实战Pikachu暴力破解
暴力破解
使用工具:burp suite
暴力破解介绍
暴力破解是一攻击具手段,在web攻击中,一般会使用这种手段对应用系统的认证信息进行获取。 其过程就是使用大量的认证信息在认证接口进行尝试登录,直到得到正确的结果。 为了提高效率,暴力破解一般会使用带有字典的工具来进行自动化操作。
理论上来说,大多数系统都是可以被暴力破解的,只要攻击者有足够强大的计算能力和时间,所以断定一个系统是否存在暴力破解漏洞,其条件也不是绝对的。 我们说一个web应用系统存在暴力破解漏洞,一般是指该web应用系统没有采用或者采用了比较弱的认证安全策略,导致其被暴力破解。
认证防御策略包括:
是否要求用户设置复杂的密码
是否每次认证都使用安全的验证码
是否对尝试登录的行为进行判断和限制(如:过去15分钟内有五次错误登录,则锁定的用户将无法登录。)
如果锁定的用户尝试使用有效密码登录,即使密码有效,也会显示其用户名或密码不正确。这将使得无法知道系统上是否有使用该密码的有效帐户以及该帐户是否被锁定。
是否采用了双因素认证等
1、基于表单的暴力破解
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR.'inc/config.inc.php'; include_once $PIKA_ROOT_DIR.'inc/mysql.inc.php'; $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "bf_form.php"){ $ACTIVE = array('','active open','','active',"","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","",""); } include_once $PIKA_ROOT_DIR.'header.php'; $link=connect(); $html=""; //典型的问题,没有验证码,没有其他控制措施,可以暴力破解 if(isset($_POST['submit']) && $_POST['username'] && $_POST['password']){ $username = $_POST['username']; $password = $_POST['password']; $sql = "select * from users where username=? and password=md5(?)"; $line_pre = $link->prepare($sql); $line_pre->bind_param('ss',$username,$password); if($line_pre->execute()){ $line_pre->store_result(); if($line_pre->num_rows>0){ $html.= '<p> login success</p>'; } else{ $html.= '<p> username or password is not exists~</p>'; } } else{ $html.= '<p>执行错误:'.$line_pre->errno.'错误信息:'.$line_pre->error.'</p>'; } } ?> <div class="main-content" xmlns="http://www.w3.org/1999/html"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="burteforce.php">暴力破解</a> </li> <li class="active">基于表单的暴力破解</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="这里一共有三个用户: admin/123456 pikachu/000000 test/abc123"> 点一下提示~ </a> </div> <div class="page-content"> <div class="bf_form"> <div class="bf_form_main"> <h4 class="header blue lighter bigger"> <i class="ace-icon fa fa-coffee green"></i> Please Enter Your Information </h4> <form method="post" action="bf_form.php"> <!