分布式文档存储数据库之MongoDB访问控制
上一篇博客主要聊了下mongodb的分片机制以及分片集群的搭建,回顾请参考https://www.cnblogs.com/qiuhom-1874/p/13958295.html;今天我们来了解下mongodb的访问控制;
什么是访问控制?
简单讲访问控制就是指,哪些用户可以访问哪些资源,对资源有哪些操作(权限);在mongodb中我们把数据库、或者集合叫做资源;也就说访问控制是用来限制某些用户对数据库或集合的操作;我们在mysql数据库中,我们通过给账号授权的方式达到控制哪些用户可以从哪些主机访问数据库,对数据库有哪些操作;其中账号由用户名称和主机地址构成;在mongodb中采用的不是用户+主机地址的方式,而是通过给用户赋予一个或多个角色,这个角色或多个角色的所有权限就是这个用户拥有的权限;默认情况mongodb是没有启用访问控制的,所以只要能够连接上mongodb实例,我们就可以在其上做任何操作,在某种程度上,这是一种极为不安全的方式,为了杜绝这种不安全的访问方式,我们需要对mongodb进行访问控制;
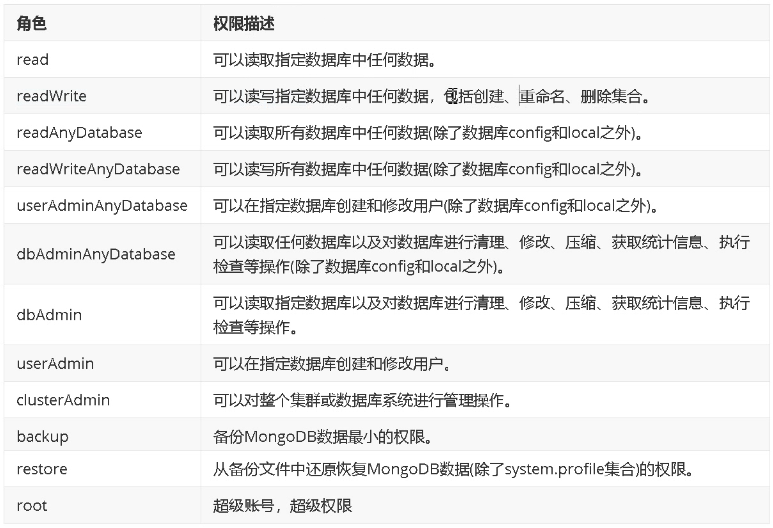
mongodb中的角色权限说明
mongodb默认内置了一些角色,不同的角色拥有不同的权限,如下图
查看mongodb中某个数据库所有内置角色
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 | > db.runCommand({rolesInfo:1,showBuiltinRoles:true}){ "roles" : [ { "role" : "dbAdmin", "db" : "test", "isBuiltin" : true, "roles" : [ ], "inheritedRoles" : [ ] }, { "role" : "dbOwner", "db" : "test", "isBuiltin" : true, "roles" : [ ], "inheritedRoles" : [ ] }, { "role" : "enableSharding", "db" : "test", "isBuiltin" : true, "roles" : [ ], "inheritedRoles" : [ ] }, { "role" : "read", "db" : "test", "isBuiltin" : true, "roles" : [ ], "inheritedRoles" : [ ] }, { "role" : "readWrite", "db" : "test", "isBuiltin" : true, "roles" : [ ], "inheritedRoles" : [ ] }, { "role" : "userAdmin", "db" : "test", "isBuiltin" : true, "roles" : [ ], "inheritedRoles" : [ ] } ], "ok" : 1}> |
提示:以上是mongodb中test库的默认角色;如果要查看其它库,我们需要切换到其他库,然后运行上述命令查看即可;
查询当前数据中的某个角色
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | > dbtest> db.runCommand({rolesInfo:"userAdmin"}){ "roles" : [ { "role" : "userAdmin", "db" : "test", "isBuiltin" : true, "roles" : [ ], "inheritedRoles" : [ ] } ], "ok" : 1}> |
查询其他数据库中指定的角色权限
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 | > db.runCommand({rolesInfo:{role:"userAdmin",db:"config"}}){ "roles" : [ { "role" : "userAdmin", "db" : "config", "isBuiltin" : true, "roles" : [ ], "inheritedRoles" : [ ] } ], "ok" : 1}> db.runCommand({rolesInfo:{role:"root",db:"config"}}){ "roles" : [ ], "ok" : 1 }> db.runCommand({rolesInfo:{role:"root",db:"admin"}}){ "roles" : [ { "role" : "root", "db" : "admin", "isBuiltin" : true, "roles" : [ ], "inheritedRoles" : [ ] } ], "ok" : 1}> |
