$" /> 239 </property> 240 </bean> 241 --> 242 </util:list> 243 244 <bean id="auditTrailManager" class="com.github.inspektr.audit.support.Slf4jLoggingAuditTrailManager" /> 245 246 <bean id="healthCheckMonitor" class="org.jasig.cas.monitor.HealthCheckMonitor" p:monitors-ref="monitorsList" /> 247 248 <util:list id="monitorsList"> 249 <bean class="org.jasig.cas.monitor.MemoryMonitor" p:freeMemoryWarnThreshold="10" /> 250 <!-- 251 NOTE 252 The following ticket registries support SessionMonitor: 253 * DefaultTicketRegistry 254 * JpaTicketRegistry 255 Remove this monitor if you use an unsupported registry. 256 --> 257 <bean class="org.jasig.cas.monitor.SessionMonitor" 258 p:ticketRegistry-ref="ticketRegistry" 259 p:serviceTicketCountWarnThreshold="5000" 260 p:sessionCountWarnThreshold="100000" /> 261 </util:list> 262 </beans>
但是配置好后,编译出现了问题,Error creating bean with name 'centralAuthenticationService' defined in .
这个问题是因为少了cas中jdbc的源码,将上述mvn eclipse:eclipse编译好的cas-server-support-jdbc项目导入Myeclipse中,并将项目中的代码按现有目录拷贝到Web项目中,

现项目图片
最后编译项目,打开项目地址,并输入数据库中的账号与密码,即可变废为宝了。
再次就是其他4个jar的代码,你可以通过拷贝的方式考入当前项目中。
问题1:
Failed to execute goal org.apache.maven.plugins:maven-checkstyle-plugin
该问题是因为你想在源码的根目录直接运行编译命令 C:\Users\Jadyer\Desktop\cas-4.0.5>mvn install -DskipTests 但最终没发现\cas-4.0.5\cas-server-webapp\target\目录下生成cas.war 文件
其实,是需要在 C:\Users\Jadyer\Desktop\cas-4.0.5\cas-server-webapp>目录下执行该命令,才会生成war文件。如图:
 、
、
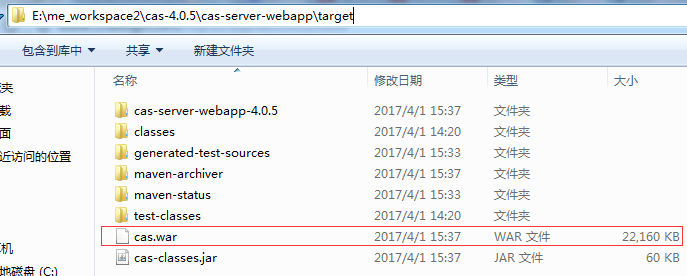
最后编译了30分钟

最终是生成了一大堆文件
查阅资料
http://blog.csdn.net/jadyer/article/details/46875393
http://blog.csdn.net/yanjunlu/article/details/45498509
http://blog.csdn.net/shadowsick/article/details/42191273
http://blog.csdn.net/small_love/article/details/6664831





