k8s 的账户授权RBAC
集群认证和授权(RBAC)
主体(subject)---->认证----->授权(action)----->准入控制(object)
- subject:表示三类主体,user,group,serviceAccount。
- action:能对Object做什么,例如:get、list、watch、patch、delete、update、create等。
- object:主要表现为以下三类对象。
- Resource:代表一类资源,也被称为Resource Group,例如Secret。
- Resource Names:代表ResourceGroup中具体的单个资源。
- Non-Resource URLs:它被称为非资源URL或称为虚拟URL对象,是k8s中所需要的特殊动作(不需要多关注)。
授权管理
授权模式
授权模式定义认证成功的用户对集群的操作权限,有kube-apiserver配置文件定义:
[root@master ~]# vim /etc/kubernetes/manifests/kube-apiserver.yaml
......
#在spec.containers下的command中添加参数--authorization-mode指定
spec:
containers:
- command:
- --authorization-mode=Node,RBAC
......
支持的模式:
- AlwaysAllow,允许用户所有请求。(测试使用)
- AlwaysDeny,拒绝用户所有请求,不管用户是否具有权限,但不限制admin用户。
- ABAC,Attribute Based Access Control,详情参考ABAC。
- Webhook,详情参考Webhook。
- RBAC,Role Based Access Control,基于角色的访问控制,只有明确了赋予用户权限,用户才能执行相关操作。
- Node,用于各个node上的kubelet访问apiserver时使用。
role管理
kubernetes为了方便管理权限,将一组特定权限赋予角色,然后将角色赋予用户,那么用户将继承该角色具有的权限。
Role: 定义一组规则,用于访问某一命名空间中的Kubernetes资源。
角色分类
- role,namespace角色,限定用户访问特定namespace。role绑定给用户,称之为rolebinding。
- clusterrole,集群角色,可以管理集群,包括所有namespace中资源。clusterrole绑定给用户,称之为clusterrolebinding。
权限由kubernetes系统预定义的,clusterroles/admin中包涵系统中全部权限列表。
cluster role管理
ClusterRole: 定义了一组访问集群中Kubernetes资源(包括所有命名空间)的规则。
常见clusterrole
kubernetes系统中已经预定义了很多cluster role,常见的clusterrole如下:
- view,对系统中几乎所有的对象都有get、list和watch权限。
- edit,对系统中几乎所有的对象都有get、list和watch权限。其中部分对象额外具有create、delete、deletecollection、patch、update权限。
- admin,对系统中大部分的对象具有所有权限。基本上用于绑定用户到特定namespace中
- cluster-admin,对系统中所有的对象具有所有权限。
Service Account
Service Account,即服务账户,pod使用Service Account身份运行容器。
赋予Service Account相应角色,则使用该Service Account身份运行的pod中进程将具有对应Service Account的权限。
在每个namespace中都有一个名称为default的Service Account。每个Service Account都有一个Secret。
sa会创建一个secret,pod或deployment使用sa账户时,会将sa的secret进行挂载到pods中使用。
用户授权案例
账户的创建与绑定
1、创建指定namespace
root@deploy:~/yaml# kubectl create ns rbac
root@deploy:~/yaml# kubectl config set-context --namespace rbac --current
2、创建sa账户
root@deploy:~/yaml# kubectl create serviceaccount lxh
root@deploy:~/yaml# kubectl get sa
NAME SECRETS AGE
default 0 5m
lxh 0 57s
3、创建role角色,normal-user
针对rbac名称空间下的pod拥有查看、修改和删除权限。
针对rbac名称空间下的deployment查看的权限
root@deploy:~/yaml/rbac-yaml# cat role.yaml
