lvs持久连接及防火墙标记实现多端口绑定服务
lvs持久连接及防火墙标记实现多端口绑定服务
PPC:将来自于一个客户端发往某VIP的某端口的所有请求统统定向至同一个RS;
PFMC: 端口绑定,port affinity
基于防火墙标记,将两个或以上的端口绑定为同一个服务

普通的非持久连接配置:
# ipvsadm -A -t 192.168.8.40:80 -s rr
# ipvsadm -a -t 192.168.8.40:80 -r 192.168.8.101 -g
# ipvsadm -a -t 192.168.8.40:80 -r 192.168.8.102 -g
持久连接配置:
添加一个访问80端口的持久连接,发现此时同一个IP访问80端口,都转发给同一个RS响应,同理22号端口的ssh服务也可以类似配置
# ipvsadm -A -t 192.168.8.40:80 -s rr -p 600
# ipvsadm -a -t 192.168.8.40:80 -r 192.168.8.101 -g
# ipvsadm -a -t 192.168.8.40:80 -r 192.168.8.102 -g
# ipvsadm -L -n
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.8.40:80 rr persistent 600
-> 192.168.8.101:80 Route 1 0 0
-> 192.168.8.102:80 Route 1 0 0
清空此前的配置
# ipvsadm -C
在600秒以内,来自同一个客户端的请求都转发到同一个RS(192.168.8.40:0 表示任意端口)
# ipvsadm -A -t 192.168.8.40:0 -s rr -p 600
# ipvsadm -a -t 192.168.8.40:0 -r 192.168.8.101 -g
# ipvsadm -a -t 192.168.8.40:0 -r 192.168.8.102 -g
# ipvsadm -L -n
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.8.40:0 rr persistent 600
-> 192.168.8.101:0 Route 1 0 0
-> 192.168.8.102:0 Route 1 0 0
此时可以观察到,通过同一台客户端不管是访问ssh还是web服务都指向了同一个RS的IP
DR做CA服务器
在rs上安装ssl服务(通过yum默认安装的配置方法)
# yum install -y mod_ssl
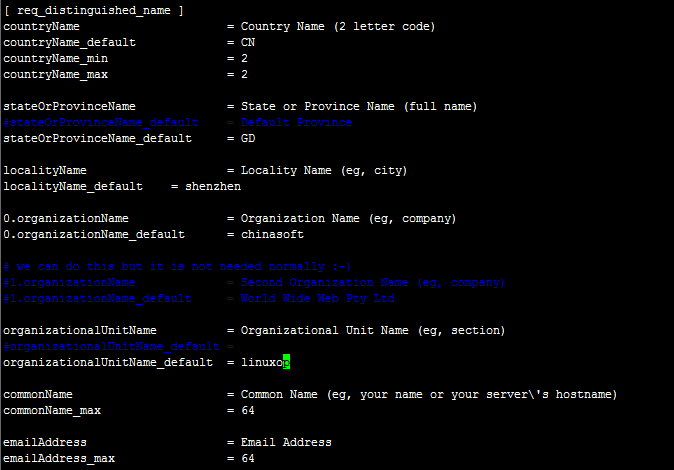
# vim ../tls/openssl.cnf
countryName_default = CN
stateOrProvinceName_default = GD
localityName_default = shenzhen
0.organizationName_default = chinasoft
organizationalUnitName_default = linuxop
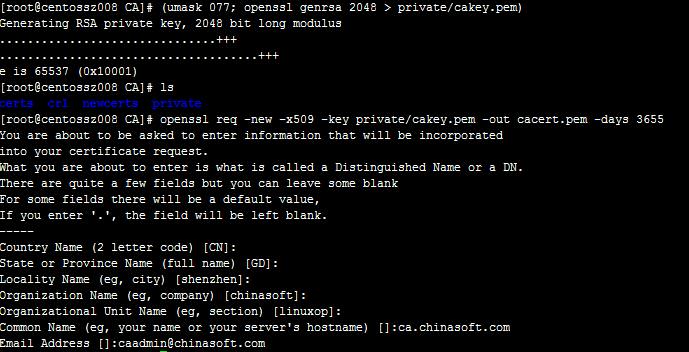
# (umask 077; openssl genrsa 2048 > private/cakey.pem)
# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3655
# touch index.txt serial crlnumber
# echo 01 > serial
# cd /etc/httpd
# mkdir ssl
# cd ssl
# (umask 077; openssl genrsa 1024 > httpd.key)
# openssl req -new -key httpd.key -out httpd.csr
# scp httpd.csr 192.168.8.100:/tmp
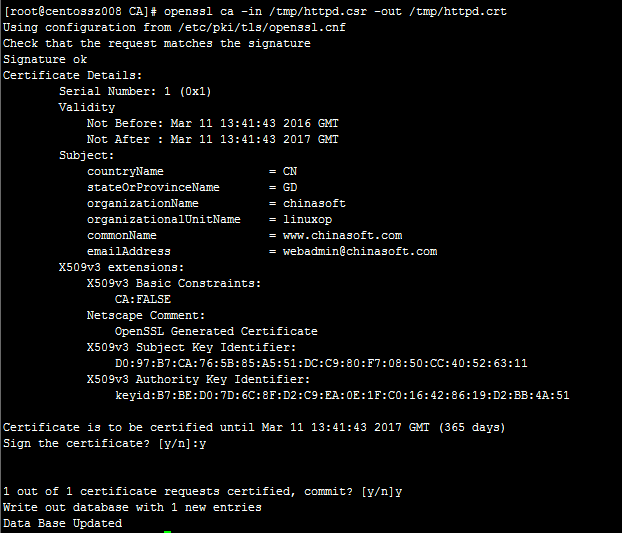
# openssl ca -in /tmp/httpd.csr -out /tmp/httpd.crt
# scp /tmp/httpd.crt 192.168.8.101:/etc/httpd/ssl
回到rs1 192.168.8.101
在rs2 192.168.8.102上创建目录 # mkdir /etc/httpd/ssl
将生成的证书和key拷贝到8.102上
# scp httpd.crt httpd.key 172.16.100.12:/etc/httpd/ssl/
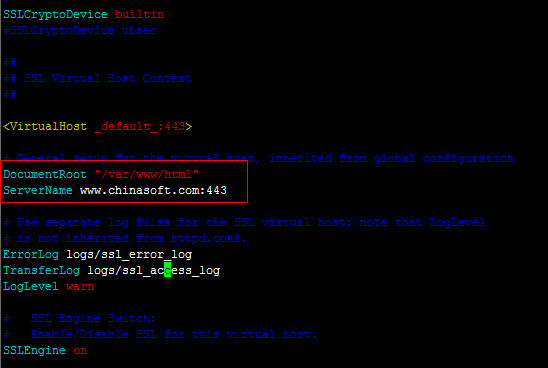
