zabbix使用自动发现功能批量监控服务器端口的可用性
使用自动发现脚本批量监控服务器端口的可用性 1.编写自动发现脚本 # cat /usr/local/zabbix_agents_3.2.0/scripts/web_site_code_status.sh #!/bin/bash UrlFile="/usr/local/zabbix_agents_3.2.0/scripts/WEB.txt" IFS=$'\n' web_site_discovery () { WEB_SITE=($(cat $UrlFile|grep -v "^#")) printf '{\n' printf '\t"data":[\n' num=${#WEB_SITE[@]} for site in ${WEB_SITE[@]} do num=$(( $num - 1 )) url=$(echo $site|awk '{print $1}') ip=$(echo $site|awk '{print $2}') if [ $num -ne 0 ] ; then printf "\t\t{\"{#SITENAME}\":\""%s"\",\"{#PROXYIP}\":\""${ip}"\"},\n" ${url} else printf "\t\t{\"{#SITENAME}\":\""%s"\",\"{#PROXYIP}\":\""${ip}"\"}\n" ${url} printf '\t]\n' printf '}\n' fi done } web_site_code () { /usr/bin/nmap $1 -p 873 2>/dev/null | grep -c open } case "$1" in web_site_discovery) web_site_discovery ;; web_site_code) web_site_code $2 ;; *) echo "Usage:$0 {web_site_discovery|web_site_code [URL]}" ;; esac 2.需要监控的服务器列表 [root@cbs_logs_master:/usr/local/zabbix_agents_3.2.0/scripts]# cat WEB.txt ws_cbs_frontend_web01 1.1.1.1 ws_cbs_frontend_web02 1.1.1.2 # 监控选项 [root@cbs_logs_master:/usr/local/zabbix_agents_3.2.0/conf/zabbix_agentd]# more web_site_discovery.conf UserParameter=web.site.discovery,/usr/local/zabbix_agents_3.2.0/scripts/web_site_code_status.sh web_site_discovery UserParameter=web.site.code[*],/usr/local/zabbix_agents_3.2.0/scripts/web_site_code_status.sh web_site_code $1 # 本机测试
# /usr/local/zabbix_agents_3.2.0/scripts/web_site_code_status.sh web_site_discovery
{
"data":[
{"{#SITENAME}":"ws_cbs_frontend_web01","{#PROXYIP}":"1.1.1.1"},
{"{#SITENAME}":"ws_cbs_frontend_web02","{#PROXYIP}":"1.1.1.2"}
]
}
[root@cbs_logs_master:/usr/local/zabbix_agents_3.2.0/conf/zabbix_agentd]# /usr/local/zabbix_agents_3.2.0/scripts/web_site_code_status.sh web_site_code 1.1.1.1 1 # zabbix服务端测试 # zabbix_get -s 192.168.11.42 -k 'web.site.code[1.1.1.1]' 1
监控模板

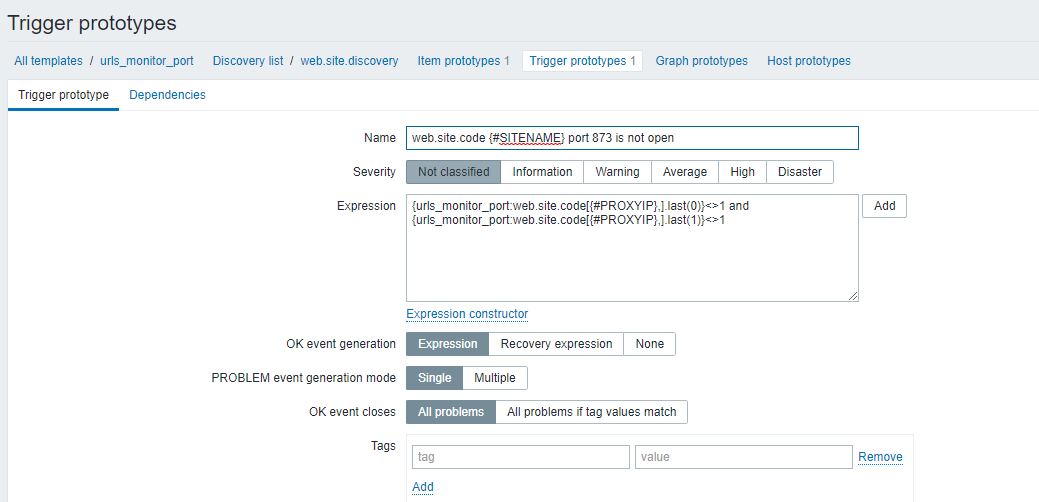