-- <fieldset>--> <label> <span> <input type="text" name="username" placeholder="Username" /> <i class="ace-icon fa fa-user"></i> </span> </label> </br> <label> <span> <input type="password" name="password" placeholder="Password" /> <i class="ace-icon fa fa-lock"></i> </span> </label> <div class="space"></div> <div class="clearfix"> <label><input class="submit" name="submit" type="submit" value="Login" /></label> <!-- <button type="button" name="submit">--> <!-- <i class="ace-icon fa fa-key"></i>--> <!-- <span class="bigger-110">Login</span>--> <!-- </button>--> </div> </form> <?php echo $html;?> </div><!-- /.widget-main --> </div><!-- /.widget-body --> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR.'footer.php'; ?>
源码分析:
允许任何人尝试任意次数尝试,登录到任何用户而不会造成任何影响
查找漏洞步骤与方法:
- 前端页面没有验证码字段,打开浏览器开发者模式查看源码也没有生成验证码代码
- 使用burp抓包,输入任意用户名和密码点击登录后,burp中将抓包数据发送到Repeater(重发器)
- Repeater(重发器)中重复几次发送,查看响应Rerder标签中都提示用户名或密码错误,说明防暴力破解,将数据包发送到(lntruder测试器)中进行爆破
攻击爆破(lntruder测试器)
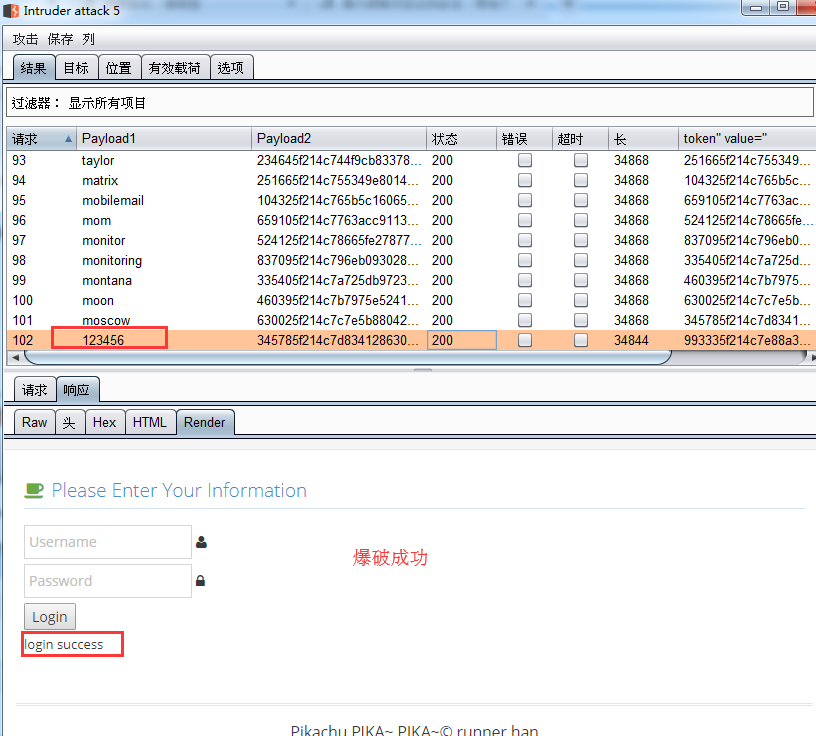
- 如果用户名和密码都不知道:同时爆破用户名和密码,攻击类型选择Pitchfork(交叉),有效载荷中分别加载用户名和密码字典。
- 如果知道用户名而不知道密码,只需要爆破密码,攻击类选择默认(Sniper),有效载荷中导入密码字典。
- 如图爆出用户名:admin 密码:123456
2、验证码绕过(on server)
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR.'inc/config.inc.php'; include_once $PIKA_ROOT_DIR.'inc/mysql.inc.php'; $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "bf_server.php"){ $ACTIVE = array('','active open','','','active',"","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","",""); } include_once $PIKA_ROOT_DIR.'header.php'; $link=connect(); $html=""; if(isset($_POST['submit'])) { if (empty($_POST['username'])) { $html .