容器编排系统K8s之访问控制--RBAC授权
前文我们了解了k8s上的访问控制机制,主要对访问控制中的第一关用户认证做了相关说明以及常规用户的配置文件的制作,回顾请参考:https://www.cnblogs.com/qiuhom-1874/p/14207381.html;今天我们来了解下k8s上的访问控制第二关RBAC授权相关话题;
在k8s上授权的机制有很多,最常用的有ABAC和RBAC;ABAC(attribute based access control)这种是基于属性做访问控制;RBAC(role based access control)这种是基于角色做访问控制;所谓基于属性做访问控制是指,对k8s上的资源的某种属性做授权,授权给相关用户对该资源的某个属性有什么权限;同样的逻辑基于角色做访问控制就是指把k8s上的资源,授权给对应角色有什么权限;那角色和用户有什么关系呢?对于RBAC授权模型来说,在k8s上用户是没法直接关联资源;它是通过角色对象来实现对资源的授权;用户授权是通过角色绑定对象来关联到对应角色;只要用户绑定到对应角色,那么该用户就拥有绑定角色上的所有权限;比如,在k8s上有一个角色名为pod-reader,这个角色能够对default名称空间下的pod资源有只读权限;对其他名称空间任何资源没有任何权限;如果一个用户绑定到该角色上,对应用户就有对default名称空间下的pod资源拥有只读权限,对其他名称空间任何资源没有任何权限;对于k8s上的资源来说,资源有两个级别,一个是名称空间级别的资源,一个是集群级别的资源;比如pod,svc,pvc等等这些资源都是名称空间级别资源,它们的存在必须是在某个名称空间下;对于类似像pv,node,ns这些资源就是集群级别资源,它们的存在不依赖任何名称空间;这样一来对于角色而言就有名称空间级别的角色,也有集群级别角色;名称空间级别的角色就是用来定义特定名称空间下的资源权限,集群级别角色就是用来定义整个集群上的资源权限;在k8s上这两种角色分别叫role和clusterrole;role和clusterrole都是k8s上的资源,我们要给某个用户授权,首先把对应角色资源实例化为一个角色对象,然后把用户和角色对象绑定起来即可;用户怎么绑定到角色上呢?在k8s上绑定这个操作也是通过资源对象实现的;绑定也有两种,一种是rolebinding,一种是clusterrolebinding;rolebinding是名称空间级别资源,它主要用来把对应用户和对应名称空间上的角色(role)做绑定;对应用户就能拥有对应角色在对应名称空间下对应资源的权限;clusterrolebinding主要用来把用户绑定到集群级别角色(clusterrole)上,对应用户就能拥有对整个集群上的对应角色拥有的对应资源的权限;简单讲角色(role/clusterrole)就是用来定义资源的权限,rolebinding和clusterrolebinding是用来关联用户和角色的关系;如下图所示;
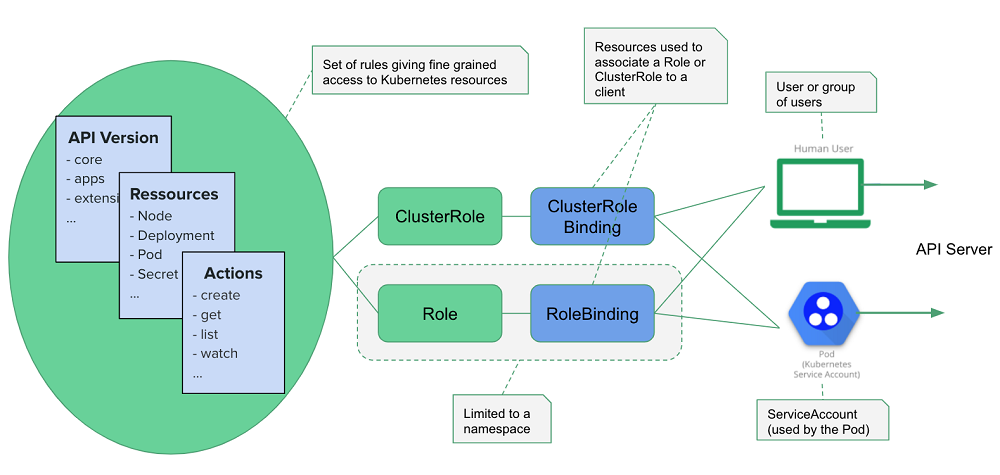
提示:这里需要注意一点,clusterrole是包含名称空间级别的role;也就是说clusterrole既可以用clusterrolebinding来绑定,也可以用rolebinding来绑定,如果rolebinding绑定的是一个集群级别的角色(clusterrole)那么对应绑定至clusterrole的用户的权限就会缩小到对应名称空间下,而非整个集群,原因是rolebinding是名称空间级别资源;
查看apiserver启用授权插件

提示:apiserver配置启用RBAC插件需要用--authorization-mode选项来指定对应启用的授权插件,在k8s1.6以后的版本,默认apiserver会启用Node和RBAC授权插件;
创建角色
使用陈述时命令create,创建角色的语法格式
Usage: kubectl create role NAME --verb=verb --resource=resource.group/subresource [--resource-name=resourcename] [--dry-run=server|client|none] [options]
提示:以上create role表示创建的是名称空间级别的角色,如果没有指定其名称空间表示默认名称空间;--verb是用来指定对应的权限,比如get,list,watch等等;--resource使用来指定资源资源类型,比如pods,services,daemonsets,replicasets等等;--resource-name用来指定对应具体的资源的名称;如果要指定名称空间使用-n选项指定即可;默认不指定表示default名称空间;
示例:使用陈述时命令创建名为pod-reader的角色,该角色拥有对default名称空间下的pod资源有list,get和watch权限;
[root@master01 ~]# kubectl create role pod-reader --verb=list --verb=get --verb=watch --resource=pods role.rbac.authorization.k8s.io/pod-reader created [root@master01 ~]# kubectl get role NAME CREATED AT pod-reader 2020-12-31T11:27:39Z [root@master01 ~]# kubectl describe role pod-reader Name: pod-reader Labels: <none> Annotations: <none> PolicyRule: Resources Non-Resource URLs Resource Names Verbs --------- ----------------- -------------- ----- pods [] [] [list get watch] [root@master01 ~]#
提示:可以看到pod-reader角色对pods资源有list,get,watch权限;
使用陈述式命令创建clusterrole
命令使用语法格式