kind: Role
apiVersion: rbac.authorization.k8s.io/v1
metadata:
namespace: rbac
name: normal-user
rules:
- apiGroups: ["*"]
resources: ["pods/exec"]
#verbs: ["*"]
##RO-Role
verbs: ["get", "list", "watch", "create"]
- apiGroups: ["*"]
resources: ["pods"]
#verbs: ["*"]
##RO-Role
verbs: ["get", "list", "watch", "delete"]
- apiGroups: ["apps/v1"]
resources: ["deployments"]
#verbs: ["get", "list", "watch", "create", "update", "patch", "delete"]
##RO-Role
verbs: ["get", "watch", "list"]
root@deploy:~/yaml/rbac-yaml# kubectl apply -f role.yaml
root@deploy:~/yaml/rbac-yaml# kubectl get role
NAME CREATED AT
normal-user 2022-08-19T05:19:11Z
4、将sa账户绑定到role normal-user角色
root@deploy:~/yaml/rbac-yaml# vim role-bind.yaml
kind: RoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: role-bind
namespace: rbac
subjects:
- kind: ServiceAccount
name: lxh
namespace: rbac
roleRef:
kind: Role
name: normal-user
apiGroup: rbac.authorization.k8s.io
root@deploy:~/yaml/rbac-yaml# kubectl apply -f role-bind.yaml
#查看sa账户绑定role角色
root@deploy:~/yaml/rbac-yaml# kubectl get rolebindings.rbac.authorization.k8s.io -o yaml
apiVersion: v1
items:
- apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"rbac.authorization.k8s.io/v1","kind":"RoleBinding","metadata":{"annotations":{},"name":"role-bind","namespace":"rbac"},"roleRef":{"apiGroup":"rbac.authorization.k8s.io","kind":"Role","name":"normal-user"},"subjects":[{"kind":"ServiceAccount","name":"lxh","namespace":"rbac"}]}
creationTimestamp: "2022-08-19T05:17:56Z"
name: role-bind
namespace: rbac
resourceVersion: "712005"
uid: d3e3daf6-0eea-425b-9e5a-335ad0406722
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: normal-user
subjects:
- kind: ServiceAccount
name: lxh
namespace: rbac
kind: List
metadata:
resourceVersion: ""
5、创建sa账户secret类型token(1.23版本前不需要手动创建)
root@deploy:~/yaml/rbac-yaml# cat sa-token.yaml
apiVersion: v1
kind: Secret
type: kubernetes.io/service-account-token
metadata:
name: lxh-token
namespace: rbac
annotations:
kubernetes.io/service-account.name: "lxh"
root@deploy:~/yaml/rbac-yaml# kubectl apply -f sa-token.yaml
#获取sa账户token
root@deploy:~/yaml/rbac-yaml# kubectl describe secrets lxh-token|grep token
Name: lxh-token