创建一个用户名为tom,其角色为超级管理员角色root
1 2 3 4 5 6 7 8 9 10 11 12 13 | > use adminswitched to db admin> db.createUser({user:"tom",pwd:"admin123.com",roles:[{"role":"root","db":"admin"}]})Successfully added user: { "user" : "tom", "roles" : [ { "role" : "root", "db" : "admin" } ]}> |
查看当前库用户列表
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | > dbadmin> db.getUsers()[ { "_id" : "admin.tom", "userId" : UUID("67bf434a-49fc-4ed5-9e9b-23c443a2fc93"), "user" : "tom", "db" : "admin", "roles" : [ { "role" : "root", "db" : "admin" } ], "mechanisms" : [ "SCRAM-SHA-1", "SCRAM-SHA-256" ] }]> |
创建数据库管理员用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 | > db.createUser({user:"jerry",pwd:"admin123.com",roles:["userAdminAnyDatabase"]})Successfully added user: { "user" : "jerry", "roles" : [ "userAdminAnyDatabase" ] }> db.getUsers()[ { "_id" : "admin.jerry", "userId" : UUID("5d0b77f2-b7f1-40cd-8149-f08b2e1e6a80"), "user" : "jerry", "db" : "admin", "roles" : [ { "role" : "userAdminAnyDatabase", "db" : "admin" } ], "mechanisms" : [ "SCRAM-SHA-1", "SCRAM-SHA-256" ] }, { "_id" : "admin.tom", "userId" : UUID("67bf434a-49fc-4ed5-9e9b-23c443a2fc93"), "user" : "tom", "db" : "admin", "roles" : [ { "role" : "root", "db" : "admin" } ], "mechanisms" : [ "SCRAM-SHA-1", "SCRAM-SHA-256" ] }]> |
提示:如果创建用户时,未指定db,则表示当前该用户对当前所在db生效;
删除用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 | > db.dropUser("jerry")true> db.getUsers()[ { "_id" : "admin.tom", "userId" : UUID("67bf434a-49fc-4ed5-9e9b-23c443a2fc93"), "user" : "tom", "db" : "admin", "roles" : [ { "role" : "root", "db" : "admin" } ], "mechanisms" : [ "SCRAM-SHA-1", "SCRAM-SHA-256" ] }]> |
提示:删除用户,需切换到对应数据下,指定对应用户名称即可;在mongodb中用户是对应数据库的,一个用户可以对应一个或多个数据库,在指定数据库删除用户,就表示删除指定用户对指定数据库的访问权限;
修改指定用户的密码
1 2 3 4 | > dbadmin> db.changeUserPassword("tom","123456")> |
提示:修改用户密码,第一个是指定用户的名称,第二个是指定新密码;
验证用户名和密码
给错误的密码
1 2 3 4 5 6 | > dbadmin> db.auth("tom","admin")Error: Authentication failed.0> |
给正确的密码