Usage: kubectl create clusterrole NAME --verb=verb --resource=resource.group [--resource-name=resourcename] [--dry-run=server|client|none] [options]
提示:使用语法和创建名称空间级别的角色一样,不同的是指定创建的是clusterrole;
示例:创建一个名为cluster-pods-reader角色,拥有对集群所有名称空间下的pods和servers资源有get,list,watch权限;
[root@master01 ~]# kubectl create clusterrole cluster-pods-reader --verb=get --verb=list --verb=watch --resource=pods --resource=services clusterrole.rbac.authorization.k8s.io/cluster-pods-reader created [root@master01 ~]# kubectl get clusterrole cluster-pods-reader NAME CREATED AT cluster-pods-reader 2020-12-31T11:35:03Z [root@master01 ~]# kubectl describe clusterrole cluster-pods-reader Name: cluster-pods-reader Labels: <none> Annotations: <none> PolicyRule: Resources Non-Resource URLs Resource Names Verbs --------- ----------------- -------------- ----- pods [] [] [get list watch] services [] [] [get list watch] [root@master01 ~]#
提示:可以看到cluster-pods-reader角色有对pods资源和services资源有get,list,watch权限;
创建rolebinding
命令语法格式
Usage: kubectl create rolebinding NAME --clusterrole=NAME|--role=NAME [--user=username] [--group=groupname] [--serviceaccount=namespace:serviceaccountname] [--dry-run=server|client|none] [options]
提示:创建rolebinding需要指定对应的名称,指定clusterrole或者role角色的名称,指定对应的用户名称,或者对应的组名;如果对应用户是sa账号,需要用--serviceaccount选项来指定对应sa的名称;sa的名称由名称空间:sa名称;如果要指定名称空间使用-n选项指定即可;默认不指定表示default名称空间;
示例:创建名为tom-pods-reader的rolebinding,其中指定对应tom用户绑定至pod-reader角色
[root@master01 ~]# kubectl create rolebinding tom-pods-reader --role=pod-reader --user=tom rolebinding.rbac.authorization.k8s.io/tom-pods-reader created [root@master01 ~]# kubectl get rolebinding NAME ROLE AGE tom-pods-reader Role/pod-reader 5s [root@master01 ~]# kubectl describe rolebinding tom-pods-reader Name: tom-pods-reader Labels: <none> Annotations: <none> Role: Kind: Role Name: pod-reader Subjects: Kind Name Namespace ---- ---- --------- User tom [root@master01 ~]#
提示;这里没有显示名称空间是那个名称空间;默认没有显示就是default名称空间;
验证:使用tom用户的配置文件,看看是否可以列出default名称空间下的pod列表呢?
[root@master01 ~]# kubectl config view --kubeconfig=/tmp/myk8s.config
apiVersion: v1
clusters:
- cluster:
certificate-authority-data: DATA+OMITTED
server: https://192.168.0.41:6443
name: myk8s
contexts:
- context:
cluster: myk8s
user: tom
name: tom@myk8s
current-context: tom@myk8s
kind: Config
preferences: {}
users:
- name: tom
user:
client-certificate-data: REDACTED
client-key-data: REDACTED
username: tom
[root@master01 ~]# kubectl get pod --kubeconfig=/tmp/myk8s.config
NAME READY STATUS RESTARTS AGE
nginx-pod-demo 1/1 Running 1 44h
web-0 1/1 Running 2 2d21h
web-1 1/1 Running 2 2d21h
web-2 1/1 Running 2 2d21h
web-3 1/1 Running 3 2d21h
[root@master01 ~]#
提示:可以看到使用tom用户的配置文件,使用kubectl工具加载对应配置文件,在default名称空间下是可以正常列出pod列表;
验证:使用tom用户的配置文件看看是否列出kube-system名称空间下的pod列表呢?
