2021.8.12CTF刷题
rsa
RSA 加密原理

公钥=(E , N)
私钥=(D, N)
对外,我们只暴露公钥。



一:


答案:
125631357777427553
二:
题目:
Math is cool! Use the RSA algorithm to decode the secret message, c, p, q, and e are parameters for the RSA algorithm.
p = 9648423029010515676590551740010426534945737639235739800643989352039852507298491399561035009163427050370107570733633350911691280297777160200625281665378483
q = 11874843837980297032092405848653656852760910154543380907650040190704283358909208578251063047732443992230647903887510065547947313543299303261986053486569407
e = 65537
c = 83208298995174604174773590298203639360540024871256126892889661345742403314929861939100492666605647316646576486526217457006376842280869728581726746401583705899941768214138742259689334840735633553053887641847651173776251820293087212885670180367406807406765923638973161375817392737747832762751690104423869019034
Use RSA to find the secret message
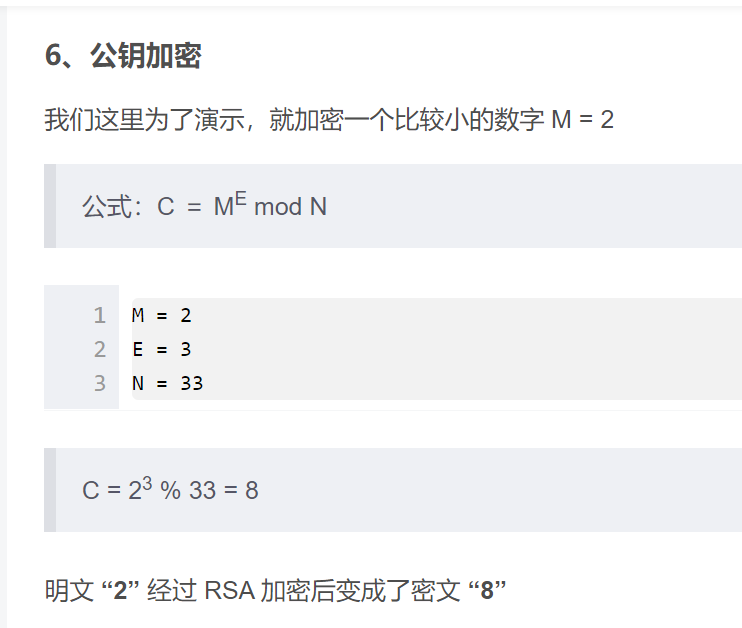
先用工具求出d
注意:题目中的e是十进制,在RSA Tool2中要改为16进制
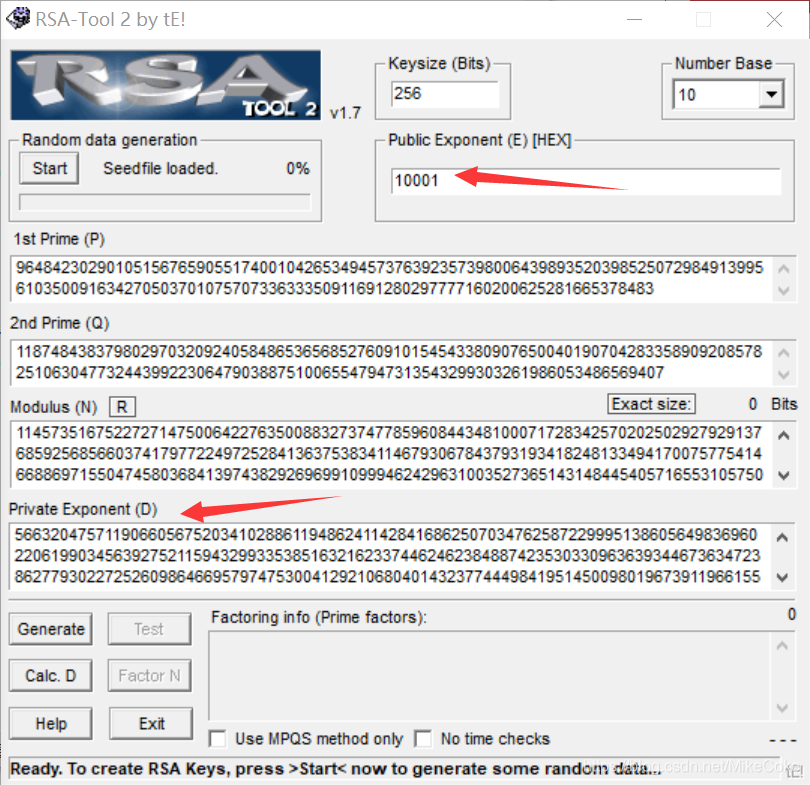
再用python函数pow()即可求出flag