# vim /etc/httpd/conf.d/ssl.conf
DocumentRoot "/var/www/html"
ServerName www.chinasoft.com:443
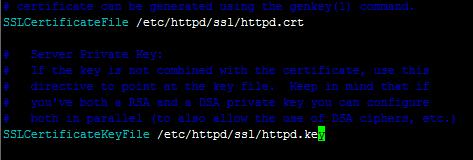
SSLCertificateFile /etc/httpd/ssl/httpd.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
# scp conf.d/ssl.conf 192.168.8.102:/etc/httpd/conf.d/
/configure --prefix=/usr/local/apache --sysconfdir=/etc/httpd24 --enable-so --enable--ssl --enable-cgi --enable-rewrite --with-zlib --with-pcre --with-apr=/usr/local/apr --with-apr-util=/usr/local/apr-util --enable-modeles=most --enable-mpms-shared=all --with-mpm=event
可以看到--enable--ssl 这个选项,说明是安装了ssl模块的,需要手动开启该配置
①加载ssl模块
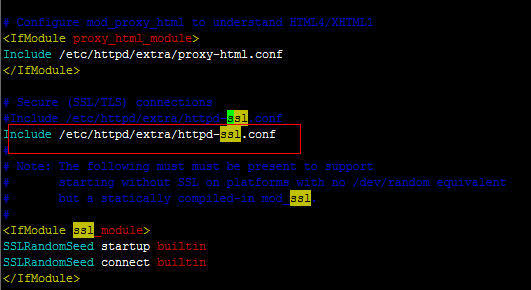
# vim /etc/httpd/httpd.conf
LoadModule ssl_module modules/mod_ssl.so
Include /etc/httpd/extra/httpd-ssl.conf
②配置httpd的key及认证文件目录
vim /etc/httpd/extra/httpd0ssl.conf
SSLCertificateFile "/etc/httpd/ssl/httpd.crt"
SSLCertificateKeyFile "/etc/httpd/ssl/httpd.key"
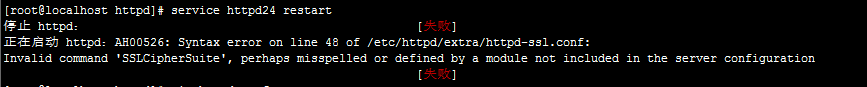
重启httpd服务,报错
停止 httpd: [失败]
正在启动 httpd:AH00526: Syntax error on line 48 of /etc/httpd/extra/httpd-ssl.conf:
Invalid command 'SSLCipherSuite', perhaps misspelled or defined by a module not included in the server configuration
需要加载mod_socache_shmcb模块
vim /etc/httpd/httpd.conf
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so
通过访问各自服务器的https可以看到已经生效
# ipvsadm -A -t 192.168.8.40:443 -s rr
# ipvsadm -a -t 192.168.8.40:443 -r 192.168.8.101 -g
# ipvsadm -a -t 192.168.8.40:443 -r 192.168.8.102 -g
# ipvsadm -L -n
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.8.40:443 rr
-> 192.168.8.101:443 Route 1 0 12
-> 192.168.8.102:443 Route 1 0 6
基于防火墙标记实现多端口绑定http和https服务,同时也做到了负载均衡
# iptables -t mangle -A PREROUTING -d 192.168.8.40 -p tcp --dport 80 -j MARK --set-mark 10
# iptables -t mangle -A PREROUTING -d 192.168.8.40 -p tcp --dport 443 -j MARK --set-mark 10
# service iptables save
# ipvsadm -A -f 10 -s rr
# ipvsadm -a -f 10 -r 192.168.8.101 -g
LVS持久连接:
PCC:将来自于同一个客户端发往VIP的所有请求统统定向至同一个RS;PPC:将来自于一个客户端发往某VIP的某端口的所有请求统统定向至同一个RS;
PFMC: 端口绑定,port affinity
