2021 DozerCTF
DozerCTF 2021
rank:1st
周末打了这个比赛,我AK了逆向方向,最后两道一血,其中一道唯一解。
下面放出我RE的wp

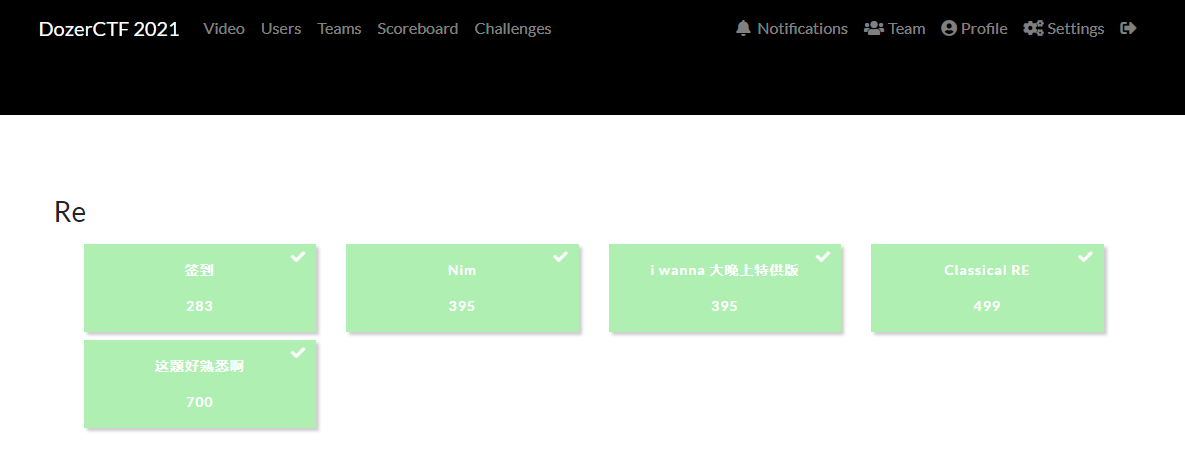
Re
签到
先跑程序:
Have you ever seen a total lunar eclipse? It would be a pity if you didn't see it on May 26
Do you want to know the flag?(yes/no)
yes
here is the flag
first way : -01256AELT_aceilnprstu
second way : T0-LA1526Eta_lcienrpsu
You have known too much. Find a third way
dont forget Dozerctf{}
md5{third way}:2ab8484a34cdb3c6e4bbb4910e4f1dbf
就是构造二叉树,给出前序遍历中序遍历,找后序遍历的结果。

Dozerctf{-2651EAL0_eicpsrnlautT}
I wanna be the Dozer
昨晚看到上题的消息就已经猜到有多简单了
早上起来秒了
gm8decompiler.exe直接反编译
双击打开工程文件,直接看背景文件
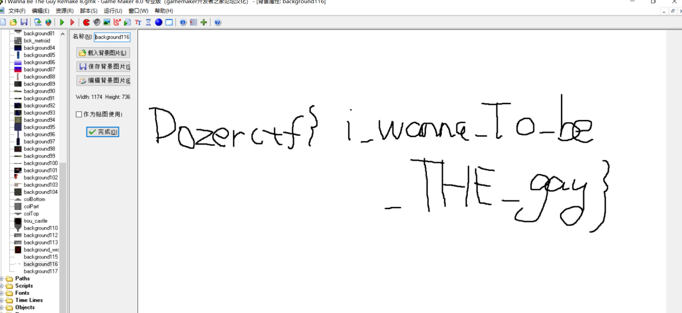
Dozerctf{i_wanna_To_be_THE_gay}
NIM

程序先解一串base64,然后进行des加密,动调发现密钥为DozerCTF。写脚本解密。
s=[ 0x4D, 0x48, 0x68, 0x43, 0x4F, 0x44, 0x46, 0x45, 0x4F, 0x54,
0x6C, 0x47, 0x4F, 0x44, 0x59, 0x34, 0x51, 0x6A, 0x59, 0x30,
0x4D, 0x55, 0x4D, 0x30, 0x4E, 0x30, 0x55, 0x30, 0x4E, 0x6A,
0x51, 0x79, 0x4D, 0x30, 0x45, 0x79, 0x51, 0x6B, 0x51, 0x32,
0x4F, 0x44, 0x41, 0x7A, 0x52, 0x45, 0x52, 0x46, 0x4D, 0x6B,
0x55, 0x33, 0x4D, 0x55, 0x4D, 0x78, 0x4F, 0x44, 0x51, 0x32,
0x51, 0x30, 0x51, 0x34, 0x52, 0x6A, 0x55, 0x35, 0x52, 0x6A,
0x55, 0x79, 0x4E, 0x44, 0x45, 0x35, 0x51, 0x54, 0x51, 0x34,
0x4F, 0x44, 0x6C, 0x47, 0x4D, 0x6B, 0x45, 0x77, 0x4D, 0x54,
0x51, 0x30, 0x4D, 0x45, 0x49, 0x34, 0x4F, 0x54, 0x6B, 0x77,
0x4F, 0x45, 0x55, 0x7A, 0x52, 0x44, 0x55, 0x35, 0x52, 0x44,
0x67, 0x34, 0x52, 0x44, 0x49, 0x77, 0x4D, 0x6A, 0x4D, 0x79,
0x4E, 0x54, 0x67, 0x78, 0x51, 0x6B, 0x59, 0x30, 0x4D, 0x55,
0x45, 0x7A, 0x4F, 0x54, 0x59, 0x7A, 0x4F, 0x55, 0x59, 0x78,
0x4E, 0x30, 0x55, 0x34, 0x52, 0x44, 0x41, 0x77, 0x4D, 0x7A,