e = 65537 p = 9648423029010515676590551740010426534945737639235739800643989352039852507298491399561035009163427050370107570733633350911691280297777160200625281665378483 q = 11874843837980297032092405848653656852760910154543380907650040190704283358909208578251063047732443992230647903887510065547947313543299303261986053486569407 n = p*q #密文 C = 83208298995174604174773590298203639360540024871256126892889661345742403314929861939100492666605647316646576486526217457006376842280869728581726746401583705899941768214138742259689334840735633553053887641847651173776251820293087212885670180367406807406765923638973161375817392737747832762751690104423869019034 d = 56632047571190660567520341028861194862411428416862507034762587229995138605649836960220619903456392752115943299335385163216233744624623848874235303309636393446736347238627793022725260986466957974753004129210680401432377444984195145009801967391196615524488853620232925992387563270746297909112117451398527453977 #求明文 M = pow(C,d,n) #快速求幂取模运算 print(M)
答案:
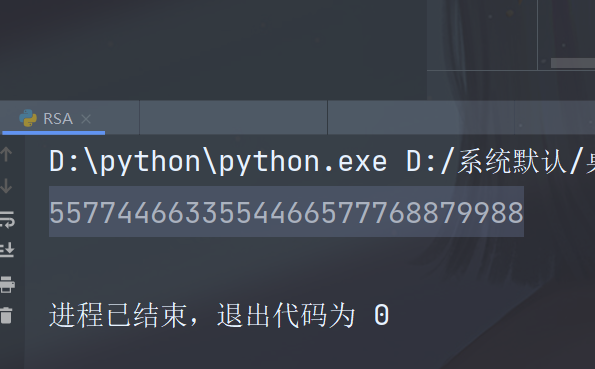
flag{5577446633554466577768879988}
三:
类型:Basic题目名称:easy RSA
题目内容:
已知一段加密的信息为:0xdc2eeeb2782c,且已知加密所用的公钥:(N=322831561921859 e = 23)
请解密出明文,提交时请将数字转化成ascii码提交,比如你解出的明文是0x6162,请提交字符串ab
提交格式:PCTF{明文字符串}
