用harbor搭建自己的镜像库
节点一:Ubuntu 20.04.4 harbor+docker 节点二:Ubuntu 20.04.4 kerbernetes集群的master节点
harbor版本包:harbor-offline-installer-v2.5.0.tgz
1、解压harbor包,cd harbor目录
2、harbor默认配置文件示例是这个harbor.yml.tmpl,复制一份修改
cp harbor.yml.tmpl harbor.yml;vim harbor.yml
1 hostname: reg.k8smaster.org 2 3 http: 4 port: 80 5 6 https: 7 port: 443 8 certificate: /data/certs/k8smaster.org.crt 9 private_key: /data/certs/k8smaster.org.key 10 11 harbor_admin_password: yesterday 12 13 database: 14 password: root123 15 max_idle_conns: 100 16 max_open_conns: 900 17 18 data_volume: /data 19 20 trivy: 21 ignore_unfixed: false 22 skip_update: false 23 offline_scan: false 24 insecure: false 25 26 jobservice: 27 max_job_workers: 10 28 29 notification: 30 webhook_job_max_retry: 10 31 32 chart: 33 absolute_url: disabled 34 log: 35 level: info 36 local: 37 rotate_count: 50 38 rotate_size: 200M 39 location: /var/log/harbor 40 41 _version: 2.5.0 42 43 proxy: 44 http_proxy: 45 https_proxy: 46 no_proxy: 47 components: 48 - core 49 - jobservice 50 - trivy 51 52 upload_purging: 53 enabled: true 54 age: 168h 55 interval: 24h 56 dryrun: false
3、生成自签名证书
