RawIP and Ethernet Encapsulation In Pcap
Why is there RAW_IP pcap? How to generate this pcap without Ethernet header?
One way to convert a RAW_IP file to an ethernet encapsulated file (which can then be merged with other ethernet-encapsulated files):
-
Use tshark to get a hex dump of the packets from the RAW_IP file:
tshark -nxr pcap-file-name | grep -vP "^ +\d" > foo.txt( grep is used to remove the "summary" lines from the tshark output).
-
Use text2pcap to convert back to a pcap file while adding dummy ethernet headers:
text2pacp -e 0x0800 foo.txt foo.pcap
If you want to keep the timestamps, you'll have to play around a bit with the tshark output to get a text file which contains the timestamps in a format which text2pcap will accept and also contains the hex packet info.
[[ Does tcpslice have an option to remove ethernet headers ? (Looking at the man page, it appears that tcpslice is used to extract time-ranges from a pcap file).
If you do have a way to remove ethernet headers from a capture file, you must make sure the resulting pcap file has an encapsulation type of RAW_IP before trying to read it with wireshark, mergecap , etc).
Also note that the -T switch to mergecap just forces the encapsulation type specified in the file; The actual encapsulation isn't altered (i.e., no bytes are added/changed/deleted). ]]
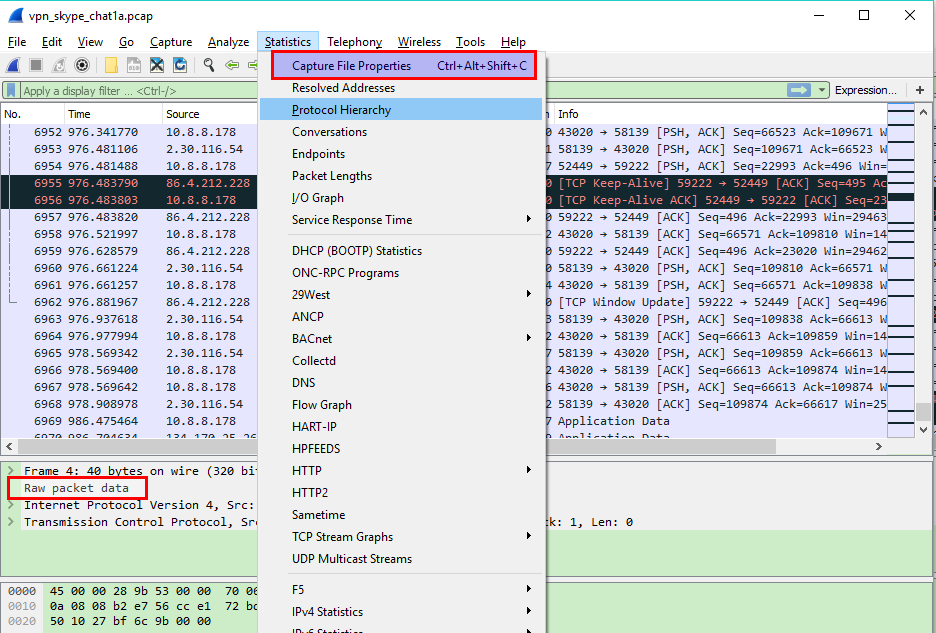
If Wireshark tries to decode L3 as L2 information, the encapsulation type of that file must be incorrect. You can verify the encapsulation type with capinfos (command line tool installed with Wireshark), or in Wireshark itself using the Statistics -> "Capture File Properties" menu option.
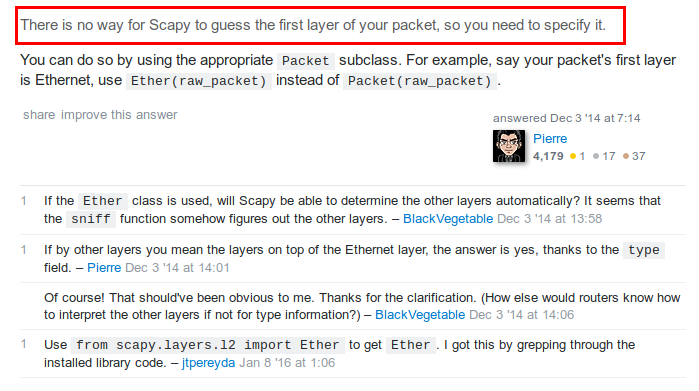
How to use Scapy to parse this pcap file without "Ethernet header"?