目前已知的是n、e和密文c,
所以我们可以先将n进行分解,分解成p和q
用下面这个在线分解素数的网站
factordb
http://factordb.com/index.php?query=322831561921859
再用工具求出d
然后用python求出明文M
最后转为string
答案:
PCTF{3a5Y}
四:
题目:
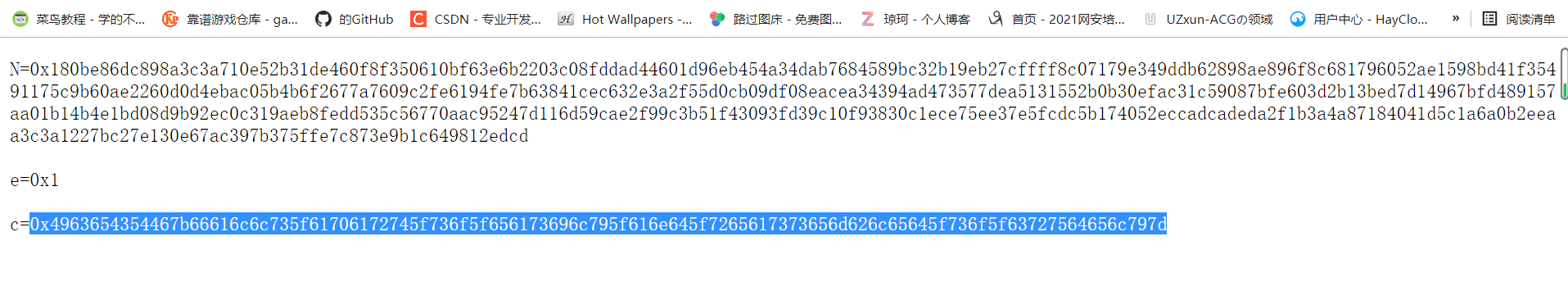
题目给出了N,e,和c。 尝试一下N是否已经被分解过。
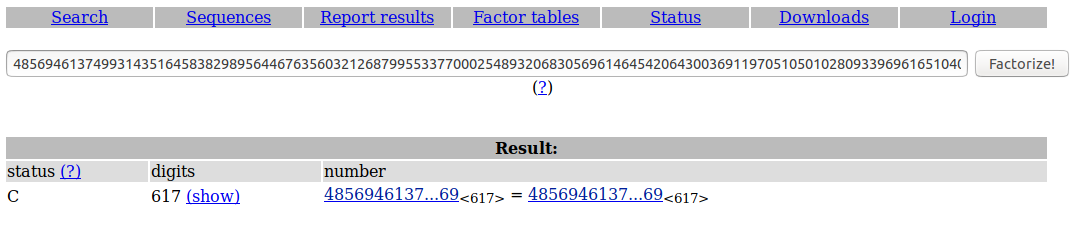
看到分解N的方法行不通。 这时候注意到 e =1。
这时候加密的过程实际为 c = m^e = m ^ 1 = m mod N。
也就是说消息m的数值形式对N取模的余数是密文c。 消息与密文的关系为 m = c + N*k (k=0,1,2,3...)
2. 解题步骤
从0开始选择不同的k尝试16进制解码,如果得出的为可读明文即证明我们找到flag。
k = 0 : 解码得出
m=c
说明密文等于明文,于是将密文十六进制解码可得
答案:
IceCTF{falls_apart_so_easily_and_reassembled_so_crudely}
五:
d = 0x12314d6d6327261ee18a7c6ce8562c304c05069bc8c8e0b34e0023a3b48cf5849278d3493aa86004b02fa6336b098a3330180b9b9655cdf927896b22402a18fae186828efac14368e0a5af2c4d992cb956d52e7c9899d9b16a0a07318aa28c8202ebf74c50ccf49a6733327dde111393611f915f1e1b82933a2ba164aff93ef4ab2ab64aacc2b0447d437032858f089bcc0ddeebc45c45f8dc357209a423cd49055752bfae278c93134777d6e181be22d4619ef226abb6bfcc4adec696cac131f5bd10c574fa3f543dd7f78aee1d0665992f28cdbcf55a48b32beb7a1c0fa8a9fc38f0c5c271e21b83031653d96d25348f8237b28642ceb69f0b0374413308481
