Ripple20漏洞
关于Ripple20
国外安全研究人员在由Treck开发的TCP/IP协议栈中发现了多个漏洞,这一系列漏洞统称为Ripple20。这些漏洞广泛存在于嵌入式和物联网设备中,影响了多个行业领域(包括医疗、运输、能源、电信、工业控制、零售和商业等),涉及了众多供应商(包括HP、Schneider Electric、Intel、Rockwell Automation、Caterpillar、Baxter等)。
CVE-2020-11896:可对支持IPv4隧道的设备进行远程代码执行攻击;
CVE-2020-11897:可对支持IPv6协议的设备进行远程代码执行攻击;
CVE-2020-11901:可对支持DNS协议的设备进行远程代码执行攻击;
CVE-2020-11898:IPv4/ICMPv4协议组件可能存在信息泄露漏洞;
CVE-2020-11900:IPv4隧道组件可能存在内存释放后重用漏洞;
CVE-2020-11902:IPv6OverIPv4隧道组件可能存在越界读取漏洞;
影响
Treck协议栈检测
Treck协议栈自定义了类型为165(0xa5)的ICMP包,并一旦收到165的ICMP包会回复类型为166的ICMP包响应。
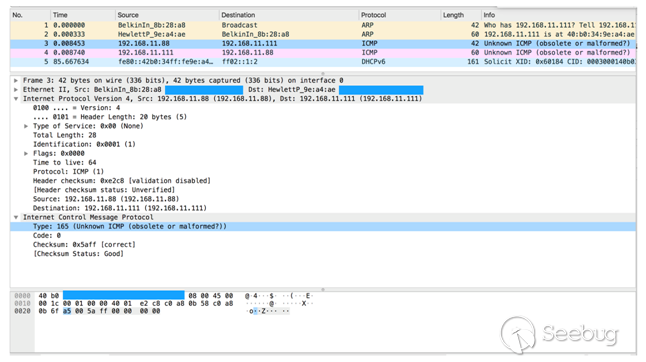
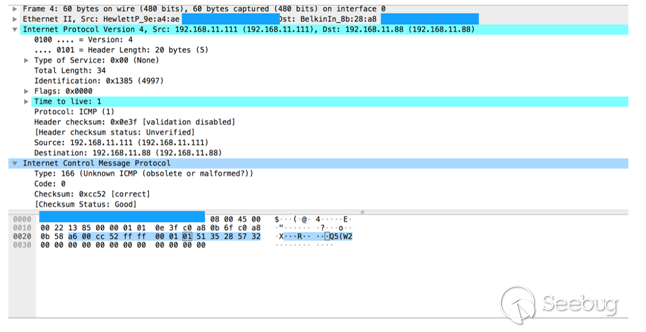
然后,接收目标返回的icmp响应包数据,其中type =0xa6,code =0,ICMP报文第9字节后的六个字节为0x01,0x51,0x35,0x28,0x57,0x32(大端)或0x51,0x01,0x28,0x35,0x32,0x57(小端)。 满足上述的条件,则表明目标设备为treck 协议栈。如下图所示:
使用python模拟发ICMP包
from scapy.all import *
target = "192.168.1.1"
ip = IP()
icmp = ICMP()
ip.dst = target
icmp.type = 0xa5
icmp.code = 0
send(ip/icmp)
抓包确实可以看到流量 测了一下发现工位旁边的HP打印机使用了Treck TCP/IP
检测规则
绿盟
https://github.com/CERTCC/PoC-Exploits/blob/master/vu-257161/vu-257161.rules
# Possible remote code execution, or DoS using IP-in-IP tunneled fragmented packets
alert ip any any -> any any (msg:"VU#257161:CVE-2020-11896,CVE-2020-11898 Fragments inside IP-in-IP tunnel https://kb.cert.org"; ip_proto:4; fragbits:M; sid:1367257161; rev:1;)
# Type 0 Routing header deprecated per RFC 5095
alert ipv6 any any -> any any (msg:"VU#257161:CVE‑2020‑11897 IPv6 deprecated RH Type 0 source routing attack"; decode-event:ipv6.rh_type_0;sid:1368257161; rev:1;)
# IPv6 multicast destination
alert ipv6 any any -> ff00::/8 any (msg:"VU#257161:CVE‑2020‑11899 Multicast out-of-bound read";sid:1369257161; rev:1;)
#IP-in-IP packet tunneling
alert ip any any -> any any (msg:"VU#257161:CVE-2020-11900 IP-in-IP tunnel Double-Free https://kb.cert.org"; ip_proto:4; sid:1370257161; rev:1;)
#Malformed DNS with large payload
alert dns any any -> any any (msg:"VU#257161:CVE-2020-11901 DNS malformed response to provide incorrect size for heap allocation error"; dsize:>128 ; app-layer-event:dns.malformed_data; sid:1371257161; rev:1;)
#uses ICMPv4 to report a parameter problem in a crafted packet X (IPv4 + ICMPv4 type=param‑problem + X),
alert icmp any any -> any any (msg:"VU#257161:CVE-2020-11902 ICMPv4 parameter problem with tunnel inside"; itype:12; sid:1372257161; rev:1;)
alert icmp any any -> any any (msg:"VU#257161:CVE-2020-CVE‑2020‑11910 anomalous ICMPv4 type 3,code 4 Path MTU Discovery"; itype:3; icode:4; sid:1373257161; rev:1;)
alert icmp any any -> any any (msg:"VU#257161:CVE-2020-CVE‑2020‑1191 anomalous ICMPv4 Address Mask Reply message (type 18, code 0)"; itype:18; icode:0; sid:1374257161; rev:1;)