<?xml version="1.0" encoding="UTF-8"?> <zabbix_export> <version>3.4</version> <date>2019-11-08T12:33:05Z</date> <groups> <group> <name>Templates</name> </group> </groups> <templates> <template> <template>urls_monitor_port</template> <name>urls_monitor_port</name> <description/> <groups> <group> <name>Templates</name> </group> </groups> <applications/> <items/> <discovery_rules> <discovery_rule> <name>web.site.discovery</name> <type>0</type> <snmp_community/> <snmp_oid/> <key>web.site.discovery</key> <delay>180;180/1-7,00:00-24:00</delay> <status>0</status> <allowed_hosts/> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <params/> <ipmi_sensor/> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <filter> <evaltype>0</evaltype> <formula/> <conditions/> </filter> <lifetime>30d</lifetime> <description/> <item_prototypes> <item_prototype> <name>web.site.discovery</name> <type>0</type> <snmp_community/> <snmp_oid/> <key>web.site.code[{#PROXYIP},]</key> <delay>30</delay> <history>90d</history> <trends>365d</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <params/> <ipmi_sensor/> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications/> <valuemap/> <logtimefmt/> <preprocessing/> <jmx_endpoint/> <application_prototypes/> <master_item_prototype/> </item_prototype> </item_prototypes> <trigger_prototypes> <trigger_prototype> <expression>{urls_monitor_port:web.site.code[{#PROXYIP},].last(0)}<>1 and {urls_monitor_port:web.site.code[{#PROXYIP},].last(1)}<>1</expression> <recovery_mode>0</recovery_mode> <recovery_expression/> <name>web.site.code {#SITENAME} port 873 is not open</name> <correlation_mode>0</correlation_mode> <correlation_tag/> <url/> <status>0</status> <priority>0</priority> <description/> <type>0</type> <manual_close>0</manual_close> <dependencies/> <tags/> </trigger_prototype> </trigger_prototypes> <graph_prototypes/> <host_prototypes/> <jmx_endpoint/> </discovery_rule> </discovery_rules> <httptests/> <macros/> <templates/> <screens/> </template> </templates> </zabbix_export>
同时监控多个端口的场景
需求:
客户端要访问mongodb获取数据,从mongodb内部监控这些端口不客观,直接在api服务器中判断端口的可用性更佳
需要监控的端口有:
20000
21000
27001
27002
27003
注意:
自动发现最终触发器中出现的参数必须在一个自动发现的过程中展示出来,否则不可用
如下示例中的 服务器名、服务器ip和服务器端口都同时定义在一个自动发现任务中
1.机器和端口列表
服务器名称(方便报警显示名称) 服务器ip 服务器端口