基于防火墙标记,将两个或以上的端口绑定为同一个服务
一、安装ipvs环境
具体请参考博文 LVS负载均衡器DR模型的实现(http://blog.csdn.net/reblue520/article/details/50857078)
普通的非持久连接配置:
# ipvsadm -A -t 192.168.8.40:80 -s rr
# ipvsadm -a -t 192.168.8.40:80 -r 192.168.8.101 -g
# ipvsadm -a -t 192.168.8.40:80 -r 192.168.8.102 -g
持久连接配置:
添加一个访问80端口的持久连接,发现此时同一个IP访问80端口,都转发给同一个RS响应,同理22号端口的ssh服务也可以类似配置
# ipvsadm -A -t 192.168.8.40:80 -s rr -p 600
# ipvsadm -a -t 192.168.8.40:80 -r 192.168.8.101 -g
# ipvsadm -a -t 192.168.8.40:80 -r 192.168.8.102 -g
# ipvsadm -L -n
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.8.40:80 rr persistent 600
-> 192.168.8.101:80 Route 1 0 0
-> 192.168.8.102:80 Route 1 0 0
清空此前的配置
# ipvsadm -C
在600秒以内,来自同一个客户端的请求都转发到同一个RS(192.168.8.40:0 表示任意端口)
# ipvsadm -A -t 192.168.8.40:0 -s rr -p 600
# ipvsadm -a -t 192.168.8.40:0 -r 192.168.8.101 -g
# ipvsadm -a -t 192.168.8.40:0 -r 192.168.8.102 -g
# ipvsadm -L -n
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.8.40:0 rr persistent 600
-> 192.168.8.101:0 Route 1 0 0
-> 192.168.8.102:0 Route 1 0 0
此时可以观察到,通过同一台客户端不管是访问ssh还是web服务都指向了同一个RS的IP
二、安装httpd服务
apache服务可以通过手动编译安装也可以通过yum自动安装,安装过程略1.配置https服务
DR做CA服务器
在rs上安装ssl服务(通过yum默认安装的配置方法)
# yum install -y mod_ssl
2.DR 192.168.8.100配置
# cd /etc/pki/CA# vim ../tls/openssl.cnf
countryName_default = CN
stateOrProvinceName_default = GD
localityName_default = shenzhen
0.organizationName_default = chinasoft
organizationalUnitName_default = linuxop
# (umask 077; openssl genrsa 2048 > private/cakey.pem)
# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 3655
# touch index.txt serial crlnumber
# echo 01 > serial
3.RS上的操作
# cd /etc/httpd
# mkdir ssl
# cd ssl
# (umask 077; openssl genrsa 1024 > httpd.key)
# openssl req -new -key httpd.key -out httpd.csr
# scp httpd.csr 192.168.8.100:/tmp
4.DR 192.168.8.100配置
# openssl ca -in /tmp/httpd.csr -out /tmp/httpd.crt
# scp /tmp/httpd.crt 192.168.8.101:/etc/httpd/ssl
回到rs1 192.168.8.101
在rs2 192.168.8.102上创建目录 # mkdir /etc/httpd/ssl
将生成的证书和key拷贝到8.102上
# scp httpd.crt httpd.key 172.16.100.12:/etc/httpd/ssl/
# vim /etc/httpd/conf.d/ssl.conf
DocumentRoot "/var/www/html"