Type: kubernetes.io/service-account-token
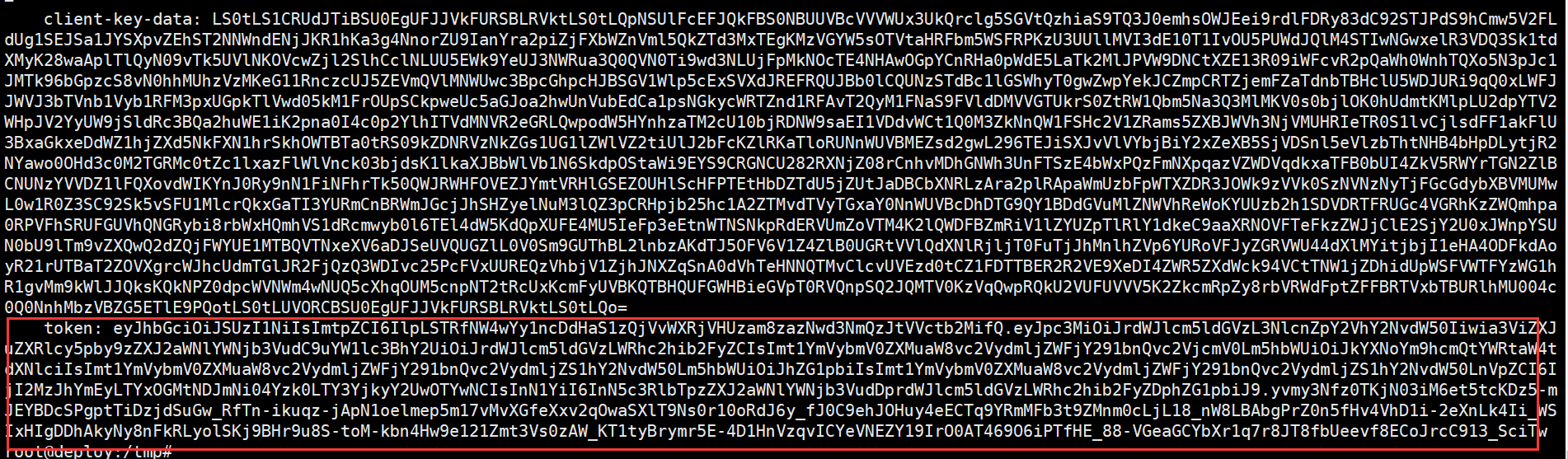
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlpLSTRfNW4wYy1ncDdHaS1zQjVvWXRjVHUzam8zazNwd3NmQzJtVVctb2MifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJyYmFjIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6Imx4aC10b2tlbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJseGgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI0MjdhMDdmNi1hYzNhLTRjZDItYWViNC0xOGJlMTNhYjZiZTIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6cmJhYzpseGgifQ.UnCLtXk96Ycj30jR_4NAaIxwfoSoeg36Clvgnc6UOJAdhf2f5jMSvw174AshDZfcDb4S-gWZbRNeN0-RsT8MocXqa37LQg_ZgoMQAhAvc7fxH32dhoPENrIvX63z9KISCpFqdeU5AX4vL_XIH9LXXjOdcbALYMsiDw_DwupLqajzIyzuu9aCMqrrAVA-RUtnKRaRfCWw4hL0Y39hKpf0QxEnY7jzrg906-6Kcl7zC9izkEb4WMG2Fsw0USGNEnjWPcI1DaZtXIpUnHOecpZlgpWFCSZwaldz3TI0QMzhCTi3nVKUkz3iVjiYUoOpKS5buTFfBJNyolRkgsw-H3bqlQ
登录dashboard
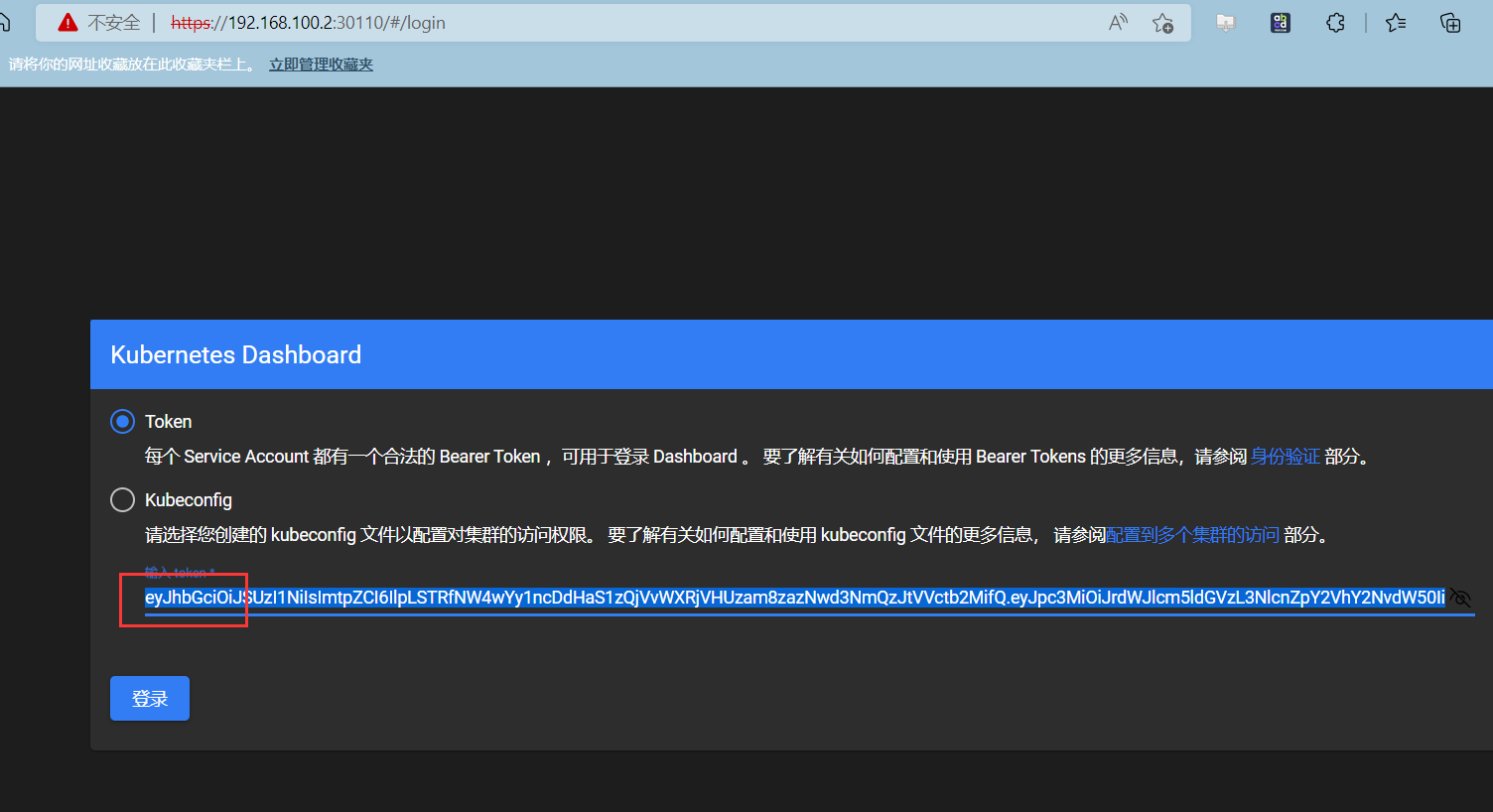
登录验证
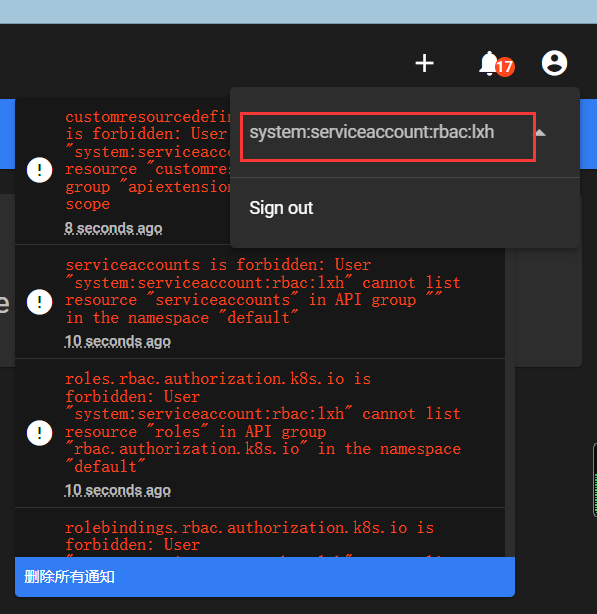
在rbac名称空间下创建一个pod
root@deploy:~/yaml/rbac-yaml# kubectl run web --image nginx --image-pull-policy IfNotPresent
pod/web created
root@deploy:~/yaml/rbac-yaml# kubectl get pods
NAME READY STATUS RESTARTS AGE
web 1/1 Running 0 2s
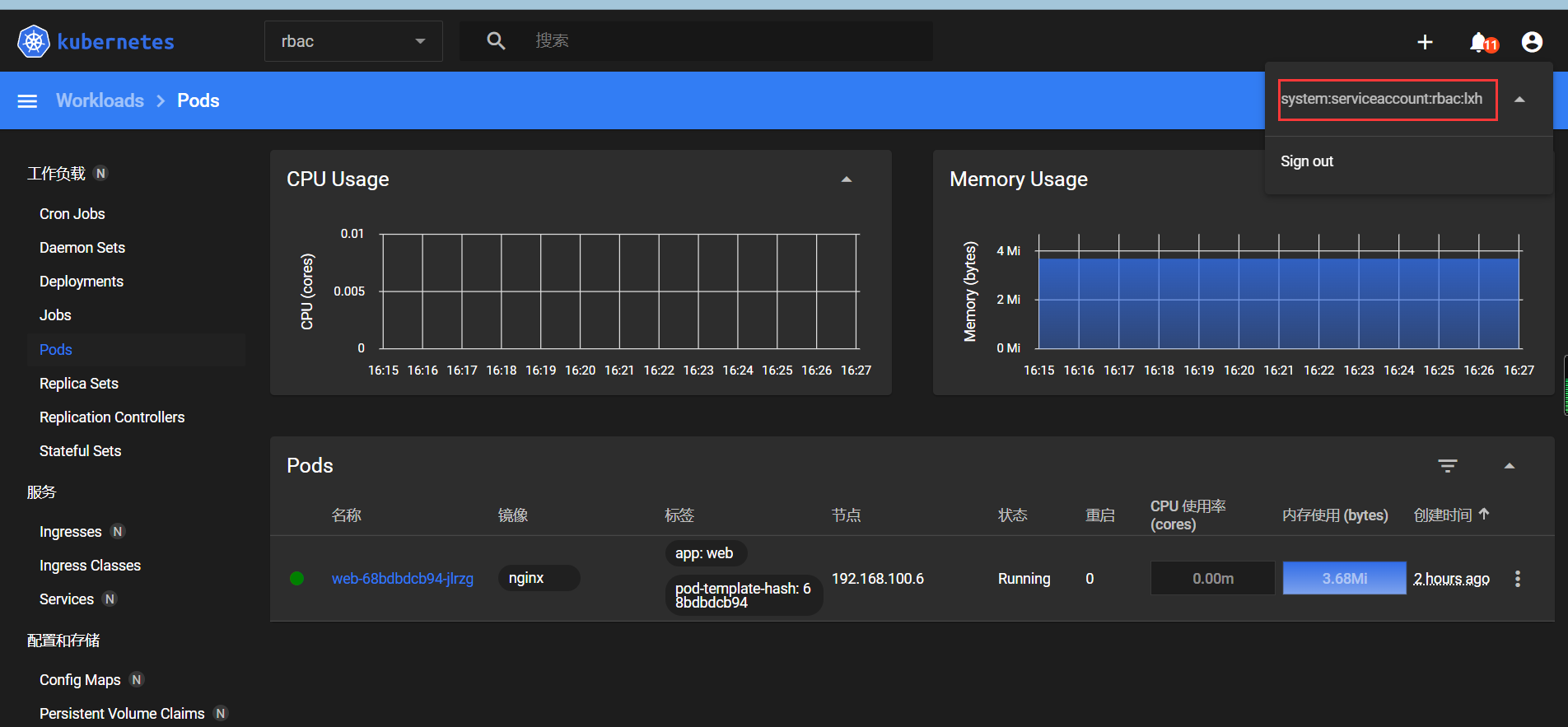
使用lxh sa账户仅可以查看到rbac的名称空间的资源
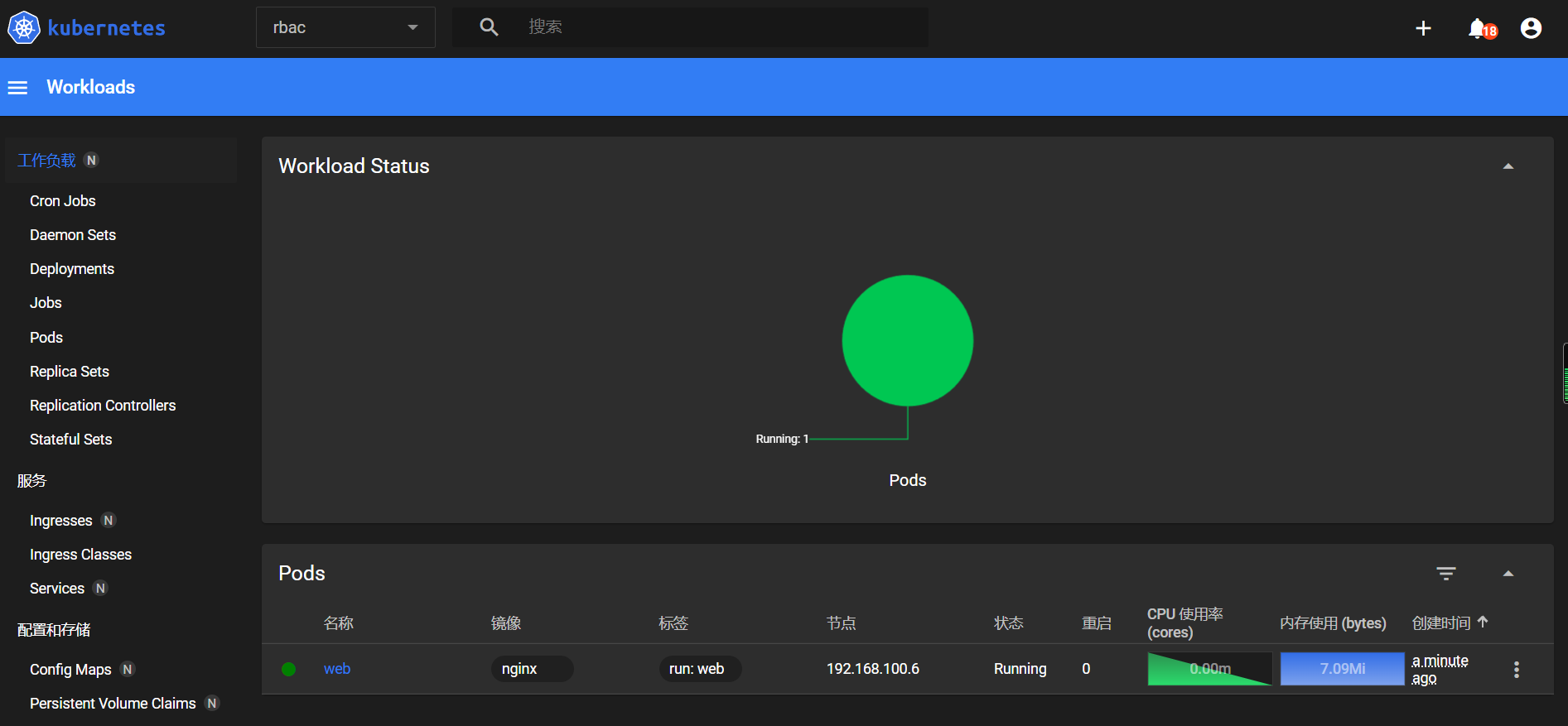
对pod进行删除
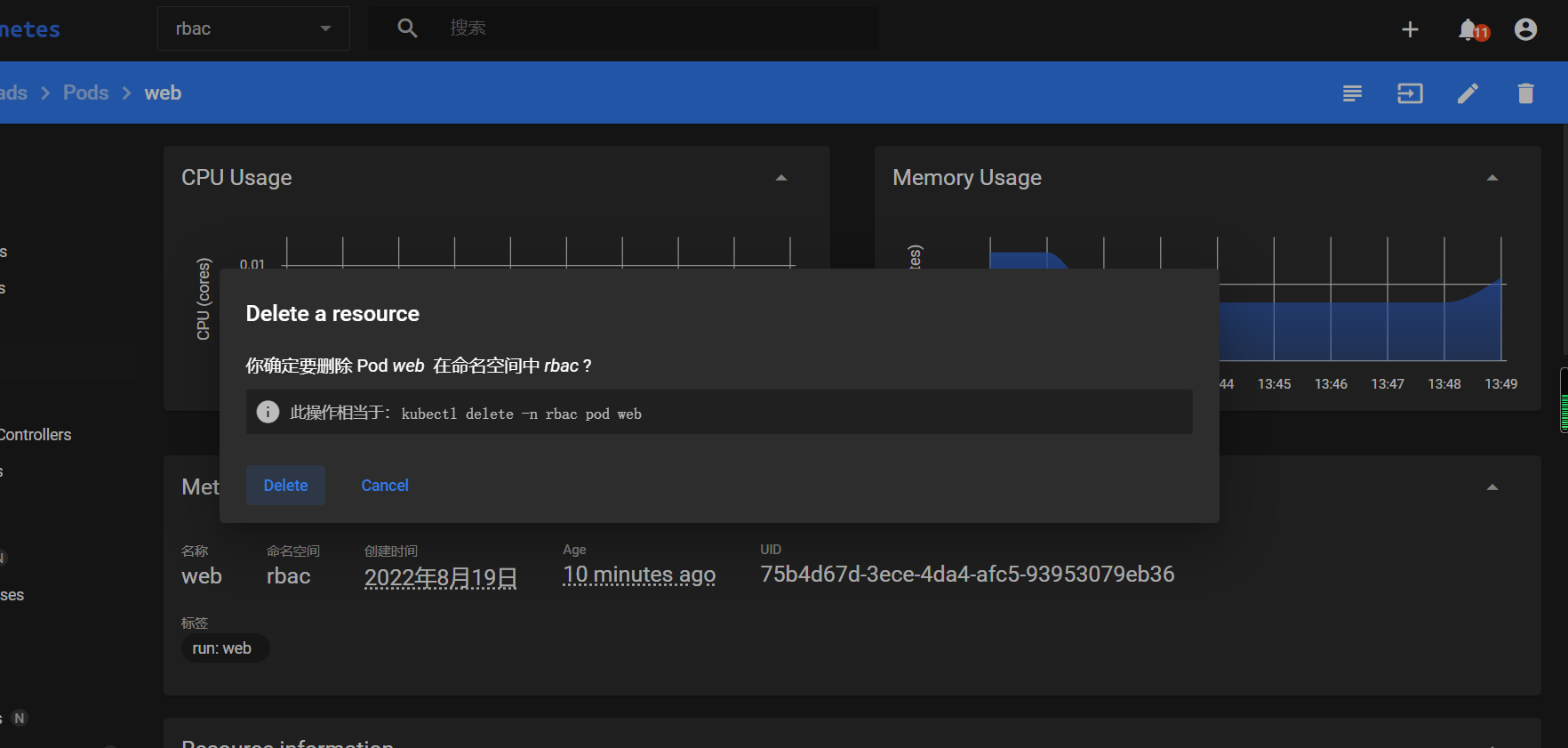
pod已经被删除
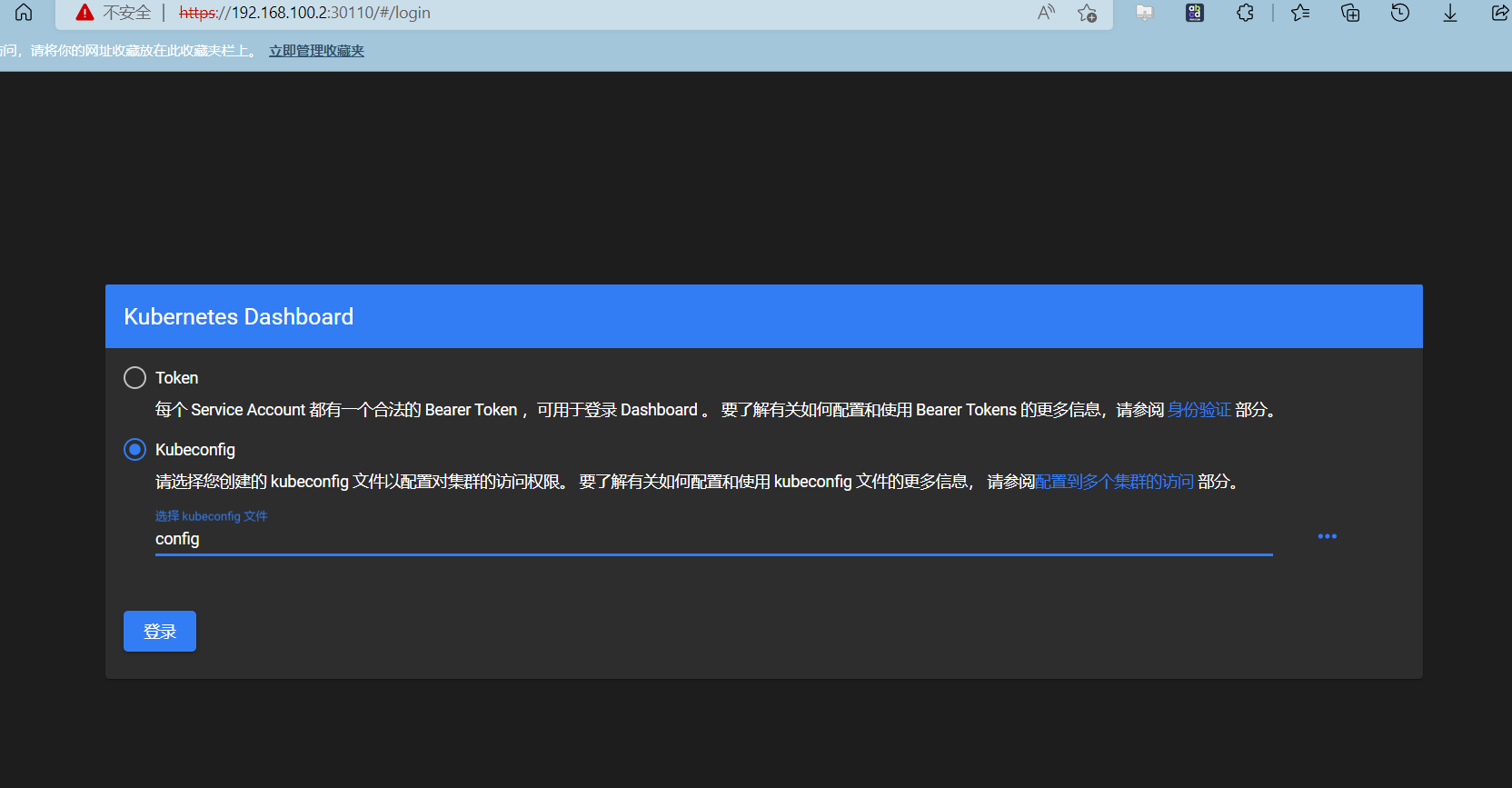
将token附件到k8s的集群配置文件中,dashborad登录使用config文件登录
root@deploy:~# cp /root/.kube/config /tmp/
root@deploy:~# cd /tmp/
root@deploy:/tmp# vim config
root@deploy:~# kubectl -n kubernetes-dashboard describe secrets dashboard-admin-user
Name: dashboard-admin-user
Namespace: kubernetes-dashboard
Labels: <none>
Annotations: kubernetes.io/service-account.name: admin
kubernetes.io/service-account.uid: 2632aba2-618c-42f6-8c94-67b92ce09604
Type: kubernetes.io/service-account-token
Data
====
ca.crt: 1302 bytes
namespace: 20 bytes