from scapy.layers.inet import IP from scapy.utils import PcapReader def pcap2_parser(input_f): try: # pkts_lst = rdpcap(input_f) # this will read all packets in memory at once, please don't use it directly. # input_f = '/home/kun/PycharmProjects/Pcap2Sessions_Scapy/1_pcaps_data/vpn_hangouts_audio2.pcap' # myreader = PcapReader(input_f) # iterator, please use it to process large file, such as more than 4 GB except MemoryError as me: print('memory error ', me) return -1 except FileNotFoundError as fnfe: print('file not found ', fnfe) return -2 except: print('other exceptions') return -10 # Step 2. achieve all the session in pcap. # data.stats pkts_stats = {'non_Ether_IPv4_pkts': 0, 'non_IPv4_pkts': 0, 'non_TCP_UDP_pkts': 0, 'TCP_pkts': 0, 'UDP_pkts': 0} cnt = 0 sess_dict = {} first_print_flg = True while True: pkt = myreader.read_packet() if pkt is None: break # step 1. parse "Ethernet" firstly if pkt.name == "Ethernet": if first_print_flg: first_print_flg = False print('\'%s\' encapsulated by "Ethernet Header" directly' % input_f) if pkt.payload.name.upper() in ['IP', 'IPV4']: if pkt.payload.payload.name.upper() in ["TCP", "UDP"]: if cnt == 0: print('packet[0] info: "%s:%d-%s:%d-%s"+%s' % ( pkt.payload.src, pkt.payload.payload.sport, pkt.payload.dst, pkt.payload.payload.dport, pkt.payload.payload.name, pkt.payload.payload.payload)) ### ... if pkt.payload.payload.name.upper() == "TCP": pkts_stats['TCP_pkts'] += 1 else: pkts_stats['UDP_pkts'] += 1 else: pkts_stats['non_TCP_UDP_pkts'] += 1 # pkts_stats['IPv4_pkts'] += 1 else: pkts_stats['non_IPv4_pkts'] += 1 else: # step 2. if this pkt can not be recognized as "Ethernet", then try to parse it as (IP,IPv4) pkt = IP(pkt) # without ethernet header, then try to parse it as (IP,IPv4) if first_print_flg: first_print_flg = False print('\'%s\' encapsulated by "IP Header" directly, without "Ethernet Header" ' % input_f) if pkt.name.upper() in ['IP', 'IPV4']: if pkt.payload.name.upper() in ["TCP", "UDP"]: if cnt == 0: print('packet[0] info: "%s:%d-%s:%d-%s"+%s' % ( pkt.src, pkt.payload.sport, pkt.dst, pkt.payload.dport, pkt.payload.name, pkt.payload.payload)) ### ... if pkt.payload.name.upper() == "TCP": pkts_stats['TCP_pkts'] += 1 else: pkts_stats['UDP_pkts'] += 1 else: pkts_stats['non_TCP_UDP_pkts'] += 1 # pkts_stats['IPv4_pkts'] += 1 else: pkts_stats['non_IPv4_pkts'] += 1 # print('unknown packets type!',pkt.name) pkts_stats['non_Ether_IPv4_pkts'] += 1 print('packet info:"srcIP:srcPort-dstIP:dstPort-prtcl" + IP_payload') if __name__ == '__main__': input_f = '' pcap2_parser()
Reference:
https://stackoverflow.com/questions/6388890/pcap-capture-merge-problem
https://metacpan.org/pod/distribution/File-PCAP/bin/acap2pcap
https://osqa-ask.wireshark.org/questions/54397/pcap-without-l2-frame-in-wireshark
https://stackoverflow.com/questions/27262291/how-to-create-a-scapy-packet-from-raw-bytes
posted on 2018-10-19 23:18 Quinn-Yann 阅读(1295) 评论(0) 编辑 收藏 举报