[root@master01 ~]# kubectl get pod -n kube-system --kubeconfig=/tmp/myk8s.config Error from server (Forbidden): pods is forbidden: User "tom" cannot list resource "pods" in API group "" in the namespace "kube-system" [root@master01 ~]#
提示:可以看到对应tom用户是没有权限列出kube-system名称空间下的pod资源;
创建clusterrolebinding
命令使用语法格式
Usage: kubectl create clusterrolebinding NAME --clusterrole=NAME [--user=username] [--group=groupname] [--serviceaccount=namespace:serviceaccountname] [--dry-run=server|client|none] [options]
提示:使用方式和创建rolebinding一样,不同的是clusterrolebinding不能关联role角色;
示例:创建名为tom-all-pod-reader的clusterrolebinding,并关联cluster-pods-reader角色和tom用户;
[root@master01 ~]# kubectl create clusterrolebinding tom-all-pod-reader --clusterrole=cluster-pods-reader --user=tom clusterrolebinding.rbac.authorization.k8s.io/tom-all-pod-reader created [root@master01 ~]# kubectl get clusterrolebinding tom-all-pod-reader NAME ROLE AGE tom-all-pod-reader ClusterRole/cluster-pods-reader 20s [root@master01 ~]# kubectl describe clusterrolebinding tom-all-pod-reader Name: tom-all-pod-reader Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: cluster-pods-reader Subjects: Kind Name Namespace ---- ---- --------- User tom [root@master01 ~]#
验证:使用tom用户的配置文件查看kube-system名称空间下的pod资源列表
[root@master01 ~]# kubectl get pod -n kube-system --kubeconfig=/tmp/myk8s.config NAME READY STATUS RESTARTS AGE coredns-7f89b7bc75-k9gdt 1/1 Running 18 23d coredns-7f89b7bc75-kp855 1/1 Running 16 23d etcd-master01.k8s.org 1/1 Running 22 23d kube-apiserver-master01.k8s.org 1/1 Running 17 23d kube-controller-manager-master01.k8s.org 1/1 Running 19 23d kube-flannel-ds-cx8d5 1/1 Running 20 23d kube-flannel-ds-jz6r4 1/1 Running 11 12d kube-flannel-ds-ndzl6 1/1 Running 21 23d kube-flannel-ds-rjtn9 1/1 Running 23 23d kube-flannel-ds-zgq92 1/1 Running 20 23d kube-proxy-cr8j8 1/1 Running 13 11d kube-proxy-h8fzw 1/1 Running 8 11d kube-proxy-jfzfh 1/1 Running 9 11d kube-proxy-rq8wl 1/1 Running 8 11d kube-proxy-sj72v 1/1 Running 8 11d kube-scheduler-master01.k8s.org 1/1 Running 19 23d [root@master01 ~]# kubectl get pod --kubeconfig=/tmp/myk8s.config NAME READY STATUS RESTARTS AGE nginx-pod-demo 1/1 Running 1 44h web-0 1/1 Running 2 2d21h web-1 1/1 Running 2 2d21h web-2 1/1 Running 2 2d21h web-3 1/1 Running 3 2d22h [root@master01 ~]# kubectl get svc --kubeconfig=/tmp/myk8s.config NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 3d1h nginx ClusterIP None <none> 80/TCP 3d [root@master01 ~]# kubectl get svc -n kube-system --kubeconfig=/tmp/myk8s.config NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kube-dns ClusterIP 10.96.0.10 <none> 53/UDP,53/TCP,9153/TCP 23d [root@master01 ~]#
提示:可以看到把tom用户用clusterrolebinding关联到对应clusterrole角色上,就拥有对应角色上的权限;
验证:使用tom用户的配置文件查看pv或node集群级别资源,看看是否可以正常列出?
[root@master01 ~]# kubectl get pv --kubeconfig=/tmp/myk8s.config Error from server (Forbidden): persistentvolumes is forbidden: User "tom" cannot list resource "persistentvolumes" in API group "" at the cluster scope [root@master01 ~]# kubectl get node --kubeconfig=/tmp/myk8s.config Error from server (Forbidden): nodes is forbidden: User "tom" cannot list resource "nodes" in API group "" at the cluster scope [root@master01 ~]#
提示:使用tom用户的配置文件查看pv和node资源,apiserver直接拒绝了;原因是对应的clusterrole角色上没有查看pv和node的权限;所以对应用户也就没有相应的查看权限;
示例:创建rolebinding,把tom用户关联到clusterrole类型角色cluster-pods-reader
[root@master01 ~]# kubectl create rolebinding tom-rolebinding-clusterrole --clusterrole=cluster-pods-reader --user=tom rolebinding.rbac.authorization.k8s.io/tom-rolebinding-clusterrole created [root@master01 ~]# kubectl get rolebinding NAME ROLE AGE tom-pods-reader Role/pod-reader 20m tom-rolebinding-clusterrole ClusterRole/cluster-pods-reader 12s [root@master01 ~]# kubectl describe rolebinding tom-rolebinding-clusterrole Name: tom-rolebinding-clusterrole Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: cluster-pods-reader Subjects: Kind Name Namespace ---- ---- --------- User tom [root@master01 ~]#
验证:使用tom用户的配置文件,看看现在tom用户是否还有对应kube-system中的pod资源有列出权限呢?