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlpLSTRfNW4wYy1ncDdHaS1zQjVvWXRjVHUzam8zazNwd3NmQzJtVVctb2MifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdXNlciIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjI2MzJhYmEyLTYxOGMtNDJmNi04Yzk0LTY3YjkyY2UwOTYwNCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDphZG1pbiJ9.yvmy3Nfz0TKjN03iM6et5tcKDz5-mJEYBDcSPgptTiDzjdSuGw_RfTn-ikuqz-jApN1oelmep5m17vMvXGfeXxv2qOwaSXlT9Ns0r10oRdJ6y_fJ0C9ehJOHuy4eECTq9YRmMFb3t9ZMnm0cLjL18_nW8LBAbgPrZ0n5fHv4VhD1i-2eXnLk4Ii_WSIxHIgDDhAkyNy8nFkRLyolSKj9BHr9u8S-toM-kbn4Hw9e121Zmt3Vs0zAW_KT1tyBrymr5E-4D1HnVzqvICYeVNEZY19IrO0AT469O6iPTfHE_88-VGeaGCYbXr1q7r8JT8fbUeevf8ECoJrcC913_SciTw
添加token到config
root@deploy:/tmp# tail -5 config
- name: admin
user:
client-certificate-data: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUQxekNDQXIrZ0F3SUJBZ0lVSEVSSE8yaysvRjA1Lzd0bTBieGpmUmR4MThzd0RRWUpLb1pJaHZjTkFRRUwKQlFBd1lURUxNQWtHQTFVRUJoTUNRMDR4RVRBUEJnTlZCQWdUQ0VoaGJtZGFhRzkxTVFzd0NRWURWUVFIRXdKWQpVekVNTUFvR0ExVUVDaE1EYXpoek1ROHdEUVlEVlFRTEV3WlRlWE4wWlcweEV6QVJCZ05WQkFNVENtdDFZbVZ5CmJtVjBaWE13SUJjTk1qSXdOekk0TURNd09EQXdXaGdQTWpBM01qQTNNVFV3TXpBNE1EQmFNR2N4Q3pBSkJnTlYKQkFZVEFrTk9NUkV3RHdZRFZRUUlFd2hJWVc1bldtaHZkVEVMTUFrR0ExVUVCeE1DV0ZNeEZ6QVZCZ05WQkFvVApEbk41YzNSbGJUcHRZWE4wWlhKek1ROHdEUVlEVlFRTEV3WlRlWE4wWlcweERqQU1CZ05WQkFNVEJXRmtiV2x1Ck1JSUJJakFOQmdrcWhraUc5dzBCQVFFRkFBT0NBUThBTUlJQkNnS0NBUUVBcVVVWUx3UkQrclg5SGVtQzhiaS8KU0NydHpobDliRHova3ZRQ0cvN3QvdkkyT3UvYWw5V2FLdUg1SEJSa1JYSXpvZEhST2NNWndENjJKR1hKa3g4Ngp6K2VPSGp2K2tqYmYxV21mZ1ZpeUJGU3dzMUxIMzVGYW5sOTVtaHRFbm5WSFRPKzU3UUllMVI3dE10T1IvOU5PClFnSUJTOEkyMDRsMXpUd1Q0N0pNbXVzMitvMGhlTlQyN09vTk5UVlNKOVcwZjl2SlhCclNLUU5EWk9YeUJ3NWQKbmt0NEFTdE4vcHdzS1IxaTJDTnExODRwMDhqWHRHa0pWdE5LaTk2MlJPVW9DNCtXZE13R09iWFcvR2pQaWh0Wgp4U0F6OTd6SXNSTE5Pemxqc3EvLzdIYTFIc1czeG11RnczcUJ5ZEVmQVlMNWUwc3BpcGhpcHJBSGV1Wlp5cExSClV3SURBUUFCbzM4d2ZUQU9CZ05WSFE4QkFmOEVCQU1DQmFBd0hRWURWUjBsQkJZd0ZBWUlLd1lCQlFVSEF3RUcKQ0NzR0FRVUZCd01DTUF3R0ExVWRFd0VCL3dRQ01BQXdIUVlEVlIwT0JCWUVGT0laUjdBdVI0ang3MXEvblRnMwpnU1R0YW9rR01COEdBMVVkSXdRWU1CYUFGTVl6R3RXR2NkOG55b2xJTENxNkE1Mmh4Wk9GTUEwR0NTcUdTSWIzCkRRRUJDd1VBQTRJQkFRQjk2OUtJMzVGRXdmSXRzbm43UlVJOVYrSlRpSkhXVFhnTy9JRHQySXZ2ZXBqLzR3dVQKV0FITFpFbmhGbTVTMjNDVmdvMlJEOTJGcGZEL0RWWWV6L0dPVU14bmEzM3ZFVHZoRGhXSEZMUU44aFRHdXU4agptN25mS1RCUm1MQkdVNnVxakx6OHhDSk8rUXZKZi9pSTFxd1c0OW1NbFAyTWoyQUN5SWNHejU0WjRFTnAwZTFCCm1zb1RzUkxUcXlQclVTL2U5U0ZwWm94Y0xPTWQvaHRuMXFCT2ZvcHpzWWNJU1ZHMTJuRFlGSzQrUzNXZzJ4cDQKQjdaQUhtMm81T2ZOTk9uaHNpTzNIb0FYdTdncFh4M1I3YnYxL3JFbk9YOG5FN2szSE1MVmVYN1JvOXp3WEtmOApDYnplWm4ydlRWQ3BXT0t3ODcyZ0dPV2FLMytsWTlRTmVFYVoKLS0tLS1FTkQgQ0VSVElGSUNBVEUtLS0tLQo=
