NetCore Ocelot 之 Authorization
Ocelot supports claims based authorization which is run post authentication. This means if ou have a route you want to authorize you can add the following to you Route configuration.
"RouteClaimsRequirement": {
"client_role": "admin"
}
Add the Authorization middlware to request pipeline.
app.UseOcelot().Wait();
app.UseAuthentication();
app.UseAuthorization();
if the request access token with the claim type: 'client_role' and value is 'admin', the user will be authorized.
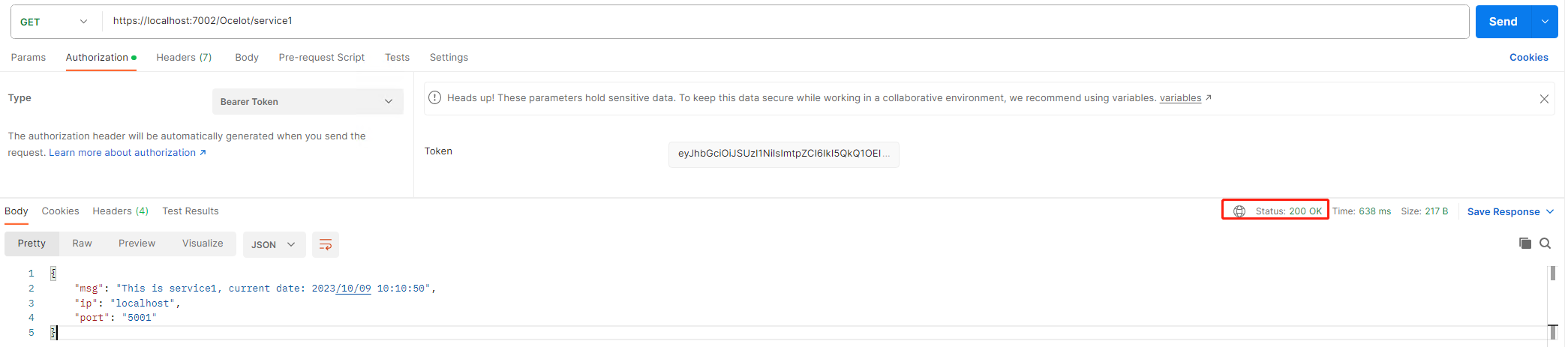
The access token is bellow
{
"nbf": 1696813802,
"exp": 1696817402,
"iss": "https://localhost:9000",
"aud": [
"APIResource1",
"APIResource2"
],
"client_id": "clientId",
"client_role": "admin",
"client_nickname": "tom",
"client_Emai": "tom@163.com",
"jti": "EB792F9B19537B4ACC28B76FD5588804",
"iat": 1696813802,
"scope": [
"apiscope1",
"apiscope2"
]
}
IdentityServer4 ClientClaim configuration
Claims = new List<ClientClaim> { new ClientClaim(IdentityModel.JwtClaimTypes.Role,"admin"), new ClientClaim(IdentityModel.JwtClaimTypes.NickName,"tom"), new ClientClaim("Emai","tom@163.com") }
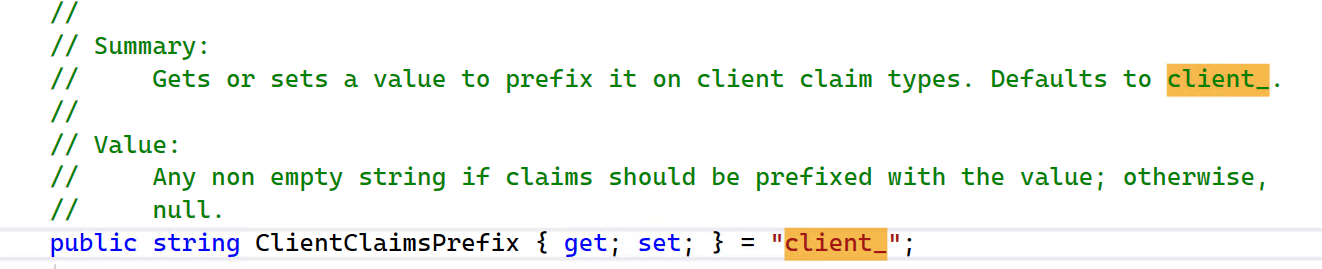
And why the generated claim type with the client_ prefix, it's the default value configured in IdentityServer4.Model.Client, you can change and override the default prefix or set to empty.
OK, that's all the Authorization process, so easy.
分类:
微服务系列
, ASP.NET Core






【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 无需6万激活码!GitHub神秘组织3小时极速复刻Manus,手把手教你使用OpenManus搭建本
· C#/.NET/.NET Core优秀项目和框架2025年2月简报
· Manus爆火,是硬核还是营销?
· 终于写完轮子一部分:tcp代理 了,记录一下
· 【杭电多校比赛记录】2025“钉耙编程”中国大学生算法设计春季联赛(1)