0x45, 0x33, 0x4E, 0x6A, 0x63, 0x34, 0x52, 0x45, 0x4E, 0x44,
0x51, 0x54, 0x4D, 0x30, 0x52, 0x45, 0x45, 0x34, 0x51, 0x54,
0x42, 0x46, 0x4D, 0x7A, 0x45, 0x30, 0x4E, 0x44, 0x42, 0x43,
0x4F, 0x44, 0x6B, 0x35, 0x4D, 0x44, 0x68, 0x46, 0x4D, 0x30,
0x51, 0x31, 0x4F, 0x55, 0x51, 0x33, 0x52, 0x54, 0x67, 0x78,
0x4F, 0x54, 0x4A, 0x44, 0x51, 0x55, 0x49, 0x34, 0x51, 0x7A,
0x68, 0x47, 0x4E, 0x30, 0x4E, 0x45, 0x4F, 0x44, 0x6B, 0x7A,
0x4D, 0x54, 0x49, 0x7A, 0x4E, 0x44, 0x42, 0x45, 0x4D, 0x55,
0x59, 0x30, 0x4E, 0x44, 0x51, 0x30, 0x4F, 0x54, 0x64, 0x43,
0x4E, 0x54, 0x67, 0x77, 0x52, 0x6B, 0x4A, 0x45, 0x51, 0x54,
0x42, 0x45, 0x4D, 0x6B, 0x55, 0x31, 0x52, 0x6B, 0x56, 0x46,
0x4F, 0x54, 0x45, 0x7A, 0x51, 0x6A, 0x6C, 0x43, 0x4F, 0x54,
0x67, 0x32, 0x4E, 0x6A, 0x64, 0x47, 0x51, 0x55, 0x5A, 0x45,
0x4F, 0x55, 0x45, 0x32, 0x51, 0x54, 0x55, 0x79, 0x4F, 0x44,
0x59, 0x78, 0x51, 0x54, 0x55, 0x7A, 0x4E, 0x54, 0x64, 0x42,
0x52, 0x6A, 0x59, 0x33, 0x4E, 0x55, 0x46, 0x45, 0x4D, 0x6A,
0x56, 0x47, 0x4D, 0x44, 0x63, 0x32, 0x51, 0x6A, 0x6C, 0x43,
0x51, 0x54, 0x55, 0x33, 0x52, 0x54, 0x51, 0x32, 0x4E, 0x44,
0x49, 0x7A, 0x51, 0x54, 0x4A, 0x43, 0x52, 0x44, 0x59, 0x34,
0x4D, 0x44, 0x4E, 0x45, 0x51, 0x54, 0x5A, 0x45, 0x51, 0x30,
0x51, 0x77, 0x4E, 0x7A, 0x4A, 0x43, 0x4E, 0x30, 0x4D, 0x31,
0x4D, 0x45, 0x56, 0x42, 0x51, 0x54, 0x52, 0x43, 0x4D, 0x44,
0x59, 0x35, 0x52, 0x44, 0x59, 0x35, 0x4D, 0x54, 0x49, 0x31,
0x51, 0x7A, 0x49, 0x33, 0x4E, 0x45, 0x4A, 0x43, 0x4D, 0x55,
0x49, 0x31, 0x52, 0x44, 0x64, 0x44, 0x51, 0x30, 0x4A, 0x46,
0x4D, 0x30, 0x51, 0x7A, 0x52, 0x45, 0x46, 0x47, 0x4E, 0x30,
0x55, 0x30, 0x4E, 0x6A, 0x51, 0x79, 0x4D, 0x30, 0x45, 0x79,