ServerName www.chinasoft.com:443
SSLCertificateFile /etc/httpd/ssl/httpd.crt
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key
# scp conf.d/ssl.conf 192.168.8.102:/etc/httpd/conf.d/
5.192.168.8.101 因为是自己编译安装的apache服务,需要单独配置
编译安装时的配置参数/configure --prefix=/usr/local/apache --sysconfdir=/etc/httpd24 --enable-so --enable--ssl --enable-cgi --enable-rewrite --with-zlib --with-pcre --with-apr=/usr/local/apr --with-apr-util=/usr/local/apr-util --enable-modeles=most --enable-mpms-shared=all --with-mpm=event
可以看到--enable--ssl 这个选项,说明是安装了ssl模块的,需要手动开启该配置
①加载ssl模块
# vim /etc/httpd/httpd.conf
LoadModule ssl_module modules/mod_ssl.so
Include /etc/httpd/extra/httpd-ssl.conf
②配置httpd的key及认证文件目录
vim /etc/httpd/extra/httpd0ssl.conf
SSLCertificateFile "/etc/httpd/ssl/httpd.crt"
SSLCertificateKeyFile "/etc/httpd/ssl/httpd.key"
重启httpd服务,报错
停止 httpd: [失败]
正在启动 httpd:AH00526: Syntax error on line 48 of /etc/httpd/extra/httpd-ssl.conf:
Invalid command 'SSLCipherSuite', perhaps misspelled or defined by a module not included in the server configuration
需要加载mod_socache_shmcb模块
vim /etc/httpd/httpd.conf
LoadModule socache_shmcb_module modules/mod_socache_shmcb.so
通过访问各自服务器的https可以看到已经生效
三、配置基于https服务的持久连接
# ipvsadm -A -t 192.168.8.40:443 -s rr
# ipvsadm -a -t 192.168.8.40:443 -r 192.168.8.101 -g
# ipvsadm -a -t 192.168.8.40:443 -r 192.168.8.102 -g
# ipvsadm -L -n
IP Virtual Server version 1.2.1 (size=4096)
Prot LocalAddress:Port Scheduler Flags
-> RemoteAddress:Port Forward Weight ActiveConn InActConn
TCP 192.168.8.40:443 rr
-> 192.168.8.101:443 Route 1 0 12
-> 192.168.8.102:443 Route 1 0 6
基于防火墙标记实现多端口绑定http和https服务,同时也做到了负载均衡
# iptables -t mangle -A PREROUTING -d 192.168.8.40 -p tcp --dport 80 -j MARK --set-mark 10
# iptables -t mangle -A PREROUTING -d 192.168.8.40 -p tcp --dport 443 -j MARK --set-mark 10
# service iptables save
# ipvsadm -A -f 10 -s rr
# ipvsadm -a -f 10 -r 192.168.8.101 -g
# ipvsadm -a -f 10 -r 192.168.8.102 -g




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律