openssl req -newkey rsa:4096 -nodes -sha256 -keyout /data/certs/k8smaster.org.key -addext "subjectAltName = DNS:reg.k8smaster.org" -x509 -days 365 -out /data/certs/k8smaster.org.crt
root@kubemaster:/data/certs# ll
total 32
drwxr-xr-x 2 root root 4096 Jun 16 22:12 ./
drwxr-xr-x 9 root root 4096 May 5 22:39 ../
-rw-r--r-- 1 root root 2082 Jun 16 22:12 harbor.org.crt
-rw------- 1 root root 3272 Jun 16 22:08 harbor.org.key
-rw-r--r-- 1 root root 2175 May 5 22:39 k8smaster.org.crt
-rw------- 1 root root 3272 May 5 22:37 k8smaster.org.key
-rw-r--r-- 1 root root 2191 May 5 22:23 mydomain.com.crt
-rw------- 1 root root 3272 May 5 22:21 mydomain.com.key
4、安装harbor
cd harbor目录
./install.sh --with-notary --with-trivy --with-chartmuseum
成功就这样:
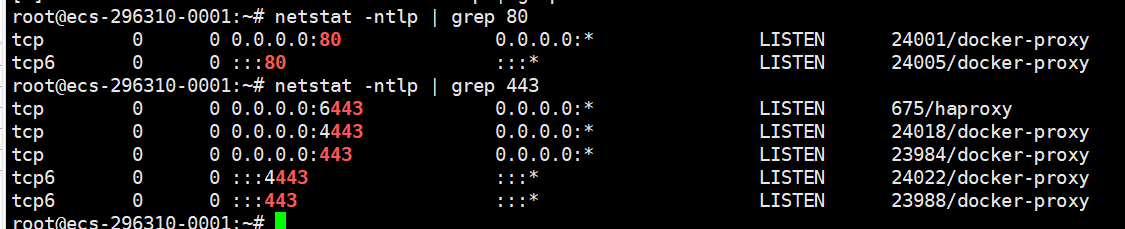
5、添加域名到hosts文件
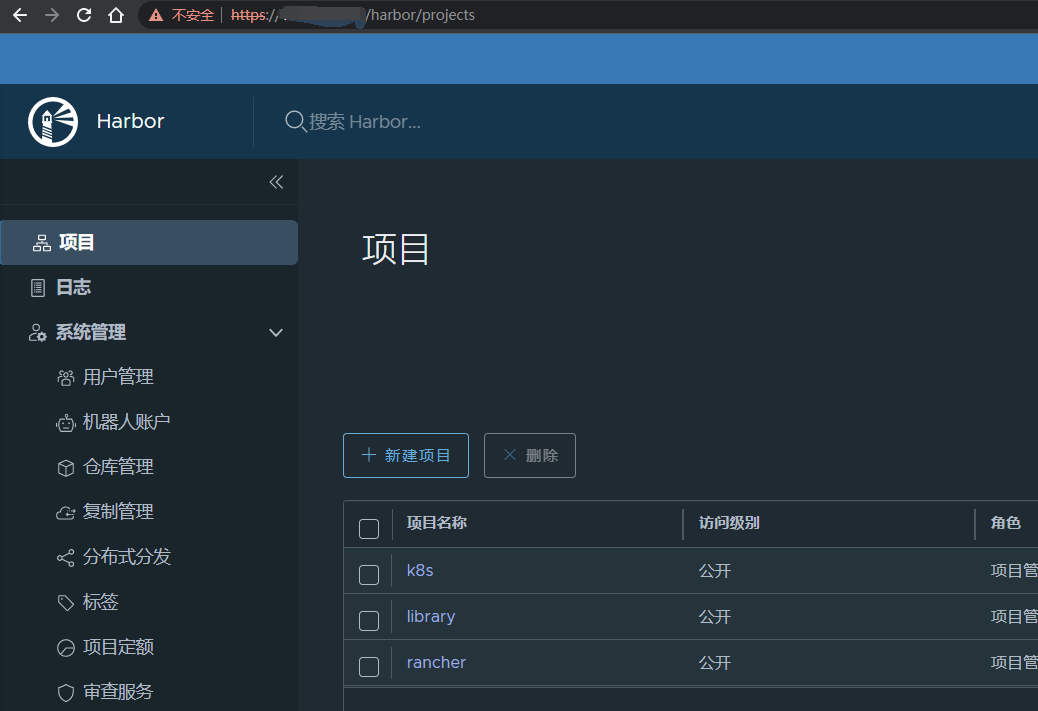
6、web测试 harbor服务器ip,登录进来就这样吧
6、使用docker上传镜像时需要配置证书
mkdir -p /etc/docker/certs.d/reg.k8smaster.org
cp /data/certs/k8smaster.org.crt /etc/docker/certs.d/reg.k8smaster.org
docker login reg.k8smaster.org #命令行上传之前西安登录harbor
7、harbor镜像的上传zabbix为例
docker search zabbix
docker pull zabbix/zabbix-agent