0x51, 0x6B, 0x51, 0x32, 0x4F, 0x44, 0x41, 0x7A, 0x52, 0x44,
0x4D, 0x33, 0x51, 0x6B, 0x4E, 0x43, 0x4D, 0x30, 0x56, 0x46,
0x4D, 0x6A, 0x55, 0x34, 0x4F, 0x54, 0x67, 0x31, 0x52, 0x6A,
0x59, 0x33, 0x52, 0x54, 0x51, 0x32, 0x4E, 0x44, 0x49, 0x7A,
0x51, 0x54, 0x4A, 0x43, 0x52, 0x44, 0x59, 0x34, 0x4D, 0x44,
0x4E, 0x45, 0x51, 0x7A, 0x4D, 0x33, 0x51, 0x6A, 0x55, 0x79,
0x51, 0x6B, 0x51, 0x30, 0x52, 0x54, 0x4A, 0x47, 0x4E, 0x44,
0x67, 0x30, 0x52, 0x54, 0x52, 0x43, 0x4D, 0x44, 0x59, 0x35,
0x52, 0x44, 0x59, 0x35, 0x4D, 0x54, 0x49, 0x31, 0x51, 0x7A,
0x49, 0x33, 0x4E, 0x45, 0x49, 0x33, 0x4E, 0x54, 0x6B, 0x32,
0x4D, 0x55, 0x55, 0x78, 0x52, 0x44, 0x4D, 0x34, 0x51, 0x30,
0x59, 0x31, 0x52, 0x6A, 0x4D, 0x7A, 0x4E, 0x55, 0x55, 0x79,
0x4D, 0x30, 0x4D, 0x32, 0x4F, 0x45, 0x51, 0x32, 0x4E, 0x30,
0x56, 0x45, 0x4E, 0x44, 0x4E, 0x44, 0x4D, 0x54, 0x59, 0x33,
0x4F, 0x45, 0x52, 0x44, 0x51, 0x30, 0x45, 0x7A, 0x4E, 0x45,
0x52, 0x42, 0x4F, 0x45, 0x45, 0x77, 0x52, 0x54, 0x4E, 0x47,
0x4E, 0x7A, 0x5A, 0x44, 0x4E, 0x44, 0x64, 0x42, 0x4E, 0x54,
0x45, 0x35, 0x4D, 0x6B, 0x51, 0x77, 0x52, 0x45, 0x46, 0x46,
0x4E, 0x44, 0x64, 0x44, 0x4F, 0x55, 0x4E, 0x42, 0x4E, 0x54,
0x6B, 0x77, 0x4F, 0x55, 0x52, 0x42, 0x4E, 0x44, 0x49, 0x31,
0x4D, 0x7A, 0x63, 0x77, 0x4E, 0x54, 0x59, 0x78, 0x4D, 0x54,
0x42, 0x44, 0x52, 0x54, 0x46, 0x44, 0x52, 0x6A, 0x59, 0x33,
0x4D, 0x55, 0x51, 0x30, 0x4E, 0x30, 0x4D, 0x35, 0x51, 0x30,
0x45, 0x31, 0x4F, 0x54, 0x41, 0x35, 0x52, 0x45, 0x45, 0x30,
0x4D, 0x6A, 0x55, 0x7A, 0x4F, 0x44, 0x51, 0x33, 0x4D, 0x6A,
0x63, 0x31, 0x4D, 0x30, 0x59, 0x78, 0x52, 0x55, 0x45, 0x33,
0x4F, 0x55, 0x46, 0x44, 0x4F, 0x41, 0x3D, 0x3D]
from Crypto.Cipher import DES
import base64
key=b'DozerCTF'