1 2 3 4 5 | > dbadmin> db.auth("tom","123456")1> |
创建一个普通用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 | > use testdbswitched to db testdb> db.createUser({user:"test",pwd:"admin",roles:[{role:"readWrite",db:"testdb"}]})Successfully added user: { "user" : "test", "roles" : [ { "role" : "readWrite", "db" : "testdb" } ]}> db.getUsers()[ { "_id" : "testdb.test", "userId" : UUID("95ecb34c-46f4-44fa-8948-4f0875499d8e"), "user" : "test", "db" : "testdb", "roles" : [ { "role" : "readWrite", "db" : "testdb" } ], "mechanisms" : [ "SCRAM-SHA-1", "SCRAM-SHA-256" ] }]> |
提示:以上就创建了一个名为test的用户,它可对testdb这个库下的所有collection做读写操作;
创建一个多角色的用户
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 | > dbtestdb> db.createUser(... {... user:"jerry1",... pwd:"admin123.com",... roles:[... {role:"clusterAdmin",db:"admin"},... {role:"readWrite",db:"testdb"},... {role:"read",db:"testdb1"}... ]... })Successfully added user: { "user" : "jerry1", "roles" : [ { "role" : "clusterAdmin", "db" : "admin" }, { "role" : "readWrite", "db" : "testdb" }, { "role" : "read", "db" : "testdb1" } ]}> db.getUsers()[ { "_id" : "testdb.jerry1", "userId" : UUID("43d66bf8-1e3a-4c14-ad73-5961b5a7660f"), "user" : "jerry1", "db" : "testdb", "roles" : [ { "role" : "clusterAdmin", "db" : "admin" }, { "role" : "readWrite", "db" : "testdb" }, { "role" : "read", "db" : "testdb1" } ], "mechanisms" : [ "SCRAM-SHA-1", "SCRAM-SHA-256" ] }, { "_id" : "testdb.test", "userId" : UUID("95ecb34c-46f4-44fa-8948-4f0875499d8e"), "user" : "test", "db" : "testdb", "roles" : [ { "role" : "readWrite", "db" : "testdb" } ], "mechanisms" : [ "SCRAM-SHA-1", "SCRAM-SHA-256" ] }]> |
提示:在mongodb中一个用户可以授权拥有多个角色权限;
开启mongodb服务端访问控制配置
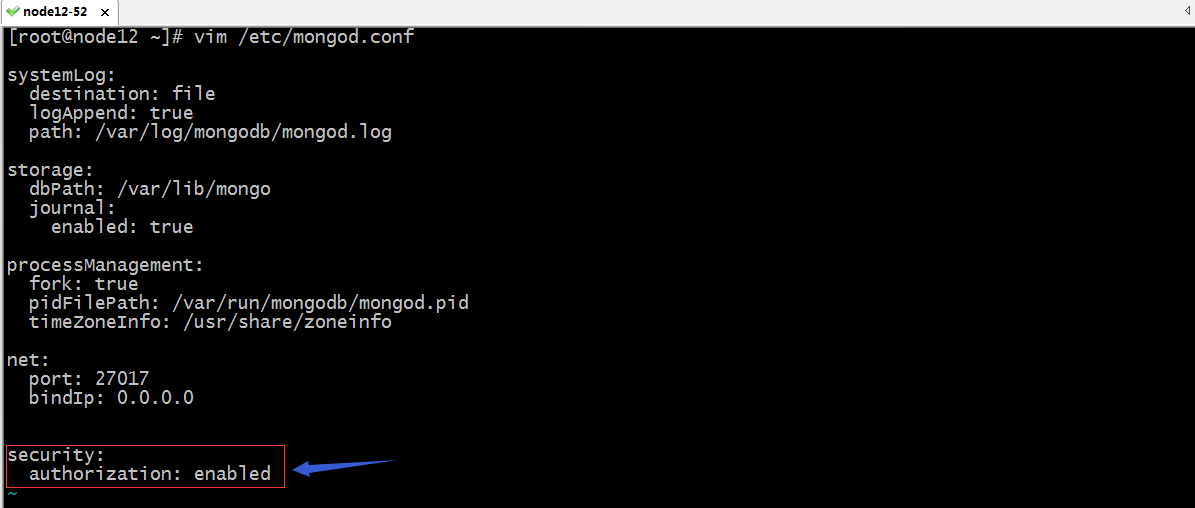
重启服务
1 2 3 4 5 6 7 8 9 | [root@node12 ~]# systemctl restart mongod.service [root@node12 ~]# ss -tnlState Recv-Q Send-Q Local Address:Port Peer Address:Port LISTEN 0 128 *:22 *:* LISTEN 0 100 127.0.0.1:25 *:* LISTEN 0 128 *:27017 *:* LISTEN 0 128 :::22 :::* LISTEN 0 100 ::1:25 :::* [root@node12 ~]# |
测试:现在连接mongodb,看看会发生什么?
