注册驱动
注册驱动
最近看xp内核的时候,竟然要自己注册驱动,在网上简单的搜了一下,发现没什么教程。
后来灵机一动,自己学逆向的,把平时注册驱动的程序给逆一下不就好了吗?
查看壳
好像没什么问题
ida静态分析
简单的看了一些程序自己的函数,发现有Dialogfunc,点进去看看
先来看看这段源码
.text:00402275 DialogFunc proc near ; DATA XREF: start+E↓o .text:00402275 .text:00402275 hDlg = dword ptr 8 .text:00402275 arg_4 = dword ptr 0Ch .text:00402275 arg_8 = dword ptr 10h .text:00402275 arg_C = dword ptr 14h .text:00402275 .text:00402275 push ebp .text:00402276 mov ebp, esp .text:00402278 mov eax, [ebp+arg_4] .text:0040227B cmp eax, 111h .text:00402280 jnz short loc_402295 .text:00402282 push [ebp+arg_C] ; int .text:00402285 push [ebp+arg_8] ; int .text:00402288 push [ebp+arg_4] ; int .text:0040228B push [ebp+hDlg] ; hWnd .text:0040228E call sub_401B0F .text:00402293 jmp short loc_402310 .text:00402295 ; --------------------------------------------------------------------------- .text:00402295 .text:00402295 loc_402295: ; CODE XREF: DialogFunc+B↑j .text:00402295 cmp eax, 110h .text:0040229A jnz short loc_4022AF .text:0040229C push [ebp+arg_C] ; int .text:0040229F push [ebp+arg_8] ; int .text:004022A2 push [ebp+arg_4] ; int .text:004022A5 push [ebp+hDlg] ; hWnd .text:004022A8 call sub_40196B .text:004022AD jmp short loc_402310 .text:004022AF ; --------------------------------------------------------------------------- .text:004022AF .text:004022AF loc_4022AF: ; CODE XREF: DialogFunc+25↑j .text:004022AF cmp eax, 24h .text:004022B2 jnz short loc_4022C7 .text:004022B4 push [ebp+arg_C] .text:004022B7 push [ebp+arg_8] .text:004022BA push [ebp+arg_4] .text:004022BD push [ebp+hDlg] .text:004022C0 call sub_4021F7 .text:004022C5 jmp