enc=0xB81D99F868B641C47E46423A2BD6803DDE2E71C1846CD8F59F52419A4889F2A01440B89908E3D59D88D20232581BF41A39639F17E8D00317678DCCA34DA8A0E31440B89908E3D59D7E8192CAB8C8F7CD89312340D1F444497B580FBDA0D2E5FEE913B9B98667FAFD9A6A52861A5357AF675AD25F076B9BA57E46423A2BD6803DA6DCD072B7C50EAA4B069D69125C274BB1B5D7CCBE3D3DAF7E46423A2BD6803D37BCB3EE258985F67E46423A2BD6803DC37B52BD4E2F484E4B069D69125C274B75961E1D38CF5F335E23C68D67ED43C1678DCCA34DA8A0E3F76C47A5192D0DAE47C9CA5909DA42537056110CE1CF671D47C9CA5909DA42538472753F1EA79AC8
de=DES.new(key,DES.MODE_ECB)
print(de.decrypt(long_to_bytes(enc)))
得到一个奇怪的字符串。
'$*000000*000*0000*000000*00***000***0000*00*000000*00000****00000***0000*00000**0*0*0*00*00000*0000****0*00****0000*0*00*000*0000***0*00*0***0000*00*****000*0000*00*000*000*0000*0***00*0***0000*0*0000***0**00****000000000*00000*000000000**0000*0000000000*$'
然后看着代码,发现在最后出现
这很迷宫,恰逢早上AK了dasctf的逆向,其中也有一道迷宫。然后就找长宽。
# $*000000*000*000
# 0*000000*00***00
# 0***0000*00*0000
# 00*00000****0000
# 0***0000*00000**
# 0*0*0*00*00000*0
# 000****0*00****0
# 000*0*00*000*000
# 0***0*00*0***000
# 0*00*****000*000
# 0*00*000*000*000
# 0*0***00*0***000
# 0*0*0000***0**00
# ****000000000*00
# 000*000000000**0
# 000*0000000000*$
得到如图的迷宫,从左上到右下。

走的时候发现有两条路,一条比较短,一天比较长,然后选了短的,发现刚好32位
dssdssdssddsssdddsssddwddsdssdsd
然后进入程序,ida附加,下断。
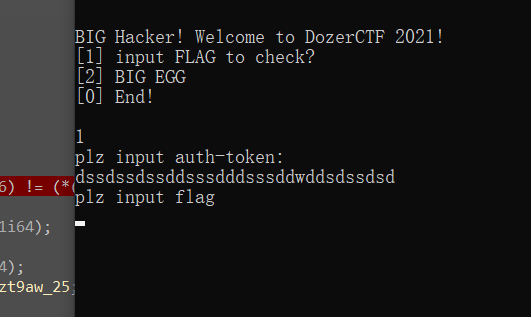
动调发现,v60是个定值,v63是我们输入的值,v65是最终要比较的值。且为异或。
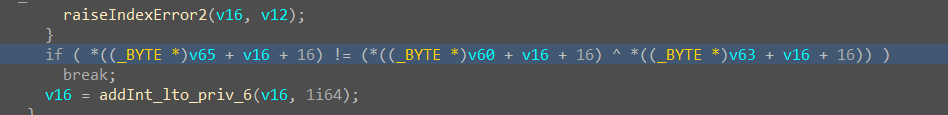
故脚本如下
dd=[ 0x27, 0x5C, 0x4F, 0x01, 0x45, 0x07, 0x15, 0x5F, 0x42, 0x5C,
0x51, 0x1C, 0x07, 0x57, 0x6F, 0x1D, 0x5F, 0x43, 0x0A, 0x5E,
0x5B, 0x14, 0x3E, 0x11, 0x5F, 0x01, 0x3E, 0x00, 0x00, 0x57,
0x12, 0x1F]
