数字证书编码ASN.1
数字证书编码ASN.1
一、任务详情
- 参考附件中图书p223 中13.2的实验指导,完成DER编码
- 序列号=1174(0x0496),证书签发者 DN="CN=Virtual CA,C=CN",证书持有者DN="CN=你的名字拼音, OU=Person,C=CN",证书有效期=20200222000000-20220222000000。
- 用echo -n -e "编码" > 你的学号.der中,用OpenSSL asn1parse 分析编码的正确性
- 提交编码过程文档(推荐markdown格式)
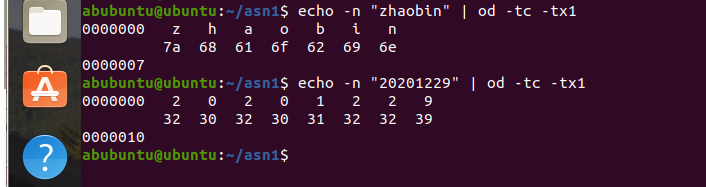
二、查看姓名、学号的16进制ASCLL码
echo -n "zhaobin" | od -tc -tx1
echo -n "20201229" | od -tc -tx1
三、ASN.1描述与实例
1.TBSCertificate 的 ASN.1描述与实例
TBSCertificate格式用ASN.1描述如下:
TBSCertificate :=SEQUENCE {
version
[0] EXPLICIT Version DEFAULT v1,
serialNumber
CertificateSerialNumber,
signature
Algorithmldentifier,
issuer
Name,
validity
Validity,
subject
Name,
subjectPublicKeyInfo SubjectPublicKeyInfo,
issuerUniqueID[1] IMPLICIT Uniqueldentifier OPTIONAL,
-- If present, version MUST be v2 or v3
subjectUniqueID [2] IMPLICIT Uniqueldentifier OPTIONAL,
-- If present, version MUST be v2 or v3
extensions[3]EXPLICIT Extensions OPTIONAL
-- If present, version MUST be v3
}
Extensions ::=SEQUENCE SIZE (1..MAX) OF ExtensionTBSCertificate 中各项内容具体值如下所示。
| TBSCertificate | 值 |
|---|---|
| version | 02 |
| serialNumber | 04 96 |
| signature | sha 1 WithRSAEncryption ( 1.2.840.113549.1.1.5) |
| issuer | “CN=Virtual CA,C=CN” |