short loc_402310 .text:004022C7 ; --------------------------------------------------------------------------- .text:004022C7 .text:004022C7 loc_4022C7: ; CODE XREF: DialogFunc+3D↑j .text:004022C7 cmp eax, 5 .text:004022CA jnz short loc_4022DF .text:004022CC push [ebp+arg_C] ; int .text:004022CF push [ebp+arg_8] ; int .text:004022D2 push [ebp+arg_4] ; int .text:004022D5 push [ebp+hDlg] ; hWnd .text:004022D8 call sub_40217E .text:004022DD jmp short loc_402310 .text:004022DF ; --------------------------------------------------------------------------- .text:004022DF .text:004022DF loc_4022DF: ; CODE XREF: DialogFunc+55↑j .text:004022DF cmp eax, 233h .text:004022E4 jnz short loc_4022F9 .text:004022E6 push [ebp+arg_C] ; int .text:004022E9 push [ebp+arg_8] ; hDrop .text:004022EC push [ebp+arg_4] ; int .text:004022EF push [ebp+hDlg] ; int .text:004022F2 call sub_402222 .text:004022F7 jmp short loc_402310 .text:004022F9 ; --------------------------------------------------------------------------- .text:004022F9 .text:004022F9 loc_4022F9: ; CODE XREF: DialogFunc+6F↑j .text:004022F9 cmp eax, 10h .text:004022FC jnz short loc_40230A .text:004022FE push 0 ; nResult .text:00402300 push [ebp+hDlg] ; hDlg .text:00402303 call EndDialog .text:00402308 jmp short loc_402310 .text:0040230A ; --------------------------------------------------------------------------- .text:0040230A .text:0040230A loc_40230A: ; CODE XREF: DialogFunc+87↑j .text:0040230A xor eax, eax .text:0040230C leave .text:0040230D retn 10h .text:00402310 ; --------------------------------------------------------------------------- .text:00402310 .text:00402310 loc_402310: ; CODE XREF: DialogFunc+1E↑j .text:00402310 ; DialogFunc+38↑j ... .text:00402310 xor eax, eax .text:00402312 inc eax .text:00402313 leave .text:00402314 retn 10h .text:00402314 DialogFunc endp