c=0x126c24e146ae36d203bef21fcd88fdeefff50375434f64052c5473ed2d5d2e7ac376707d76601840c6aa9af27df6845733b9e53982a8f8119c455c9c3d5df1488721194a8392b8a97ce6e783e4ca3b715918041465bb2132a1d22f5ae29dd2526093aa505fcb689d8df5780fa1748ea4d632caed82ca923758eb60c3947d2261c17f3a19d276c2054b6bf87dcd0c46acf79bff2947e1294a6131a7d8c786bed4a1c0b92a4dd457e54df577fb625ee394ea92b992a2c22e3603bf4568b53cceb451e5daca52c4e7bea7f20dd9075ccfd0af97f931c0703ba8d1a7e00bb010437bb4397ae802750875ae19297a7d8e1a0a367a2d6d9dd03a47d404b36d7defe8469
N=0x1564aade6f1b9f169dcc94c9787411984cd3878bcd6236c5ce00b4aad6ca7cb0ca8a0334d9fe0726f8b057c4412cfbff75967a91a370a1c1bd185212d46b581676cf750c05bbd349d3586e78b33477a9254f6155576573911d2356931b98fe4fec387da3e9680053e95a4709934289dc0bc5cdc2aa97ce62a6ca6ba25fca6ae38c0b9b55c16be0982b596ef929b7c71da3783c1f20557e4803de7d2a91b5a6e85df64249f48b4cf32aec01c12d3e88e014579982ecd046042af370045f09678c9029f8fc38ebaea564c29115e19c7030f245ebb2130cbf9dc1c340e2cf17a625376ca52ad8163cfb2e33b6ecaf55353bc1ff19f8f4dc7551dc5ba36235af9758b
解题步骤
打开文件后看到有好几个参数,除了有正常的N,e,c外,还有d。 直接上python


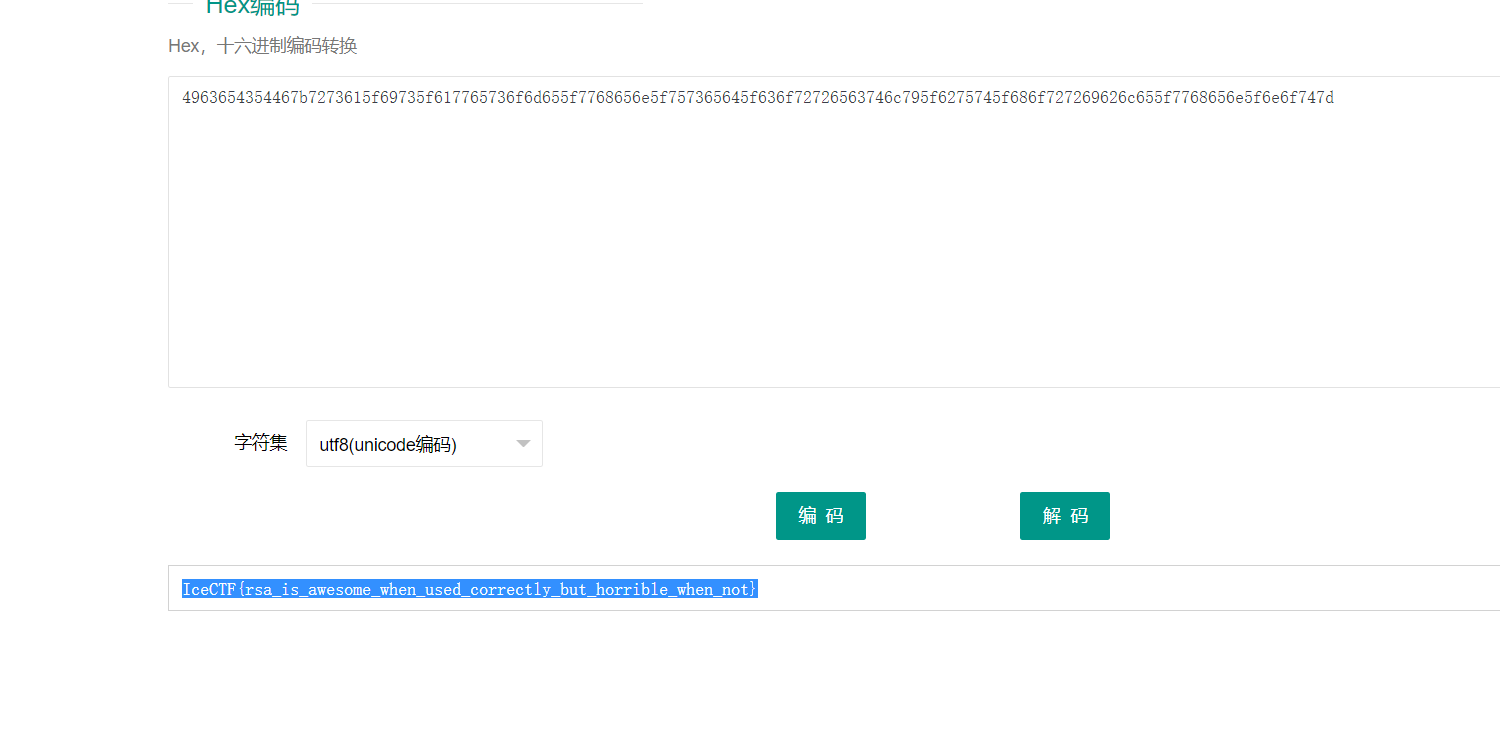
答案:IceCTF{rsa_is_awesome_when_used_correctly_but_horrible_when_not}