docker tag zabbix/zabbix-agent:latest reg.k8smaster.org/library/zabbix/zabbix-agent:latest
docker push reg.k8smaster.org/library/zabbix/zabbix-agent:latest
传完仓库就这样
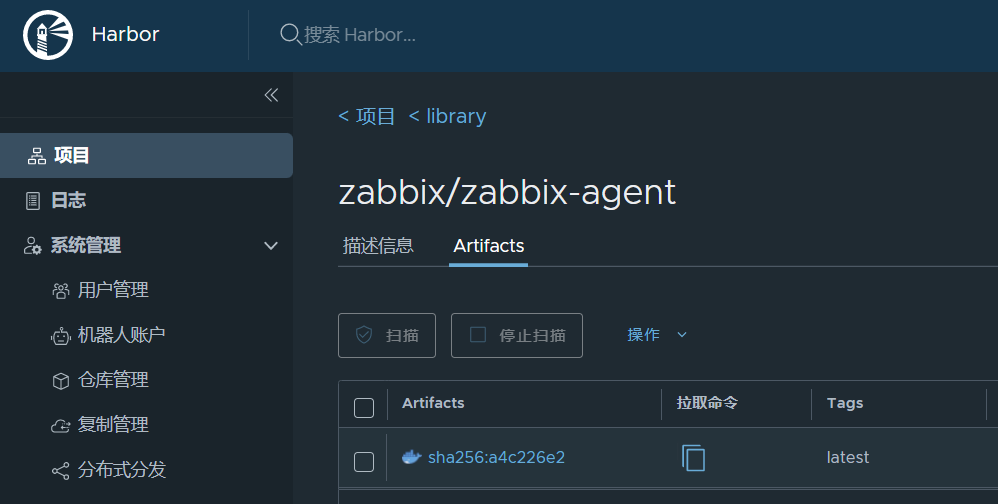
7,k8s的容器访问harbor配置
k8s节点上操作,使用containerd容器
# mkdir -p /etc/containerd/certs.d/reg.k8smaster.org
# scp harbor服务器ip:/data/certs/k8smaster.org.crt /etc/containerd/certs.d/reg.k8smaster.org
# vim /etc/containerd/config.toml [plugins."io.containerd.grpc.v1.cri".registry] config_path = "/etc/containerd/certs.d" #指定证书路径
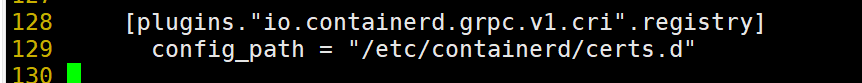
# systemctl restart containerd
# crictl pull reg.k8smaster.org/library/nginx:latest #测试拉取镜像
8、
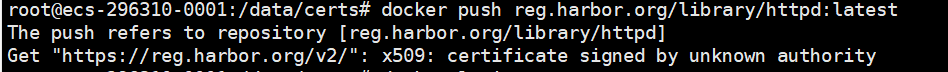
报错一截图;原因:docker没有login
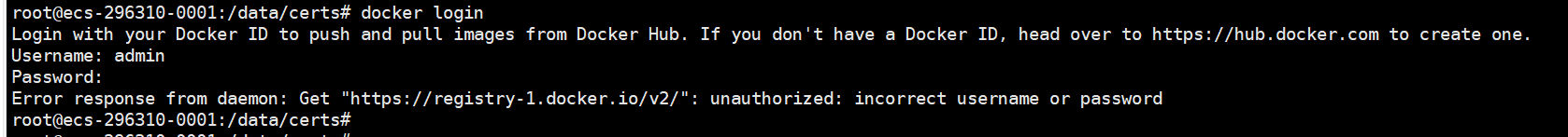
报错二截图;原因:docker没有导证书
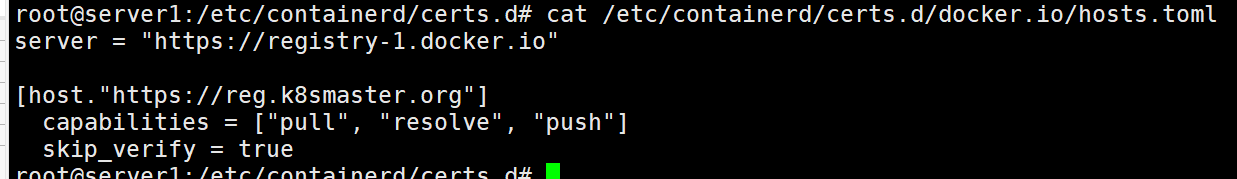
问题三:K8s节点上拉取镜像不加前缀,直接拉取镜像名称(设置默认仓库)的配置
# mkdir -p /etc/containerd/certs.d/docker.io
# vim /etc/containerd/certs.d/docker.io/hosts.toml server = "https://registry-1.docker.io" [host."https://reg.westos.org"] capabilities = ["pull", "resolve", "push"] skip_verify = true



 浙公网安备 33010602011771号
浙公网安备 33010602011771号