1 2 3 4 5 6 7 8 9 10 11 | [root@node12 ~]# mongoMongoDB shell version v4.4.1connecting to: mongodb://127.0.0.1:27017/?compressors=disabled&gssapiServiceName=mongodbImplicit session: session { "id" : UUID("68fa2f83-64a4-42c2-8d64-9ee73a77e883") }MongoDB server version: 4.4.1> show dbs> dbtest> show tablesWarning: unable to run listCollections, attempting to approximate collection names by parsing connectionStatus> |
提示:现在我们直接连接mongodb是可以正常连接,但是我们没法查看数据列表以及collections了;这个时候我们就需要进行用户认证了;
认证用户
1 2 3 4 5 6 7 8 9 10 11 12 | > dbtest> db.auth("test","admin")Error: Authentication failed.0> use testdbswitched to db testdb> db.auth("test","admin")1> show dbs> show collections> |
提示:认证用户必须切换到对应的数据库下做认证;我这里test用户只能对testdb库下的所有collection进行读写,所以认证以后,我们在使用 show dbs命令就看不到系统admin和config库了;除了上述连接数据库以后使用db.auth()做用户认证,我们也可直接在连接数据库时指定用户名和密码,如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 | [root@node12 ~]# mongo -utest -padmin testdbMongoDB shell version v4.4.1connecting to: mongodb://127.0.0.1:27017/testdb?compressors=disabled&gssapiServiceName=mongodbImplicit session: session { "id" : UUID("60c43e94-04c6-46f4-be07-07ca8fa06b2f") }MongoDB server version: 4.4.1> show dbs> exitbye[root@node12 ~]# mongo -utest -padmin 192.168.0.52:27017/testdbMongoDB shell version v4.4.1connecting to: mongodb://192.168.0.52:27017/testdb?compressors=disabled&gssapiServiceName=mongodbImplicit session: session { "id" : UUID("a30dbd64-7b59-4a8e-b95d-02ff30e256f3") }MongoDB server version: 4.4.1> show dbs> show tables> |
以上就是在mongodb中开启访问控制,创建用户,授权的操作;我们只需要在配置文件中指定开启认证功能,然后使用具有创建用户权限的用户登录数据库创建用户授权即可;

 简单讲访问控制就是指,哪些用户可以访问哪些资源,对资源有哪些操作(权限);在mongodb中我们把数据库、或者集合叫做资源;也就说访问控制是用来限制某些用户对数据库或集合的操作;我们在mysql数据库中,我们通过给账号授权的方式达到控制哪些用户可以从哪些主机访问数据库,对数据库有哪些操作;其中账号由用户名称和主机地址构成;在mongodb中采用的不是用户+主机地址的方式,而是通过给用户赋予一个或多个角色,这个角色或多个角色的所有权限就是这个用户拥有的权限;默认情况mongodb是没有启用访问控制的,所以只要能够连接上mongodb实例,我们就可以在其上做任何操作,在某种程度上,这是一种极为不安全的方式,为了杜绝这种不安全的访问方式,我们需要对mongodb进行访问控制;
简单讲访问控制就是指,哪些用户可以访问哪些资源,对资源有哪些操作(权限);在mongodb中我们把数据库、或者集合叫做资源;也就说访问控制是用来限制某些用户对数据库或集合的操作;我们在mysql数据库中,我们通过给账号授权的方式达到控制哪些用户可以从哪些主机访问数据库,对数据库有哪些操作;其中账号由用户名称和主机地址构成;在mongodb中采用的不是用户+主机地址的方式,而是通过给用户赋予一个或多个角色,这个角色或多个角色的所有权限就是这个用户拥有的权限;默认情况mongodb是没有启用访问控制的,所以只要能够连接上mongodb实例,我们就可以在其上做任何操作,在某种程度上,这是一种极为不安全的方式,为了杜绝这种不安全的访问方式,我们需要对mongodb进行访问控制;



· PostgreSQL 和 SQL Server 在统计信息维护中的关键差异
· C++代码改造为UTF-8编码问题的总结
· DeepSeek 解答了困扰我五年的技术问题
· 为什么说在企业级应用开发中,后端往往是效率杀手?
· 用 C# 插值字符串处理器写一个 sscanf
· [翻译] 为什么 Tracebit 用 C# 开发
· 腾讯ima接入deepseek-r1,借用别人脑子用用成真了~
· Deepseek官网太卡,教你白嫖阿里云的Deepseek-R1满血版
· DeepSeek崛起:程序员“饭碗”被抢,还是职业进化新起点?
· RFID实践——.NET IoT程序读取高频RFID卡/标签