eus-image-design-mongo01 172.30.0.1 20000
# cat /usr/local/zabbix_agents/scripts/server_ips.txt
eus-image-design-mongo01 172.30.0.1 20000
eus-image-design-mongo01 172.30.0.1 21000
eus-image-design-mongo01 172.30.0.1 27001
eus-image-design-mongo01 172.30.0.1 27002
eus-image-design-mongo01 172.30.0.1 27003
eus-image-design-mongo02 172.30.0.18 20000
eus-image-design-mongo02 172.30.0.18 21000
eus-image-design-mongo02 172.30.0.18 27001
eus-image-design-mongo02 172.30.0.18 27002
eus-image-design-mongo02 172.30.0.18 27003
2.自动发现脚本
# cat /usr/local/zabbix_agents_3.2.0/scripts/server_code_status.sh
#!/bin/bash UrlFile="/usr/local/zabbix_agents_3.2.0/scripts/server_ips.txt" IFS=$'\n' server_ip_discovery () { WEB_SITE=($(cat $UrlFile|grep -v "^#")) printf '{\n' printf '\t"data":[\n' num=${#WEB_SITE[@]} for site in ${WEB_SITE[@]} do num=$(( $num - 1 )) url=$(echo $site|awk '{print $1}') ip=$(echo $site|awk '{print $2}') port=$(echo $site|awk '{print $3}') if [ $num -ne 0 ] ; then printf "\t\t{\"{#SITENAME}\":\""%s"\",\"{#PROXYIP}\":\""${ip}"\",\"{#SERVERPORT}\":\""${port}"\"},\n" ${url} else # 要特别注意json的格式定义 { } 括号要对应得上 printf "\t\t{\"{#SITENAME}\":\""%s"\",\"{#PROXYIP}\":\""${ip}"\",\"{#SERVERPORT}\":\""${port}"\"}\n" ${url} printf '\t]\n' printf '}\n' fi done } server_port_code () {
# 有时候 nmap会被主机阻止,此时可以使用nc命令进行替代
# /usr/bin/nc -zv $1 $2 2>/dev/null | grep -c "succeeded"
/usr/bin/nmap $1 -p $2 2>/dev/null | grep -c open
} case "$1" in server_ip_discovery) server_ip_discovery ;; server_port_discovery) server_port_discovery ;; server_port_code) server_port_code $2 $3 ;; *) echo "Usage:$0 {server_port_discovery|server_ip_discovery|server_port_code [URL]}" ;; esac
3.监控项定义
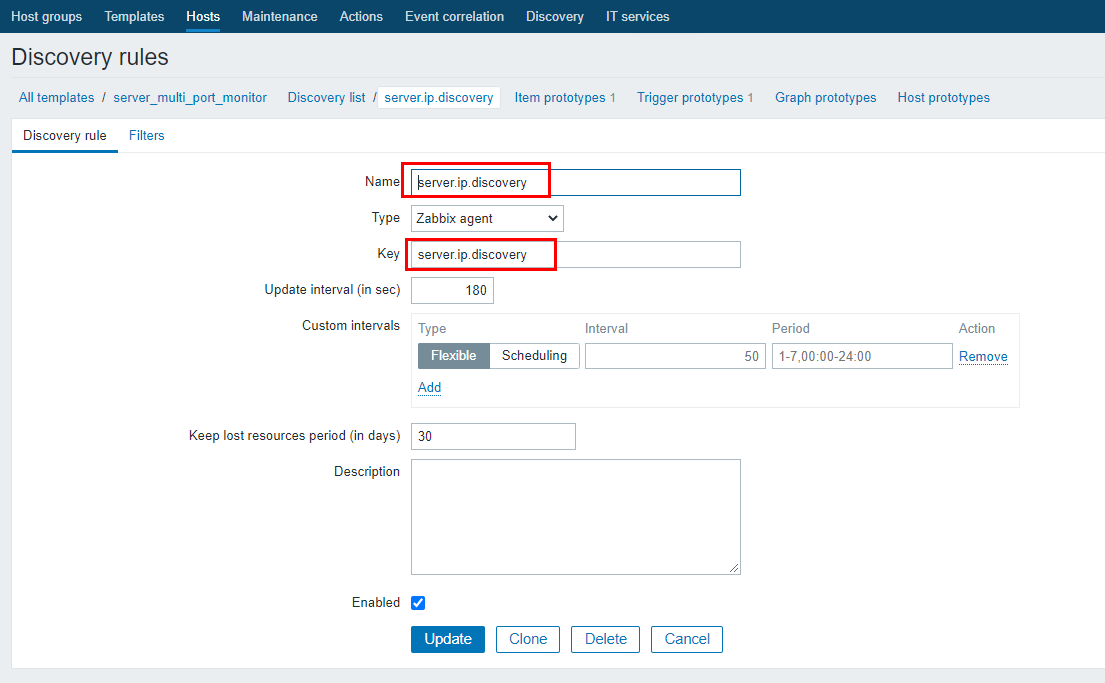
# vim /usr/local/zabbix_agents_3.2.0/conf/zabbix_agentd/server_site_discovery.conf
UserParameter=server.ip.discovery,/usr/local/zabbix_agents_3.2.0/scripts/server_code_status.sh server_ip_discovery
UserParameter=server.port.code[*],/usr/local/zabbix_agents_3.2.0/scripts/server_code_status.sh server_port_code $1 $2
4.本机测试