[root@master01 ~]# kubectl get pods -n kube-system --kubeconfig=/tmp/myk8s.config NAME READY STATUS RESTARTS AGE coredns-7f89b7bc75-k9gdt 1/1 Running 18 23d coredns-7f89b7bc75-kp855 1/1 Running 16 23d etcd-master01.k8s.org 1/1 Running 22 23d kube-apiserver-master01.k8s.org 1/1 Running 17 23d kube-controller-manager-master01.k8s.org 1/1 Running 19 23d kube-flannel-ds-cx8d5 1/1 Running 20 23d kube-flannel-ds-jz6r4 1/1 Running 11 12d kube-flannel-ds-ndzl6 1/1 Running 21 23d kube-flannel-ds-rjtn9 1/1 Running 23 23d kube-flannel-ds-zgq92 1/1 Running 20 23d kube-proxy-cr8j8 1/1 Running 13 11d kube-proxy-h8fzw 1/1 Running 8 11d kube-proxy-jfzfh 1/1 Running 9 11d kube-proxy-rq8wl 1/1 Running 8 11d kube-proxy-sj72v 1/1 Running 8 11d kube-scheduler-master01.k8s.org 1/1 Running 19 23d [root@master01 ~]#
提示:这里还是能够列出kube-system名称空间下的pod,其原因是我们没有删除之前的clusterrolebinding,所以对应tom用户还有对kube-system的权限;
验证:删除clusterrolebinding tom-all-pod-reader 看看tom用户是否还有对kube-system中的pod列出权限呢?
[root@master01 ~]# kubectl get clusterrolebinding tom-all-pod-reader NAME ROLE AGE tom-all-pod-reader ClusterRole/cluster-pods-reader 14m [root@master01 ~]# kubectl delete clusterrolebinding tom-all-pod-reader clusterrolebinding.rbac.authorization.k8s.io "tom-all-pod-reader" deleted [root@master01 ~]# kubectl get rolebinding NAME ROLE AGE tom-pods-reader Role/pod-reader 27m tom-rolebinding-clusterrole ClusterRole/cluster-pods-reader 7m7s [root@master01 ~]# kubectl get pods -n kube-system --kubeconfig=/tmp/myk8s.config Error from server (Forbidden): pods is forbidden: User "tom" cannot list resource "pods" in API group "" in the namespace "kube-system" [root@master01 ~]#
提示:可以看到此时tom用户就没有对kube-system名称空间下的pod有列出权限了;
验证:使用tom用户的配置文件,查看default名称空间下的pods和service资源,看看是否有权限?
[root@master01 ~]# kubectl get pods --kubeconfig=/tmp/myk8s.config NAME READY STATUS RESTARTS AGE nginx-pod-demo 1/1 Running 1 45h web-0 1/1 Running 2 2d22h web-1 1/1 Running 2 2d22h web-2 1/1 Running 2 2d22h web-3 1/1 Running 3 2d22h [root@master01 ~]# kubectl get svc --kubeconfig=/tmp/myk8s.config NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 3d1h nginx ClusterIP None <none> 80/TCP 3d [root@master01 ~]#
提示:可以看到tom用户在default名称空间下能够正常列出pod和service资源;从上面的示例可以看到当rolebinding绑定的是一个clusterrole,对应clusterrole的权限就会降低至对应rolebinding的名称空间;
使用资源清单创建角色
示例:使用资源清单创建role-demo角色
[root@master01 ~]# cat role-demo.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: Role metadata: name: role-demo namespace: testing rules: - apiGroups: [""] resources: ["pods","pods/log","services"] verbs: ["get","list","watch"] [root@master01 ~]#
提示:role资源没有spec字段,它的群组是rbac.authorization.k8s.io/v1,对应类型为Role;metadata字段中的name用于指定对应role的名称;namespace用户指定对应的名称空间;roles字段用来描述对资源和权限,该字段为一个列表对象,一个对象必须有apiGroup,resources和verbs字段;其中apiGroup字段用来描述对应资源所属群组,默认不写任何群组表示核心群组v1;如果是匹配所有群组可以写成“*”;该字段是一个列表类型数据,所以必须用中括号将其括起来,即便没有值;resources字段用来描述对应的资源,这里的资源如果可以使用复数形式的必须使用复数形式;所谓复数是指对应资源名称单词的复数形式;该字段也是一个列表,可以使用中括号,也可以直接使用-开头写对应的值;verbs字段用来描述对应的权限,该字段也是一个列表,可以使用中括号或者“-”开头从下一行直接写值的方式;上述资源清单表示创建一个名为role-demo的角色在testing名称空间;对应角色拥有对该名称空间下的pod,pods/log和services资源有get,list,watch权限;
创建名称空间并应用配置清单
[root@master01 ~]# kubectl get ns NAME STATUS AGE default Active 23d ingress-nginx Active 9d kube-node-lease Active 23d kube-public Active 23d kube-system Active 23d [root@master01 ~]# kubectl create ns testing namespace/testing created [root@master01 ~]# kubectl apply -f role-demo.yaml role.rbac.authorization.k8s.io/role-demo created [root@master01 ~]# kubectl get role -n testing NAME CREATED AT role-demo 2020-12-31T12:46:53Z [root@master01 ~]# kubectl describe role role-demo -n testing Name: role-demo Labels: <none> Annotations: <none> PolicyRule: Resources Non-Resource URLs Resource Names Verbs --------- ----------------- -------------- ----- pods/log [] [] [get list watch] pods [] [] [get list watch] services [] [] [get list watch] [root@master01 ~]#