| validity | notBefore=20200222000000、notAfter=20220222000000 |
| subject | “CN=chenshaoqing,OU=Person,C=CN” |
| subjectPublicKeyInfo | 空 |
| issuerUniquelD subjectUniquelD | 空 |
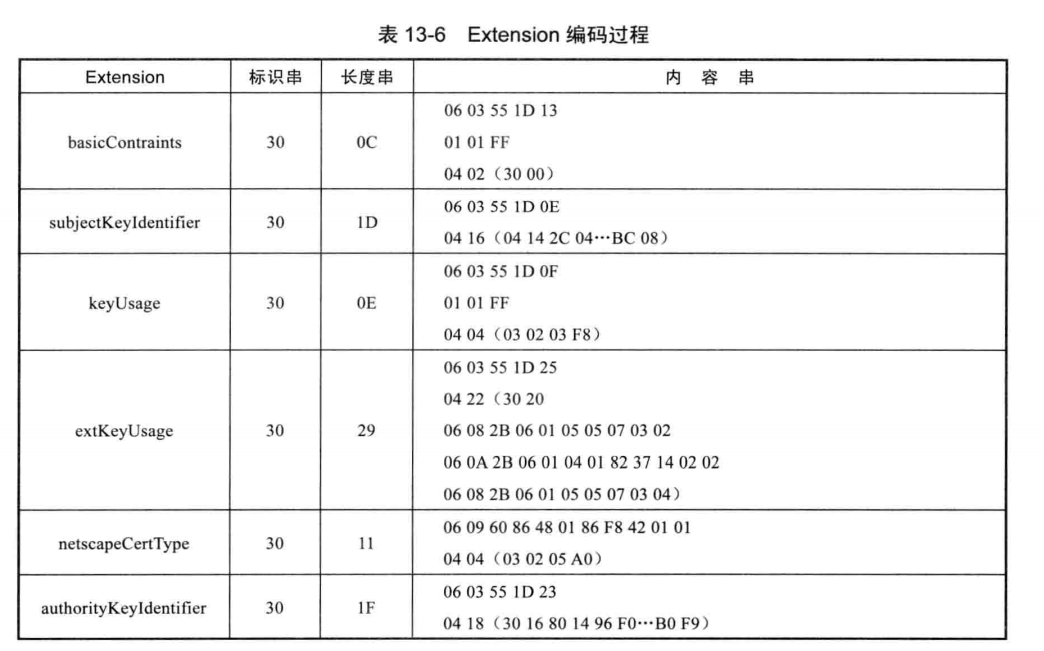
| extensions | 包含6个扩展项(Extension ): basicContraints、subjectKeyldentifier、keyUsage、extKeyUsage,netscapeCertType、authorityKeyIdentifier |
2.Extension的ASN.1描述与实例Extension格式用ASN.1描述如下:
Extension :=SEQUENCE {
extnID
OBJECT IDENTIFIER,
critical
BOOLEAN DEFAULT FALSE,
extnValue
OCTET STRING }
Extension各扩展项值如下所示。

3.Certificate 的ASN.1描述与实例Certificate格式用ASN.1描述如下:
Certificate ::=SEQUENCE {
tbsCertificate
TBSCertificate,
signatureAlgorithm
AlgorithmIdentifier,
signature Value
BIT STRING }
四、DER编码过程
(一)对Extension进行DER编码
各扩展项具体内容用ASN.1描述如下:
BasicConstraints ::=SEQUENCE{
cA
BOOLEAN DEFAULT FALSE,
pathLenConstraint
INTEGER (O..MAX)OPTIONAL}
SubjectKeyIdentifier ::= Keyldentifier
(KeyIdentifier ::= OCTET STRING)KeyUsage ::= BIT STRING
ExtKeyUsageSyntax ::= SEQUENCE SIZE (1..MAX)OF KeyPurposeld
(KeyPurposeld ::= OBJECT IDENTIFIER)NetscapeCertType ::= BIT STRING
AuthorityKeyldentifier ::=SEQUENCE{
keyIdentifier
[O] KeyIdentifier
OPTIONAL,
authorityCertIssuer
[1]GeneralNames
OPTIONAL,