# /usr/local/zabbix_agents_3.2.0/scripts/server_code_status.sh server_ip_discovery
{
"data":[
{"{#SITENAME}":"eus-image-design-mongo01","{#PROXYIP}":"172.30.0.1","{#SERVERPORT}":"20000"},
{"{#SITENAME}":"eus-image-design-mongo01","{#PROXYIP}":"172.30.0.1","{#SERVERPORT}":"21000"},
{"{#SITENAME}":"eus-image-design-mongo01","{#PROXYIP}":"172.30.0.1","{#SERVERPORT}":"27001"},
{"{#SITENAME}":"eus-image-design-mongo01","{#PROXYIP}":"172.30.0.1","{#SERVERPORT}":"27002"},
{"{#SITENAME}":"eus-image-design-mongo01","{#PROXYIP}":"172.30.0.1","{#SERVERPORT}":"27003"},
{"{#SITENAME}":"eus-image-design-mongo02","{#PROXYIP}":"172.30.0.18","{#SERVERPORT}":"20000"},
{"{#SITENAME}":"eus-image-design-mongo02","{#PROXYIP}":"172.30.0.18","{#SERVERPORT}":"21000"},
{"{#SITENAME}":"eus-image-design-mongo02","{#PROXYIP}":"172.30.0.18","{#SERVERPORT}":"27001"},
{"{#SITENAME}":"eus-image-design-mongo02","{#PROXYIP}":"172.30.0.18","{#SERVERPORT}":"27002"},
{"{#SITENAME}":"eus-image-design-mongo02","{#PROXYIP}":"172.30.0.18","{#SERVERPORT}":"27003"},
]
}
# /usr/local/zabbix_agents_3.2.0/scripts/server_code_status.sh server_port_code 172.30.0.1 21000
1
zabbbix端的配置
key:
server.port.code[{#PROXYIP},{#SERVERPORT},]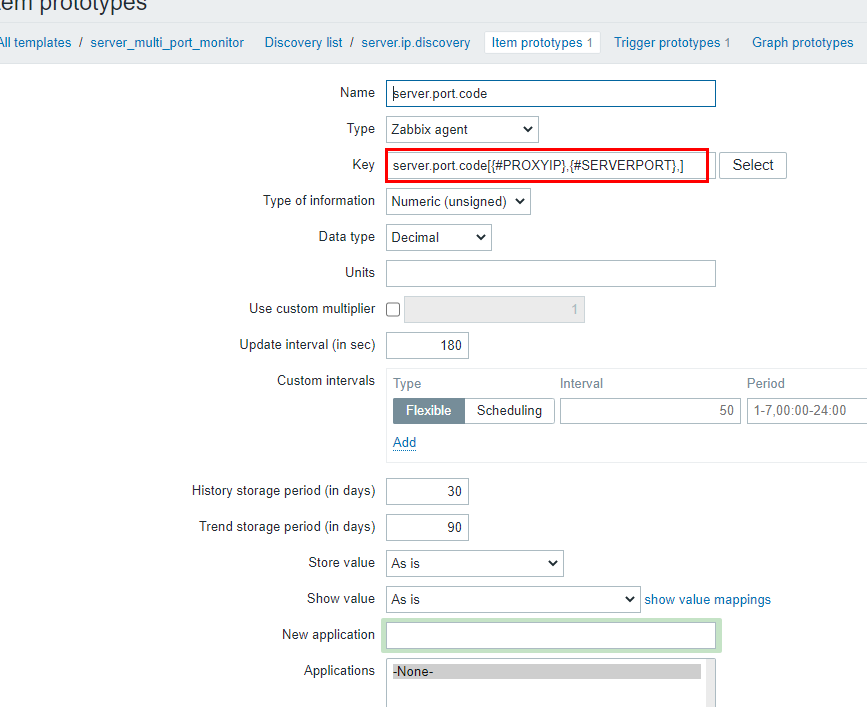
trigger:
name:
server.port.code {#SITENAME} port {#SERVERPORT}] was down
{server_multi_port_monitor:server.port.code[{#PROXYIP},{#SERVERPORT},].count(#3,1,"eq")}=0
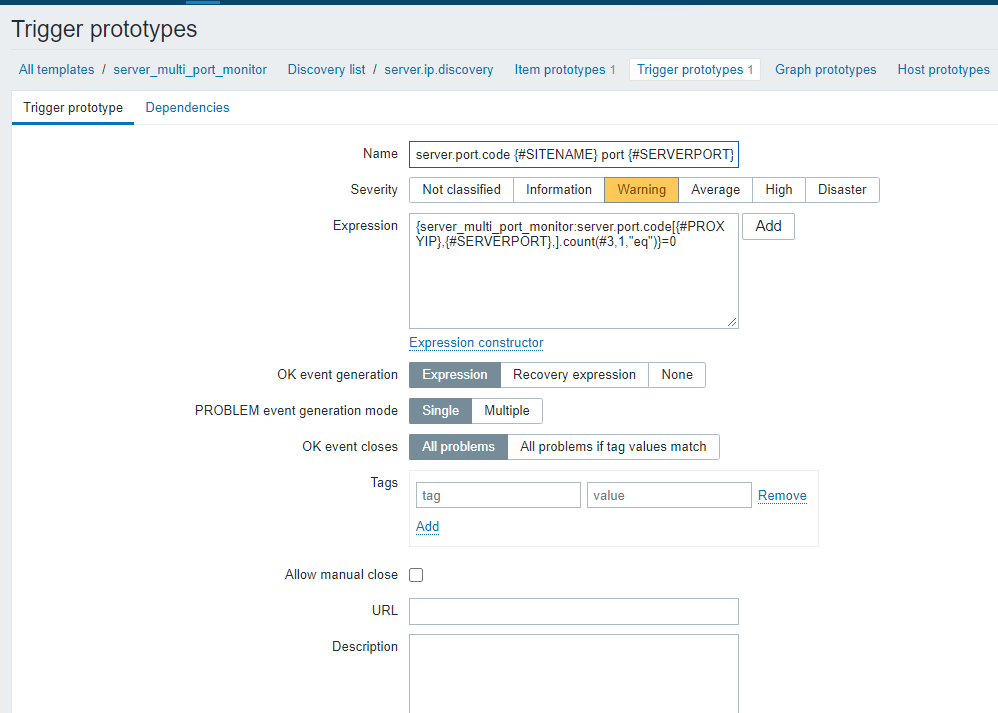
模板
<?xml version="1.0" encoding="UTF-8"?> <zabbix_export> <version>3.2</version> <date>2020-09-29T09:22:54Z</date> <groups> <group> <name>Templates_ALL_Group-[EUS]</name> </group> </groups> <templates> <template> <template>server_multi_port_monitor</template> <name>server_multi_port_monitor</name> <description/> <groups> <group> <name>Templates_ALL_Group-[EUS]</name> </group> </groups> <applications/> <items/> <discovery_rules> <discovery_rule> <name>server.ip.discovery</name> <type>0</type> <snmp_community/> <snmp_oid/> <key>server.ip.discovery</key> <delay>180</delay> <status>0</status> <allowed_hosts/> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <delay_flex/> <params/> <ipmi_sensor/> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <filter> <evaltype>0</evaltype> <formula/> <conditions/> </filter> <lifetime>30</lifetime> <description/> <item_prototypes> <item_prototype> <name>server.port.code</name> <type>0</type> <snmp_community/> <multiplier>0</multiplier> <snmp_oid/> <key>server.port.code[{#PROXYIP},{#SERVERPORT},]</key> <delay>180</delay> <history>30</history> <trends>90</trends> <status>0</status> <value_type>3</value_type> <allowed_hosts/> <units/> <delta>0</delta> <snmpv3_contextname/> <snmpv3_securityname/> <snmpv3_securitylevel>0</snmpv3_securitylevel> <snmpv3_authprotocol>0</snmpv3_authprotocol> <snmpv3_authpassphrase/> <snmpv3_privprotocol>0</snmpv3_privprotocol> <snmpv3_privpassphrase/> <formula>1</formula> <delay_flex/> <params/> <ipmi_sensor/> <data_type>0</data_type> <authtype>0</authtype> <username/> <password/> <publickey/> <privatekey/> <port/> <description/> <inventory_link>0</inventory_link> <applications/> <valuemap/> <logtimefmt/> <application_prototypes/> </item_prototype> </item_prototypes> <trigger_prototypes> <trigger_prototype> <expression>{server_multi_port_monitor:server.port.code[{#PROXYIP},{#SERVERPORT},].count(#5,1,"eq")}=0</expression> <recovery_mode>0</recovery_mode> <recovery_expression/> <name>server.port.code {#SITENAME} port {#SERVERPORT}] was down</name> <correlation_mode>0</correlation_mode> <correlation_tag/> <url/> <status>0</status> <priority>2</priority> <description/> <type>0</type> <manual_close>0</manual_close> <dependencies/> <tags/> </trigger_prototype> </trigger_prototypes> <graph_prototypes/> <host_prototypes/> </discovery_rule> </discovery_rules> <httptests/> <macros/> <templates/> <screens/> </template> </templates> </zabbix_export>





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· Linux系列:如何用heaptrack跟踪.NET程序的非托管内存泄露
· 开发者必知的日志记录最佳实践
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· 震惊!C++程序真的从main开始吗?99%的程序员都答错了
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 单元测试从入门到精通
· 上周热点回顾(3.3-3.9)
· winform 绘制太阳,地球,月球 运作规律