示例:使用资源清单创建rolebinding
[root@master01 ~]# cat rolebinding-demo.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: rolebinding-demo namespace: testing roleRef: kind: Role name: role-demo apiGroup: rbac.authorization.k8s.io subjects: - kind: User apiGroup: rbac.authorization.k8s.io name: tom [root@master01 ~]#
提示:使用资源清单创建rolebinding,需要用roleRef字段来指定引用的role或clusterrole,该字段为一个对象,其中kind指定对应角色的类型,Role表示引用名称空间级别的role;ClusterRole表示引用集群级别角色clusterrole;apiGroup是用来描述对应角色的不带版本api群组;subjects字段用来描述对应用户或组,该字段为一个列表对象;其中kind字段用来表示对应的是用户还是用户组;User表示用户,Group表示用户组;ServiceAccount表示是一个sa用户;apiGroup用来指定对应不带版本的api群组;name用来指定用户名或组名或sa名;上述资源清单表示把tom用户和role-demo角色做关联,即授权tom用户拥有role-demo角色的权限;
验证:在未应用资源清单前使用tom用户的配置文件查看testing名称空间下的pod资源
[root@master01 ~]# kubectl get pods -n testing --kubeconfig=/tmp/myk8s.config Error from server (Forbidden): pods is forbidden: User "tom" cannot list resource "pods" in API group "" in the namespace "testing" [root@master01 ~]#
提示:在未应用上述资源清单,tom用户对testing名称空间的资源没有任何权限;
应用资源清单
[root@master01 ~]# kubectl apply -f rolebinding-demo.yaml rolebinding.rbac.authorization.k8s.io/rolebinding-demo created [root@master01 ~]# kubectl get rolebinding -n testing NAME ROLE AGE rolebinding-demo Role/role-demo 31s [root@master01 ~]# kubectl describe rolebinding rolebinding-demo -n testing Name: rolebinding-demo Labels: <none> Annotations: <none> Role: Kind: Role Name: role-demo Subjects: Kind Name Namespace ---- ---- --------- User tom [root@master01 ~]# kubectl get pods -n testing --kubeconfig=/tmp/myk8s.config No resources found in testing namespace. [root@master01 ~]#
提示:可以看到应用资源清单以后,再次使用tom用户的配置文件查看testing名称空间下的pod资源,就没有提示没有权限拒绝,只是告诉我们对应名称空间下没有pod资源;
示例:使用资源清单创建clusterrole
[root@master01 ~]# cat clusterrole-demo.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRole metadata: name: clusterrole-demo rules: - apiGroups: [""] resources: ["pods","nodes","PersistentVolume"] verbs: ["get","list","watch","create","delete"] [root@master01 ~]#
提示:使用资源清单创建clusterrole和创建role是一样的格式,不同的是对应kind的值不同,不需要指定名称空间;其他的都一样;
应用资源清单
[root@master01 ~]# kubectl apply -f clusterrole-demo.yaml clusterrole.rbac.authorization.k8s.io/clusterrole-demo created [root@master01 ~]# kubectl get clusterrole clusterrole-demo NAME CREATED AT clusterrole-demo 2020-12-31T13:23:48Z [root@master01 ~]# kubectl describe clusterrole clusterrole-demo Name: clusterrole-demo Labels: <none> Annotations: <none> PolicyRule: Resources Non-Resource URLs Resource Names Verbs --------- ----------------- -------------- ----- PersistentVolume [] [] [get list watch create delete] nodes [] [] [get list watch create delete] pods [] [] [get list watch create delete] [root@master01 ~]#
示例:使用资源清单创建clusterrolebinding
[root@master01 ~]# cat clusterrolebinding.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: clusterrolebinding-demo roleRef: kind: ClusterRole name: clusterrole-demo apiGroup: rbac.authorization.k8s.io subjects: - kind: User apiGroup: rbac.authorization.k8s.io name: tom [root@master01 ~]#
提示:使用资源清单创建clusterrolebinding和创建rolebinding的格式一样,不同的是创建clusterrolebinding不需要指定名称空间,对应kind值为ClusterRoleBinding;其他字段的使用方式和role一样;上述资源清单表示把tom用户和clusterrole-demo角色做关联;
验证:在没有应用资源清单前使用tom用户的配置文件查看kube-system名称空间下的pod资源
[root@master01 ~]# kubectl get pods -n kube-system --kubeconfig=/tmp/myk8s.config Error from server (Forbidden): pods is forbidden: User "tom" cannot list resource "pods" in API group "" in the namespace "kube-system" [root@master01 ~]#
提示:没有应用资源清单前使用tom用户的配置文件查看kube-system名称空间下的pod资源,是被apiserver拒绝的;
应用配置清单