client-key-data: LS0tLS1CRUdJTiBSU0EgUFJJVkFURSBLRVktLS0tLQpNSUlFcEFJQkFBS0NBUUVBcVVVWUx3UkQrclg5SGVtQzhiaS9TQ3J0emhsOWJEei9rdlFDRy83dC92STJPdS9hCmw5V2FLdUg1SEJSa1JYSXpvZEhST2NNWndENjJKR1hKa3g4NnorZU9IanYra2piZjFXbWZnVml5QkZTd3MxTEgKMzVGYW5sOTVtaHRFbm5WSFRPKzU3UUllMVI3dE10T1IvOU5PUWdJQlM4STIwNGwxelR3VDQ3Sk1tdXMyK28waAplTlQyN09vTk5UVlNKOVcwZjl2SlhCclNLUU5EWk9YeUJ3NWRua3Q0QVN0Ti9wd3NLUjFpMkNOcTE4NHAwOGpYCnRHa0pWdE5LaTk2MlJPVW9DNCtXZE13R09iWFcvR2pQaWh0WnhTQXo5N3pJc1JMTk96bGpzcS8vN0hhMUhzVzMKeG11RnczcUJ5ZEVmQVlMNWUwc3BpcGhpcHJBSGV1Wlp5cExSVXdJREFRQUJBb0lCQUNzSTdBc1lGSWhyT0gwZwpYekJCZmpCRTZjemFZaTdnbTBHclU5WDJURi9qQ0xLWFJJWVJ3bTVnb1Vyb1RFM3pxUGpkTlVwd05kM1FrOUpSCkpweUc5aGJoa2hwUnVubEdCa1psNGkycWRTZnd1RFAvT2QyM1FNaS9FVldDMVVGTUkrS0ZtRW1Qbm5Na3Q3MlMKV0s0bjlOK0hUdmtKMlpLU2dpYTV2WHpJV2YyUW9jSldRc3BQa2huWE1iK2pna0I4c0p2YlhITVdMNVR2eGRLQwpodW5HYnhzaTM2cU10bjRDNW9saEI1VDdvWCt1Q0M3ZkNnQW1FSHc2V1ZRams5ZXBJWVh3NjVMUHRIeTR0S1lvCjlsdFF1akFlU3BxaGkxeDdWZ1hjZXd5NkFXN1hrSkhOWTBTa0tRS09kZDNRVzNkZGs1UG1lZWlVZ2tiUlJ2bFcKZlRKaTloRUNnWUVBMEZsd2gwL296TEJiSXJvVlVYbjBiY2xZeXB5SjVDSnl5eVlzbThtNHB4bHpDLytjR2NYawo0OHd3c0M2TGRMc0tZc1lxazFlWlVnck03bjdsK1lkaXJBbWlVb1N6SkdpOStaWi9EYS9CRGNCU282RXNjZ08rCnhvMDhGNWh3UnFTSzE4bWxPQzFmNXpqazVZWDVqdkxaTFB0bUI4ZkV5RWYrTGN2ZlBCNUNzYVVDZ1lFQXovdWIKYnJ0Ry9nN1FiNFhrTk50QWJRWHFOVEZJYmtVRHlGSEZOUHlScHFPTEtHbDZTdU5jZUtJaDBCbXNRLzAra2plRApaWmUzbFpWTXZDR3JOWk9zVVk0SzNVNzNyTjFGcGdybXBVMUMwL0w1R0Z3SC92Sk5vSFU1MlcrQkxGaTI3YURmCnBRWmJGcjJhSHZyelNuM3lQZ3pCRHpjb25hc1A2ZTMvdTVyTGxaY0NnWUVBcDhDTG9QY1BDdGVuMlZNWVhReWoKYUUzb2h1SDVDRTFRUGc4VGRhKzZWQmhpa0RPVFhSRUFGUVhQNGRybi8rbWxHQmhVS1dRcmwyb0l6TEl4dW5KdQpXUFE4MU5IeFp3eEtnWTNSNkpRdERVUmZoVTM4K2lQWDFBZmRiV1lZYUZpTlRlY1dkeC9aaXRNOVFTeFkzZWJjClE2SjY2U0xJWnpYSUN0bU9lTm9vZXQwQ2dZQjFWYUE1MTBQVTNxeXV6aDJSeUVQUGZlL0V0Sm9GUThBL2lnbzAKdTJ5OFV6V1Z4ZlB0UGRtVVlQdXNlRjljT0FuTjJhMnlhZVp6YURoVFJyZGRVWU44dXlMYitjbjI1eHA4ODFkdAoyR21rUTBaT2ZOVXgrcWJhcUdmTGlJR2FjQzQ3WDIvc25PcFVxUUREQzVhbjV1ZjhJNXZqSnA0dVhTeHNNQTMvClcvUVEzd0tCZ1FDTTBER2R2VE9XeDI4ZWR5ZXdWck94VCtTNW1jZDhidUpWSFVWTFYzWG1hR1gvMm9kWlJJQksKQkNPZ0dpcWVNWm4wNUQ5cXhqOUM5cnpNT2tRcUxKcmFyUVBKQTBHQUFGWHBieGVpT0RVQnpSQ2JQMTV0KzVqQwpRQkU2VUFUVVV5K2ZkcmRpZy8rbVRWdFptZFFBRTVxbTBURlhMU004c0Q0NnhMbzVBZG5ETlE9PQotLS0tLUVORCBSU0EgUFJJVkFURSBLRVktLS0tLQo=