= "<p class='notice'>用户名不能为空</p>"; } else { if (empty($_POST['password'])) { $html .= "<p class='notice'>密码不能为空</p>"; } else { if (empty($_POST['vcode'])) { $html .= "<p class='notice'>验证码不能为空哦!</p>"; } else { // 验证验证码是否正确 if (strtolower($_POST['vcode']) != strtolower($_SESSION['vcode'])) { $html .= "<p class='notice'>验证码输入错误哦!</p>"; //应该在验证完成后,销毁该$_SESSION['vcode'] }else{ $username = $_POST['username']; $password = $_POST['password']; $vcode = $_POST['vcode']; $sql = "select * from users where username=? and password=md5(?)"; $line_pre = $link->prepare($sql); $line_pre->bind_param('ss',$username,$password); if($line_pre->execute()){ $line_pre->store_result(); //虽然前面做了为空判断,但最后,却没有验证验证码!!! if($line_pre->num_rows()==1){ $html.='<p> login success</p>'; }else{ $html.= '<p> username or password is not exists~</p>'; } }else{ $html.= '<p>执行错误:'.$line_pre->errno.'错误信息:'.$line_pre->error.'</p>'; } } } } } } ?> <div class="main-content" xmlns="http://www.w3.org/1999/html"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="burteforce.php">暴力破解</a> </li> <li class="active">验证码绕过(on server)</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="这个验证码好像一直有效哎!用户还是那三个默认用户."> 点一下提示~ </a> </div> <div class="page-content"> <div class="bf_form"> <div class="bf_form_main"> <h4 class="header blue lighter bigger"> <i class="ace-icon fa fa-coffee green"></i> Please Enter Your Information </h4> <form method="post" action="bf_server.php"> <!-- <fieldset>--> <label> <span> <input type="text" name="username" placeholder="Username" /> <i class="ace-icon fa fa-user"></i> </span> </label> </br> <label> <span> <input type="password" name="password" placeholder="Password" /> <i class="ace-icon fa fa-lock"></i> </span> </label> </br> <label> <span> <input type="text" name="vcode" placeholder="验证码" /> <i class="ace-icon fa fa-lock"></i> </span> </label> </br> <label> <img src="../../inc/showvcode.php" onclick="this.src='../../inc/showvcode.php?'