authorityCertSerialNumber [2] CertificateSerialNumber OPTIONAL }(KeyIdentifier ::= OCTET STRING)
Extension为 SEQUENCE结构类型,不同扩展项DER编码值包含在OCTET STRING类型extnValue中,编码规则采用结构类型定长模式。各扩展项DER编码值用括号分隔。其中,对于BIT STRING类型,编码后第1个字节表示填充位数或未使用位数。
(二)对TBSCertificate进行DER编码
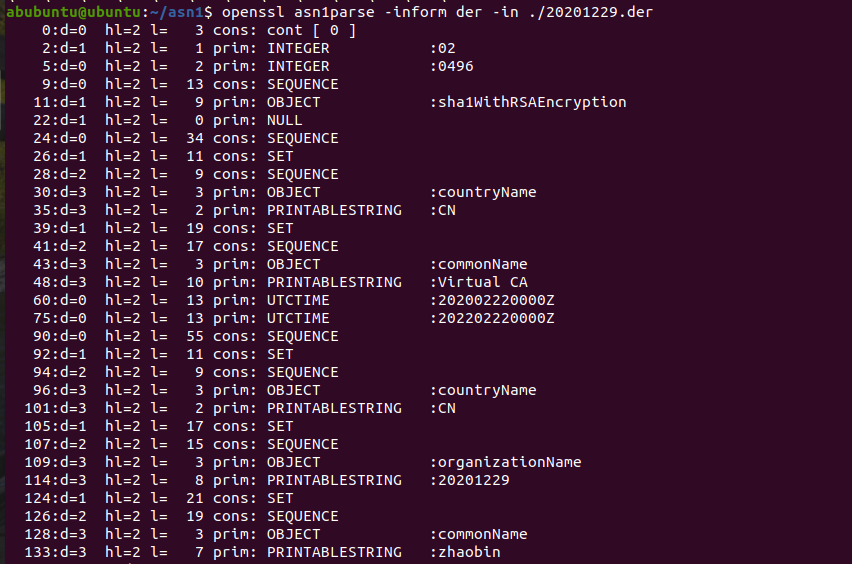
验证:openssl asn1parse -inform der -in ./20201229.der
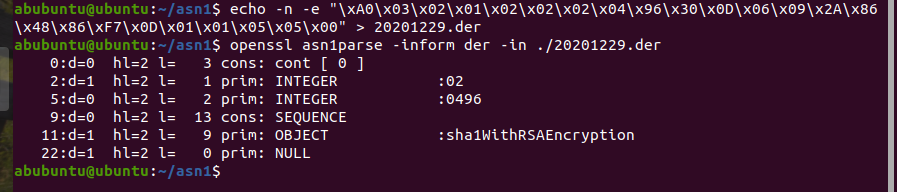
1.序列号1174(0x0496)
echo -n -e "\xA0\x03\x02\x01\x02\x02\x02\x04\x96\x30\x0D\x06\x09\x2A\x86\x48\x86\xF7\x0D\x01\x01\x05\x05\x00" > 20201229.der
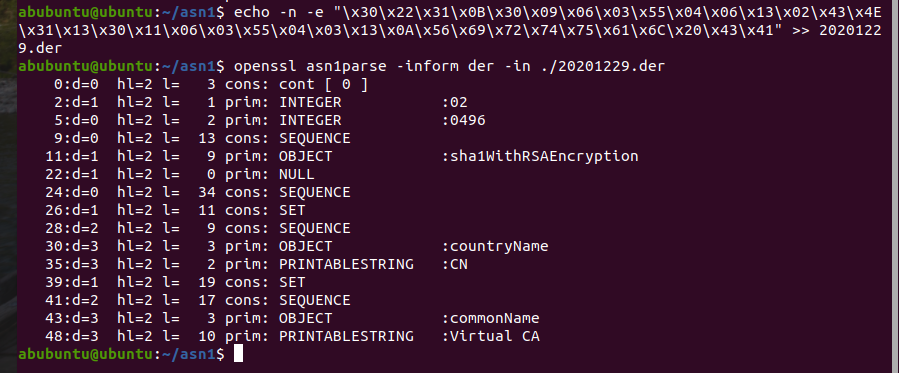
2.证书签发者DN="CN=Virtual CA
echo -n -e "\x30\x22\x31\x0B\x30\x09\x06\x03\x55\x04\x06\x13\x02\x43\x4E\x31\x13\x30\x11\x06\x03\x55\x04\x03\x13\x0A\x56\x69\x72\x74\x75\x61\x6C\x20\x43\x41" >> 20201229.der
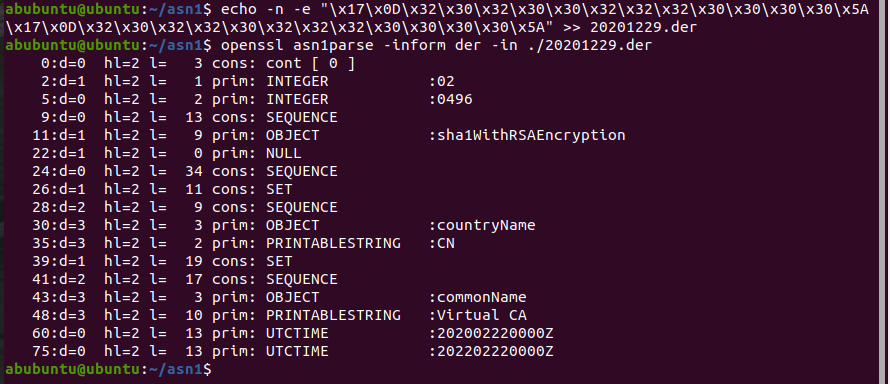
3.证书有效期=20200222000000-20220222000000
echo -n -e "\x17\x0D\x32\x30\x32\x30\x30\x32\x32\x32\x30\x30\x30\x30\x5A\x17\x0D\x32\x30\x32\x32\x30\x32\x32\x32\x30\x30\x30\x30\x5A" >> 20201229.der
4.证书持有者DN=CN=zhaobin, OU=Person
echo -n -e "\x30\x37\x31\x0B\x30\x09\x06\x03\x55\x04\x06\x13\x02\x43\x4E\x31\x11\x30\x0F\x06\x03\x55\x04\x0A\x13\x08\x32\x30\x32\x30\x31\x32\x32\x39\x31\x15\x30\x13\x06\x03\x55\x04\x03\x13\x07\x7a\x68\x61\x6f\x62\x69\x6e" >> 20201229.der