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlpLSTRfNW4wYy1ncDdHaS1zQjVvWXRjVHUzam8zazNwd3NmQzJtVVctb2MifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlcm5ldGVzLWRhc2hib2FyZCIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJkYXNoYm9hcmQtYWRtaW4tdXNlciIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjI2MzJhYmEyLTYxOGMtNDJmNi04Yzk0LTY3YjkyY2UwOTYwNCIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlcm5ldGVzLWRhc2hib2FyZDphZG1pbiJ9.yvmy3Nfz0TKjN03iM6et5tcKDz5-mJEYBDcSPgptTiDzjdSuGw_RfTn-ikuqz-jApN1oelmep5m17vMvXGfeXxv2qOwaSXlT9Ns0r10oRdJ6y_fJ0C9ehJOHuy4eECTq9YRmMFb3t9ZMnm0cLjL18_nW8LBAbgPrZ0n5fHv4VhD1i-2eXnLk4Ii_WSIxHIgDDhAkyNy8nFkRLyolSKj9BHr9u8S-toM-kbn4Hw9e121Zmt3Vs0zAW_KT1tyBrymr5E-4D1HnVzqvICYeVNEZY19IrO0AT469O6iPTfHE_88-VGeaGCYbXr1q7r8JT8fbUeevf8ECoJrcC913_SciTw
使用config文件登录
生成普通账户config文件
创建证书目录
root@master1:~# mkdir /root/rbac/certs
1、创建用户csr证书文件
root@master1:~/rbac/certs# cat lxh.json
{
"CN": "China",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "BeiJing",
"L": "BeiJing",
"O": "k8s",
"OU": "System"
}
]
}
2、签发证书
cfssl安装:
master节点执行
准备证书签发环境:
root@master1:~# apt install golang-cfssl
下载cfssl
项目地址:https://github.com/cloudflare/cfssl/releases
cfssl_1.6.1_linux_amd64:
https://github.com/cloudflare/cfssl/releases/download/v1.6.1/cfssl_1.6.1_linux_amd64
cfssljson_1.6.1_linux_amd64:
https://github.com/cloudflare/cfssl/releases/download/v1.6.1/cfssljson_1.6.1_linux_amd64
cfssl-certinfo_1.6.1_linux_amd64:
https://github.com/cloudflare/cfssl/releases/download/v1.6.1/cfssl-certinfo_1.6.1_linux_amd64
下载上传后,并重命名
root@master1:/data/velero# mv cfssl-certinfo_1.6.1_linux_amd64 cfssl-certinfo
root@master1:/data/velero# mv cfssl_1.6.1_linux_amd64 cfssl
root@master1:/data/velero# mv cfssljson_1.6.1_linux_amd64 cfssljson
赋予可执行权限并移动到/usr/local/bin/目录下
root@master1:/data/velero# chmod a+x cfssl-certinfo cfssl cfssljson
root@master1:/data/velero# cp cfssl-certinfo cfssl cfssljson /usr/local/bin/
注意:
如果使用kubeas部署也可以从/etc/kubeasz/bin/目录下拷贝到master节点上
root@deploy:~# scp /etc/kubeasz/bin/cfssl* master1:/usr/local/bin
master节点测试使用cfssl
root@master1:/data/velero# cfssl --help
从部署节点deploy拷贝集群证书文件到master节点
root@deploy:~# scp /etc/kubeasz/clusters/k8s-cluster1/ssl/ca-config.json master1:/root/rbac/certs
签发证书
root@master1:~/rbac/certs# cfssl gencert -ca=/etc/kubernetes/ssl/ca.pem -ca-key=/etc/kubernetes/ssl/ca-key.pem -config=./ca-config.json -profile=kubernetes ./lxh.json | cfssljson -bare lxh
root@master1:~/rbac/certs# ll
total 24
drwxr-xr-x 2 root root 120 Aug 19 16:07 ./
drwxr-xr-x 3 root root 19 Aug 19 15:52 ../
-rw-r--r-- 1 root root 483 Aug 19 15:58 ca-config.json
-rw------- 1 root root 1675 Aug 19 15:59 user-key.pem
-rw-r--r-- 1 root root 993 Aug 19 15:59 user.csr
-rw-r--r-- 1 root root 219 Aug 19 15:57 user.json
-rw-r--r-- 1 root root 1383 Aug 19 15:59 user.pem
生成集群配置文件kubenetes config
root@master1:~/rbac/certs# kubectl config set-cluster cluster1 \
--certificate-authority=/etc/kubernetes/ssl/ca.pem \
--embed-certs=true \
--server=https://192.168.100.2:6443 \
--kubeconfig=./user.kubeconfig
root@master1:~/rbac/certs# ll
total 24
drwxr-xr-x 2 root root 120 Aug 19 16:07 ./
drwxr-xr-x 3 root root 19 Aug 19 15:52 ../
-rw-r--r-- 1 root root 483 Aug 19 15:58 ca-config.json
-rw------- 1 root root 1675 Aug 19 15:59 user-key.pem
-rw-r--r-- 1 root root 993 Aug 19 15:59 user.csr
-rw-r--r-- 1 root root 219 Aug 19 15:57 user.json
-rw------- 1 root root 1937 Aug 19 16:07 user.kubeconfig
-rw-r--r-- 1 root root 1383 Aug 19 15:59 user.pemset-cluster 设置集群名称
--server 指定apiserver地址
3、设置客户端认证
复制用户证书到k8s集群证书目录下
root@master1:~/rbac/certs# cp lxh.pem lxh-key.pem /etc/kubernetes/ssl/
创建用户认证到集群配置文件
root@master1:~/rbac/certs# kubectl config set-credentials lxh \
--client-certificate=/etc/kubernetes/ssl/lxh.pem \
--client-key=/etc/kubernetes/ssl/lxh-key.pem \
--embed-certs=true \
--kubeconfig=./user.kubeconfig
4、设置上下文
root@master1:~/rbac/certs# kubectl config set-context cluster1 \
--cluster=cluster1 \
--user=lxh \
--namespace=rbac \
--kubeconfig=./user.kubeconfig
5、设置默认上下文
root@master1:~/rbac/certs# kubectl config use-context cluster1 --kubeconfig=user.kubeconfig
Switched to context "cluster1".