[root@master01 ~]# kubectl apply -f clusterrolebinding.yaml clusterrolebinding.rbac.authorization.k8s.io/clusterrolebinding-demo created [root@master01 ~]# kubectl get clusterrolebinding clusterrolebinding-demo NAME ROLE AGE clusterrolebinding-demo ClusterRole/clusterrole-demo 15s [root@master01 ~]# kubectl describe clusterrolebinding clusterrolebinding-demo Name: clusterrolebinding-demo Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: clusterrole-demo Subjects: Kind Name Namespace ---- ---- --------- User tom [root@master01 ~]# kubectl get pods -n kube-system --kubeconfig=/tmp/myk8s.config NAME READY STATUS RESTARTS AGE coredns-7f89b7bc75-k9gdt 1/1 Running 18 23d coredns-7f89b7bc75-kp855 1/1 Running 16 23d etcd-master01.k8s.org 1/1 Running 22 23d kube-apiserver-master01.k8s.org 1/1 Running 17 23d kube-controller-manager-master01.k8s.org 1/1 Running 19 23d kube-flannel-ds-cx8d5 1/1 Running 20 23d kube-flannel-ds-jz6r4 1/1 Running 11 13d kube-flannel-ds-ndzl6 1/1 Running 21 23d kube-flannel-ds-rjtn9 1/1 Running 23 23d kube-flannel-ds-zgq92 1/1 Running 20 23d kube-proxy-cr8j8 1/1 Running 13 11d kube-proxy-h8fzw 1/1 Running 8 11d kube-proxy-jfzfh 1/1 Running 9 11d kube-proxy-rq8wl 1/1 Running 8 11d kube-proxy-sj72v 1/1 Running 8 11d kube-scheduler-master01.k8s.org 1/1 Running 19 23d [root@master01 ~]#
提示:可以看到应用资源清单以后,再使用tom用户的配置文件查看kube-system名称空间下的pod就可以正常列出了,说明对应tom用户授权成功;
查看系统默认的clusterrole
[root@master01 ~]# kubectl get clusterrole NAME CREATED AT admin 2020-12-08T06:39:13Z cluster-admin 2020-12-08T06:39:13Z cluster-pods-reader 2020-12-31T11:35:03Z clusterrole-demo 2020-12-31T13:23:48Z edit 2020-12-08T06:39:13Z flannel 2020-12-08T06:59:56Z kubeadm:get-nodes 2020-12-08T06:39:15Z nginx-ingress-clusterrole 2020-12-21T15:16:13Z system:aggregate-to-admin 2020-12-08T06:39:13Z system:aggregate-to-edit 2020-12-08T06:39:13Z system:aggregate-to-view 2020-12-08T06:39:13Z system:auth-delegator 2020-12-08T06:39:13Z system:basic-user 2020-12-08T06:39:13Z system:certificates.k8s.io:certificatesigningrequests:nodeclient 2020-12-08T06:39:13Z system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 2020-12-08T06:39:13Z system:certificates.k8s.io:kube-apiserver-client-approver 2020-12-08T06:39:13Z system:certificates.k8s.io:kube-apiserver-client-kubelet-approver 2020-12-08T06:39:13Z system:certificates.k8s.io:kubelet-serving-approver 2020-12-08T06:39:13Z system:certificates.k8s.io:legacy-unknown-approver 2020-12-08T06:39:13Z system:controller:attachdetach-controller 2020-12-08T06:39:13Z system:controller:certificate-controller 2020-12-08T06:39:13Z system:controller:clusterrole-aggregation-controller 2020-12-08T06:39:13Z system:controller:cronjob-controller 2020-12-08T06:39:13Z system:controller:daemon-set-controller 2020-12-08T06:39:13Z system:controller:deployment-controller 2020-12-08T06:39:13Z system:controller:disruption-controller 2020-12-08T06:39:13Z system:controller:endpoint-controller 2020-12-08T06:39:13Z system:controller:endpointslice-controller 2020-12-08T06:39:13Z system:controller:endpointslicemirroring-controller 2020-12-08T06:39:13Z system:controller:expand-controller 2020-12-08T06:39:13Z system:controller:generic-garbage-collector 2020-12-08T06:39:13Z system:controller:horizontal-pod-autoscaler 2020-12-08T06:39:13Z system:controller:job-controller 2020-12-08T06:39:13Z system:controller:namespace-controller 2020-12-08T06:39:13Z system:controller:node-controller 2020-12-08T06:39:13Z system:controller:persistent-volume-binder 2020-12-08T06:39:13Z system:controller:pod-garbage-collector 2020-12-08T06:39:13Z system:controller:pv-protection-controller 2020-12-08T06:39:13Z system:controller:pvc-protection-controller 2020-12-08T06:39:13Z system:controller:replicaset-controller 2020-12-08T06:39:13Z system:controller:replication-controller 2020-12-08T06:39:13Z system:controller:resourcequota-controller 2020-12-08T06:39:13Z system:controller:root-ca-cert-publisher 2020-12-08T06:39:13Z