Kubernetes NetworkPolicy总结
准备实验环境
创建命名空间
[root@master10 manifests]/ kubectl config set-context --namespace web --current
Context "kubernetes-admin@kubernetes" modified.
创建pod web1
[root@master10 manifests]/ kubectl run web1 --image=nginx --image-pull-policy=IfNotPresent
pod/web1 created
生成发布文件
[root@master10 manifests]/ kubectl exec -it web1 -- bash
root@web1:/ echo Hello web1 > /usr/share/nginx/html/index.html
root@web1:/
exit
创建pod web2
[root@master10 manifests] kubectl run web2 --image=nginx --image-pull-policy=IfNotPresent
pod/web2 created
验证创建的pod
[root@master10 manifests] kubectl get pods --show-labels
NAME READY STATUS RESTARTS AGE LABELS
test 1/1 Running 0 5m37s run=test
web1 1/1 Running 0 18m run=web1
web2 1/1 Running 0 17m run=web2
生成发布文件
[root@master10 manifests] kubectl exec -it web2 -- bash
root@web2:/ echo Hello web2 > /usr/share/nginx/html/index.html
root@web2:/
exit
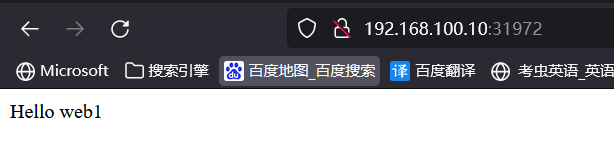
创建service web1和web2
[root@master10 manifests] kubectl expose pod web1 --port=80 --target-port=80 --type=NodePort
[root@master10 manifests] kubectl expose pod web2 --port=80 --target-port=80 --type=NodePort
[root@master10 manifests] kubectl get svc
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
web1 NodePort 10.100.150.156 <none> 80:31972/TCP 2m9s
web2 NodePort 10.108.8.97 <none> 80:31354/TCP 111s
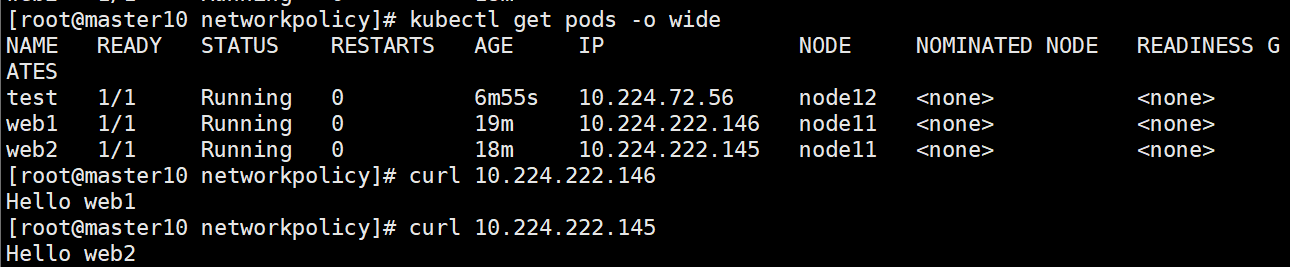
创建测试pod,验证访问web1和web2 pod
[root@master10 manifests] kubectl run test --image=nginx --image-pull-policy=IfNotPresent
pod/test created
[root@master10 manifests] kubectl exec -it test -- curl web1
Hello web1
[root@master10 manifests] kubectl exec -it test -- curl web2
Hello web2
[root@master10 manifests] kubectl exec -it web2 -- curl web1
Hello web1
集群访问:
集群节点外部访问:

根据标签限定
示例1:
对namespace web 下的 run:web1 这个pod进行限制
只允许 run:test这个标签的pod可以访问 web1的80端口
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
run: test
ports:
- protocol: TCP
port: 80
创建策略
[root@master10 networkpolicy] kubectl create -f networkpolicy.yaml
networkpolicy.networking.k8s.io/my-network-policy created
查看策略
[root@master10 networkpolicy] kubectl describe networkpolicies.networking.k8s.io
Name: my-network-policy
Namespace: web
Created on: 2022-07-04 11:37:06 +0800 CST
Labels: <none>
Annotations: <none>
Spec:
PodSelector: run=web1
Allowing ingress traffic:
To Port: 80/TCP
From:
PodSelector: run=test
Not affecting egress traffic
Policy Types: Ingress
示例2:
允许同一namespce中所有pod访问具有标签run:web1的pod 80 端口
matchLabels中不使用任何标签,则允许同一ns中所有pod
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
ports:
- protocol: TCP
port: 80也可以写成 - podSelector: {},省略matchlabels:
根据ns限定
用于限定,来源于其他namespace中pod。
示例1:
允许具有标签project: myproject的namespace中所有pod,访问当前ns中具有标签run: web1的pod 80端口。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Ingress
ingress:
- from:
- namespaceSelector:
matchLabels:
project: myproject
ports:
- protocol: TCP
port: 80
给network-test这个ns添加标签project=myproject,此时该ns中pod可以访问web1.web
kubectl label ns network-test project=myproject
示例2:
允许所有namespace中所有pod,访问当前ns中具有标签run: web1的pod 80端口。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Ingress
ingress:
- from:
- namespaceSelector: {}
ports:
- protocol: TCP
port: 80
根据pod IP限定
示例1:
允许网段172.17.0.0/16但不包括子网172.17.1.0/24中主机,访问具有标签 run: web1 的pod 80端口。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Ingress
ingress:
- from:
- ipBlock:
cidr: 172.17.0.0/16
except:
- 172.17.1.0/24
ports:
- protocol: TCP
port: 80
不限定端口
示例:
允许具有run:test标签的pod对名为web的ns下的web1进行访问,不限制端口。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
run: test
限定端口范围
允许被限制的pod,同一ns下的run:test标签的pod可以访问被限制pod的32000-32768端口。
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Ingress
ingress:
- from:
- podSelector:
matchLabels:
run: test
ports:
- protocol: TCP
port: 32000
endPort: 32768
限制pod出口访问
1、Egress-podSelector-Pod出口方向目的IP及目的端口限制-只允许访问指定的10.0.0.0/24和12.0.0.0/24地址段范围的服务端口80和服务端口53
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Egress
egress:
- to:
- ipBlock:
cidr: 10.0.0.0/24
- ipBlock:
cidr: 12.0.0.0/24
ports:
- protocol: TCP
port: 80
- protocol: UDP
port: 53
- protocol: TCP
port: 53
2、对pod web1出口限制仅能访问web2的80和53 dns端口服务
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Egress
egress:
- to:
- podSelector:
matchLabels:
run: we2
ports:
- protocol: TCP
port: 80
- protocol: TCP
port: 53
- protocol: UDP
port: 53
3、限制pod web只能访问标签为project=myproject的ns下的pod资源的80和53端口服务
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: my-network-policy
namespace: web
spec:
podSelector:
matchLabels:
run: web1
policyTypes:
- Egress
egress:
- to:
- namespaceSelector:
matchLabels:
project: myproject
ports:
- protocol: TCP
port: 80
- protocol: TCP
port: 53
- protocol: UDP
port: 53本文来自博客园,作者:PunchLinux,转载请注明原文链接:https://www.cnblogs.com/punchlinux/p/16677939.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号