+new Date().getTime();" /> </label> <div class="space"></div> <div class="clearfix"> <label><input class="submit" name="submit" type="submit" value="Login" /></label> </div> </form> <?php echo $html;?> </div><!-- /.widget-main --> </div><!-- /.widget-body --> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR.'footer.php'; ?>
源码分析:
验证码在完成验证后没有销毁,导致只要输入正确的验证码就可以无限制使用。php默认23分钟后才能自动销毁。
查找漏洞步骤与方法:
- 在登录页面输入任意用户名和密码,输入正确的验证码,点击提交发现提示用户名或密码错误
- 开启burp抓包,登录页面输入任意用户名、密码、正确验证码点击登录,burp中将抓取的数据表发送到Repeater(重发器),原来拦截的数据包一定要【弃包】要不然在重发器会提示验证码错误。
- Repeater(重发器)中重复几次发送,查看响应Rerder标签中都提示用户名或密码错误,说明验证码未销毁,将数据包发送到(lntruder测试器)中进行爆破
攻击爆破(lntruder测试器):
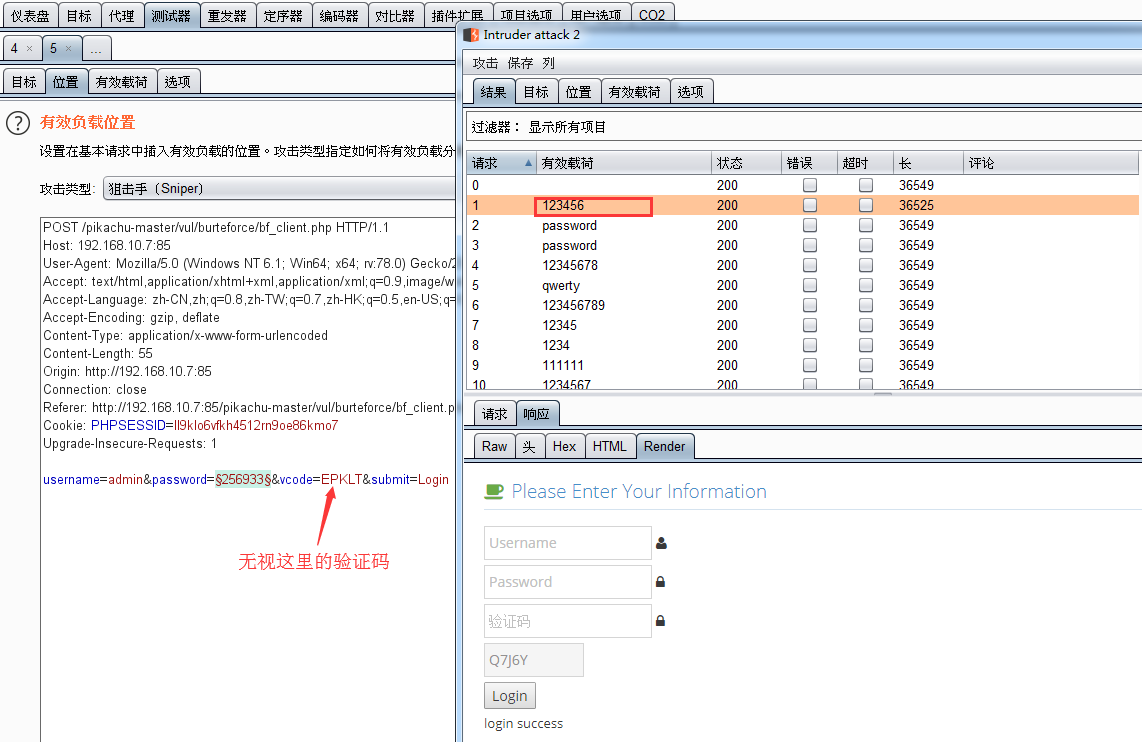
- 设置变量、选择攻击类型Sniper、导入有效载荷
- 如图:爆出用户名:admin 密码:123456
3、验证码绕过(on client)
前端生成验证码源码:

<script language="javascript" type="text/javascript">
var code; //在全局 定义验证码
function createCode() {
code = "";
var codeLength = 5;//验证码的长度
var checkCode = document.getElementById("checkCode");
var selectChar = new Array(0, 1, 2, 3, 4, 5, 6, 7, 8, 9,'A','B','C','D','E','F','G','H','I','J','K','L','M','N','O','P','Q','R','S','T','U','V','W','X','Y','Z');//所有候选组成验证码的字符,当然也可以用中文的
for (var i = 0; i < codeLength; i++) {
var charIndex = Math.floor(Math.random() * 36);
code += selectChar[charIndex];
}
//alert(code);
if (checkCode) {
checkCode.className = "code";
checkCode.value = code;
}
}
function validate() {
var inputCode = document.querySelector('#bf_client .vcode').value;
if (inputCode.length <= 0) {
alert("请输入验证码!");
return false;
} else if (inputCode != code) {
alert("验证码输入错误!");
createCode();//刷新验证码
return false;
}
else {
return true;
}
}
createCode();
</script>
源码分析验:
验证码由前端代码生成,使用burp抓包直接绕过
查找漏洞步骤与方法:
- 打开浏览器的开发者工具,查看前端代码发现:<input type="text" onclick="createCode()" readonly="readonly" id="checkCode" class="code" style="width: 100px">说明验证码是前端js生成
- 开启burp抓包,前端页面中输入任意用户名、密码,正确验证码后点击登录。burp中将抓取的数据包发送到Repeater(重发器)
- Repeater(重发器)中重复几次发送,查看响应Rerder标签中都提示用户名或密码错误,说明验证码无效
攻击爆破(lntruder测试器)
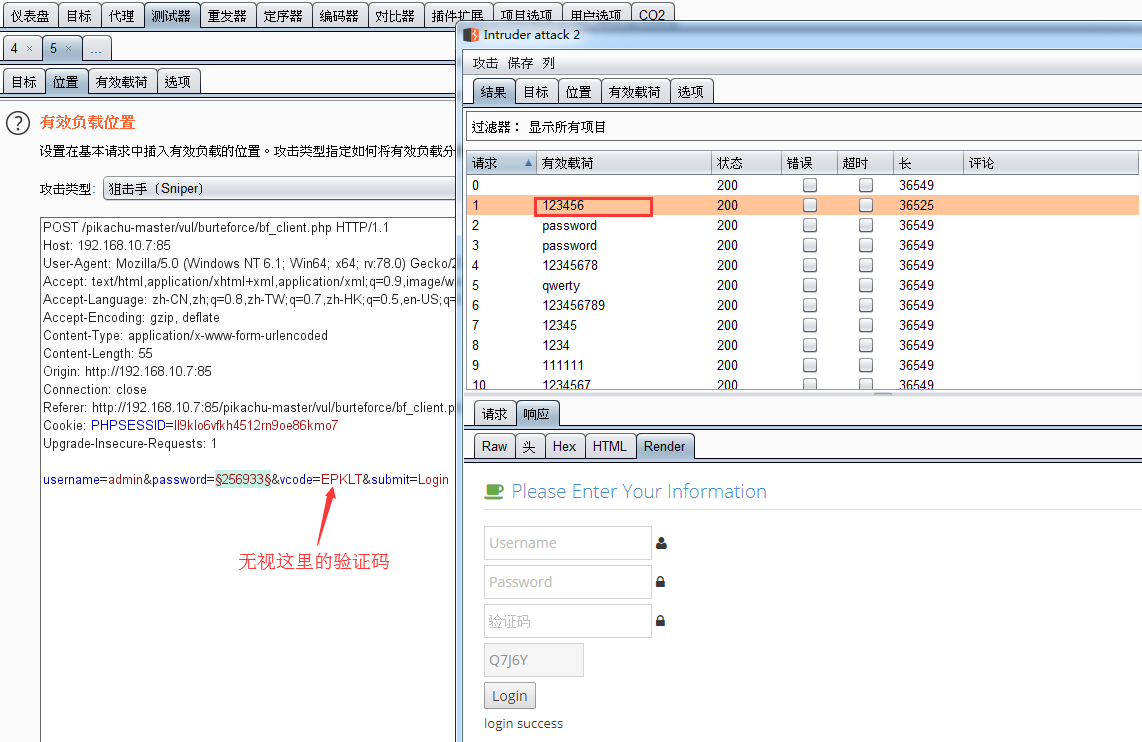
- 发送到攻击爆破(lntruder测试器)进行爆破
- 如图爆出用户名:admin 密码:123456

4、token防爆破
源码:

<?php /** * Created by runner.han * There is nothing new under the sun */ $PIKA_ROOT_DIR = "../../"; include_once $PIKA_ROOT_DIR.'inc/config.inc.php'; include_once $PIKA_ROOT_DIR.'inc/mysql.inc.php'; include_once $PIKA_ROOT_DIR.'inc/function.php'; $SELF_PAGE = substr($_SERVER['PHP_SELF'],strrpos($_SERVER['PHP_SELF'],'/')+1); if ($SELF_PAGE = "bf_client.php"){ $ACTIVE = array('','active open','','','','','active',"","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","","",""); } include_once $PIKA_ROOT_DIR.'header.php'; $link=connect(); $html=""; if(isset($_POST['submit']) && $_POST['username'] && $_POST['password'] && $_POST['token']==$_SESSION['token']){ $username = $_POST['username']; $password = $_POST['password']; $sql = "select * from users where username=? and password=md5(?)"; $line_pre = $link->prepare($sql); $line_pre->bind_param('ss',$username,$password); if($line_pre->execute()){ $line_pre->store_result(); if($line_pre->num_rows>0){ $html.= '<p> login success</p>'; } else{ $html.= '<p> username or password is not exists~</p>'; } } else{ $html.= '<p>执行错误:'.$line_pre->errno.'错误信息:'.$line_pre->error.'</p>'; } } //生成token set_token(); ?> <div class="main-content" xmlns="http://www.w3.org/1999/html"> <div class="main-content-inner"> <div class="breadcrumbs ace-save-state" id="breadcrumbs"> <ul class="breadcrumb"> <li> <i class="ace-icon fa fa-home home-icon"></i> <a href="burteforce.php">暴力破解</a> </li> <li class="active">token防爆破?</li> </ul><!-- /.breadcrumb --> <a href="#" style="float:right" data-container="body" data-toggle="popover" data-placement="bottom" title="tips(再点一下关闭)" data-content="token了解下,后面搞CSRF会用到....虽然这里并没有什么鸟用."> 点一下提示~ </a> </div> <div class="page-content"> <div class="bf_form"> <div class="bf_form_main"> <h4 class="header blue lighter bigger"> <i class="ace-icon fa fa-coffee green"></i> Please Enter Your Information </h4> <form id="bf_client" method="post" action="bf_token.php" "> <!-- <fieldset>--> <label> <span> <input type="text" name="username" placeholder="Username" /> <i class="ace-icon fa fa-user"></i> </span> </label> </br> <label> <span> <input type="password" name="password" placeholder="Password" /> <i class="ace-icon fa fa-lock"></i> </span> </label> </br> <input type="hidden" name="token" value="<?php echo $_SESSION['token'];?>" /> <label><input class="submit" name="submit" type="submit" value="Login" /></label> </form> <?php echo $html;?> </div><!-- /.widget-main --> </div><!-- /.widget-body --> </div><!-- /.page-content --> </div> </div><!-- /.main-content --> <?php include_once $PIKA_ROOT_DIR.'footer.php'; ?>
源码分析:
token对暴力破解没有什么用
查找漏洞步骤与方法:
- 通过浏览器开发者工具查看前端代码,发现使用了token进行防暴力破解:<input type="hidden" name="token" value="647585f2147a259f81752151326">
- 开启burp抓包,登录页面输入任意用户名、密码、正确验证码点击登录,burp中将抓取的数据表发送到Repeater(重发器)
- Repeater(重发器)中重复几次发送,发现需要验证token,我们抓包的token已经失效
攻击爆破(lntruder测试器)
密码和toekn添加变量,攻击类型选择 Pitchfork(交叉)
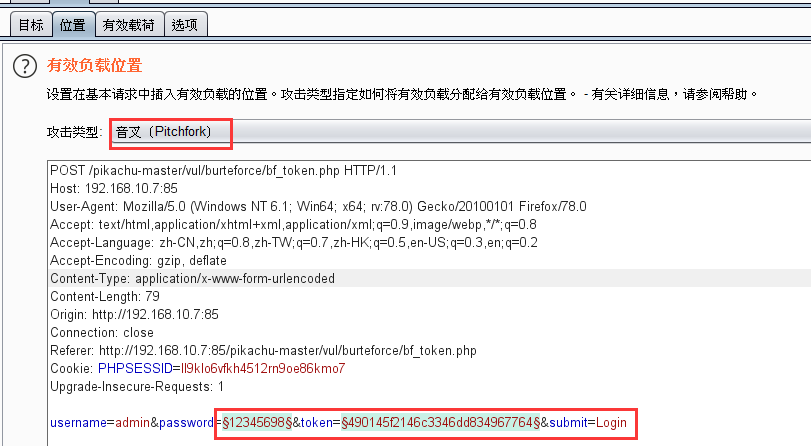
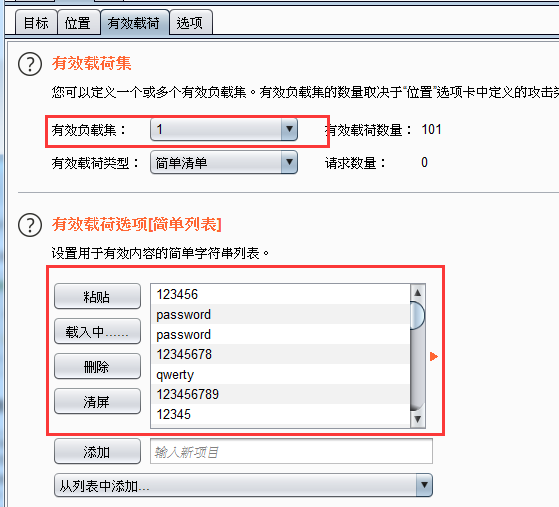
有效载荷
有效负载集1:导入密码字典
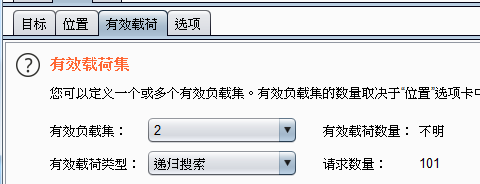
有效负载集:2 类型选择:递归搜索
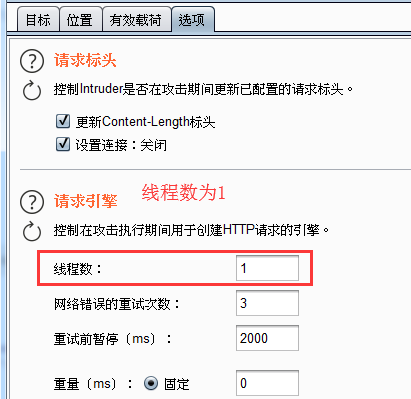
切换到选项:
设置获取响应中toekn的规则:

线程数设置:1
如图爆破成功:用户名:admin 密码:123456