system:controller:route-controller 2020-12-08T06:39:13Z system:controller:service-account-controller 2020-12-08T06:39:13Z system:controller:service-controller 2020-12-08T06:39:13Z system:controller:statefulset-controller 2020-12-08T06:39:13Z system:controller:ttl-controller 2020-12-08T06:39:13Z system:coredns 2020-12-08T06:39:15Z system:discovery 2020-12-08T06:39:13Z system:heapster 2020-12-08T06:39:13Z system:kube-aggregator 2020-12-08T06:39:13Z system:kube-controller-manager 2020-12-08T06:39:13Z system:kube-dns 2020-12-08T06:39:13Z system:kube-scheduler 2020-12-08T06:39:13Z system:kubelet-api-admin 2020-12-08T06:39:13Z system:monitoring 2020-12-08T06:39:13Z system:node 2020-12-08T06:39:13Z system:node-bootstrapper 2020-12-08T06:39:13Z system:node-problem-detector 2020-12-08T06:39:13Z system:node-proxier 2020-12-08T06:39:13Z system:persistent-volume-provisioner 2020-12-08T06:39:13Z system:public-info-viewer 2020-12-08T06:39:13Z system:service-account-issuer-discovery 2020-12-08T06:39:13Z system:volume-scheduler 2020-12-08T06:39:13Z view 2020-12-08T06:39:13Z [root@master01 ~]#
提示:以system开头的都是系统默认创建的clusterrole角色;这些角色都是用来给对应组件授权用的,比如,system:kube-dns就是用来给kube-dns这个pod在apiserver上验证授权需要使用的角色;system:kube-controller-manager这个角色就是用来kube-controller-manager这个pod在apiserver上拥有的权限;kube-controller-manager这个pod向apiserver验证时,首先把对应的证书发送给apiserver,apiserver通过识别对应证书中CN的名字来确定对应的用户名;如果对应用户名是system:kube-controller-manager,那么对应kube-controller-manager这个pod就拥有对应该角色的所有权限;如果我们手动部署的k8s集群,对应controller-manager的证书中CN名称不是system:kube-controller-manager,那么我们手动部署的k8s集群将不能正常工作,对于其他组件也是类似的逻辑;除了内置了以system开头的很多clusterrole,k8s为了方便我们授权,它还内置了4个特殊的clusterrole,分别是cluster-admin,admin,edit和view;其中cluster-admin是拥有对整个集群的所有资源拥有所有权限,默认这个角色被clusterrolebinding绑定在system:master这个组上;对应kuberctl使用的证书文件中O的信息就是system:master,所以我们使用kubectl加载默认的配置文件可以操作整个集群上的所有资源;admin角色也是一个管理员权限,不同于cluster-admin,admin角色一般用于通过rolebinding来实现对特有名称空间的管理员授权;edit和view也是类似的逻辑,主要用于通过rolebinding来实现特有名称空间下的特定管理员;比如快速授权某个用户在某个名称空间下拥有只读权限,那么我们就可以把对应用户通过rolebinding将其绑定至view这个clusterrole角色上;如果只允许某个用户拥有对应名称空间下的所有资源的修改权限,就可以把对应用户通过rolebinding绑定到edit这个clusterrole角色上;当然以上几个角色也可以通过clusterrolebinding来绑定,用clusterrolebinding来绑定,对应用户就是对应整个集群的所有资源;有了上述4个内置的clusterrole,我们就可以快速的将某个用户授权为特定的角色:
查看kubectl默认证书中的信息
复制配置文件中的client-certificate-data 对应的被base64编码处理过的信息,然后通过base64 -d将其解密,然后使用openssl x509 -text -noout 来查看对应证书中的信息

提示:可以看到当前kubectl的证书中O=system:master CN=kubernetes-admin;之所以kubectl能够管理集群资源是因为对应证书中的O=system:master,该信息直接对应k8s上的集群角色cluster-admin;对应集群角色就是通过clusterrolebinding绑定到system:master组;所以kubectl就拥有对k8s整个集群资源的管控;
示例:授权tom用户为集群管理员
[root@master01 ~]# cat tom-clusterrolebinding-cluster-admin.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: ClusterRoleBinding metadata: name: tom-cluster-admin roleRef: kind: ClusterRole name: cluster-admin apiGroup: rbac.authorization.k8s.io subjects: - kind: User apiGroup: rbac.authorization.k8s.io name: tom [root@master01 ~]#
提示:上述资源表示通过clusterrolebinding授权tom用户拥有cluster-admin角色的所有权限,即集群管理员;
应用资源清单
[root@master01 ~]# kubectl apply -f tom-clusterrolebinding-cluster-admin.yaml clusterrolebinding.rbac.authorization.k8s.io/tom-cluster-admin created [root@master01 ~]# kubectl get clusterrolebinding tom-cluster-admin NAME ROLE AGE tom-cluster-admin ClusterRole/cluster-admin 21s [root@master01 ~]# kubectl describe clusterrolebinding tom-cluster-admin Name: tom-cluster-admin Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: cluster-admin Subjects: Kind Name Namespace ---- ---- --------- User tom [root@master01 ~]#
验证:使用tom用户的配置文件,管理集群资源