6、追加用户token到集群配置文件
root@master1:~/rbac/certs# kubectl describe secrets -n rbac lxh-token |grep token
Name: lxh-token
Type: kubernetes.io/service-account-token
token: eyJhbGciOiJSUzI1NiIsImtpZCI6IlpLSTRfNW4wYy1ncDdHaS1zQjVvWXRjVHUzam8zazNwd3NmQzJtVVctb2MifQ.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJyYmFjIiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9zZWNyZXQubmFtZSI6Imx4aC10b2tlbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJseGgiLCJrdWJlcm5ldGVzLmlvL3NlcnZpY2VhY2NvdW50L3NlcnZpY2UtYWNjb3VudC51aWQiOiI0MjdhMDdmNi1hYzNhLTRjZDItYWViNC0xOGJlMTNhYjZiZTIiLCJzdWIiOiJzeXN0ZW06c2VydmljZWFjY291bnQ6cmJhYzpseGgifQ.UnCLtXk96Ycj30jR_4NAaIxwfoSoeg36Clvgnc6UOJAdhf2f5jMSvw174AshDZfcDb4S-gWZbRNeN0-RsT8MocXqa37LQg_ZgoMQAhAvc7fxH32dhoPENrIvX63z9KISCpFqdeU5AX4vL_XIH9LXXjOdcbALYMsiDw_DwupLqajzIyzuu9aCMqrrAVA-RUtnKRaRfCWw4hL0Y39hKpf0QxEnY7jzrg906-6Kcl7zC9izkEb4WMG2Fsw0USGNEnjWPcI1DaZtXIpUnHOecpZlgpWFCSZwaldz3TI0QMzhCTi3nVKUkz3iVjiYUoOpKS5buTFfBJNyolRkgsw-H3bqlQ
root@master1:~/rbac/certs# vim user.kubeconfig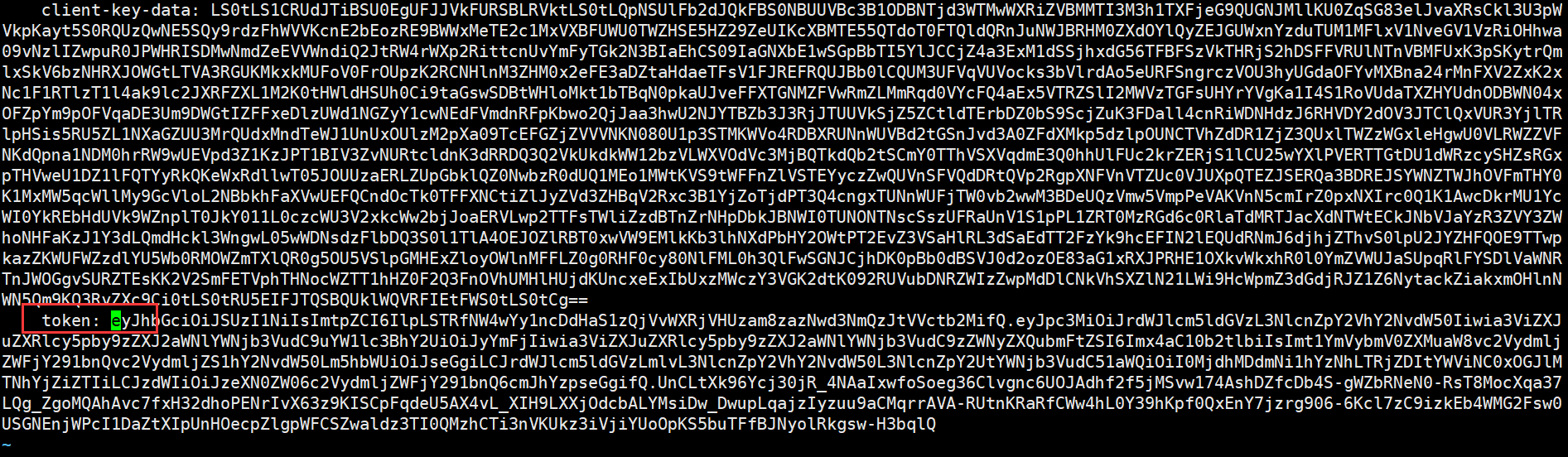
使用user.kubeconfig登录kuboard
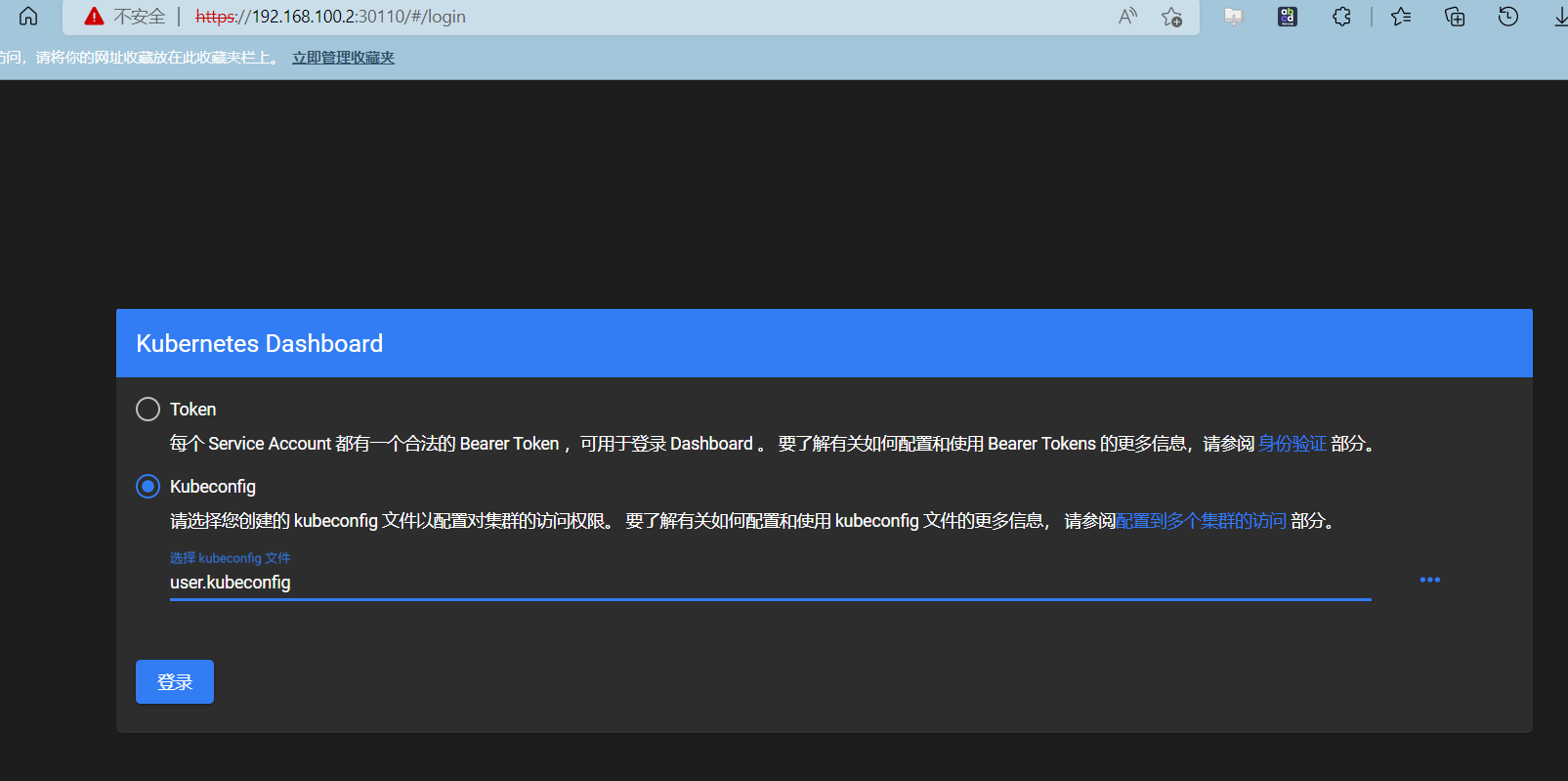
登录成功
本文来自博客园,作者:PunchLinux,转载请注明原文链接:https://www.cnblogs.com/punchlinux/p/16603504.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号