发现有6个call函数,其中有个是EndDialog,其他几个依次点进去看看(由于之前我用过这个软件,所以我知道这函数的部分功能和字符串)
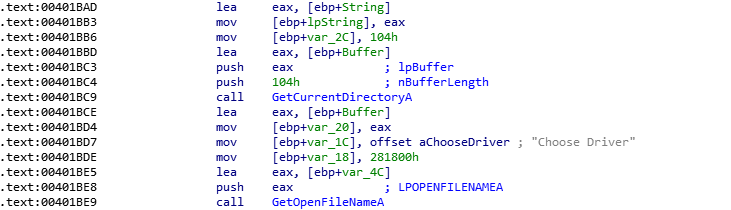
第一个函数,简单的看了下,发现调用了GetCurrentDirectory,用来获取文件的路径的
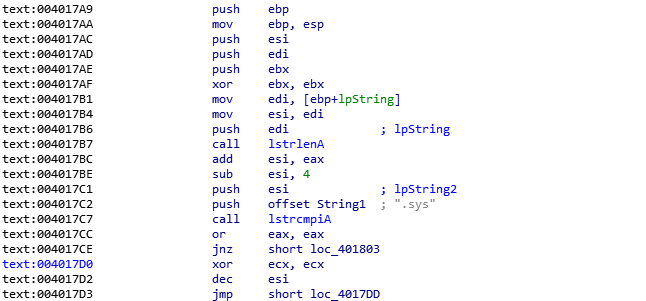
接着往下看,有一个函数,验证是否为.sys驱动文件
再看后面的函数
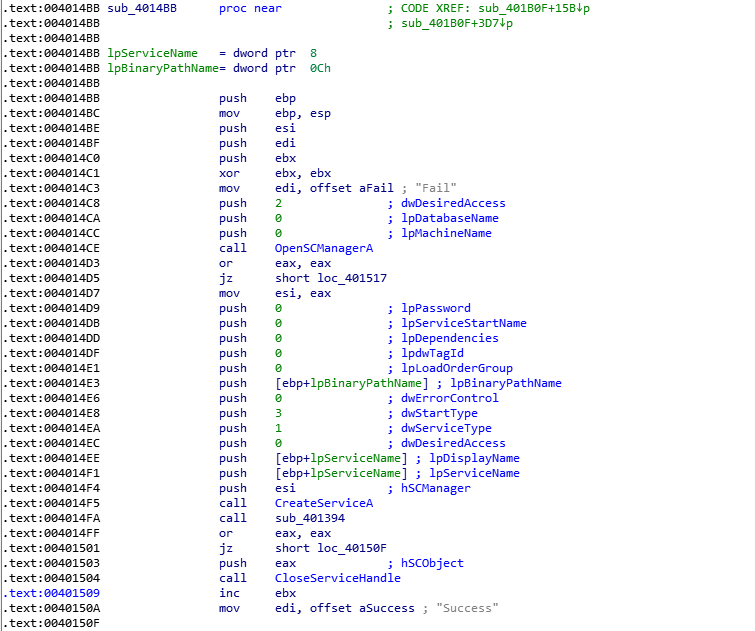
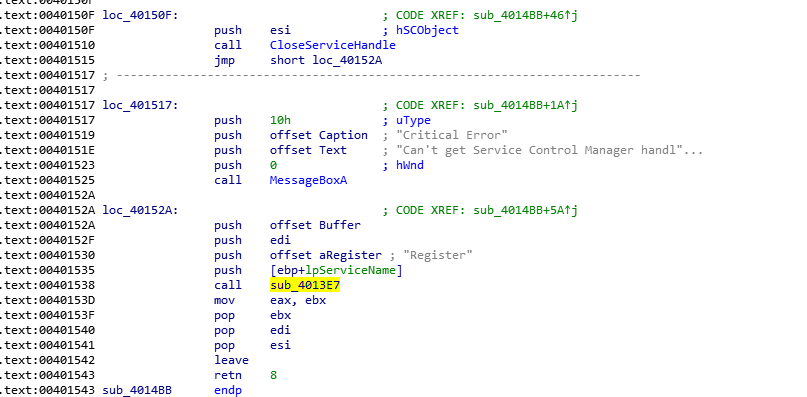
函数CreateService查了文档后,发现是创建服务的,来看看函数原型
SC_HANDLE CreateService( SC_HANDLE hSCManager, // handle to service control manager database LPCTSTR lpServiceName, // pointer to name of service to start LPCTSTR lpDisplayName, // pointer to display name DWORD dwDesiredAccess, // type of access to service DWORD dwServiceType, // type of service DWORD dwStartType, // when to start service DWORD dwErrorControl, // severity if service fails to start LPCTSTR lpBinaryPathName, // pointer to name of binary file LPCTSTR lpLoadOrderGroup, // pointer to name of load ordering group LPDWORD lpdwTagId, // pointer to variable to get tag identifier LPCTSTR lpDependencies, // pointer to array of dependency names LPCTSTR lpServiceStartName, // pointer to account name of service LPCTSTR lpPassword // pointer to password for service account );
知道注册驱动的地方后,该去找卸载驱动的地方了
由于我用过程序,发现卸载驱动里有个unregister,所以我直接交叉引用一下就行

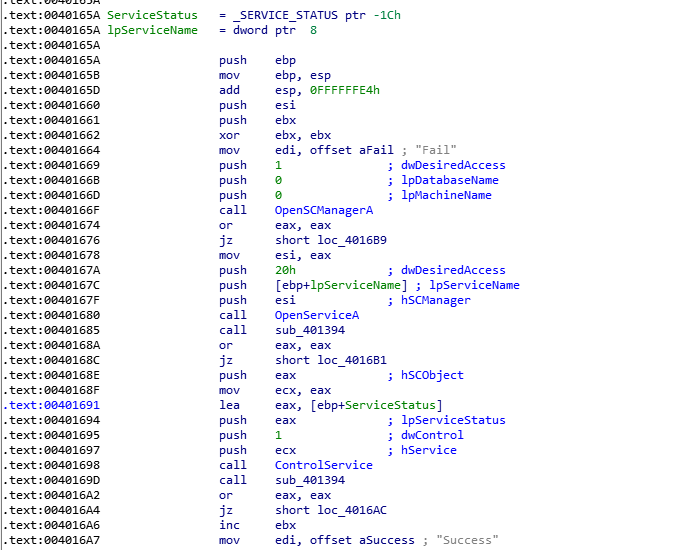
这是停止驱动的代码
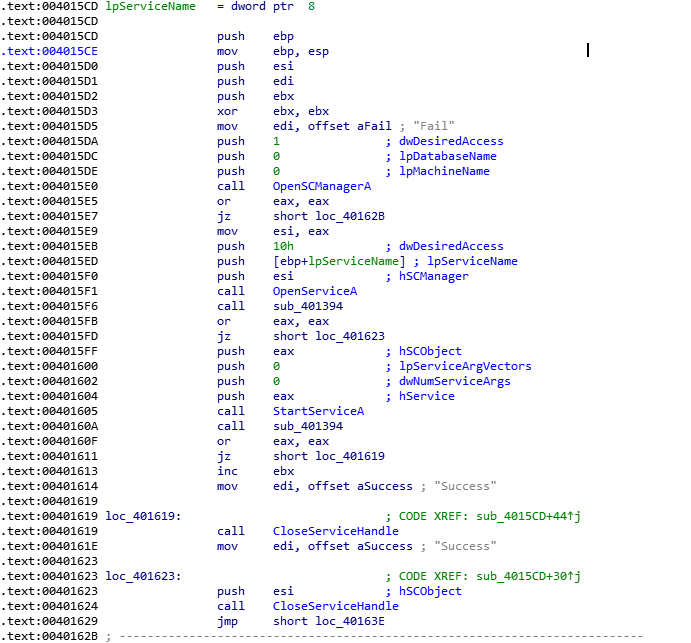
运行驱动的代码
总结
写的不是很好,没有敲注释上去,所以注册驱动、运行驱动、停止驱动、卸载驱动也就是那么几个函数,并且这个程序相对于比较简单的。