[root@master01 ~]# kubectl get all --kubeconfig=/tmp/myk8s.config NAME READY STATUS RESTARTS AGE pod/nginx-pod-demo 1/1 Running 1 47h pod/web-0 1/1 Running 2 3d pod/web-1 1/1 Running 2 3d pod/web-2 1/1 Running 2 3d pod/web-3 1/1 Running 3 3d NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 3d3h service/nginx ClusterIP None <none> 80/TCP 3d3h NAME READY AGE statefulset.apps/web 4/4 3d3h [root@master01 ~]# kubectl delete all --all --kubeconfig=/tmp/myk8s.config pod "nginx-pod-demo" deleted pod "web-0" deleted pod "web-1" deleted pod "web-2" deleted pod "web-3" deleted service "kubernetes" deleted service "nginx" deleted statefulset.apps "web" deleted [root@master01 ~]# kubectl apply -f statefulset-demo.yaml --kubeconfig=/tmp/myk8s.config service/nginx created statefulset.apps/web created [root@master01 ~]# kubectl get all --kubeconfig=/tmp/myk8s.config NAME READY STATUS RESTARTS AGE pod/web-0 1/1 Running 0 9s pod/web-1 1/1 Running 0 6s pod/web-2 1/1 Running 0 4s NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE service/kubernetes ClusterIP 10.96.0.1 <none> 443/TCP 85s service/nginx ClusterIP None <none> 80/TCP 9s NAME READY AGE statefulset.apps/web 3/3 9s [root@master01 ~]#
提示:可以看到我们使用tom用户的配置文件和默认配置文件是一样的效果,瞬间tom用户就变成了集群管理;
删除tom-cluster-admin这个clusterrolebinding
[root@master01 ~]# kubectl delete -f tom-clusterrolebinding-cluster-admin.yaml clusterrolebinding.rbac.authorization.k8s.io "tom-cluster-admin" deleted [root@master01 ~]#
授权tom用户只读ingress-nginx名称空间下的所有资源
[root@master01 ~]# cat tom-ingress-nginx-view.yaml apiVersion: rbac.authorization.k8s.io/v1 kind: RoleBinding metadata: name: tom-ingress-nginx-view namespace: ingress-nginx roleRef: kind: ClusterRole name: view apiGroup: rbac.authorization.k8s.io subjects: - kind: User apiGroup: rbac.authorization.k8s.io name: tom [root@master01 ~]#
提示:上述配置表示通过ingress-nginx名称 空间下的rolebinding把tom用户绑定至view这个clusterrole上;即对应tom用户对ingress-nginx名称空间下的所有资源只有只读权限;
应用资源配置清单
[root@master01 ~]# kubectl apply -f tom-ingress-nginx-view.yaml rolebinding.rbac.authorization.k8s.io/tom-ingress-nginx-view created [root@master01 ~]# kubectl get rolebinding -n ingress-nginx NAME ROLE AGE nginx-ingress-role-nisa-binding Role/nginx-ingress-role 9d tom-ingress-nginx-view ClusterRole/view 22s [root@master01 ~]# kubectl describe rolebinding tom-ingress-nginx-view -n ingress-nginx Name: tom-ingress-nginx-view Labels: <none> Annotations: <none> Role: Kind: ClusterRole Name: view Subjects: Kind Name Namespace ---- ---- --------- User tom [root@master01 ~]#
验证:使用tom用户的配置文件管理ingress-nginx名称空间下的资源
[root@master01 ~]# kubectl get pods -n ingress-nginx --kubeconfig=/tmp/myk8s.config NAME READY STATUS RESTARTS AGE nginx-ingress-controller-5466cb8999-dzn5d 1/1 Running 0 33s [root@master01 ~]# kubectl get pods --kubeconfig=/tmp/myk8s.config Error from server (Forbidden): pods is forbidden: User "tom" cannot list resource "pods" in API group "" in the namespace "default" [root@master01 ~]# kubectl delete pod nginx-ingress-controller-5466cb8999-dzn5d -n ingress-nginx --kubeconfig=/tmp/myk8s.config Error from server (Forbidden): pods "nginx-ingress-controller-5466cb8999-dzn5d" is forbidden: User "tom" cannot delete resource "pods" in API group "" in the namespace "ingress-nginx" [root@master01 ~]#
提示:可以看到现在tom用户只能查看ingress-nginx名称空间下的资源,不能查看default名称空间下的资源,其次对ingress-nginx名称空间下的pod资源没有删除权限;

 在k8s上授权的机制有很多,最常用的有ABAC和RBAC;ABAC(attribute based access control)这种是基于属性做访问控制;RBAC(role based access control)这种是基于角色做访问控制;所谓基于属性做访问控制是指,对k8s上的资源的某种属性做授权,授权给相关用户对该资源的某个属性有什么权限;同样的逻辑基于角色做访问控制就是指把k8s上的资源,授权给对应角色有什么权限;那角色和用户有什么关系呢?对于RBAC授权模型来说,在k8s上用户是没法直接关联资源;它是通过角色对象来实现对资源的授权;用户授权是通过角色绑定对象来关联到对应角色;只要用户绑定到对应角色,那么该用户就拥有绑定角色上的所有权限;
在k8s上授权的机制有很多,最常用的有ABAC和RBAC;ABAC(attribute based access control)这种是基于属性做访问控制;RBAC(role based access control)这种是基于角色做访问控制;所谓基于属性做访问控制是指,对k8s上的资源的某种属性做授权,授权给相关用户对该资源的某个属性有什么权限;同样的逻辑基于角色做访问控制就是指把k8s上的资源,授权给对应角色有什么权限;那角色和用户有什么关系呢?对于RBAC授权模型来说,在k8s上用户是没法直接关联资源;它是通过角色对象来实现对资源的授权;用户授权是通过角色绑定对象来关联到对应角色;只要用户绑定到对应角色,那么该用户就拥有绑定角色上的所有权限;