ff=[0x63, 0x33, 0x35, 0x64, 0x37, 0x64, 0x61, 0x39, 0x39, 0x31,
0x30, 0x65, 0x65, 0x32, 0x30, 0x64, 0x30, 0x36, 0x61, 0x30,
0x34, 0x63, 0x61, 0x65, 0x37, 0x64, 0x61, 0x62, 0x65, 0x36,
0x66, 0x62]
for i in range(len(dd)):
print(chr(dd[i]^ff[i]),end='')
Dozerctf{maybe_youknow_the_beat}
Classical RE
安卓逆向,Ollvm混淆
加密源码在so文件里面。再到对应函数,ollvm的。。头皮发麻,本来要放弃的,不过看代码长度混淆后才300行有点短。直接逆了。然后动调这个so文件,猜+动调。
一直动调跟踪输入流。
发现加密很简单,就是
用‘dozer’对输入流进行循环异或,然后再将密文切割开来前面一半异或后面。
倒过来求,然后拼接在一起就行了,,hh侥幸拿了一血。
ds=[ 0x18, 0x3A, 0x18, 0x1E, 0x27, 0x1A, 0x0E, 0x39,0x15,0x1D,
0x3B, 0x06, 0x09, 0x3A, 0x17, 0x05, 0x1C, 0x03]
do='dozer'
print(bytearray(ds))
for i in range(len(ds)):
print(chr(ord(do[i%len(do)])^ds[i]),end='')
print('\n')
dd='o_is_easy'
ss='|Ub{U~aCp'
# for i in range(len(ds)):
# print(chr(ds[i]^dss[i]^ord(do[i%len(do)])),end='')
print('\n')
po=[0x18, 0x3A, 0x18, 0x1E, 0x27, 0x1A, 0x0E, 0x39,0x15]
po1=[0x1D,
0x3B, 0x06, 0x09, 0x3A, 0x17, 0x05, 0x1C, 0x03]
#android_o_is_easy
for i in range(len(po)):
print(chr(po[i]^po1[i]^ord(do[i%5])),end='')
#android_so_is_easy
#Dozerctf{android_so_is_easy }
这题好熟悉啊
from malduck import *
data = open("./dump", "rb").read()[0x5060:0x5b6e0]
enc_flag = data[:0x80]
candidate = b""
key_iv = []
x = 0
while x < len(data) - 0x10:
candidate = data[x:x+0x10]
if data.count(candidate) > 1:
key_iv.append(candidate)
x += 1
#print(aes.cbc.decrypt(key_iv[0], key_iv[1], enc_flag))
print(aes.cbc.decrypt(key_iv[1], key_iv[0], enc_flag))
#b'ICw\x8eq\x9a\x94MT \xd3u\x11u\xdf\x86ctf ,flag is Dozerctf{maybe_you_know_this_challenge}\n\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc\xcc'
#Dozerctf{maybe_you_know_this_challenge}


